Anti-virus report for 2017: forget about malware

Nowadays, in just a few hours more malware is being created than in the entire twentieth century. Targets are changing, techniques are becoming more complex, the number of attack vectors is increasing, and the tools for carrying out attacks have become more individual and are being created for specific targets. The attackers carefully study their victims in order to adapt their strategies and achieve the maximum possible effect.
The effectiveness, efficiency and profitability of cyber-attacks are constantly confirmed by numbers: during 2017, on average, up to 285,000 new samples were found daily.
The PandaLabs anti-virus laboratory prepared an annual report and presented its forecasts for 2018 .
')
Introduction
Luis Corrons
Technical Director of the PandaLabs antivirus laboratory

In the heart of the company
In a company that develops information security solutions, the anti-virus laboratory is its brain. It is from here that threat research activities and cyber defense techniques are coordinated.
We bear on our shoulders the entire burden of responsibility for the safety of our customers. If one of them is infected, then it will be a failure for us. The good news is that the number of malware incidents that are analyzed in PandaLabs tends to zero.
One way to evaluate that we do our work really well is to analyze and evaluate our decisions by an independent test lab. These days, the most thorough research is certainly carried out as part of testing real-world security solutions (Real World Test) from AV-Comparatives . This test gives the highest mark for detecting threats, and it was awarded to our solutions:


What's the secret?
In the final chapter of this report, I will speak about this in more detail, but in general the secret is to “forget” about malware. If we focus on anti-malware, the battle will be lost before it starts.
Using Machine Learning technology to protect our users means that PandaLabs technicians get significantly more time and resources to research the attacks themselves.
And this is very bad news for intruders. Our team Threat Hunting analyzes and tracks abnormal patterns of behavior, no matter how innocent they may seem at first glance. As a result, we were able to detect a huge number of new attacks, some of which we will cover in this report.
The combination of the most advanced technologies and managed services allows us to classify 100% of active processes and clearly know what is happening during their execution. Unlimited visibility and absolute control reduces the impact of any threat to zero.
Evolution of attacks
In companies and banks, there are many more cases of robberies than ever before, but with the peculiarity that attackers can now be thousands of kilometers from the victim, never physically approaching her.
In fact, the attacked device may not have access to data or resources of interest to cyber-criminals, because such a device can only be used as an attack launch point.
They will use horizontal promotion through the corporate network until they find the data they are interested in or the system they want to disable.
Thus, these new technology to penetrate the system of protection and concealment of malicious programs allow threats to go unnoticed in corporate networks for long periods of time.
Now
Cyber crime is an attractive and profitable business. Malefactors use more (and better) digital and financial resources that allows them to develop more and more sophisticated attacks.
Almost everyone can launch an attack thanks to the wider availability of technology, the black market and open source tools. As a consequence, we all should proceed from the fact that any company can be the target of an advanced attack in order to start working on effective policies and security measures. Having mechanisms for detecting, blocking and eliminating any type of modern threats can protect your company's money and its reputation.
Almost all these crimes have an economic basis: everything is done for the sake of money. Hackers attract profitable victims. It is for this reason that we must take all possible measures to make it harder for them to launch an attack and prevent them from achieving their goal, thereby reducing their effectiveness.
In most cases, when an attack becomes difficult and attackers cannot reach their final goal, it will be easier for them to move on to another victim, where they will be able to carry out their attack faster and easier and get a higher payback level of their “investments”.
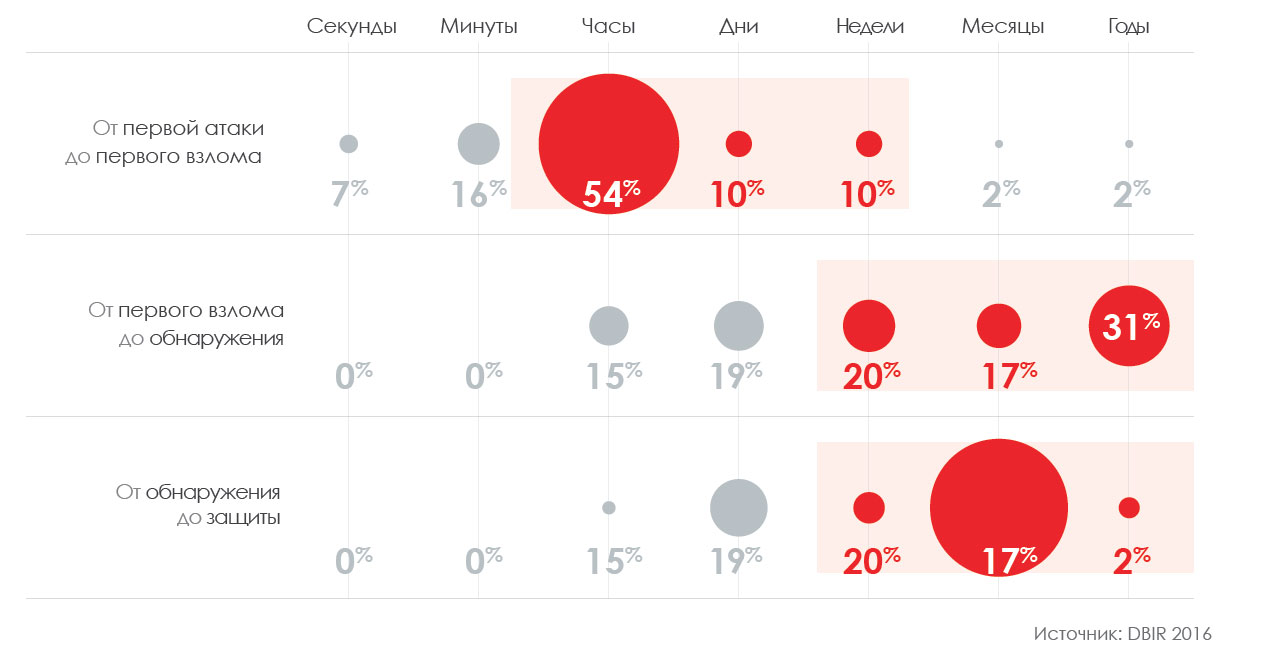
To give you an idea of the complexity of such attacks, let's say that hacking techniques were used in 62% of security breaches in companies. In fact, in only 51% of cases, hackers used malware . In other cases, they used other tools against which most companies are not protected.
In the event that your company has fallen victim to a cyber attack, it is extremely important to have expert information about it in order to know what steps need to be taken.
It is also useful to know where the attack started from, what techniques were used in it, what advances were made, how defenses were overcome, etc.
Other motivating factors
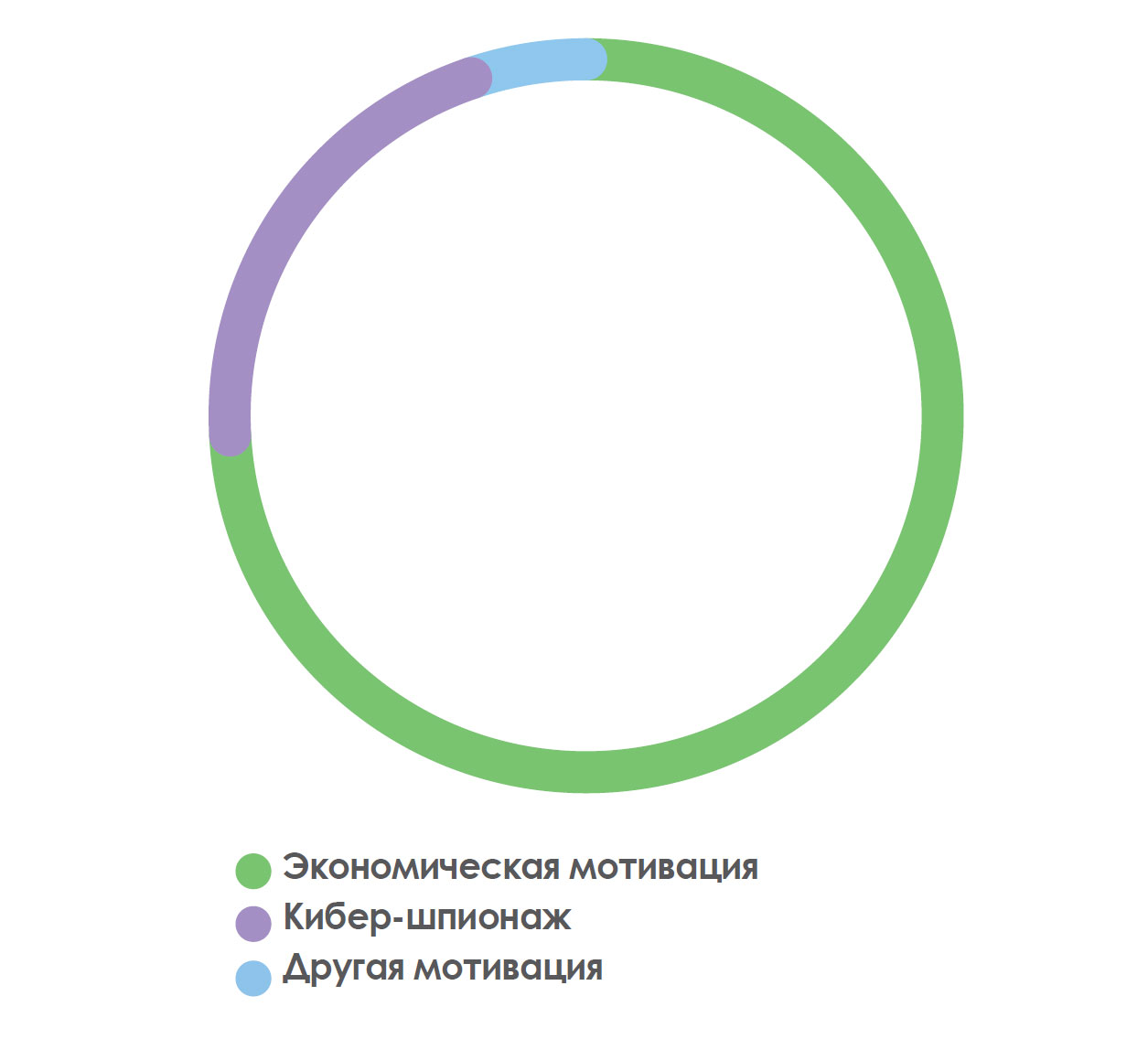
While most attacks are financially motivated, there is still a small percentage of attacks that have completely different goals.
In 2017, we saw the Petya / GoldenEye attack directed against Ukrainian companies. The motive was political, and the Ukrainian government openly accused the Russian government of being behind these attacks.
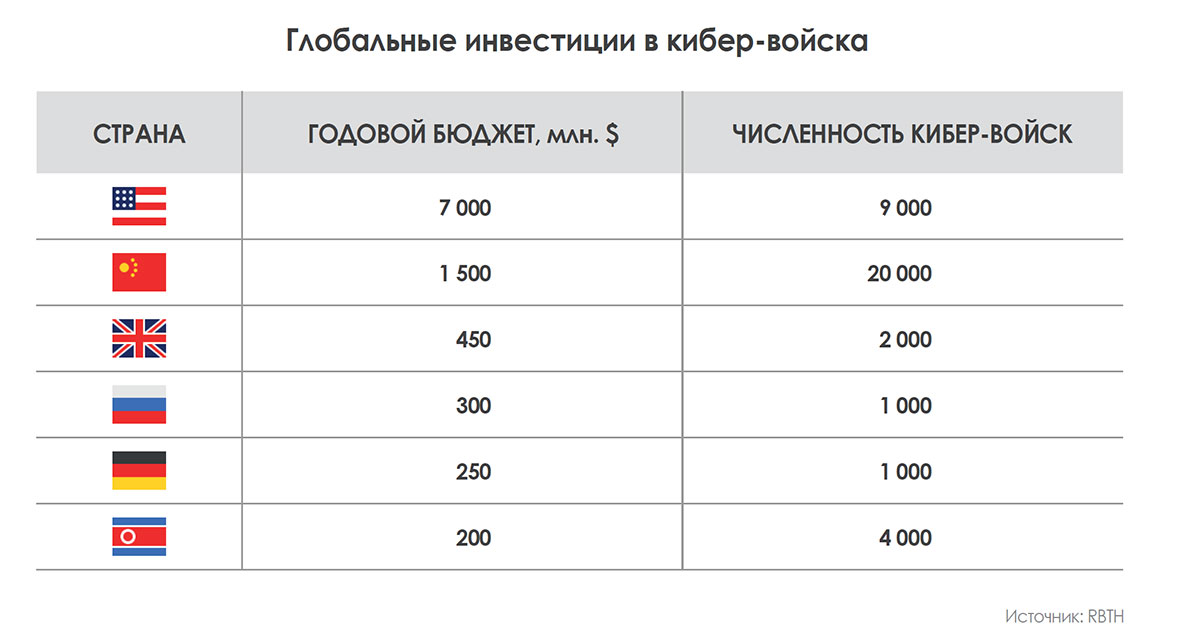
But this is not an isolated case. We are in the epicenter of the cyber-arms race, while countries create cyber troops not only for offensive operations, but also as a key initiative to enhance protection against external threats.
For example, the information security plan adopted by the previous US President Barack Obama forces his successor to prepare 100,000 new computer security experts by 2020. In fact, the goal for 2018 is to have 133 teams for cyber troops (Cyber Mission Force) .
All countries consider it a priority to include cyber troops in their armed forces as another operational unit. Indeed, such units often have at their disposal rather large budgets.
Trends
Knowing your enemy
New attack vectors help create increasingly complex attacks. Cyber criminals create new tools to take advantage of exploits. To complicate matters, they no longer rely on human interaction for the success of their attacks.
This approach involves a thorough study of their victims, their armed reaction to the operation of very specific security holes, and also involves the use of automatic and rapid spread of malicious programs without the need for human intervention.
They interact in real time with the victim's network and its security solutions, adapting to its surroundings to achieve their goals.
It is crucial to know what we are dealing with.
We at Panda Security created Cyber-Kill Chain to better visualize things from the point of view of intruders, revealing the various steps they take from the first stage to the moment they reach their final goal:
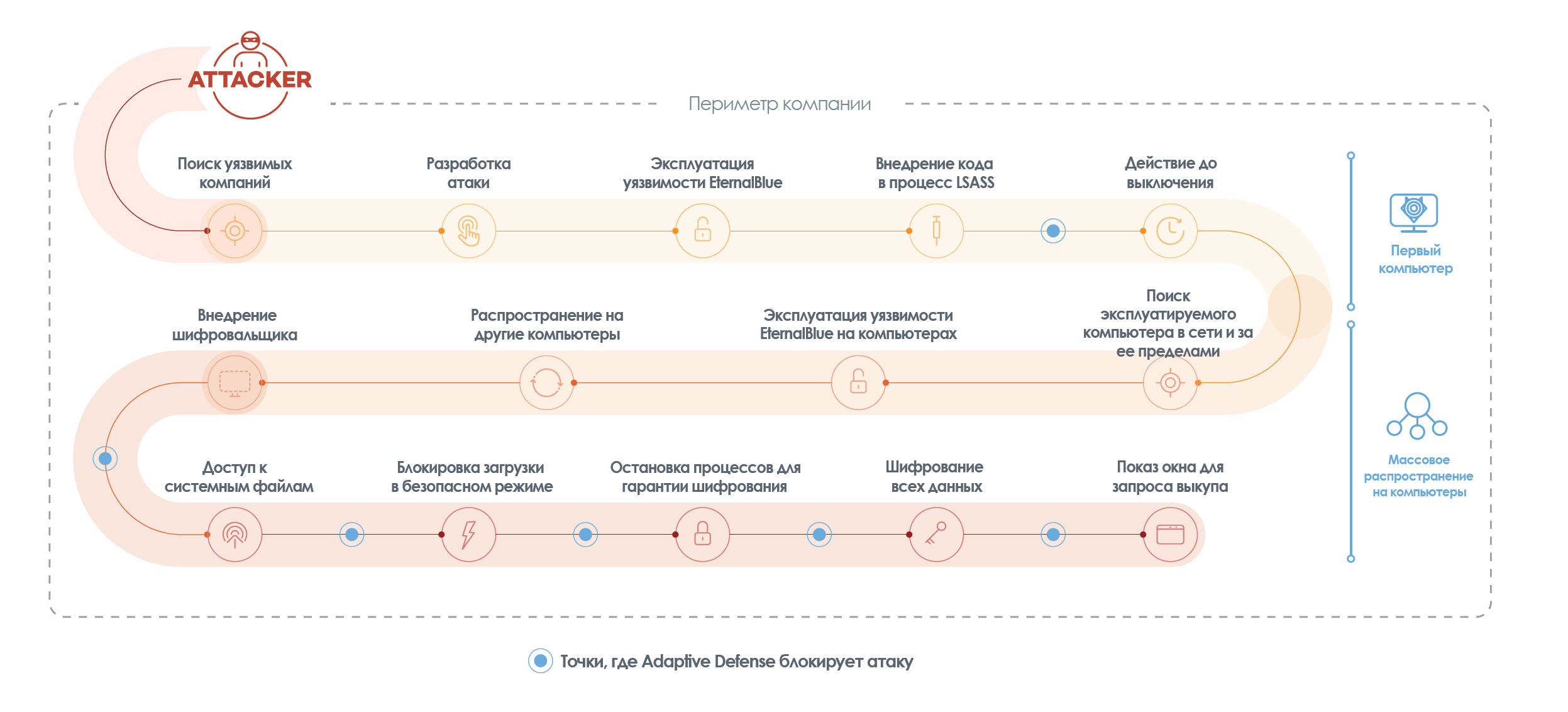
This sequence is an excellent tool for understanding how companies can significantly increase their protection capabilities by detecting and blocking threats at each stage of the attack life cycle.
Cyber-Kill Chain shows that while hackers have to go through all these phases of the chain in order to succeed, all we need to do is “just” stop the attack at any stage.
This document provides you with a detailed explanation of each section. You can also watch our video .
Target - end device
It is worth mentioning one critical moment, if we are talking about attacks. In many cases, security solution providers spend a lot of time talking about the perimeter of the network, the Internet of things and other vectors that need to be protected, but most importantly, what is often overlooked: the end device itself.
Why is this so important? If attackers cannot reach the target device, they will not be able to access other targets, extract information, collect network data, or deploy new attacks. This trend is clearly shown in the following graph (the proportion of security incidents depending on the purpose):
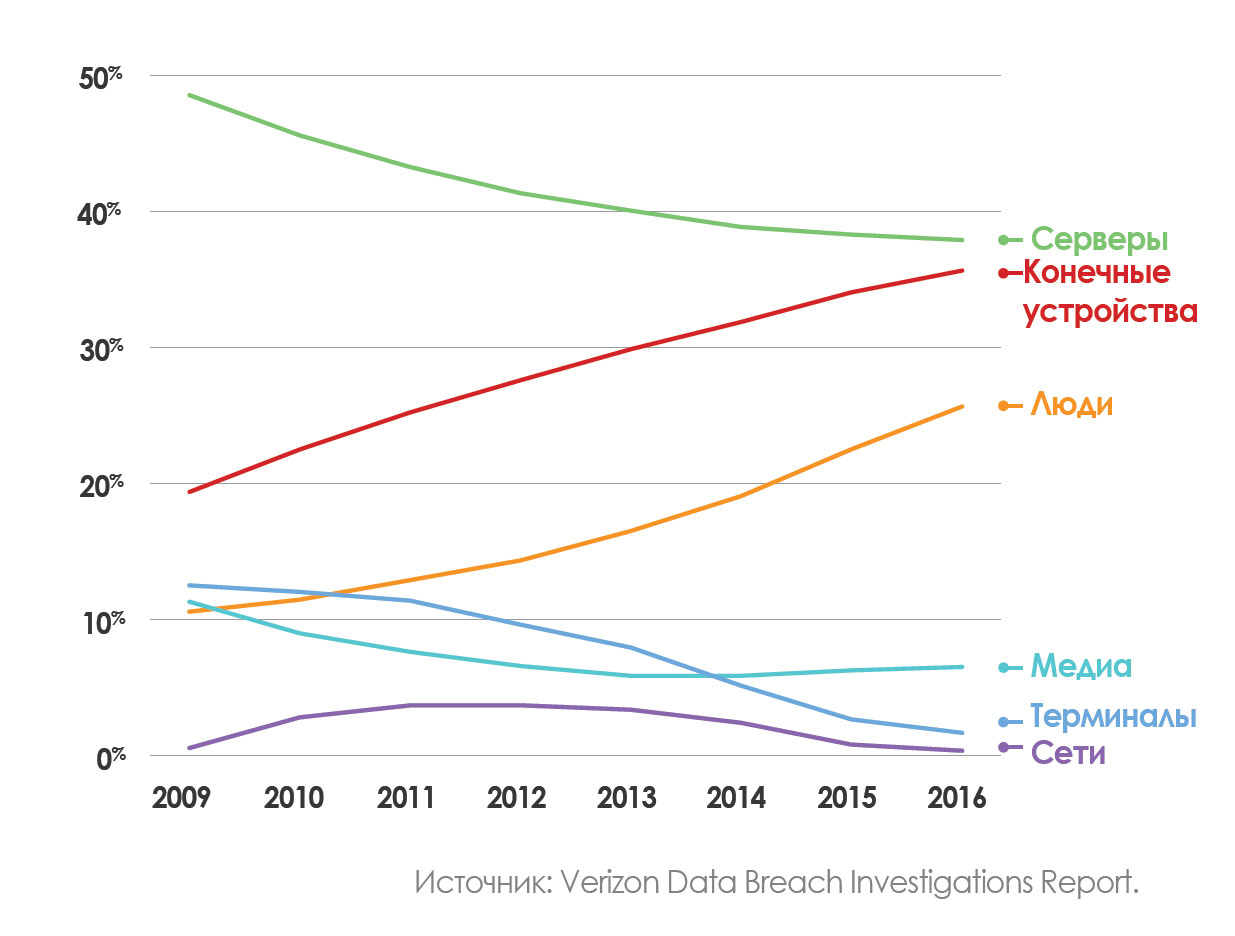
Nevertheless, significant funds in the budgets of companies for security are allocated to protect the perimeter of the network, neglecting a critical part - the final device.
This is not due to ignorance or negligence. In the past, focusing on the network perimeter really made sense. Inside the corporate network, the end devices were mostly secure, so the priority was shifted to protection against external attacks that had to overcome the perimeter.
Today, the situation has changed dramatically: the perimeter is blurred, mobility has become the norm in any company, and corporate networks are subject to much greater impact.
Malefactors more often turn their views on individual computers, knowing that if they manage to get at least to one of them, then the probability that they will be able to perform subsequent actions before they are detected becomes very high.
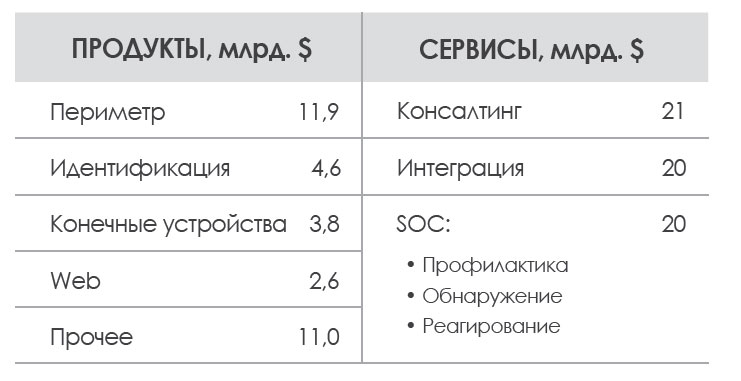
Thus, it is about setting priorities, i.e. not about the need to increase investment, but about where to invest. This was demonstrated in the Capgemini study, in which the level of investment in security was compared to the level of actual protection of corporate assets:
Numbers
One of the most obvious consequences of professionalizing attacks was an exponential increase in the number of malicious programs. According to Verizon, only the number of attacks with encryption increased by almost 50%.
This is due not only to the fact that the number of attacks has increased (although this is also true). Mostly, it depends on the expansion of the set of techniques used by cyber criminals.
More than 10 years ago we published an article where we discussed this trend. In a retrospective analysis, we saw that in 2002 10 of the most common threats caused 40% of all infections, and in 2006 this figure dropped to 10%.
What is the situation in 2017?
Since all our solutions interact with our cloud; we have all the data to analyze whether this trend has become more pronounced.
To calculate the indicators, we tied up all the malware (PE files) that we did not meet until January 1, 2017. As of September 20, 2017, we received 15,107,232 different malicious files. And these are the only ones that we have never met before. The total number of malicious programs created is significantly higher, because all the file types should be added here (scripts, documents, etc.), as well as those that, although they have just been created, have never attempted to infect our clients. The actual number should be about 75,285,000 new malware samples.
Below are 10 samples of malware that most often figured in our cloud:
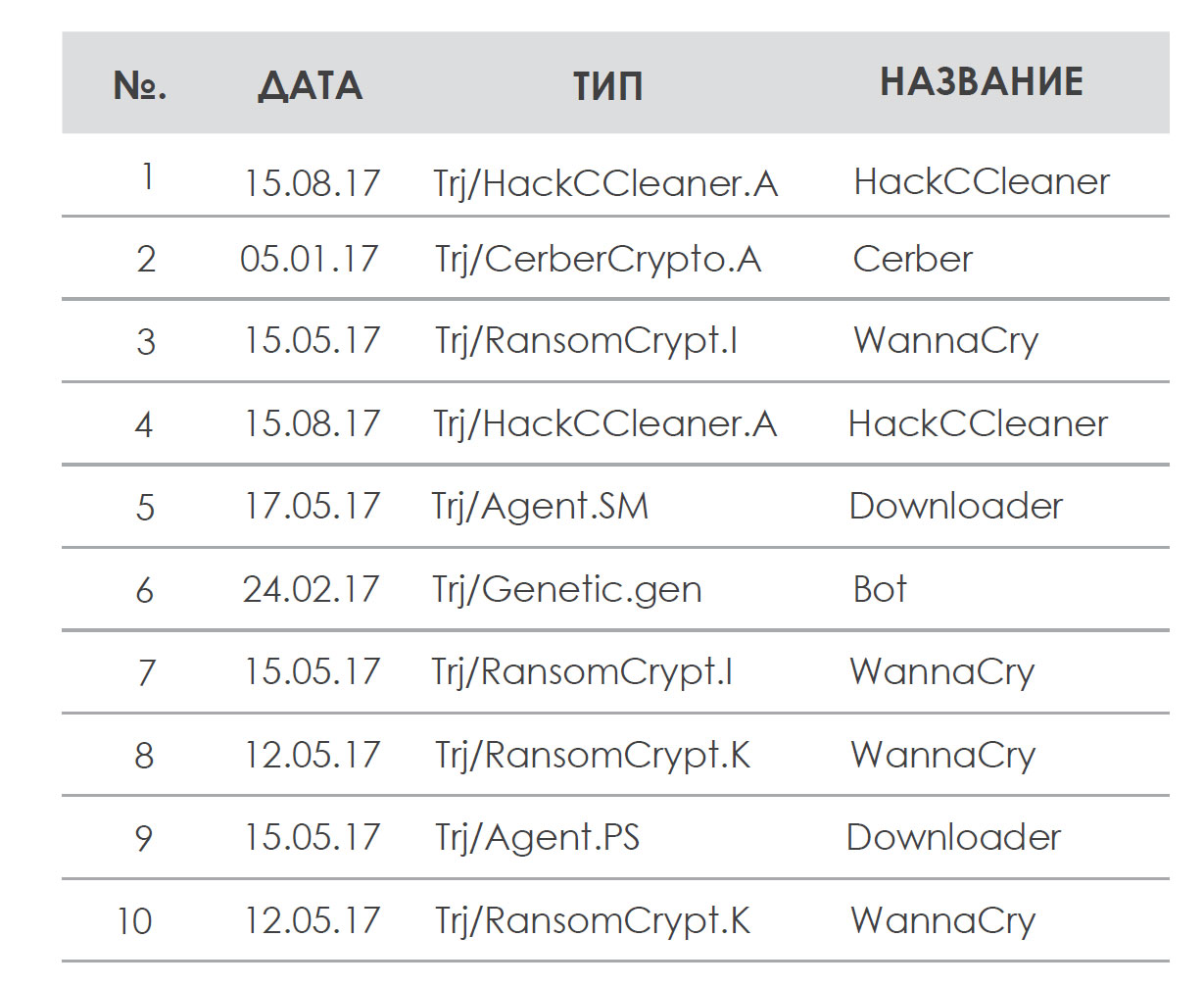
It is logical that in this “top ten” we see files related to the most serious cases that occurred in 2017: for example, WannaCry (3, 7, 9 and 10 places) and “backdoor” version of CCleaner (1 and 4 places). The rest are boot loaders (Trojans, used as an intermediary for installing all types of malware) and a bot.
Of all 15,107,232 malware samples, how many of them have we seen only once? 99.10%, i.e. 14 972 010 samples.
If we look at the numbers from the other end, we will see that only a fraction of the total number of threats is widespread.
We saw a total of 989 malicious files that were present on more than 1000 computers, i.e. only 0.01%.
This confirms what we already know: with some exceptions (for example, WannaCry or HackCCleaner), most malware changes with each new infection, so each sample has a very limited distribution.
Grouping them by families or types, it is not surprising that cryptographers (ransomware) stand out noticeably, since this is one of the most profitable types of attacks, therefore, the most popular (every year this popularity only increases).
In any case, if we want to know what risks of infection we face, then the total number of new malware samples is not so relevant indicator, in contrast to how often we can deal with them. To calculate this indicator, we measured only the attempts of infection by malware that are not detected by signatures or heuristics, including malicious attacks, fileless attacks or such attacks, within which quite legitimate system tools are used (this is becoming increasingly common in corporate environments as we saw in the case of Goldeneye / Petya in June).
For the measurements, we used data that is collected by a number of our own technologies that make up what we call Contextual Intelligence. It helps us identify patterns of malicious behavior and generate advanced cyber-defense actions against known and unknown threats.
Then we began to analyze the data on attacks.
Not all of us have the same means of protection, because Home PCs or computers in small companies are more likely to have a basic level of protection (they are more at risk), while medium and large companies have much more resources allocated for data protection.
In this report, we will take into account only those attacks that have passed all levels of protection, were not detected and were stopped at the last moment just before the computer was compromised. Companies that allocate more funds to security should have fewer such attacks — indeed, this statistic confirms. While for home users and small companies, the share of such attacks reaches 4.41%, in medium and large companies this figure drops to 2.41%.
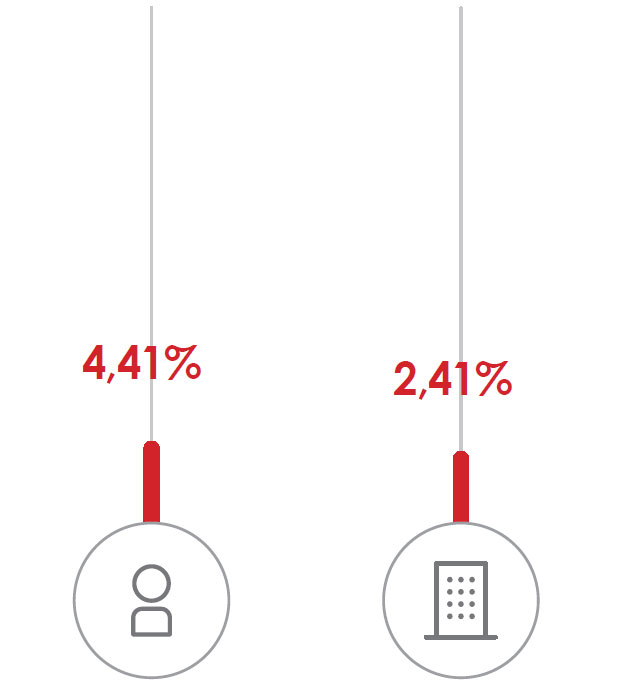
Although this data can “reassure” companies, we advise you not to deceive yourself: in order to cause damage to a company, attackers do not have to attack all computers in the corporate network. In fact, they will attack a small number of computers in order to go unnoticed, minimize the risk of detection and achieve their goals.
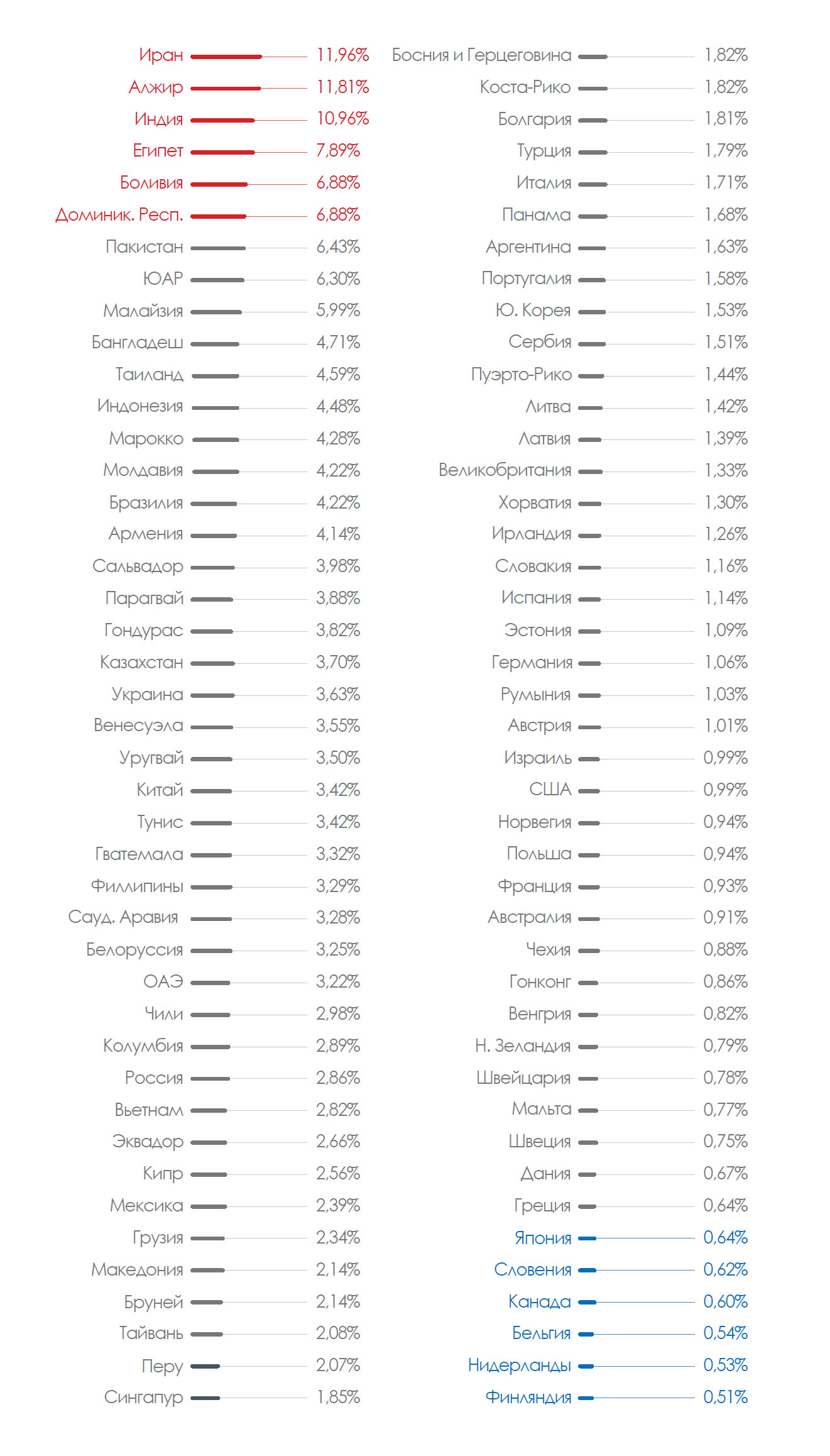
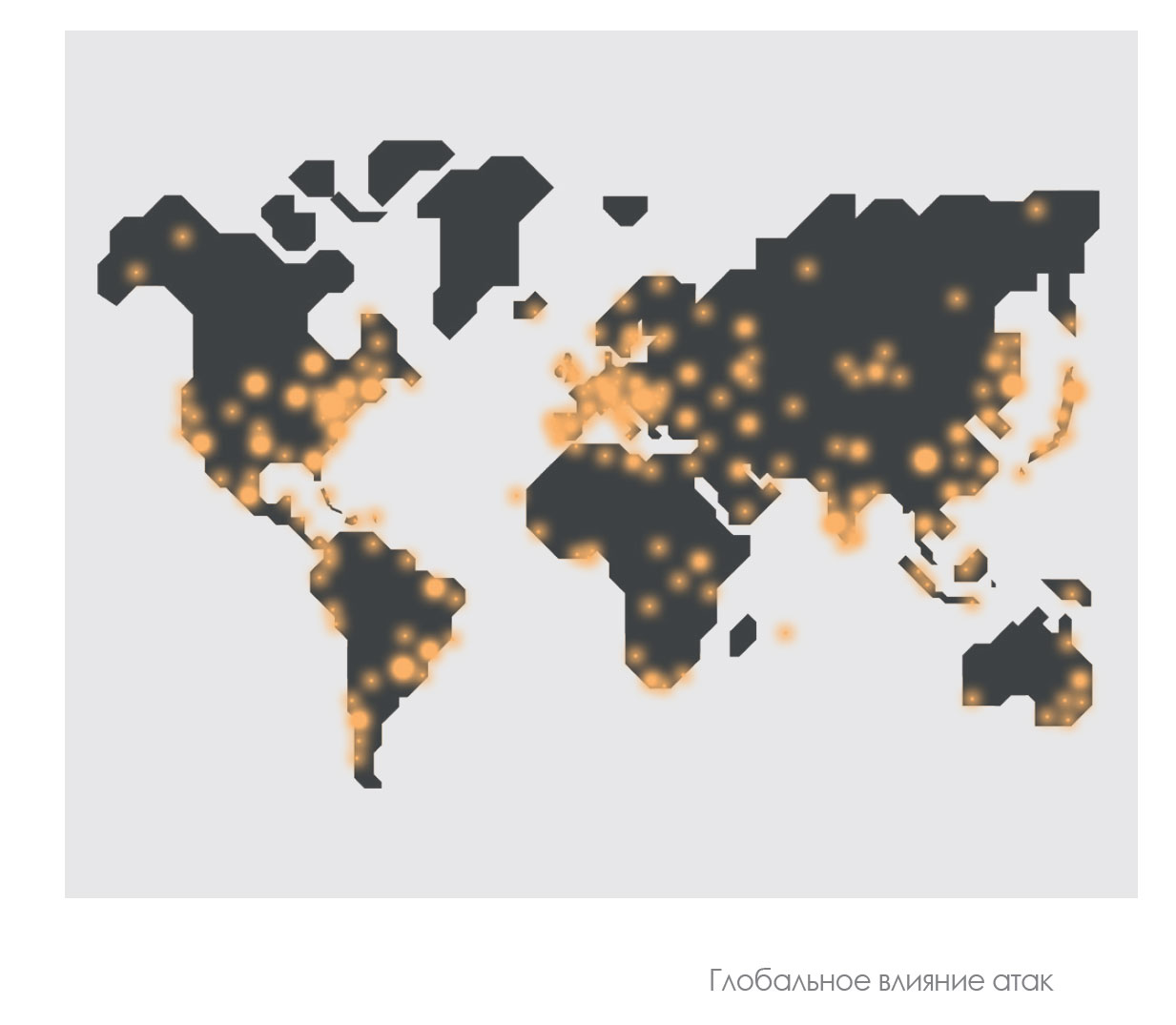
Geographical distribution of attacks.
We calculated the percentage of machines attacked in each country: the higher the percentage, the more likely it is to become a victim of new threats when using a computer in this country:
A look at 2017
Tracking the biggest attacks of 2017 is a bit like a rollercoaster ride: you cannot see what is ahead and you do not know how high you will rise or how much you will fail until you pass these sections. But despite this uncertainty, one thing is for sure: you have never seen anything like it, and you cannot easily forget about it.
Equifax, CCleaner, Saber, WPA2, Vault7, CIA, KRACK, NSA, Election Hacking ... are just some of them that we will analyze below. They cause massive infections, data thefts, encryption attacks, hacked applications, cyber wars, targeted attacks against large corporations, and vulnerabilities that hit billions of devices.
But there are two attacks that stand out from the rest due to the degree of impact and the level of damage done: WannaCry and GoldenEye / Petya.
WannaCry appeared in May 2017, wreaking havoc on corporate networks and spreading around the world, becoming one of the most serious attacks in history. Although we have seen more powerful attacks in the past (for example, Blaster or SQLSlammer) in terms of the number of victims and the speed of propagation, nevertheless, the damage from previous attacks was secondary compared to their distribution. However, in this case, being a cryptographer with network worm functionality, WannaCry blocked and encrypted data on every infected computer.
Luis Corrons, Technical Director of PandaLabs, conducted a webinar where he analyzed in detail what had happened and considered the measures that should be taken to protect against other attacks of this type. You can listen to the webinar here .
Goldeneye / NotPetya was the second most noticeable attack in 2017, like a jerk during the WannaCry earthquake. Although his victims were initially limited to a specific geographical area (Ukraine), companies from 60 countries of the world were ultimately affected by this attack.
A carefully planned attack was carried out through the MEDoc accounting application, which is very popular among companies in Ukraine. The attackers compromised the update server of this program, as a result of which all the computers on which MEDoc was installed could automatically be infected by this malware.
In addition to encrypting files, if the user under which the session was launched on a computer has administrator rights, the malware has moved to the main boot area (MBR) of the hard disk. At first it seemed that this was a WannaCry style encryptor, but after careful analysis it became clear that the hackers didn’t actually plan to provide the ability to recover files. A few days later, the Ukrainian government openly accused Russia of involvement in the attack.
Luis Corrons also spoke about this attack and its authors in his webinar, which you can listen to here .
Cyber crime
According to the Internet Crime Report 2016 Internet Crime Report , published by the Internet Crimes Complaint Center (known as IC3) created by the FBI, the damage caused by cybercrime increased by 24%, reaching 1, 3 billion US dollars. It should be noted that we are talking only about the amount reported by victims from the USA in IC3, which, according to the Center, makes up only 15% of the total number of incidents. So real damage in the USA alone can reach $ 9 billion only during 2016.
The most attractive exploits for launching attacks are known as zero-day exploits, since they are unknown to software makers and allow hackers to compromise users, despite the fact that their software is completely updated.
In April 2017, a zero-day vulnerability was discovered that affected some versions of Microsoft Word, and then it became known that it was used by hackers since at least January. In the same month, Microsoft released the required update for Office users.
RDPPatcher demonstrates the increasing level of professionalism of cyber crimes. This attack , discovered by the PandaLabs laboratory, is preparing its victim’s computer for “renting” on the black market.
Cyber criminals are doing everything possible to avoid detection, and the most effective method for this is not to use malware. Therefore, attacks that do not use malicious programs have become very popular. In the case of PandaLabs, the hackers on the computer left their open backdoor, which they later used to access the device without the need to install malware and using the sticky keys option.
In the second half of 2016, we saw several DDoS attacks, which were talked about a lot in the media, and in 2017 there were even more of them, although they were not so powerful. For example, Lloyds Bank customers had problems accessing their online bank as a result of a DDoS attack, which affected their servers.
The Italian police opened a cyber-spy network called Eye Pyramid , organized in January 2017 by two Italian citizens (they were relatives) for spying on institutions and authorities, enterprises, businessmen and politicians.
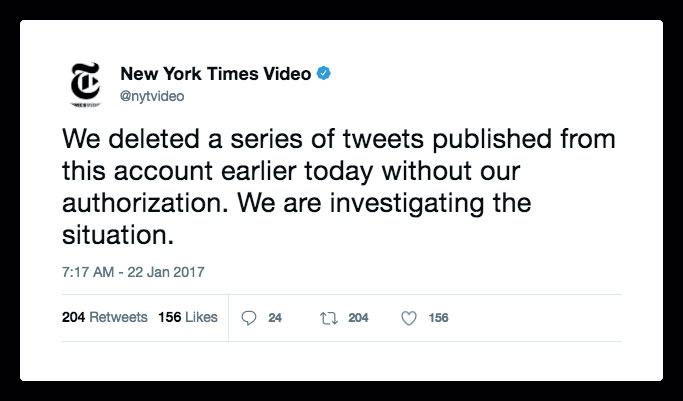
Hacking accounts in social networks has become commonplace, and one of the most striking cases occurred in January with the official New York Times Twitter account, which was hacked. As soon as they regained control of their account, they removed the tweets posted by hackers:
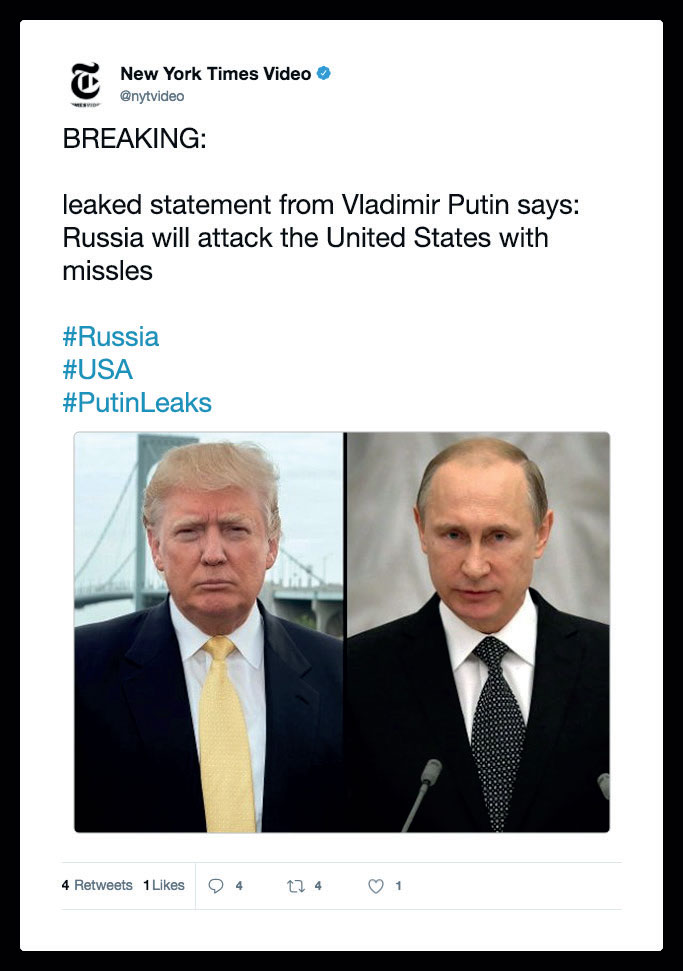
Here is an example of one of the tweets that was published on a hacked account. It states that Russia plans to launch an attack against the United States:
The same group of hackers hacked accounts of other companies, such as Netflix and Marvel.
A group of cyber criminals, known as “Turkish Crime Family”, blackmailed Apple, demanding a ransom under the threat of data destruction on iPhones, iPads and Macs owned by 250 million users. Apple did not give in to blackmail.
Corporate data theft
In 2017, data theft incidents also flashed on the news headlines. Perhaps the most ironic story of the year happened with the Israeli company Cellebrite, which offers services for hacking phones, in particular, to extract data from mobile devices. So this company was hacked, as a result of which 900 GB of data were stolen from it, including the client base, databases, as well as technical information about the company's products.
Medical records of at least 7,000 people were compromised in a security incident at the Bronx Lebanon Hospital Center in New York (USA).
Another type of security incidents in which intruders are not involved is associated with error or carelessness, with the result that data that needs to be reliably protected becomes public knowledge. This happened in the USA when the Republican party hired marketing companies accidentally left the data of 198 million registered voters (almost all of their registered voters) available to everyone.
Dow Jones accidentally allowed access to the data of 2 million of its users through the Amazon cloud service as a result of a configuration error. In this data it was possible to find user names, their email addresses, and bank card numbers.
22 were arrested in China for trafficking in Apple customer data. All evidence pointed to the fact of insider Some of the detainees worked in companies that are partners with Apple and have access to this data.
This year, HBO fell victim to several cyber attacks. In one of them, the company's servers were hacked, after which the episodes of the not yet shown series, as well as a number of internal corporate data, were stolen from them.
InterContinental Hotels Group (IHG) fell victim to the attack, which resulted in the stolen data of their customers. Although the company said in February that the attack had affected only about a dozen hotels, however, it has since become known that POS terminals in more than 1,000 of their establishments were infected. This group includes various hotel brands such as Holiday Inn, Holiday Inn Express, InterContinental, Kimpton Hotels and Crowne Plaza.
Saber Corporation is a North American company that manages reservations for 100,000 hotels and tickets for more than 70 airlines worldwide. The hackers received registration data to access one of the booking systems of this company, after which billing information and booking information became available to them.
This particular system manages reservations for individuals and travel agencies in 35,000 hotels and other places of temporary residence. As a result of the attack, 7-month data from 10 August 2016 to 9 March 2017 was compromised.
As a result of the attack on Saber, a number of hotel chains suffered, including Four Season Hotels & Resorts, Trump Hotels, Kimpton Hotels & Restaurants, Red Lion Hotels Corporation, Hard Rock Hotels and Loews Hotels.
Taringa, a popular social network in Latin America, suffered from a security breach, which stole information about more than 28 million users, including user names, email addresses, and MD5 password hashes.
But the biggest security breach in 2017 (and the worst in history) could have happened a little bit later when the giant credit reporting company Equifax was compromised. Due to the nature of the services provided, the company has a huge amount of highly confidential information about millions of people, including social insurance numbers.
The attack was carried out using a vulnerability in Apache Struts on one of the company's servers. Vulnerability (along with a corresponding update, it eliminates) was published on March 6. A few days later, hackers attacked the company's server, which was in a hacked state until the end of July, when this attack was discovered. During this period, data of about 200 million people were compromised, 70% of which are US citizens, and the rest are Great Britain and Canada. Later, the list of affected countries added to Argentina, Brazil, Uruguay, Peru, Paraguay, Ecuador and Chile.
Worse, it later turned out that the three top managers of the company took advantage of the time when the attack was discovered, and when it became known to the public, selling its shares to the company in the amount of $ 1.8 million. The head of security of the company was dismissed, and only a month later, the head of Equifax since 2005, Richard Smith, said that he was retiring.
Trojans
After Goldeneye / Petya, Netsarang encountered an attack, as a result of which, in the version of its five programs (Xmanager Enterprise 5.0, Xmanager 5.0, Xshell 5.0, Xftp 5.0 and Xlpd 5.0), a file was deployed through the backdoor. He had a valid digital signature of the company, which meant complete penetration of hackers into the company at each of its levels. But among the clients of this company there are banks and energy companies.
The loudest case with backdoors in software in 2017 undoubtedly occurred with CCleaner.
Compromised versions of the program have been installed by more than 2 million users. Hacked software expected to receive commands, and probably never performed any malicious actions.
However, Cisco researchers found that hackers had a list of companies whose computers they wanted to compromise. They included 20 well-known and large companies, including Samsung, Cisco, Sony, Intel and Microsoft.
These three attacks indicate that a very professional organization was behind them, and one can believe that they were supported by the governments of some countries. By the way, NATO stated that behind the GoldenEye / Petya attack was also the government of one of the countries.
Ciphers
The number of attacks by cryptographers is still growing, and this will continue as long as companies are willing to pay huge ransoms for returning their data.
In addition to well-known cipher family (Locky, Cerber, and others), there are special, more personalized versions for this type of victim who are willing to pay.
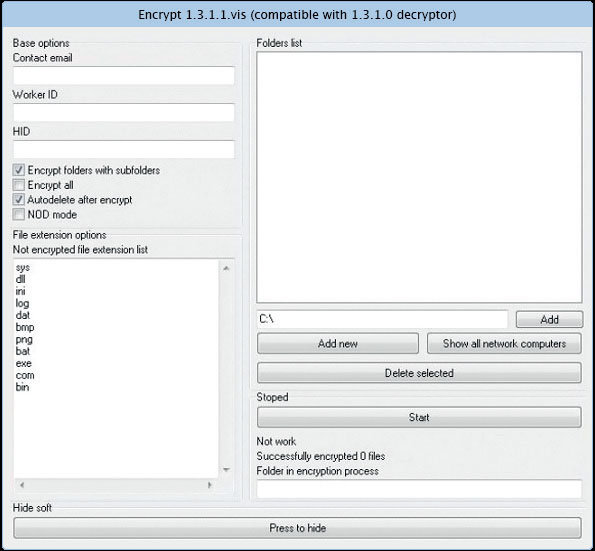
One of them was discovered by the PandaLabs laboratory - it is a cryptographer with its own user-friendly interface, called WYSIWYE, which allows cyber-criminals to set up an attack before launching it:
One of the most popular and simplest methods for penetrating a corporate network is the use of a brute-force attack through a remote desktop (RDP protocol) in Windows. The attackers scan the Internet, searching for computers that have this functionality activated, and after the potential victim has been found, they launch a brute-force attack until they have the correct registration data.
During 2017, we saw numerous examples of attacks of this type, and hackers were mainly from Russia and acted in a similar way: as soon as they got access to the computer via RDP, they installed bitcoin mining software (as a supplement), and then encrypted files or blocked access to the computer.
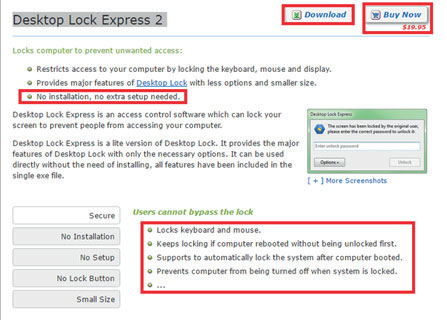
However, they do not always use malware for this. For example, in one of the cases we analyzed, hackers used the commercial application “Desktop Lock Express 2” to lock the computer:
The immediate consequences of a cipher attack are obvious: you lose access to your files.
However, cases of digital “kidnapping” can go far beyond this. As in the case of a hotel in Austria, where hotel guests were locked in their rooms after the cyber criminals turned off the software for electronic locks.
One cryptographer encrypted data on 153 Linux servers owned by the web hosting company Nayana from South Korea. Hackers have requested a ransom of $ 1.62 million. The company agreed with the criminals and reduced the amount to 1 million, which were to be paid in three payments.
Internet of Things (IoT)
For many years, there have been many warnings about the dangers associated with Internet of Things (IoT) devices, mainly due to the fact that when creating many such devices, developers did not pay enough attention to security issues.
Also, because these devices did not have an Internet connection, and therefore did not pose a particular risk, but after they had Internet connection options, they became vulnerable to attack.
It seems that they began to listen to these warnings, and in the United States senators from the Democratic and Republican parties came together to create laws that partially correct this situation.
The idea is to, among other measures, require manufacturers of products with an Internet connection to make them updated (to eliminate security holes), prohibit the use of fixed passwords, and also prevent the sale of products with known security holes.
Smart buildings
In recent years, many buildings have changed. For example, somewhere, smart meters were introduced to control energy consumption in homes and offices. In addition to the possible negative effects on electricity bills reported by consumer protection associations, there are other, less well-known security problems associated with the widespread occurrence of such devices.
As researcher Netanel Rubin explained during the recent Chaos Communications Congress in Hamburg (Germany), these smart meters pose a threat at various levels. First, because they record all the data related to energy consumption in homes and offices, then to send them to utilities, an attacker who managed to gain control over such a device will be able to see this information and use it for criminal purposes.
For example, he could see when consumption is minimal (i.e., the premises are empty) to rob a building. Given that all electrical appliances leave a “mark” on the network, he could even use this information to detect any valuable appliances that could be stolen.
Smart tv
An even more common device is Smart TV. Some of them are running the Android operating system, which has its pros and cons. About this on Twitter wrote Darren Coton, an IT developer from the United States, after an attack was made on the TV of his relative. As Coton explained, all of this happened after the victim had installed an application for watching movies on the Internet from a third-party site.
The TV was a LG model released in 2014 that worked on Google TV - a special Android version for TVs. Once the device was infected, the malware requested a ransom of $ 500 for unlocking the screen. Moreover, the requirement was fulfilled in the form of a notification from the US Department of Justice.
In addition, there are many other dangerous attacks that may indicate what is happening in this area. In February, at a Seminar of the European Broadcasting Union on Information Security, security specialist Rafael Scheel presented an exploit created by him. He can allow a hacker to remotely control Smart TV by simply launching an attack via a TDT signal.
Smart Cities
In Australia, 55 video cameras installed at traffic lights and intersections were cracked after a subcontractor connected the computer to the network to which they were connected.
On April 7, in Dallas (Texas, USA), 156 emergency sirens simultaneously turned on at 23:40. Officials managed to turn them off after about 40 minutes, but only after turning off the entire alert system. It is still unknown who was responsible for the attack.
Auto Industry
There have been reports of a new vulnerability affecting cars, especially Mazda. However, unlike previous cases, in order to compromise a car's IT system, a hacker would have to insert a USB device while the engine was running in a certain mode.
It is not surprising that cars and other cars can have an Internet connection and, accordingly, can be attacked, there are other goals in this sector. For example, car wash. At the Black Hat conference in Las Vegas (USA), researchers Billie Rios and Jonathan Butts showed how they managed to hack automatic car washes connected to the Internet. They hacked the system in such a way that they could physically attack the car and its passengers.
From the automotive sector: Segways can also be hacked remotely, with the result that hackers can control them remotely.
IOActive researcher Thomas Kilbride revealed various security vulnerabilities and incidents. The fact is that segways do not check for updates, and therefore everyone could update the device at any time with a malicious firmware that would do everything a hacker needs.
Critical Infrastructure
Dutch researcher Willem Westerhof analyzed transformers used in solar batteries to convert direct current to alternating current and to supply it to the network of one of the leading companies in the sector, SMA Solar Technologies.
In total, he revealed 21 vulnerabilities that could allow a hacker, say, to control the amount of electricity supplied to the network. Such vulnerabilities can be used remotely via the Internet.
, , . .
, , , , , , , , , .
The Food and Drug Administration at the US Department of Health and Human Services (FDA) warned nearly half a million patients to visit their doctor to update the firmware of various models of Abbott pacemakers.

Mobile devices
Malicious software designed specifically for mobile devices is still inferior to malware developed for PCs, but its basic actions are the same.
The popularity of cryptographers who give excellent results to cyber criminals is also confirmed by their focus on mobile devices.
Mobile Threats
Charger, a new threat for Android, is a good example of how malware is developing for mobile devices. Charger steals contact information and SMS messages, locks the terminal, requesting a ransom under the threat of selling some of your information on the black market every 30 minutes. The redemption rate is 0.2 Bitcoin.

Large companies are concerned about this issue, resulting in initiatives such as the Google Project Zero Contest, which increase rewards for those who find the most serious zero-day vulnerabilities (not previously discovered). The prize for first place increased from 50,000 to 200,000 US dollars, and the
second - from 30,000 to 150,000 US dollars.
Vulnerabilities
Vulnerability (CVE-2017-6975) in the firmware of Broadcom Wi-Fi chips HardMAC SoC made Apple urgently release an iOS update (10.3.1). This vulnerability, when reconnected to Wi-Fi, affects not only Apple products, but also mobile devices from other manufacturers, such as Samsung or Google, that released their updates in response to this problem in April 2017.
But if there is a vulnerability that seriously wins the "battle", then it should be KRACK, affecting the WPA2 protocol. It refers not only to mobile devices, because It affects all types of devices where WPA is implemented (PCs, routers, etc.), but still it is worth noting that the main problem concerns users of Android mobile devices.
The problem was discovered in 2016 by Belgian researchers Mati Vanhof and Frank Pessens, but it was not publicly announced until October 2017. One of the open source implementations of this protocol, “wpa_supplicant”, used in Linux and Android, is particularly vulnerable to this attack.
After Google releases the appropriate security patch for its operating system, a huge number of device manufacturers are required to implement new updates. In addition, there are hundreds of millions of devices in the world that are no longer supported by their manufacturers, and therefore, they will never receive the required updates. This problem is typical for this ecosystem.
Cyber war
Presumably, the two main attacks of the year (WannaCry and GoldenEye / Petya) were committed by the governments of two states (North Korea in the case of WannaCry and Russia in the case of GoldenEye / Petya), although there is no evidence of that. In any case, these are just a couple of cases within the framework of a fierce and covertly conducted cyber war.
The main actors are the same: the United States, Russia, the DPRK, China and Iran, although in most cases it is impossible to be sure who is actually behind any attack, because malefactors almost always do a good job of sweeping up all their tracks, and sometimes even expose other criminals.
Cyber attacks and politics are now intertwined more than ever before. After we “survived” the last US presidential elections, and before leaving the White House, Obama announced new sanctions against Russia, accusing it of organizing cyber attacks against the election campaign of Democratic Party candidate Hillary Clinton in favor of Donald Trump. As a result, 35 Russian diplomats were expelled, and two Russian-owned centers were closed.

The consequences of this are felt throughout the world. France refused to use e-voting for citizens living abroad due to the “extremely high risk” of cyber attacks. In the Netherlands, they went even further: they began to manually check the votes on the night after the elections and transmit the results by telephone to avoid the risk of possible cyber attacks.
- , , -.
, - .
, - -. 260 , 14 500 2021 .

-.

On March 7, WikiLeaks began publishing a series of documents called “Vault 7”, containing details of the technician and software tools used to penetrate smartphones, computers, and even smart TV. WikiLeaks continues to publish documents and dedicated leaks to a separate section on its website .
The good news is that you can use this public knowledge to better protect against such threats. But the problem is that other criminals can study these techniques and use them to violate the privacy of citizens.
The US is clearly concerned about attacks against US institutions. The Congressional Intelligence Committee held hearings on the consequences of Russia's attack in the 2016 presidential election, where Jeh Johnson, the former secretary of the US Department of Homeland Security under the Obama administration, confirmed that Russian President Vladimir Putin ordered an attack in order to influence the results of the US elections. He also said that Russia was unable to manipulate the voices due to these attacks.
In June, the US government accused the DPRK government of a series of cyber attacks launched since 2009, and warned of a high probability of their continuation.
The warning from the World Bank and the FBI refers to the group of hackers “Hidden Cobra” who attacked the media, aerospace and financial sectors, as well as critical infrastructure in the United States and other countries. There is evidence linking the recent WannaCry attack to this “Hidden Cobra” group, better known as the “Lazarus Group”.
One possible explanation for the fact that the attacks are attributed to North Korea is the expansion of sanctions against them by the UN, forcing them to seek alternative funding.
During the Gartner Security and Risk Management summit, which was held in Washington in June 2017, former CIA director John Brennan spoke about the alleged alliance between the Russian government and cyber-criminals in stealing data from Yahoo accounts. According to Brennan, this is only the tip of the iceberg. He warned that future cyber attacks by the governments of several countries will continue to follow this formula, and their frequency will only grow.
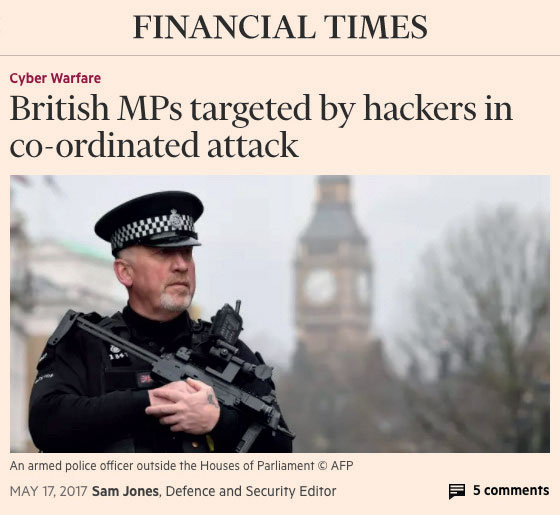
According to the Financial Times, accounts have also been hacked by a number of members of the British Parliament, who are also confident that this attack was sponsored from abroad.
This whirlwind of politically motivated cyber attacks also affects technology companies. The FSB of Russia demanded that companies such as CISCO, SAP and IBM give them the source code of their security solutions to search for possible backdoors. A few days later, the US government banned all federal agencies in the country from using Kaspersky solutions because of its proximity to the Russian government and the FSB.

Although no undisputable evidence has been provided to confirm the malicious activity of Kaspersky, it is clear that in the current situation of tension between the two powers, the US government would in any case be concerned. The United States proceeds from the fact that this company is located in a country whose power they consider almost authoritarian.
They believe that the Russian government can at any time instruct Kaspersky to use its software to launch an attack or steal information in a hypothetical case of conflict escalation.
About Threat Hunting Systems
Inaki Urzai
Chief Security Strategist at Panda Security

The number of information security experts worldwide is growing exponentially. The growth is mainly due to the actions of the governments of different countries that need to play an active role (on their own initiative or as a response) in a virtual conflict in which no one can stand aside. The governments of many countries around the world have for some time created special cyber defense agencies: in Germany, a division has recently been created with more than 13,000 cyber-soldiers, over 100,000 agents should be in the USA by 2020, in the DPRK it already seems to be their order 6,000, as well as similar units, appear to be in Russia, China, Great Britain, France, Spain, Israel, Iran and other countries.
In addition, there are experts working with manufacturers and suppliers of security solutions worldwide. All of these companies have information security experts in all countries of the world. And finally, there are cyber criminals who, as a result of the boom in the growing number of information security experts and global interest in this field, are able to find trained specialists much easier and faster.
This growth in the capacity of highly skilled employees has created an environment in which it is possible to systematically detect software vulnerabilities. It also contributes to the development of professional tools for carrying out attacks (with an improvement in their resilience and scalability), which do not use malicious programs, are carried out by criminals, and are able to adapt to the victim’s environment as quickly as possible.
As we can see with Panda Adaptive Defense, malware-based attacks can well be contained with solutions based on a “strictly positive” model created by Panda Security.
When all applications that attempt to run on a computer are classified, and only those that are really safe are allowed to run, the “detection gap” characteristic of the traditional anti-virus model disappears. Malicious programs can no longer hide in unknown files that are ignored by traditional security solutions.
The market can no longer afford to ignore the ability of this security model to prevent attacks, so it is obvious that this model will have a growing market share.
Since this approach replaces traditional antivirus models, attackers will adapt their techniques to work around it. And in this case, it is possible that attacks that are not based on the use of malicious programs will prevail.
Attacks that do not use malware are characterized by the use of tools that are often used by legitimate network administrators: for example, applications for remote installation of programs, data backup, etc.
In this approach, hackers impersonate an administrator after they can get his network registration data, so in the eyes of any external observer, they will look exactly like a legitimate network administrator performing their work.
Since , . , , Threat Hunting.
Threat Hunting , , , , , .
, , , , , , , - .
, Threat Hunting , . , , , . , , , .
Such tools will allow analysts to run personalized checks on affected computers so that they can “put” themselves at any point in the history of the event on each computer or in the activity of each user and reconstruct their steps to confirm the attack.
In the foreseeable future, traditional malicious programs in the form of clearly malicious specific programs will be replaced by non-malware operations in which the attackers usurp the identity of network users and will perform the actions they require under the guise of seemingly legitimate network users.
, , , threat hunting.
Panda Adaptive Defense — , : Threat Hunting API , , .
Attacks have become more perfect. Changed goal. Techniques have become sophisticated, the number of attack vectors has increased, and the tools for their conduct have become more refined.
The attackers carefully study their potential victims in order to better adapt the strategy of their attacks to achieve the highest possible result. Over 62% of the threats are hackers who are actively engaged in analysis and adapt their attacks accordingly and with surgical precision.

Their effectiveness, efficiency and profitability are constantly confirmed. In 2017 alone, up to 100,000 new holes and security incidents in corporate environments appeared.
, . , , -. . , , . Panda Adaptive Defense , , , , .
Thanks to this development of technology, we are able to tell you about a number of situations in which Panda Security interrupted an attack in time. Our expert research has played a crucial role here. These attacks demonstrate the development of new trends and methods of attack, confirming a Verizon study that asserts that 95% of
security incidents can be reduced to 9 models.

Thus, we also helped to improve the protocols and defensive structures of companies, even on workstations and systems that do not have direct protection from Panda Adaptive Defense.
Horizontal advances
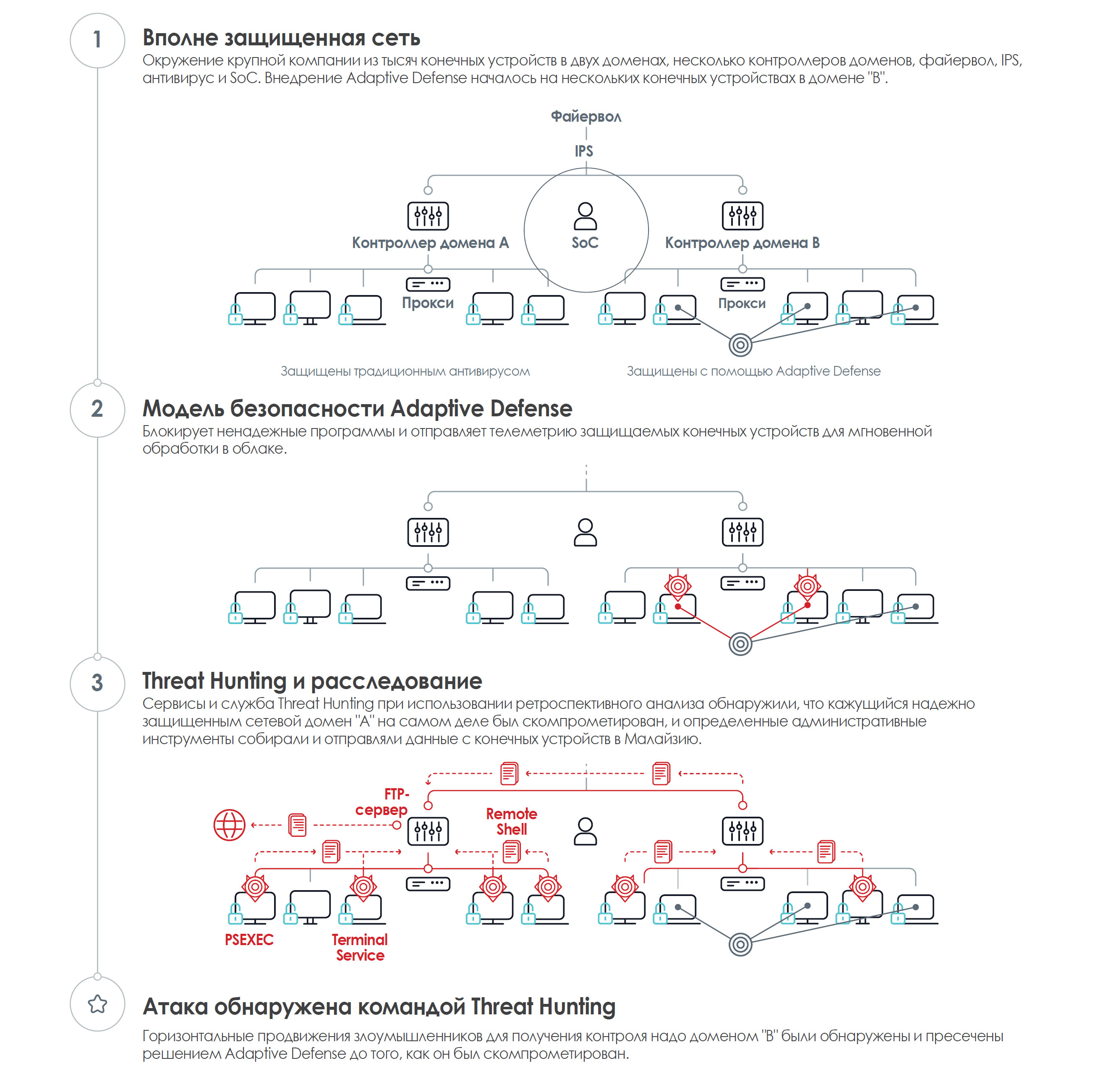
As an example of the evolution of attacks, we begin by presenting a hidden attack with adaptive horizontal promotions. This type of attack is becoming very common. This time, the company has an entire arsenal of detection and protection systems (firewall, IPS, SoC, domain controllers, proxies, traditional protection, etc.).
But no system noticed horizontal progress, which could lead to a successful attack on client assets.
However, the criminals did not expect that the company had Adaptive Defense, which in fact discovered their intentions and thwarted their attack plans:
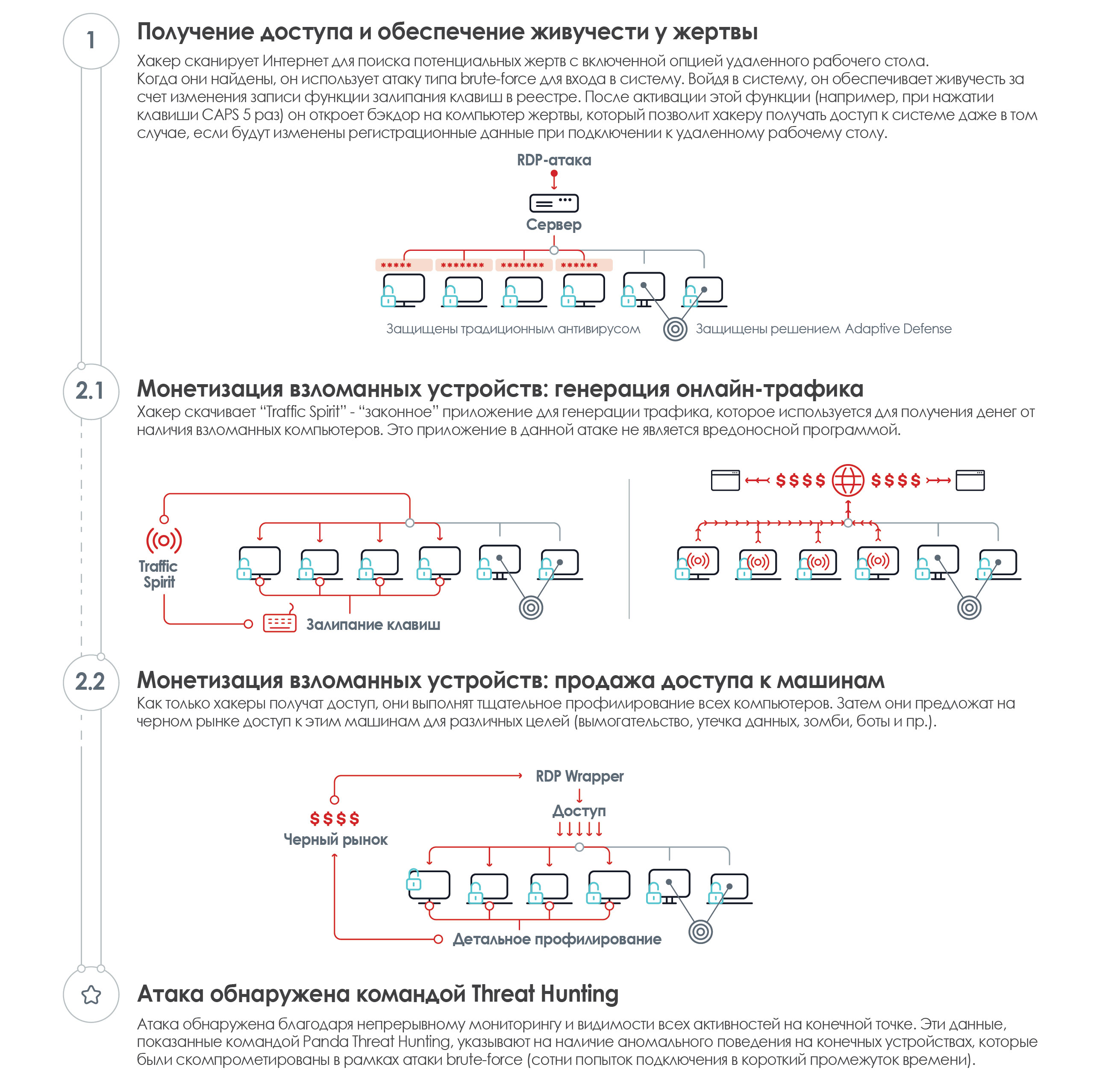
RDP: Attack without using malware
-. 51% , 2017 , - . . , , .
, RDP- : 1) -, -, 2) . . :
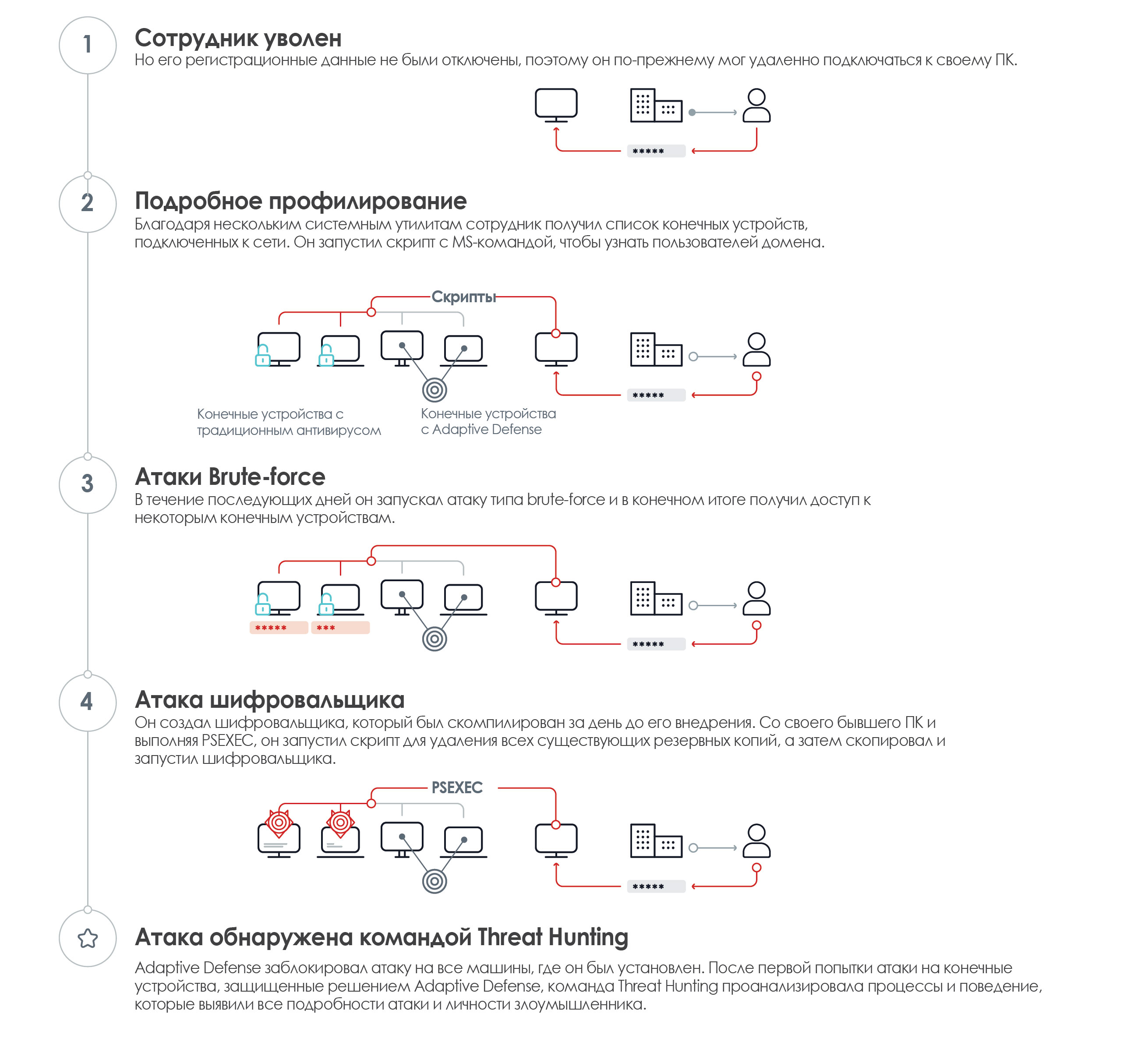
.
2017 , , . , , 25% .
.
81% - .
Despite this, being inside, employees use expansion and control strategies worthy of the best hackers to evade other security systems and damage the company's reputation and finances:
General aspects
Despite some differences, all these cases have a number of similarities:
- Preliminary study of the weaknesses of the company in preparing an attack
- Adaptation of the attack to these shortcomings, covert access, which does not cause suspicion or response from the warning systems in traditional anti-virus solutions.
- Carefully planned and planned internal moves to achieve their goals.
The common goal for all these attacks is money, as always. According to Verizon, a financial target is observed in 73% of attacks, while in 21% of attacks, the motive is espionage.
Another common denominator of all these cases is that all of these attacks were detected and prevented in time by the Threat Hunting team and solutions with enhanced protection capabilities developed by Panda Security.
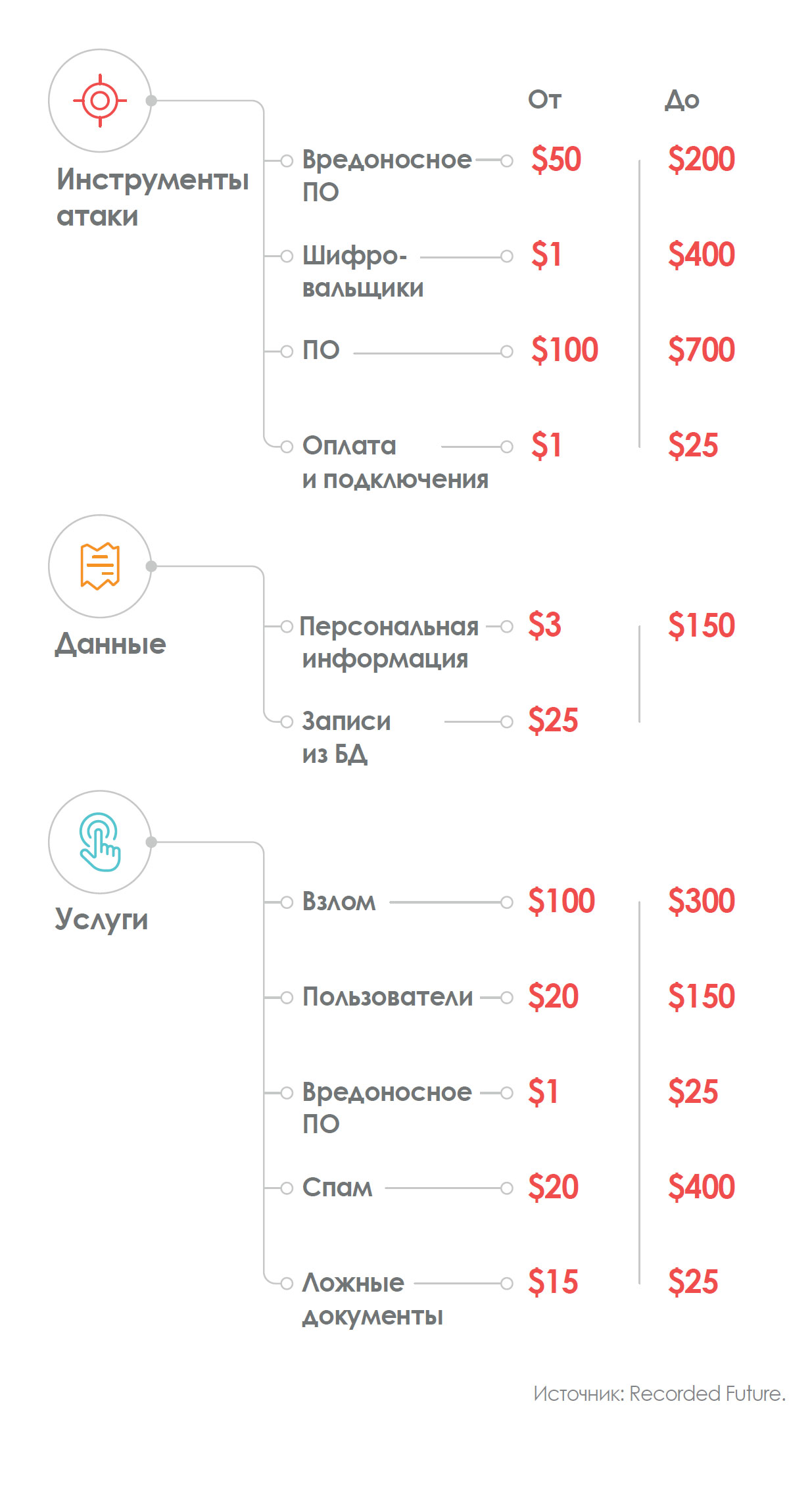
The price of attacks
We have seen how the process of “democratization” of cyber attacks was facilitated by the professionalization of hackers, the evolution of technology and the ease of access to data.
Of course, all this contributed to the popularization of these types of threats, but still these actions are due to the high profitability of the attacks.
Low-cost cyber armies allow cyber criminals to receive serious financial benefits.
GDPR:
( General Data Protection Regulation , GDPR) - .
, GDPR 2018 . .
2018 - GDPR. .
, , 4% .
. , , (Data Protection Officer, DPO). , , GDPR.
, DPO. , .
GDPR:
• , , .
• , .
• , , , ,
IP-.
• .
• « », .
• , ,
GDPR .
• , -.
• , .
• 20 4% , .

GDPR
, .
, , , .
GDPR .
— Equifax , . GDPR, , , , , .
GDPR, Equi fax . 500 , Equifax 20 . , .
GDPR . , , . . , .
, , , .
, .
, 2018 ?
, , , 2018 .
-
- — , . , , - , , , .
,
-, , - . , , . - - . , .
« »
, - , , — , . , , , , , .
— , : , , ..
, : . « » , , -, - .
WannaCry , , .
«» , . Petya/GoldenEye, . , , , , .
, , — , , , . , , : ) , ; ) , . , :
, 2018 ,
— , , , .
2017 , 62% , (49%) , ( 2017 Data Breach Investigations Report, Verizon).
Petya/GoldenEye, MEDoc . , , — CCleaner, , , , .
? : . , , , , .
, . , , , Google (Android, ).
: , Android, , , , .
, , . ? -, IoT- ( IP- ), - .
, IoT- -. , , .
, - — .
2018 , .. , .
, , . - , . , 2018 .
, 2018 50% 2017 .

2018:
, , . , , Yahoo .
2017 , , Sabre Equifax. , 2018 « »? : GDPR.
, 2018 , .
, , , , GDPR, .
. , , .
, — , , , , . . , . Facebook .
Facebook, , . , - Facebook
, Facebook - . , , . , , .
Cryptocurrency
Bitcoin . , . — -, .. .

— , .
, -:
•
• -
•
• -.
Conclusion
After we have seen the global attacks that have hit companies and institutions around the world, it’s important to know how we can protect our privacy and security on the Internet.
Software and security updates should be a priority for all companies. Cases like WannaCry or Equifax confirm this, because every day that passes without updating the vulnerable system puts the entire company at risk, as well as the integrity of its data, including information about its customers and suppliers.
Production may be jeopardized, which may cause millions in damage. One example: the AP Moller-Maersk group was one of the victims of the GoldenEye / NotPetya attack, and according to its calculations, the losses ranged from 200 to 300 million US dollars.
Countries are increasingly investing in defensive and offensive capabilities with a focus on critical infrastructures.
The ability to remotely launch an attack, which can lead to a collapse, is no longer a theory: this has already happened in Ukraine, and this can happen again in any country in the world. Criminal groups with limited funding, however, may have access to the knowledge and tools necessary to launch destructive attacks on critical infrastructure. Moreover, such attacks can be carried out not only by some special services. It is known that terrorist groups, such as ISIS (banned in Russia), are ready to use all cyber means at their disposal to further the spread of terror.
2018 is in a more dangerous position. Many professionals will need to change the mentality (and strategy) to achieve the highest levels of security and protect the assets of their corporate networks.
Anti-malware is just the beginning. We are entering an era when the best security strategy implies a lack of trust in something. Any new process that wants to run on any device connected to the network must first be enabled, and those processes that we trust must be constantly and continuously monitored in order to detect any abnormal behavior as soon as possible.
What is at home, what is in the office, the key aspects are learning and awareness. From this it follows that information security, which leaders often forget, will require more and more investments.
Having in-depth knowledge of the attacks and what they consist of should be the basis for a good defense strategy. Security based on real-time detection and response, combined with expert analysis and detailed information on how the attack occurred, are essential to repel future intrusions. Gartner Peer Insights recommends Panda Adaptive Defense as the leading EDR solution.
Signature files no longer work, and the numbers speak for themselves: over 99% of all malicious programs are never found anywhere else. Collecting signatures is already an insufficient and inefficient way to ensure detection. Many manufacturers of security solutions add them only if testing laboratories later want to conduct a malware detection test on signatures (and this is becoming less common practice), because many still believe that the results of such testing show whether product detect a threat or not.
Solutions that remain focused on the fight against malware (the majority of solutions currently available on the market) are doomed to extinction if they do not change their strategy. The number of attacks that are not used by malicious programs continues to grow. And in the face of this reality, security solutions and their users are completely lost and defenseless.
And, of course, we cannot forget about international cooperation and the creation of a single regulatory framework, for example, GDPR. Having political and economic support, as well as an appropriate action plan, will allow you to benefit from the safe use of the latest technological advances.
In the end, the thing is that it is necessary to revise the principles of information security.
Source: https://habr.com/ru/post/347430/
All Articles