Getting a personal phone number by analyzing and sorting social resources and accounts

In our information age, any technology you use can potentially be used to attack. No exception is the phone number.
In the case considered below, we will show how dangerous it is to use the binding of a single phone number to all accounts used online. We will show how this allows you to find out your personal number.
The situation described below may seem trivial against the background of such vulnerabilities as, for example, it was recently described in relation to T-Mobile users . In this case, the attacker could get full access to the personal data of any T-Mobile subscriber simply based on his phone number. This data included the status of the number and date of registration, IMSI code, email address, answers to secret questions, and even data regarding the date of the last change of the password to access the account.
')
All this information made it easy to initiate the process of replacing a SIM card, after which the attacker actually got full access to the phone, could make calls, send and receive messages, etc.
No, in the method described below, an attack with such a significant gap will not be considered. It will be easier and closer to real life.
Intelligence service
To demonstrate this vulnerability, one of the young developers of the popular XDA Developers resource was chosen. At the forum of this resource, the authors often post a lot of information about themselves, which we will use. Looking ahead, we will immediately say - the developer was not injured in the end and was notified about the problems with his security before writing this article.
The vulnerability was also tested on a US citizen, who was also subsequently notified before writing the article.
First, the attacker locates the victim. This part is extremely simple - many people write their countries and even cities in profiles of social networks - including Facebook. In our case, the developer did not conceal that he was from South Korea and was even proud of it, while the resident of the USA actively described the peculiarities of life in New York.
In addition, the attacker will need the email address of the victim, which is also not a problem in most cases.
After some of these preparations, the hacker enters the “Lost Password” page on Facebook and indicates the email address or username of the victim. If this data matches the existing social network user, and the victim has indicated the phone number as a means of password recovery, we will see the last two digits of this number:
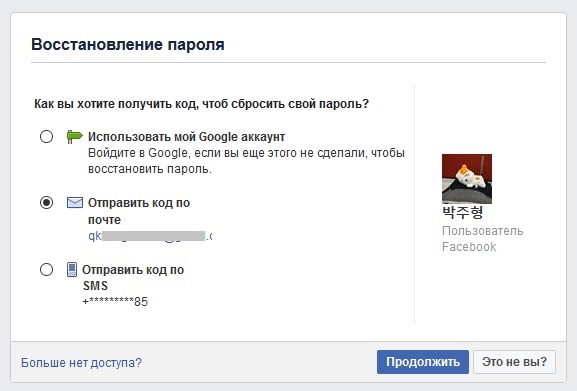
Our victim pointed out PayPal as one of the sources promoting his work on the XDA. The victim from New York also actively posted on eBay shopping experience on Facebook and also had a PayPal account. Visit this site and try to also recover the password by entering the victim's email address:
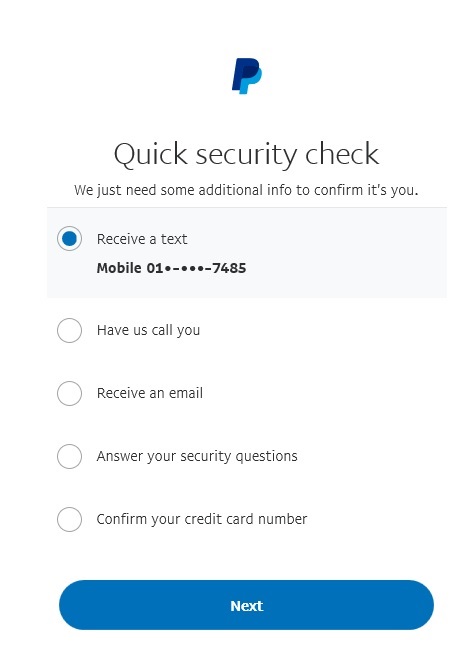
We got four more numbers.
Having carefully studied the activities of the victim with the XDA, we find that it is very active in the development using the latest 4G networks. Based on open sources, we conclude that the number of the victim starts from 010.

In the case of a US citizen, knowledge of the city - the location of the victim also made it possible to significantly reduce the number of possible codes, if the first digit is known:
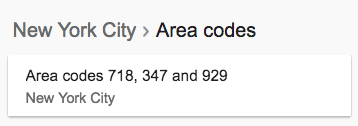
As a result of our work, it remains for us to pick up just three digits of the phone number - what’s the first three digits. Usually the list of such combinations is not particularly large and in some cases is even publicly available, especially with regard to the United States:

Finally, the attacker will have to manually send and check phone numbers from the resulting list on the Facebook login page until the full name of the victim is found or the desired email address is displayed, which confirms the number match:
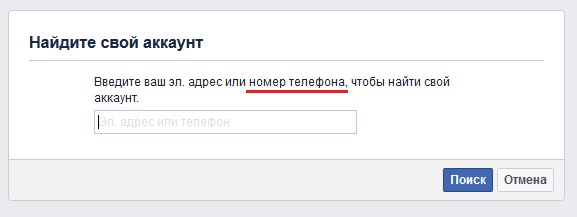
It should be noted that you can automate this part of the process using a Python script.
Thus, the attacker can find out the victim's personal phone number.
It is also possible to additionally check whether the received phone number belongs to the victim using other various methods using open sources.
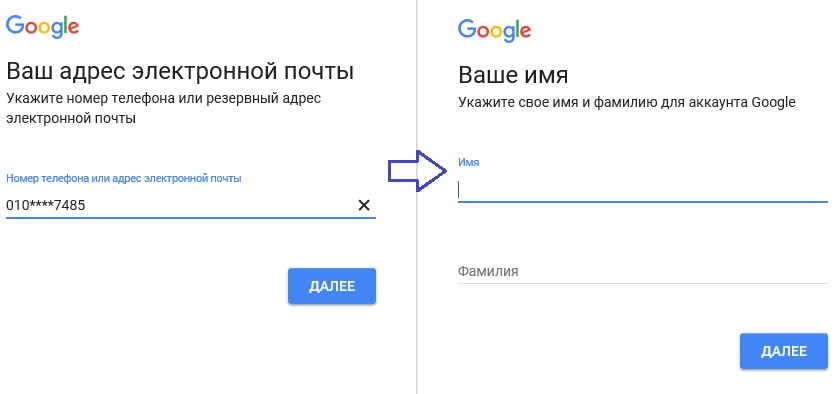
For example, if Facebook doesn’t have a specific setting, your full name and profile picture are displayed to anyone who sends your email address or phone number on the “Lost Password” page. Similarly, the function “Forgot your email address. Mail? ”from Google allows you to check the compliance of the name of the phone number:
findings
In this way,
- The attacker uses Facebook to determine the location of the victim, as well as the last two digits of the phone number
- Paypal is then used to identify additional digits of the phone number. Paypal also confirms the accuracy of Facebook data.
- The location code and the first digit of the number determine the region code - or variants of this code.
- The remaining missing digits are determined by a simple search, which can be abbreviated according to the rules for compiling the numbers of a particular operator. These numbers are substituted in the Facebook form “Lost Password” before the name of the victim or her known email address is displayed.
The above sites are selected only to demonstrate the ability to search and select a phone number. In fact, there are quite a lot of such sources of information, and not all of them limit the possibilities of automated search of captchas - and therefore scripts allow us to sort out and find a match in a relatively short time.
Protection against the above attack scheme is the use of different phone numbers when registering on different resources or limiting the possibility of using phone numbers to recover a password, gain access to a resource, etc.
PS If the material seemed interesting enough to someone to master the second part - about the risks of using virtual number services to receive SMS when registering on Internet resources, then welcome here .
Source: https://habr.com/ru/post/347302/
All Articles