Che Burashka and hacking systems selling tickets to Moscow electric trains

Around January 17, a group calling itself the Che Cherashka Research Group published a vulnerability study that allows hacking ticket sales for Moscow electric trains. The system developer is Microtech.
There is currently no rebuttal from Mikroteh.
The author has no relation to the group “Che Burahska” and is not responsible for the activities of this group. Below is the text freely distributed by this group on various resources on the Internet, and a description of the vulnerability (in the opinion of the group is incomplete), summarized and edited for readability. This text is offered to Habr's readers for review and discussion.
1. Introduction from the authors (this is the text that was distributed along with the description of the vulnerability)
The Che Burashka research team appeals to all interested parties and publishes a description of the vulnerabilities we found in the ticket sales system for Moscow electric trains.
')
We defend two independent security researchers (hereinafter referred to as Researcher 1 and Researcher 2) [the words from the sentence are deleted from the sentence at the request of one of them - details below the text]
Details of this story you can read the links below:
Pikabu
Tjournal
Lenta
We do not agree with how this story was presented in the press and at the trial. We believe that the main source of problems for Researcher 1 and Researcher 2 is the unwillingness of the developer of turnstile software and hardware to recognize and eliminate vulnerabilities in their developments.
Please read at the very bottom for more information on the case of Researcher 1 and Researcher 2 - approx. publication author
As we know, even before the establishment of the criminal case, Researcher 1 applied to Microtech with a proposal for cooperation. All over the world, it is accepted that if an independent specialist finds a vulnerability in the software and informs the developer about it, the developer at least fixes it. The most reputable companies pay money. But the letter from Researcher 1 was ignored by Mikrotech [the words from the sentence were deleted at the request of Researcher 2 - details below the text] . We suspect that this coincidence is not accidental.
We are not sure until the end whether the police acted on a tip from Mikrotech or found our colleagues in security research on their own, but we believe that the cause of their problems was precisely the position of the developer who ignores obvious problems with the security of their own systems.
The main part of the problem of software and equipment Microtech, identified by the Researcher 1 and, independently of him, by other specialists, has not been eliminated. Errors are still not fixed and ensure the vulnerability of the ticketing system for intruders. Anyone can print tickets and ride for free.
We believe that Microtech is the worst example of a monopolist who does not want to admit his mistakes and spreads unsafe software for users.
Unfortunately, the official authorities and journalists do not always delve into the subtleties of what is happening.
You can recall, as a negative example, the story of TroykaDumper.
Igor Shevtsov, who published the details of the hacking of the Moscow Troika card, in our opinion, acted as an ethical hacker. He, of course, had to contact the owners of the system first. But the owners themselves then acted constructively and eliminated the malfunction, turning to Igor for help. The version of the program published by him is still available on github, but is completely useless for the purpose of free travel.
Much worse than the reaction of representatives of Troika, was the reaction of journalists who declared Shevtsov a crook, as well as representatives of the prosecutor's office of some completely foreign, distant from Moscow city, who demanded to remove research information on the hacking technology from the Internet.
As a result, information about Shevtsov's research was removed from Habr, and his profile was blocked. The owners of the platform were reinsured; nobody demanded to block the profile from them, but they didn’t want the problems they had invented themselves with the authorities.
We have been thinking for a long time about how to correctly present the information we have found for public access. Each of us is a professional in his field. We successfully combine studies in one of the Moscow universities with full-fledged work and would not want to have trouble just because we reveal information about the negligence of the manufacturer of the equipment and software.
For this reason, we will not publish this information on Habré, although we originally prepared it for this site.
Moreover, unlike the situation with Troika, Mikrotekh is clearly not going to correct his mistakes on his own initiative.
We decided to post the text of the article, originally prepared for Habr in free access to other resources and distribute a link to it on social networks.
We urge Microtech to recognize vulnerabilities in their systems and take steps to correct them on their own.
While we publish an incomplete description of hacking equipment. But if in the near future, at least in two or three months, we do not see that the vulnerabilities have been fixed, we will fill in the gaps and publish the full information for everyone to know.
The technology of hacking suburban train tickets is much simpler than the problems that Shevtsov found on Troika cards. In order to print working tickets, a simple program under Windows or Linux is enough, a laser printer and scissors.
[Words removed from the sentence at the request of Researcher 2 - details below the text] Mikrotech does not wish to acknowledge the insecurity of his turnstiles and his software. And the losses will be incurred by railway companies that have become their customers.
You will not find any traces of the preceding Che Cherashka activities in the network.
We are not hackers, and this is a one-time nickname that we use only for one specific project.
2. Description of the vulnerability.
Investigation of the security of the turnstiles of the company Microtech
Prehistory
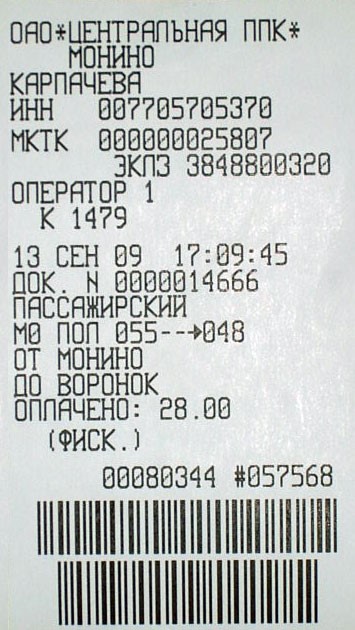
Microtech company produces a system that provides access to the platforms of suburban railways, as well as ticket distribution systems.
As it is written on the company's website - www.microteh.net, all this is called
Automated system of payment, control and accounting of travel in suburban trains ASOKUPE.
In the Moscow region, it fits in with the Troika city maps, which are used to travel in urban public transport. We pass through Microtech turnstiles every time we go to our home institution and back to Moscow.
Two years ago, we, three student friends, decided to investigate the question of how reliable the system is, limiting the passage of hares to suburban electric trains.
We wanted to be ethical hackers, we were not going to sell tickets, but would prefer to receive an award from companies for demonstrating vulnerabilities.
We decided that any legal methods of analyzing the attacked system are suitable for imitating the actions of intruders and should not be used for direct hacking and damaging effects on the equipment installed by railway workers Mikroteh. We do not want to break the law and did not do it.
Although during the reading of specialized forums we found evidence that unknown to us hackers gained access to the company's network, we did not investigate this question. However, we allowed ourselves easy forms of social engineering.
We went to specialized exhibitions and asked questions. It was very useful, as well as training materials presented to us by railway workers for employees.
We called the company itself and talked with their technical experts. It is useless in terms of technical details, but we unexpectedly learned a lot of interesting things about the relationships within this team.
We, once, talked on the phone with their superiors. Communication disappointed. We simply did not want to listen, although at that moment we did not even ask for money, but offered to do research for free.
The real sources of information were the turnstiles themselves. We do not really understand what kind of consumer audience those who sold them on avito counted on, but we bought used devices and used them for a while. They were sold along with some documentation transferred to us on a diskette. Documentation was as useful as the devices themselves. Then all three purchased turnstiles had to be taken to the garbage, as they occupied half of the room.
No less useful were our rather systematic studies of the tickets themselves, which are sold at suburban ticket offices.
During our life we bought, probably, hundreds of such tickets, but, basically, the same.
For research purposes, we had to buy more than 50 tickets for a particular system.
How the ticket distribution system works
Microtech supplies railway workers with cashier jobs and software for them.

Here is a picture from the manufacturer's website. On it - the system unit, monitor and peripheral equipment. As well as a special printer for printing tickets.
As they look at the thoughts of designers Microtech.
In fact, of course, it looks all in different places a little differently. We looked at different ticket offices and saw that the composition of the equipment supplied was changing in different directions of the railway. It must have been a different game, but the software is all the same.
Quote from the manufacturer's website: MKTF - Multifunctional cash terminal, a device made on the basis of a personal computer. Complies with the requirements of 54FZ. Designed for registration and verification of travel documents (with a bar code and on BSC). Can work in offline and online modes.
The word autonomous in the quoted text we have highlighted. It is important.
In the future we will find that this is one of the key points that provokes the vulnerability of the system to malicious intent.
In the meantime, we simply note that the entire system from Mikrotech is built on the fact that their devices are able to work offline. Apparently, for the 1990s, when, according to information from the site, this company was founded, and for earlier times, when it was a departmental design bureau, it was both rational and progressive.
But the question that someone could forge the shtrikody on a ticket in those years clearly was not. At least for the reason that there were no bar codes at that time and the validity of the tickets was checked by the eyes of the people-inspectors.
Railroad workers began to think about the complete blocking of access to railway platforms by turnstiles only in the 1990s, when the free-riders finally got them.
So here. In each specific ASOKUPE cash desk, the direction of the railway to which the cash desk and a unique cash number are indicated in the configurations are indicated in the configs.
Of course, there are additional settings, but, most importantly, each ticket office, without accessing a centralized server, is able to generate a valid ticket.
To be precise - a valid bar code on the ticket.
Information can be encoded in two ways.
Old - Interleaved 2 of 5
We give a description:
The Interleaved 2 of 5 linear code consists of a sequence of alternating black and white vertical stripes, starting and ending with black. In this code, there are two types of strips: Wide (logical "1") and narrow (logical "0"). Interleaved 2 of 5 assumes the presence of start and stop symbols. The start symbol is encoded "0000", the stop symbol is encoded "100". Between these two characters is useful information.
The code received its name, based on the fact that the information is encoded by the arrangement of two wide strips among the five. Proceeding from this, we find that with this block 10 different values can be encoded, i.e. all numbers are from 0 to 9. Interleaved (intermittent - English) it is because it is considered separately black and separately white stripes.
At odd positions (counting from left to right) the numbers are represented by strokes, and at even positions - by spaces (alternation). When encoding data with an odd number of characters ahead, "0" is written.
In Interleaved 2 of 5 barcode, it is recommended to use a check mark to increase read reliability. The control sign is located immediately after the information signs in front of the “Stop” sign. If adding a control character makes the number of characters in the data being encoded odd, a “0” is added ahead of the code line immediately after the “Start” sign.
And the new, two-dimensional Aztec code:

Tickets with him began to appear from the end of the 2015th year. It is not yet clear whether a full replacement is planned or whether it is just an experiment for compatibility with the mobile application from Microtech.
But this is a little better. Interleaved 2 out of 5, it seems, system developers have found at random, Aztec is supported by many railway companies around the world.
Be that as it may, the composition of the information encoded by both methods is the same.
What else is there?
There is, for example, such a device

Again, the picture and text from the Microtech site:
PKTF - Portable cash terminal, a device made on the basis of specialized microprocessor solutions. Complies with the requirements of 54FZ. Includes modules for printing, reading bar codes and BSK, has a compartment for setting the FN. Provides printing and verification of travel documents. It can work both autonomously and in data exchange mode with an external system.
The terminal is an independent development of Microtech, but assembled, of course, from third-party components. We bought, at different times, two pieces.
Such terminals are now armed, mainly, controllers who are ready (not) to kindly sell the ticket to a passenger, if he suddenly forgot to buy it or lost it.
Despite the fact that they were bought at different times and, apparently, were operated in different directions, they allow you to equally well check tickets purchased in any direction.
This gives us a complete understanding of the security boundaries that ASOKUPE provides. There is some kind of control information in bar codes, but it can be checked with a fairly simple device, the method of checking does not change for a long time, its variable part is vulnerable, and the algorithm for changing it is quite simple.
More details below.
How is the control of the passage on the platform
Control over the passage to the platform is quite banal.

Two readers are mounted in the turnstiles. One is a barcode ticket scanner, and the second is a contactless reader for any kind of contactless tickets, using the Mifare protocol. Scanners come from third-party manufacturers (different), and the microtech reader module seems to have developed independently.
The turnstile mechanics and readers are united with a mysterious abbreviation UCPD. It is also the control module of the turnstile and data entry devices.
The entire "intelligence" of the system is concentrated in the controller, which is part of the FAPD.
External control of them is carried out by connecting via RS-485 interface.
When a passenger brings a ticket to the scanner, checking a bar code is essentially reduced to two fairly simple actions:
- The FAPD verifies the validity of the data encoded in the barcode. The conformity of the data on the final and initial route zones to the point at which the turnstile is installed, the date of travel, some kind of control information is checked ... that's all.
- USPD checks the absence of a ticket in the stop list.
Here it must be said that the stop list is not loaded centrally, it is downloaded at the stations through the internal service. the network and then it is loaded into each group of turnstiles separately, through a hub to which the turnstiles are connected via RS-485 interface.
- , :
2222333390;20/10/2015;40
2118110622;20/10/2015;40
668690750;20/10/2015;40
84545402;20/10/2015;40
187342702;20/10/2015;40
187345542;20/10/2015;40
87534582;20/10/2015;40
2715435894;20/10/2015;40
354345614;20/10/2015;17
2710234378;20/10/2015;40
1311398318;20/10/2015;40
1242467662;20/10/2015;40
1236551358;20/10/2015;40
1576567678;20/10/2015;50– , – , – .
-, , , , . , , .
.
, . , . . 1 .
, -, .
, « » .
.
. , , .
:
1) ( , )
2) ( , )
– , , - . id, id , .
3) . , – . «».
4)
5) , (5 )
6) ID (4 ) ID , , , .
– . 10 4. 6 !
7)
8), 9) –
10)
, , .
, - , – , ?
, –
, . - – , , , . .
, , legacy .
, , .
, , , , . , , , .
. – , – 4 .
Z- – , .
Z- , , , .
– ?
, - , .
, , , , .
« » – 10-20 .
- , , - « » .
.
.
, 6 .
, , . , , – !
.
«- » . , .
«» , . .
, , , , .
, – - . , , - . , , - .
, – , , – .
.
, , - , .
, - . .
, , , , github - .
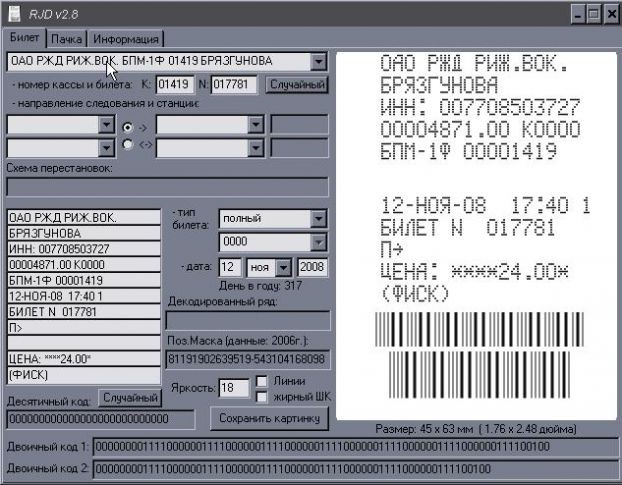
, .
, – , .
, , , .
, , . .
?
, , , .
, , .
.
Aztec , .
, , , , , .
.
, , ¾ — .
. , Android 7.
– , .
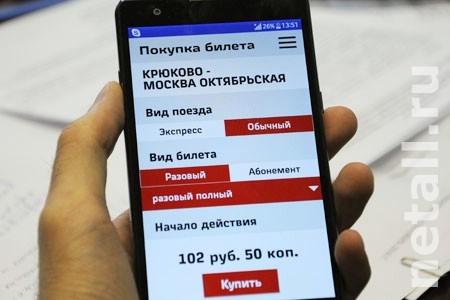
.
, ? Java.
iPhone , , . , , - iOS , , , .
, . . , .
, , , , - , , .
, – . , . .
, , , .
, , .
.
, :
- , , - . C# Windows, Windows 7, Linux.
- Java- Android 5,6,7. Aztec, , . - , .
, , NFC, , , , .
, , , .
, - .
, - ?
, , . .
P.S.
.
.
.
, , , . , .
.
.
.
, . .
.
, , . .
, , , .
, .
:
* Bom
* Gerda
* PHuntik
3. ,
.
, .
, , , — ! — , , — ! , …
, , «-» , ( ) . , , ( 20 ) £4.30, — £4.50 £6.50 — .
, :
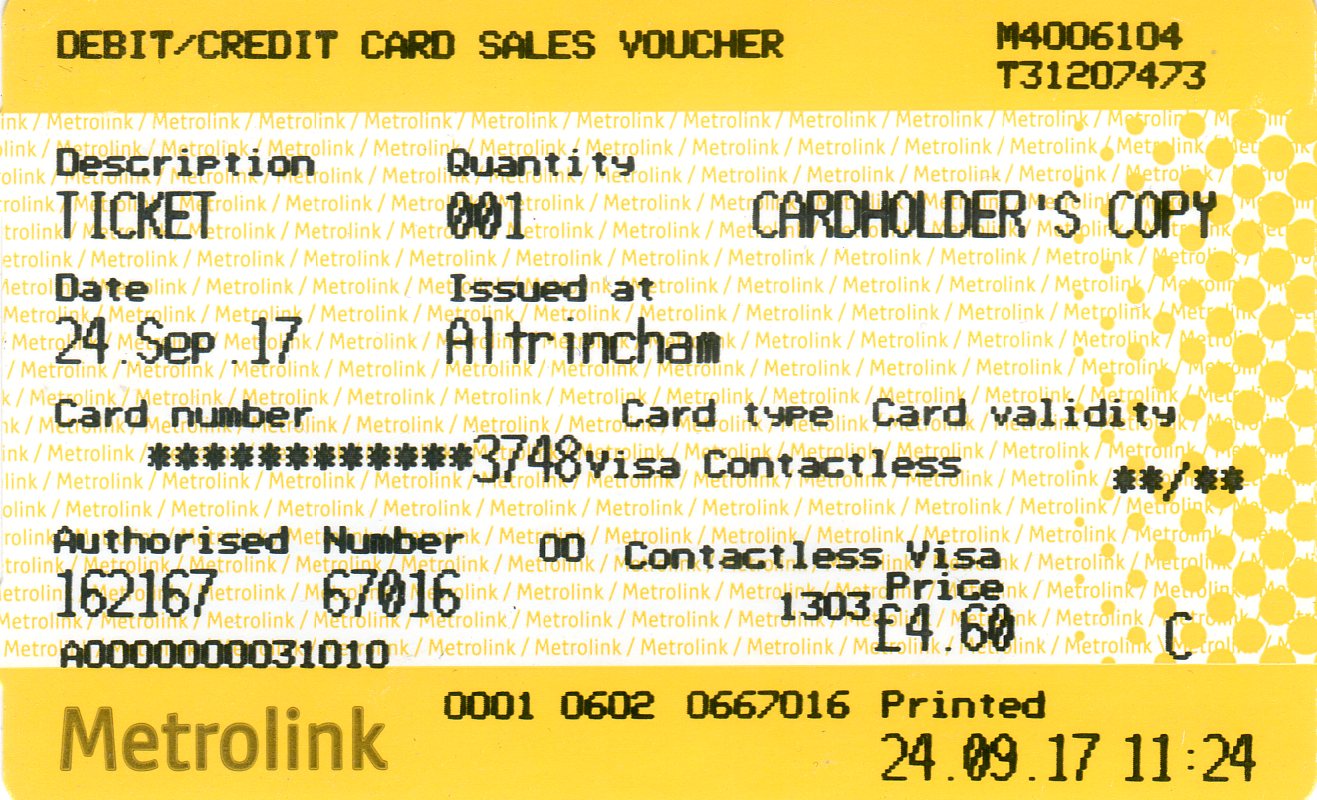
, ( !), .
-.
, — . , ! — , . .
: — , , , , « » .
. , , , , , . , — , , ? !
, — .
.
, « , » .., -, . « » — . , — — , . .
, - , - , , , — , . : « — », . , , , . .
P.S.
, , 27 , (, 2) :
!
habrahabr.ru/post/347262
. , Che Burashka .
%_____%
. .
.
..2 4 .152 , .
2
, « » , . «» .
Source: https://habr.com/ru/post/347262/
All Articles