Information security models in the work of Windows VPS
We publish a series of articles on information security of client equipment and rental VPS Windows servers. This is the third article on the topic "basics of information security." The issues described earlier:
An important issue is the consideration of various models of information security that can be used in the construction of information security systems. There are several models, each of which allows you to answer the questions posed to her.

There are three main models of information security, this is a conceptual model, a mathematical model and a functional model of information security.
')
What is the difference between them, what questions they answer and what tasks allow us to solve the basic models of information security, we consider below.
The conceptual model answers general questions and reflects schematically the general structure of the information security model, on which other models and information security concepts are built like on a rod.
To build a conceptual model of information security, no matter how simple or complex an information system is, you need at least to answer three questions: what to protect, from whom to protect and how to protect? This is a mandatory minimum, which may be sufficient for small information systems. However, taking into account the possible consequences, it is better to build a complete conceptual model of information security, in which you need to define:
The following schematically shows the most complete conceptual model of information security, which is common to all information systems.

Figure 1. A conceptual model of information security
Building a conceptual model of information security of a virtual server can be divided into several different levels. In most cases, two levels are enough - the upper, organizational and managerial, which covers the entire organization and corporate information system, and the lower or service level, which relates to individual subsystems of the information system itself and various services.
The concept or top-level program is headed by the person directly responsible for the organization’s information security. In small organizations, as a rule, the head of the organization himself, in larger ones, these duties are performed either by the head of the IT department or directly by the head of the information security department, if such a department is separated into a separate structure.
Within the framework of the top-level program strategic security decisions are made, this program should contain the following main objectives:
The main goal or concept of a lower level program is to provide reliable and economically viable protection of information subsystems, specific services or groups of services. At this level, decisions are made on the following issues: what mechanisms, means and methods of protection to use, procure and install technical means, perform day-to-day administration, monitor the information security system as a whole and monitor the condition of weak points, conduct initial training of personnel, etc.
Usually, for the program of the lower level are responsible responsible heads of departments for ensuring information security, system administrators and administrators and managers of services. The most important action at this level is to assess the criticality of both the service itself and the information that will be processed with its help.
For this level it is necessary to formulate answers to the following questions:
A few very important points to consider are:
Once the conceptual model of information security has been built, you can begin to build a mathematical and functional model of information security.
The mathematical and functional model is directly related to each other. A mathematical model is a formalized description of scenarios in the form of logical algorithms represented by a sequence of actions of violators and retaliatory measures. The calculated quantitative values of the model parameters characterize the functional dependencies that describe the processes of interaction of offenders with the protection system and the possible results of actions. It is this type of model that is most often used for quantitative assessments of the vulnerability of an object, building a protection algorithm for assessing risks and the effectiveness of measures taken.
When building these models it is necessary to rely on the following key circumstances:
In practice, in conditions of multiple risks to security risks, it is obviously not possible to make such a numerical assessment without using mathematical modeling methods.
For example, consider the mathematical model of an economically viable system for minimizing information security risks.
Based on an expert assessment of the likelihood of a threat to information security, the significance of each threat is calculated, and the level of costs in terms of restoring the system is estimated. Next, the total risk of system failure is calculated as the sum of risks for each of the areas.
The result of solving the described problem will be the distribution of the financial resource in the selected areas of the organization, minimizing the risks of system failure according to the criterion of information security.
Let the technical or socio-economic system specify (find) the dependences of the risks Ri of system performance failure on expenses Xi to avoid them (exclusion, decrease) in the i-th direction of information security (hardware, software failure, system performance failure due to insufficient qualifications of employees, managers, etc.)
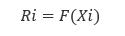
i = 1 ... n, where n is the number of specified directions.
Thus, while minimizing information security risks, we will use such an indicator as the level of costs (in material or value terms) for restoring the system to work in the event of its failure in one or several areas.
We further define the following values:
1) The total risk of system failure
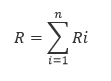
2) Z - the maximum amount of costs to reduce (eliminate) the allocated risks
3) ZMAXi - the maximum amount of expenses for the implementation of the i-th direction
4) ZMINi - the minimum amount of expenses for the implementation of the i-th direction,
Further, we can formulate the following problem of mathematical programming, in which each of the risks must be minimized, the total amount of costs to avoid them should be less than or equal to the maximum amount of costs to reduce (eliminate) the identified risks, where the costs of avoiding threats in each of directions should be greater than the minimum amount pledged for this direction, but it should not exceed the maximum amount for the same direction.

The constructed system is economically justified in the event that the sum of all the costs of avoiding, reducing or eliminating the risks compiled does not exceed or is equal to the total maximum amount of costs allocated for reducing (eliminating) the total risks.
This is just one of the examples of using mathematical modeling in building the information security system of your virtual server . Mathematical modeling can also be used to construct a mathematical model of a potential intruder, in which it is possible to determine the coefficient or probability to realize the threat of an attack by a potential intruder. Or, the problem of reserving system elements can be considered, solved to protect against breach of confidentiality of information processed in the information system.
Depending on the goals and the problem being solved, many mathematical models of a part of the information security system can be built and applied, which will help to evaluate its effectiveness even at the design stage of the information security system.
The last not unimportant question when building any models or systems is the life cycle of the model or system.
Unfortunately, it is not enough just to build an information security system using different models, but it is also necessary to observe the life cycle of this system. In which, regardless of the size of the organization and the specifics of its information system, work to ensure information security, in one form or another, should contain the following steps or steps presented in Figure 2.
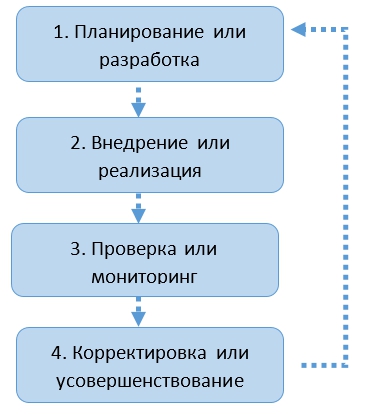
Figure 2. The life cycle of an information security system
It is important not to miss any significant aspects. This will guarantee some minimum (basic) level of information security, mandatory for any information system.
An important issue is the consideration of various models of information security that can be used in the construction of information security systems. There are several models, each of which allows you to answer the questions posed to her.

There are three main models of information security, this is a conceptual model, a mathematical model and a functional model of information security.
')
What is the difference between them, what questions they answer and what tasks allow us to solve the basic models of information security, we consider below.
Conceptual Information Security Model
The conceptual model answers general questions and reflects schematically the general structure of the information security model, on which other models and information security concepts are built like on a rod.
To build a conceptual model of information security, no matter how simple or complex an information system is, you need at least to answer three questions: what to protect, from whom to protect and how to protect? This is a mandatory minimum, which may be sufficient for small information systems. However, taking into account the possible consequences, it is better to build a complete conceptual model of information security, in which you need to define:
- Information sources
- Priority or importance of information.
- Sources of Threats
- Threat targets
- Threats
- Access methods
- Directions of protection
- Means of protection
- Protection methods
The following schematically shows the most complete conceptual model of information security, which is common to all information systems.

Figure 1. A conceptual model of information security
Building a conceptual model of information security of a virtual server can be divided into several different levels. In most cases, two levels are enough - the upper, organizational and managerial, which covers the entire organization and corporate information system, and the lower or service level, which relates to individual subsystems of the information system itself and various services.
The concept or top-level program is headed by the person directly responsible for the organization’s information security. In small organizations, as a rule, the head of the organization himself, in larger ones, these duties are performed either by the head of the IT department or directly by the head of the information security department, if such a department is separated into a separate structure.
Within the framework of the top-level program strategic security decisions are made, this program should contain the following main objectives:
- Strategic planning
- Development and implementation of information security policy
- Risk assessment and risk management
- Coordination of information security activities
- Control activities in the field of information security
The main goal or concept of a lower level program is to provide reliable and economically viable protection of information subsystems, specific services or groups of services. At this level, decisions are made on the following issues: what mechanisms, means and methods of protection to use, procure and install technical means, perform day-to-day administration, monitor the information security system as a whole and monitor the condition of weak points, conduct initial training of personnel, etc.
Usually, for the program of the lower level are responsible responsible heads of departments for ensuring information security, system administrators and administrators and managers of services. The most important action at this level is to assess the criticality of both the service itself and the information that will be processed with its help.
For this level it is necessary to formulate answers to the following questions:
- What data and information will this service serve?
- What are the possible consequences of a breach of the confidentiality, integrity and availability of this information?
- What are the threats to which the data, information, service and user will be most vulnerable?
- Are there any features of the service that require special measures - for example, territorial distribution or any other?
- What should be the characteristics of personnel relevant to safety: computer skills, discipline, reliability?
- What are the legal provisions and corporate rules that a service must meet?
A few very important points to consider are:
- “This program is not the embodiment of a simple set of technical tools built into the information system - the information security system has the most important“ political ”and managerial aspects. The program must be officially accepted and supported by top management, it must have a certain staff and a dedicated budget. Without such support, orders, directives and various “appeals” for the execution of the program will remain empty. ”
- “When building a model of information security of a physical server or VPS , you should always remember that no matter how much you want to protect information, surrounding it with dozens of fences and security systems, applying the most modern and sophisticated methods and means of protection, spent efforts and means to build an information system security must be achieved by economically viable measures. ”
Once the conceptual model of information security has been built, you can begin to build a mathematical and functional model of information security.
Mathematical and functional models of information security
The mathematical and functional model is directly related to each other. A mathematical model is a formalized description of scenarios in the form of logical algorithms represented by a sequence of actions of violators and retaliatory measures. The calculated quantitative values of the model parameters characterize the functional dependencies that describe the processes of interaction of offenders with the protection system and the possible results of actions. It is this type of model that is most often used for quantitative assessments of the vulnerability of an object, building a protection algorithm for assessing risks and the effectiveness of measures taken.
When building these models it is necessary to rely on the following key circumstances:
- Selection of mathematically rigorous criteria for assessing the optimality of the information security system for a given information system architecture;
- A clear mathematical formulation of the task of building a model of information security tools, taking into account the specified requirements for the protection system and allowing the construction of information security tools in accordance with these criteria.
In practice, in conditions of multiple risks to security risks, it is obviously not possible to make such a numerical assessment without using mathematical modeling methods.
For example, consider the mathematical model of an economically viable system for minimizing information security risks.
Based on an expert assessment of the likelihood of a threat to information security, the significance of each threat is calculated, and the level of costs in terms of restoring the system is estimated. Next, the total risk of system failure is calculated as the sum of risks for each of the areas.
The result of solving the described problem will be the distribution of the financial resource in the selected areas of the organization, minimizing the risks of system failure according to the criterion of information security.
Let the technical or socio-economic system specify (find) the dependences of the risks Ri of system performance failure on expenses Xi to avoid them (exclusion, decrease) in the i-th direction of information security (hardware, software failure, system performance failure due to insufficient qualifications of employees, managers, etc.)
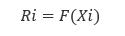
i = 1 ... n, where n is the number of specified directions.
Thus, while minimizing information security risks, we will use such an indicator as the level of costs (in material or value terms) for restoring the system to work in the event of its failure in one or several areas.
We further define the following values:
1) The total risk of system failure
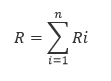
2) Z - the maximum amount of costs to reduce (eliminate) the allocated risks
3) ZMAXi - the maximum amount of expenses for the implementation of the i-th direction
4) ZMINi - the minimum amount of expenses for the implementation of the i-th direction,
Further, we can formulate the following problem of mathematical programming, in which each of the risks must be minimized, the total amount of costs to avoid them should be less than or equal to the maximum amount of costs to reduce (eliminate) the identified risks, where the costs of avoiding threats in each of directions should be greater than the minimum amount pledged for this direction, but it should not exceed the maximum amount for the same direction.

The constructed system is economically justified in the event that the sum of all the costs of avoiding, reducing or eliminating the risks compiled does not exceed or is equal to the total maximum amount of costs allocated for reducing (eliminating) the total risks.
This is just one of the examples of using mathematical modeling in building the information security system of your virtual server . Mathematical modeling can also be used to construct a mathematical model of a potential intruder, in which it is possible to determine the coefficient or probability to realize the threat of an attack by a potential intruder. Or, the problem of reserving system elements can be considered, solved to protect against breach of confidentiality of information processed in the information system.
Depending on the goals and the problem being solved, many mathematical models of a part of the information security system can be built and applied, which will help to evaluate its effectiveness even at the design stage of the information security system.
The last not unimportant question when building any models or systems is the life cycle of the model or system.
Unfortunately, it is not enough just to build an information security system using different models, but it is also necessary to observe the life cycle of this system. In which, regardless of the size of the organization and the specifics of its information system, work to ensure information security, in one form or another, should contain the following steps or steps presented in Figure 2.

Figure 2. The life cycle of an information security system
It is important not to miss any significant aspects. This will guarantee some minimum (basic) level of information security, mandatory for any information system.
Source: https://habr.com/ru/post/347088/
All Articles