Understanding Meltdown and Specter: What you need to know about new vulnerabilities found in almost all CPUs
It seems that processor manufacturers have been hit hard: within a few days, all the news sites started talking about two hardware vulnerabilities called Meltdown and Specter right away. I must say that this is a very hot week, which has not been seen in the technology industry for a long time. But I will not hurry, so let's deal with everything in order.

Security researchers working in the Google Project Zero group, along with other research groups and academic institutions, found a number of security threats associated with speculative execution. Speculative execution is one of the cornerstones of high performance modern processors and, in essence, all processors have higher performance than the built-in microcontroller. As a result, virtually every modern high-performance processor on the market, released over the past few decades, is vulnerable to one or more exploits.
At the moment, the main danger is an exploit called Meltdown. It primarily affects Intel processors, although there is evidence of the vulnerability of several ARM processors. With the help of Meltdown, malicious code can abuse the implementations of the speculative execution of Intel and ARM, which will lead to the leakage of information from other processes - directly from the omniscient core of the operating system. As a result, Meltdown can be easily used to track other processes and steal information that needs to be isolated by the kernel, other programs, or other virtual machines.
')
Meanwhile, the second type of exploit is called Specter, and the number of processors at risk of exploitation is even wider. In fact, every high-performance processor ever created - Intel, AMD, ARM and POWER - is considered vulnerable. Like Meltdown, Specter’s attack abuses speculative execution to get information that needs to be isolated. However, Specter’s peculiarity is that it is a more complex and much more insidious attack; while Meltdown is based on the abuse of a specific implementation of speculative execution, Specter can be viewed as a (previously unknown) fundamental vulnerability of speculative execution that can now be used for attacks. Specter requires more preparation efforts to force the target application to leak information, but the fundamental nature of risk means that Specter’s vulnerability is much harder to fix, and it has not yet been fully investigated.

Meltdown breaks down the most fundamental isolation between applications and the operating system. This attack allows the program to get direct access to the memory, and therefore to the secret data of other programs and the operating system.
If the processor of your computer is vulnerable, and you use an unpatched operating system, it is not safe to work with secret information. High chance of information leakage. This applies to both personal computers and cloud infrastructure. Fortunately, software patches have been released to protect against Meltdown.
Specter breaks the isolation between various applications. This allows an attacker to obtain data even from programs that comply with all safety rules and operate without errors. In fact, the security checks of the programs mentioned increase the attack surface and may make applications more susceptible to Specter. Specter's exploit is more difficult to apply than Meltdown, however, it is much more difficult to neutralize the threat of such an attack. Nevertheless, it is possible to prevent some of the already known exploit options by installing the latest software patches.
An unplanned stream of news about Meltdown and Specter came crashing into the information space, and as a result, researchers, hardware and software suppliers, and the general public tried to understand what happened and what to do about it. Now we know that these vulnerabilities were discovered last summer, since then the vector of actions of security vendors and researchers has been focused on understanding the consequences of exploits and developing the necessary fixes and recommendations. It was decided that information about Meltdown and Specter should not be published until Tuesday, January 9 - the release date of the first patch of this year.
Instead, the following happened: since the fixes for the exploits were fixed in the Linux kernel repository, users had a suspicion that something serious had happened. In connection with the rapid development of all sorts of speculations on this ground, the suppliers of software and hardware postponed the date of notification to the public and the release of patches on January 3. The result of a premature publication, as one might expect, was somewhat random: I carefully read various sources and see that even now not all published tips (or, often, not a complete list of recommendations).
As a result, I am still collecting information, and probably by the time I finish writing, something in this article will be outdated or incorrect. But at the moment this is all that we know from the moment of the news release.
It is said that, despite a lot of glaring (and sometimes fatal) inaccuracies, the “Hitchhiker's Guide to the Galaxy” guide has surpassed the “Galactic Encyclopedia” in popularity because it is a bit cheaper and because it has the words “DO NOT PANIC” written in big funny letters on the cover.
Before diving into some of the deep technical aspects of Meltdown and Specter, I think it is better to start with a review of the situation at a higher level. This includes the risks associated with new exploits, how to deal with them, and what individual users should do (if possible) in the face of danger.
For a start, the good news is: if you are not a cloud service provider, the immediate risk of these attacks is very low. The bad news is that since these exploits are based on hardware vulnerabilities, it will take some time to fix it. And there are so many devices that run many different operating systems, and all this needs to be fixed.
These are local attacks : both Meltdown and Specter are local attacks that require the execution of malicious code on the target machine. This means that these attacks are not (directly) an attack of remote code execution - as was Nimda or Code Red - which means that systems cannot be attacked just by connecting to the network. It is clear that they are closer to privilege escalation attacks, a class of attacks that help penetrate deeper into the system (to which you already have access). However, researchers have shown that they can perform Specter-based attacks using JavaScript, so a web browser can launch a malicious JavaScript file, and thus allow an attack.
This is a read-only attack (access to information). Although we mentioned that the attacks could not be carried out remotely, if Meltdown and Specter could be launched on the local system, the nature of the exploit is that it is a read-only attack. That is, all they can do is read the information from the system. They cannot directly enforce code execution in the OS kernel, other virtual machines or other programs. And yet, information disclosure attacks can be very destructive depending on what information is obtained. There is always the risk of using this information to conduct a successful attack already by executing code, which means that the threat does exist. But the real risk lies precisely in the use of these vulnerabilities by attackers to steal information, and not to control the system.
THIS:
- the way in which an attacker can observe the contents of privileged memory, bypassing existing privilege levels
- malicious code that exploits vulnerabilities and runs locally, is able to obtain critical information such as passwords and encryption keys.
IS NOT:
- service shutdown attack
- network attack
- method of injection of modified code or substitution of memory contents.
This is mainly a threat to distributed hosting environments . Given the above, these attacks are most dangerous for shared hosting environments, where several users can execute code in one system. As a result, cloud service providers, such as Amazon and Microsoft, are already taking steps to protect their services from attacks. Separate systems and devices, in comparison with cloud, have much less practical risk. The attacker still needs to run the malicious code on a separate system before he can launch the attack; but if the attacker can still do it, then the specified separate system will be in a very unenviable position.
You can protect yourself from Meltdown and Specter : since the root of the problem Meltdown and Specter is at the hardware level, ideally, this equipment would be worth replacing. However, the replacement of all systems released in 20 years does not look like an attractive idea. Like other processor errors, it can be mitigated by a combination of processor microcode and operating system updates. Vendors, such as Microsoft, Apple and Linux distributions, are already in the process of deploying these fixes, including we observed an ultra-rare unplanned update from Microsoft on Wednesday evening.
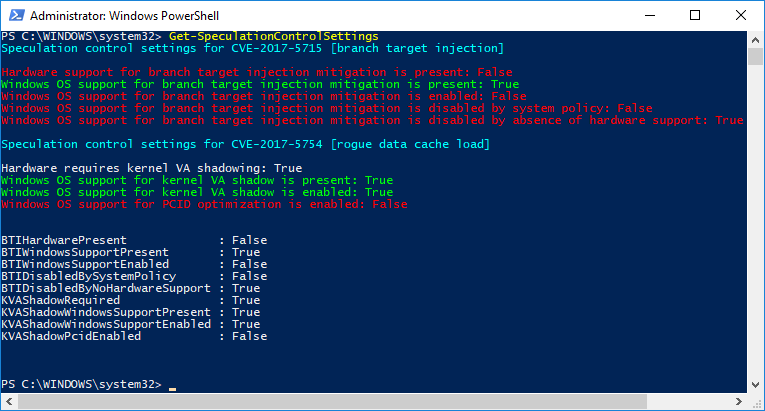
... but it will take some time : however, since the information about the exploit was released earlier than planned, not all security measures will be ready. A full set of measures requires both software updates and microcodes. As noted by Intel, mitigation efforts will require several days and weeks.
Protection from Meltdown will have an impact on performance : in a nutshell, measures to protect from Meltdown include a better separation of user-space programs from the OS kernel. As a result, contact switching between user space and the kernel occurs with serious delays. However, the actual impact of this process on performance will depend on the workload and processor architecture.
This is a bad week for Intel : Intel is the dominant CPU supplier for cloud service providers, who, in turn, are most at risk from Meltdown and Specter. Combined with the fact that Intel is much more susceptible to the more urgent threat of Meltdown than any other vendor, means that customers of high-paying Intel servers are primarily at risk of such attacks. And this, in turn, reflects badly on Intel’s reputation.
Regarding processors vulnerable to attack: Intel has confirmed that this is all Core-based architectures, including the first generation (Nehalem). It should be noted that earlier processors cannot be excluded.
For AMD, this week is better (but also not a gift) : AMD, on the contrary, has good news.
In short, their processors are not vulnerable to Meltdown attacks - and this is the only supplier among the Big 3 that has been shunned by disruptive news. Considering that Meltdown is a more urgent risk, this means that AMD and its users incur risks that are incomparably smaller than Intel users. However, AMD processors are still vulnerable to Specter attacks, and in the long run there are still too many unknown moments: how dangerous Specter is, and how much protection is possible against him.
When full updates for protection will be available for each platform : as noted above, deploying updates to protect against exploits will take several days or weeks. From a PC point of view, a Microsoft update is just one piece of the puzzle, although perhaps the most important because it can reduce the risk of Meltdown without updating the microcode. However, we are still awaiting microcode updates in order to increase protection against Specter on Intel processors (this applies equally to AMD processors).
On the other hand, Google announced that they have already released Android updates with ARM-recommended protective measures for supported Nexus and Pixel devices, but these updates do not contain all the necessary patches for the Linux kernel.
We take a set of measures to provide the most secure platforms. This includes a combination of patches for operating systems and firmware developed in collaboration with industry partners, operating system suppliers and OEM suppliers.
It is expected that the full range of protective measures will be available to users from a few days to a few weeks.
It is unclear how such safety measures will affect productivity : returning to the question of the complex of measures to protect from Meltdown, it is unclear what the impact on performance will be. Theoretically, individual operations and workloads can be slowed down by 30%, but to a large extent this will depend on how often the task switches to the core. In practice, it is still expected that the average effect in reality is less “pernicious”, especially for desktop users. But server users (with regard to performance) are less fortunate.
Meanwhile, the impact on the performance of Specter protection is virtually unknown, in part because the search for Specter protection continues. Based on what the equipment suppliers have published, the impact should be minimal.
For our part, we are still waiting for the microcode update, and even after that we will have to try out all possible consequences by trial and error. This is definitely what we should go into in the AnandTech style in the future, as soon as all necessary updates are received.
Finally, for its part, the Microsoft Azure group published its own data in customer recommendations, noting that the impact on performance is very small.
Most Azure users will not see a noticeable impact on performance after the upgrade. We worked on optimizing the data transfer paths between the processor and the disk and found no particular effect on performance after the fix was applied. Although some customers may still experience some drop in network performance.
The extent of Specter’s vulnerability is still unclear : while Meltdown is a more pressing threat, it’s already clear how it works and what needs to be done to protect it. Specter, however, is simply a variable with an unknown value. There is a lot of evidence of such attacks, but, in a broader sense, Specter attacks are a new class of attacks, not quite similar to what we have seen before. As a result, no one is sure that he fully understands the possible consequences of using an exploit. There is a risk that Specter attacks can be used much more widely than we imagine.
It is also unclear how much you can defend against Specter. The lack of understanding of Specter’s entire range of applications is not completely clear how to protect against it. The researchers working on the vulnerability are not at all sure that it will be enough to completely solve the problem of software or microcode updates. Rather, at the moment these measures should be considered as temporary solutions. Specter Specter attacks that are already known can be prevented, but defense can be useless against other Specter attacks. This is an area requiring much more research.
Finally, the question arises what measures should be taken by the owners of computers and gadgets in the face of the threat of an attack by Meltdown and Specter. The fundamental vulnerability that permits speculative execution attacks is in the hardware itself, so the problem cannot really be solved without replacing the devices. The only thing that can be done right now is to reduce the threat with the help of software and microcode patches that are trying to at least somehow close the security hole.
Cumulative update of Windows 10 Version 1703 for x64 systems (KB4056891)
A security issue has been identified in Microsoft products that may affect your system. You can help us protect your system by installing an update from Microsoft. To view the full list of fixes, refer to the relevant chapter in the Microsoft Knowledge Base. After installing the update, you will need to restart.
The answer to the question “what to do to the user” seems to be simple, but not very useful: there is little that can be done in principle. Software and microcode updates to protect against these exploits will be distributed in the usual way, so updating your systems and mobile devices to the latest OS version is the most important step you can take. As mentioned earlier, all vendors have already released or are in the process of deploying the necessary software updates. But if a specially developed narrowly targeted tool is used for the attack, the user will simply have nothing to defend. The task of manufacturers as soon as possible to find a solution to this problem.
And finally
Be sure to keep yourself up to date with events, read more information about these attacks. In particular, I want to continue exploring the importance of speculative execution and why attacking it can have significant implications for the design of the CPU. Speculative execution is a rather important function to improve performance on modern processors, but, as these attacks showed, even (seemingly) perfectly implemented, it has some unresolved security problems, which is unacceptable in the current computing era.
Meltdown and Specter should be considered more deeply, and although both of them are attacks on speculative execution, they represent very different types of attacks. Now Meltdown is the biggest problem because of its relative ease of use. But, as noted by the authors of the Specter publication, Specter is a more fundamental vulnerability that will stay with us for a long time. We have yet to see what this means for system security. And from the point of view of computer science, I expect that these discoveries will have a great impact on the entire development of future processors.
As advertising. Hurry to take advantage of the interesting offer in the new year and get a 25% discount on the first payment when ordering for 3 or 6 months!
These are not just virtual servers! This is a VPS (KVM) with dedicated drives, which can be no worse than dedicated servers, and in most cases - better! We made VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB available at a uniquely low price - from $ 29 / month , options are available with RAID1 and RAID10) , do not miss the chance to place an order for a new type of virtual server, where all resources belong to you, as on a dedicated one, and the price is much lower, with a much more productive hardware!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny? Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!

Security researchers working in the Google Project Zero group, along with other research groups and academic institutions, found a number of security threats associated with speculative execution. Speculative execution is one of the cornerstones of high performance modern processors and, in essence, all processors have higher performance than the built-in microcontroller. As a result, virtually every modern high-performance processor on the market, released over the past few decades, is vulnerable to one or more exploits.
At the moment, the main danger is an exploit called Meltdown. It primarily affects Intel processors, although there is evidence of the vulnerability of several ARM processors. With the help of Meltdown, malicious code can abuse the implementations of the speculative execution of Intel and ARM, which will lead to the leakage of information from other processes - directly from the omniscient core of the operating system. As a result, Meltdown can be easily used to track other processes and steal information that needs to be isolated by the kernel, other programs, or other virtual machines.
')
Meanwhile, the second type of exploit is called Specter, and the number of processors at risk of exploitation is even wider. In fact, every high-performance processor ever created - Intel, AMD, ARM and POWER - is considered vulnerable. Like Meltdown, Specter’s attack abuses speculative execution to get information that needs to be isolated. However, Specter’s peculiarity is that it is a more complex and much more insidious attack; while Meltdown is based on the abuse of a specific implementation of speculative execution, Specter can be viewed as a (previously unknown) fundamental vulnerability of speculative execution that can now be used for attacks. Specter requires more preparation efforts to force the target application to leak information, but the fundamental nature of risk means that Specter’s vulnerability is much harder to fix, and it has not yet been fully investigated.

Meltdown breaks down the most fundamental isolation between applications and the operating system. This attack allows the program to get direct access to the memory, and therefore to the secret data of other programs and the operating system.
If the processor of your computer is vulnerable, and you use an unpatched operating system, it is not safe to work with secret information. High chance of information leakage. This applies to both personal computers and cloud infrastructure. Fortunately, software patches have been released to protect against Meltdown.
Specter breaks the isolation between various applications. This allows an attacker to obtain data even from programs that comply with all safety rules and operate without errors. In fact, the security checks of the programs mentioned increase the attack surface and may make applications more susceptible to Specter. Specter's exploit is more difficult to apply than Meltdown, however, it is much more difficult to neutralize the threat of such an attack. Nevertheless, it is possible to prevent some of the already known exploit options by installing the latest software patches.
Hasty release did not reveal the whole situation.
An unplanned stream of news about Meltdown and Specter came crashing into the information space, and as a result, researchers, hardware and software suppliers, and the general public tried to understand what happened and what to do about it. Now we know that these vulnerabilities were discovered last summer, since then the vector of actions of security vendors and researchers has been focused on understanding the consequences of exploits and developing the necessary fixes and recommendations. It was decided that information about Meltdown and Specter should not be published until Tuesday, January 9 - the release date of the first patch of this year.
Instead, the following happened: since the fixes for the exploits were fixed in the Linux kernel repository, users had a suspicion that something serious had happened. In connection with the rapid development of all sorts of speculations on this ground, the suppliers of software and hardware postponed the date of notification to the public and the release of patches on January 3. The result of a premature publication, as one might expect, was somewhat random: I carefully read various sources and see that even now not all published tips (or, often, not a complete list of recommendations).
As a result, I am still collecting information, and probably by the time I finish writing, something in this article will be outdated or incorrect. But at the moment this is all that we know from the moment of the news release.
DO NOT PANIC
It is said that, despite a lot of glaring (and sometimes fatal) inaccuracies, the “Hitchhiker's Guide to the Galaxy” guide has surpassed the “Galactic Encyclopedia” in popularity because it is a bit cheaper and because it has the words “DO NOT PANIC” written in big funny letters on the cover.
Before diving into some of the deep technical aspects of Meltdown and Specter, I think it is better to start with a review of the situation at a higher level. This includes the risks associated with new exploits, how to deal with them, and what individual users should do (if possible) in the face of danger.
For a start, the good news is: if you are not a cloud service provider, the immediate risk of these attacks is very low. The bad news is that since these exploits are based on hardware vulnerabilities, it will take some time to fix it. And there are so many devices that run many different operating systems, and all this needs to be fixed.
What we know:
These are local attacks : both Meltdown and Specter are local attacks that require the execution of malicious code on the target machine. This means that these attacks are not (directly) an attack of remote code execution - as was Nimda or Code Red - which means that systems cannot be attacked just by connecting to the network. It is clear that they are closer to privilege escalation attacks, a class of attacks that help penetrate deeper into the system (to which you already have access). However, researchers have shown that they can perform Specter-based attacks using JavaScript, so a web browser can launch a malicious JavaScript file, and thus allow an attack.
This is a read-only attack (access to information). Although we mentioned that the attacks could not be carried out remotely, if Meltdown and Specter could be launched on the local system, the nature of the exploit is that it is a read-only attack. That is, all they can do is read the information from the system. They cannot directly enforce code execution in the OS kernel, other virtual machines or other programs. And yet, information disclosure attacks can be very destructive depending on what information is obtained. There is always the risk of using this information to conduct a successful attack already by executing code, which means that the threat does exist. But the real risk lies precisely in the use of these vulnerabilities by attackers to steal information, and not to control the system.
What is / is not detected vulnerability:
THIS:
- the way in which an attacker can observe the contents of privileged memory, bypassing existing privilege levels
- malicious code that exploits vulnerabilities and runs locally, is able to obtain critical information such as passwords and encryption keys.
IS NOT:
- service shutdown attack
- network attack
- method of injection of modified code or substitution of memory contents.
This is mainly a threat to distributed hosting environments . Given the above, these attacks are most dangerous for shared hosting environments, where several users can execute code in one system. As a result, cloud service providers, such as Amazon and Microsoft, are already taking steps to protect their services from attacks. Separate systems and devices, in comparison with cloud, have much less practical risk. The attacker still needs to run the malicious code on a separate system before he can launch the attack; but if the attacker can still do it, then the specified separate system will be in a very unenviable position.
You can protect yourself from Meltdown and Specter : since the root of the problem Meltdown and Specter is at the hardware level, ideally, this equipment would be worth replacing. However, the replacement of all systems released in 20 years does not look like an attractive idea. Like other processor errors, it can be mitigated by a combination of processor microcode and operating system updates. Vendors, such as Microsoft, Apple and Linux distributions, are already in the process of deploying these fixes, including we observed an ultra-rare unplanned update from Microsoft on Wednesday evening.

... but it will take some time : however, since the information about the exploit was released earlier than planned, not all security measures will be ready. A full set of measures requires both software updates and microcodes. As noted by Intel, mitigation efforts will require several days and weeks.
Protection from Meltdown will have an impact on performance : in a nutshell, measures to protect from Meltdown include a better separation of user-space programs from the OS kernel. As a result, contact switching between user space and the kernel occurs with serious delays. However, the actual impact of this process on performance will depend on the workload and processor architecture.
This is a bad week for Intel : Intel is the dominant CPU supplier for cloud service providers, who, in turn, are most at risk from Meltdown and Specter. Combined with the fact that Intel is much more susceptible to the more urgent threat of Meltdown than any other vendor, means that customers of high-paying Intel servers are primarily at risk of such attacks. And this, in turn, reflects badly on Intel’s reputation.
Regarding processors vulnerable to attack: Intel has confirmed that this is all Core-based architectures, including the first generation (Nehalem). It should be noted that earlier processors cannot be excluded.
For AMD, this week is better (but also not a gift) : AMD, on the contrary, has good news.
In short, their processors are not vulnerable to Meltdown attacks - and this is the only supplier among the Big 3 that has been shunned by disruptive news. Considering that Meltdown is a more urgent risk, this means that AMD and its users incur risks that are incomparably smaller than Intel users. However, AMD processors are still vulnerable to Specter attacks, and in the long run there are still too many unknown moments: how dangerous Specter is, and how much protection is possible against him.
And what is unknown:
When full updates for protection will be available for each platform : as noted above, deploying updates to protect against exploits will take several days or weeks. From a PC point of view, a Microsoft update is just one piece of the puzzle, although perhaps the most important because it can reduce the risk of Meltdown without updating the microcode. However, we are still awaiting microcode updates in order to increase protection against Specter on Intel processors (this applies equally to AMD processors).
On the other hand, Google announced that they have already released Android updates with ARM-recommended protective measures for supported Nexus and Pixel devices, but these updates do not contain all the necessary patches for the Linux kernel.
Our security measures:
We take a set of measures to provide the most secure platforms. This includes a combination of patches for operating systems and firmware developed in collaboration with industry partners, operating system suppliers and OEM suppliers.
It is expected that the full range of protective measures will be available to users from a few days to a few weeks.
It is unclear how such safety measures will affect productivity : returning to the question of the complex of measures to protect from Meltdown, it is unclear what the impact on performance will be. Theoretically, individual operations and workloads can be slowed down by 30%, but to a large extent this will depend on how often the task switches to the core. In practice, it is still expected that the average effect in reality is less “pernicious”, especially for desktop users. But server users (with regard to performance) are less fortunate.
Meanwhile, the impact on the performance of Specter protection is virtually unknown, in part because the search for Specter protection continues. Based on what the equipment suppliers have published, the impact should be minimal.
For our part, we are still waiting for the microcode update, and even after that we will have to try out all possible consequences by trial and error. This is definitely what we should go into in the AnandTech style in the future, as soon as all necessary updates are received.
Finally, for its part, the Microsoft Azure group published its own data in customer recommendations, noting that the impact on performance is very small.
Most Azure users will not see a noticeable impact on performance after the upgrade. We worked on optimizing the data transfer paths between the processor and the disk and found no particular effect on performance after the fix was applied. Although some customers may still experience some drop in network performance.
The extent of Specter’s vulnerability is still unclear : while Meltdown is a more pressing threat, it’s already clear how it works and what needs to be done to protect it. Specter, however, is simply a variable with an unknown value. There is a lot of evidence of such attacks, but, in a broader sense, Specter attacks are a new class of attacks, not quite similar to what we have seen before. As a result, no one is sure that he fully understands the possible consequences of using an exploit. There is a risk that Specter attacks can be used much more widely than we imagine.
It is also unclear how much you can defend against Specter. The lack of understanding of Specter’s entire range of applications is not completely clear how to protect against it. The researchers working on the vulnerability are not at all sure that it will be enough to completely solve the problem of software or microcode updates. Rather, at the moment these measures should be considered as temporary solutions. Specter Specter attacks that are already known can be prevented, but defense can be useless against other Specter attacks. This is an area requiring much more research.
What can users do now?
Finally, the question arises what measures should be taken by the owners of computers and gadgets in the face of the threat of an attack by Meltdown and Specter. The fundamental vulnerability that permits speculative execution attacks is in the hardware itself, so the problem cannot really be solved without replacing the devices. The only thing that can be done right now is to reduce the threat with the help of software and microcode patches that are trying to at least somehow close the security hole.

Cumulative update of Windows 10 Version 1703 for x64 systems (KB4056891)
A security issue has been identified in Microsoft products that may affect your system. You can help us protect your system by installing an update from Microsoft. To view the full list of fixes, refer to the relevant chapter in the Microsoft Knowledge Base. After installing the update, you will need to restart.
The answer to the question “what to do to the user” seems to be simple, but not very useful: there is little that can be done in principle. Software and microcode updates to protect against these exploits will be distributed in the usual way, so updating your systems and mobile devices to the latest OS version is the most important step you can take. As mentioned earlier, all vendors have already released or are in the process of deploying the necessary software updates. But if a specially developed narrowly targeted tool is used for the attack, the user will simply have nothing to defend. The task of manufacturers as soon as possible to find a solution to this problem.
And finally
Be sure to keep yourself up to date with events, read more information about these attacks. In particular, I want to continue exploring the importance of speculative execution and why attacking it can have significant implications for the design of the CPU. Speculative execution is a rather important function to improve performance on modern processors, but, as these attacks showed, even (seemingly) perfectly implemented, it has some unresolved security problems, which is unacceptable in the current computing era.
Meltdown and Specter should be considered more deeply, and although both of them are attacks on speculative execution, they represent very different types of attacks. Now Meltdown is the biggest problem because of its relative ease of use. But, as noted by the authors of the Specter publication, Specter is a more fundamental vulnerability that will stay with us for a long time. We have yet to see what this means for system security. And from the point of view of computer science, I expect that these discoveries will have a great impact on the entire development of future processors.
As advertising. Hurry to take advantage of the interesting offer in the new year and get a 25% discount on the first payment when ordering for 3 or 6 months!
These are not just virtual servers! This is a VPS (KVM) with dedicated drives, which can be no worse than dedicated servers, and in most cases - better! We made VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB available at a uniquely low price - from $ 29 / month , options are available with RAID1 and RAID10) , do not miss the chance to place an order for a new type of virtual server, where all resources belong to you, as on a dedicated one, and the price is much lower, with a much more productive hardware!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny? Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!
Source: https://habr.com/ru/post/347254/
All Articles