Two-factor authentication is simple, using the example of JaCarta U2F
Today we will talk about the U2F standard, developed by the FIDO Aliance Association, of which we are a participant , and the electronic key of our own design, JaCarta U2F , and, of course, we will show several examples of its use.
What does a person think about when hearing a mention of words like two-factor authentication, dongle, USB-token, smart card? A person who is far from being immersed in information security technologies may remember one-time SMS passwords to enter the bank, and someone will think about public key infrastructure, certificates, chains of trust.
Meanwhile, the U2F protocol, developed by the FIDO alliance, is gaining popularity among Internet companies and shows that two-factor authentication is not only safe, but easy and simple, and most importantly, clear to the end user, a non-technical specialist.
The truth is there is a minus, in contrast to the centralized enterprise use, this very end user himself should attend to strengthening authentication into his favorite services and acquire such a token for himself, and the services, in turn, should support U2F in advance.
')
There are already quite a few such services, and their list is constantly expanding. At first, the standard U2F was supported by Google (gmail, youtube, etc), Dropbox, Github. Now joined by Facebook, Salesforce, Bitbucket, Dashlane and other services and companies. U2F has received great development in a cryptocurrency environment on various crypto-exchanges and crypto-wallets, for example, Bitfinex, Coinbase and others. We will talk about this separately later.
Hacking accounts in social networks, mail and other services is not news, it is always unpleasant, and often associated with financial or reputational losses, and, as a rule, hacked accounts are protected only by a simple, maybe not simple, but still one password, without second authentication factor. Popularization of the second factor in principle, and U2F in particular, leads to an increase in the general level of computer literacy and security.
If the service itself has not yet added the ability to bind the U2F key as an authenticator, it may be possible to do this through two-factor authentication providers, for example, duo security , and the access can be configured not only in web applications. Strictly speaking, such cloud platforms use not only U2F as authenticators, and their capabilities are much broader. But not to mention this opportunity in our review article, we also could not.
We have provided one more way to integrate U2F in our JaCarta Authentication Server (JAS) authentication server, embedding is done by setting up the server and adding the necessary code to the site, access to which must be protected.
As an example of a resource where U2F support is already implemented, let’s take Google as the most popular.
And for an example of authentication using the cloud authentication provider, the service duo.com and a WordPress website.
Google
Now check the input.
To log in to your Google account profile using JaCarta U2F, follow these steps:
To protect any application or protocol by means of the DUO platform, it is necessary to choose what to protect in the platform itself and associate the platform with the protected application.
From the Web site side, add a Duo plugin, to do this, in the Search plugins menu, find Duo-Two-Factor Authentication and click Set. After installation, click Activate.
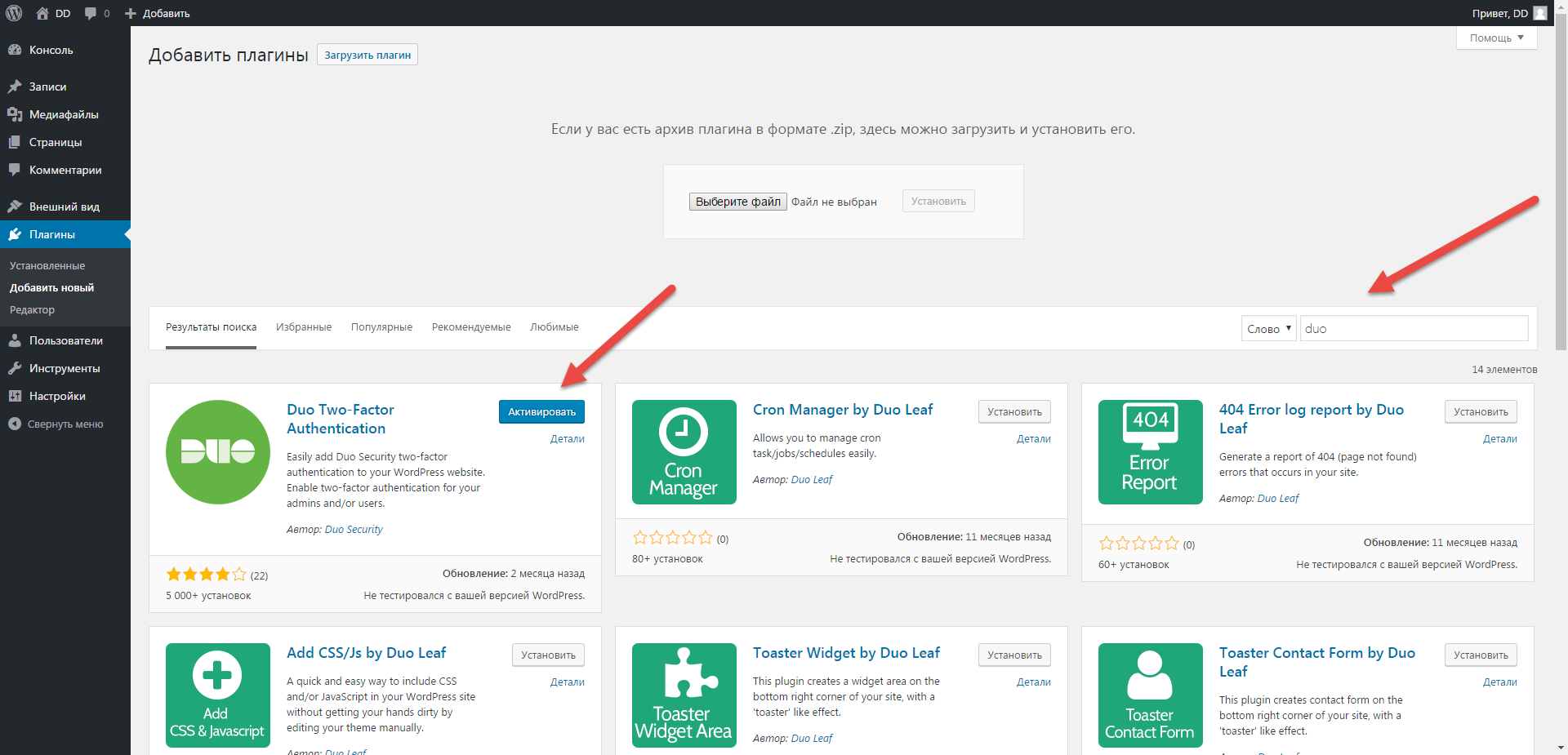
From the platform side, go to the Applications menu and select Protect an Application.

In the search menu that appears, type WordPress and click Protect this Application.
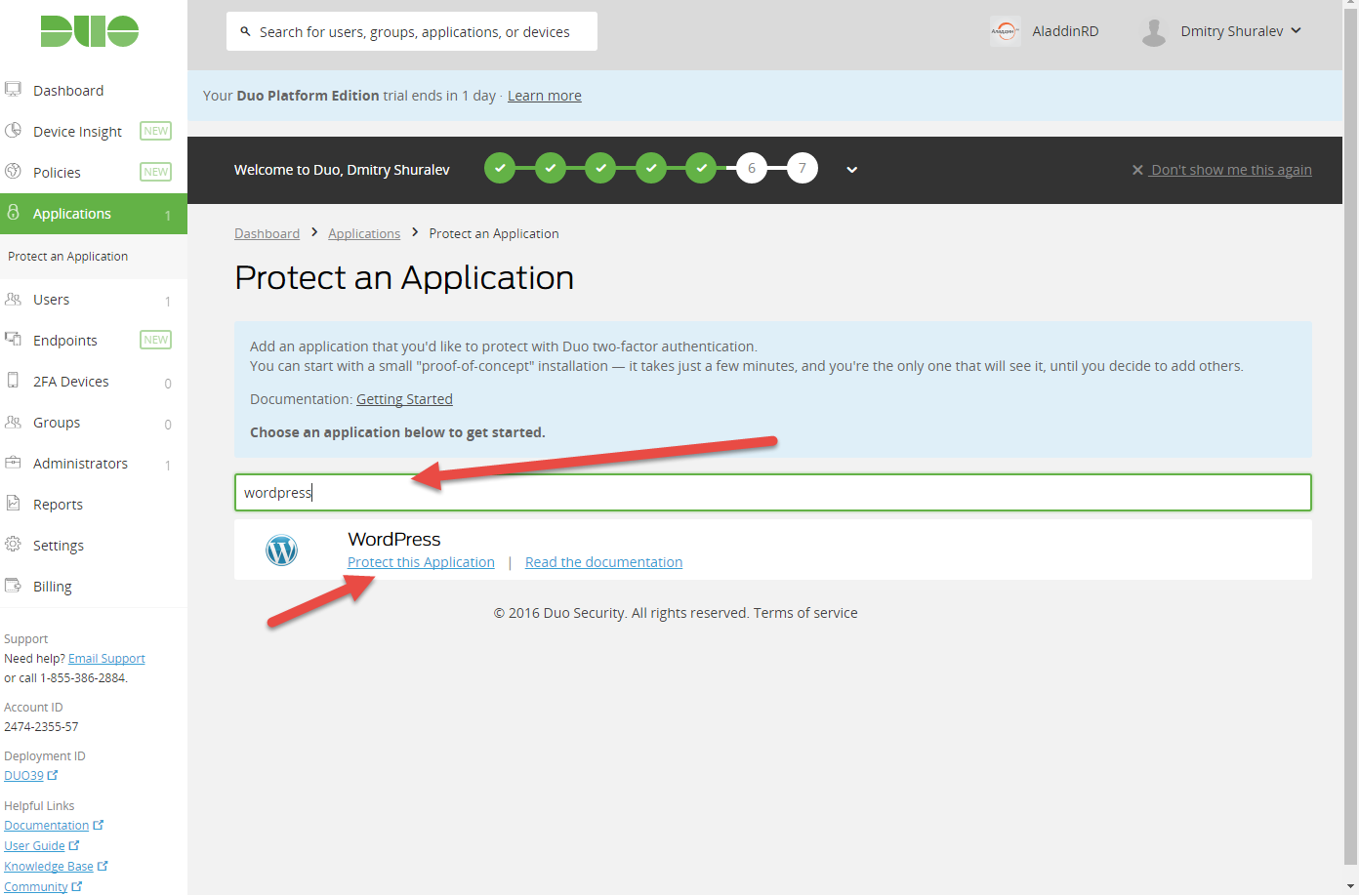
The 3 key fields, Integration Key, Secret Key and API Hostname are displayed.
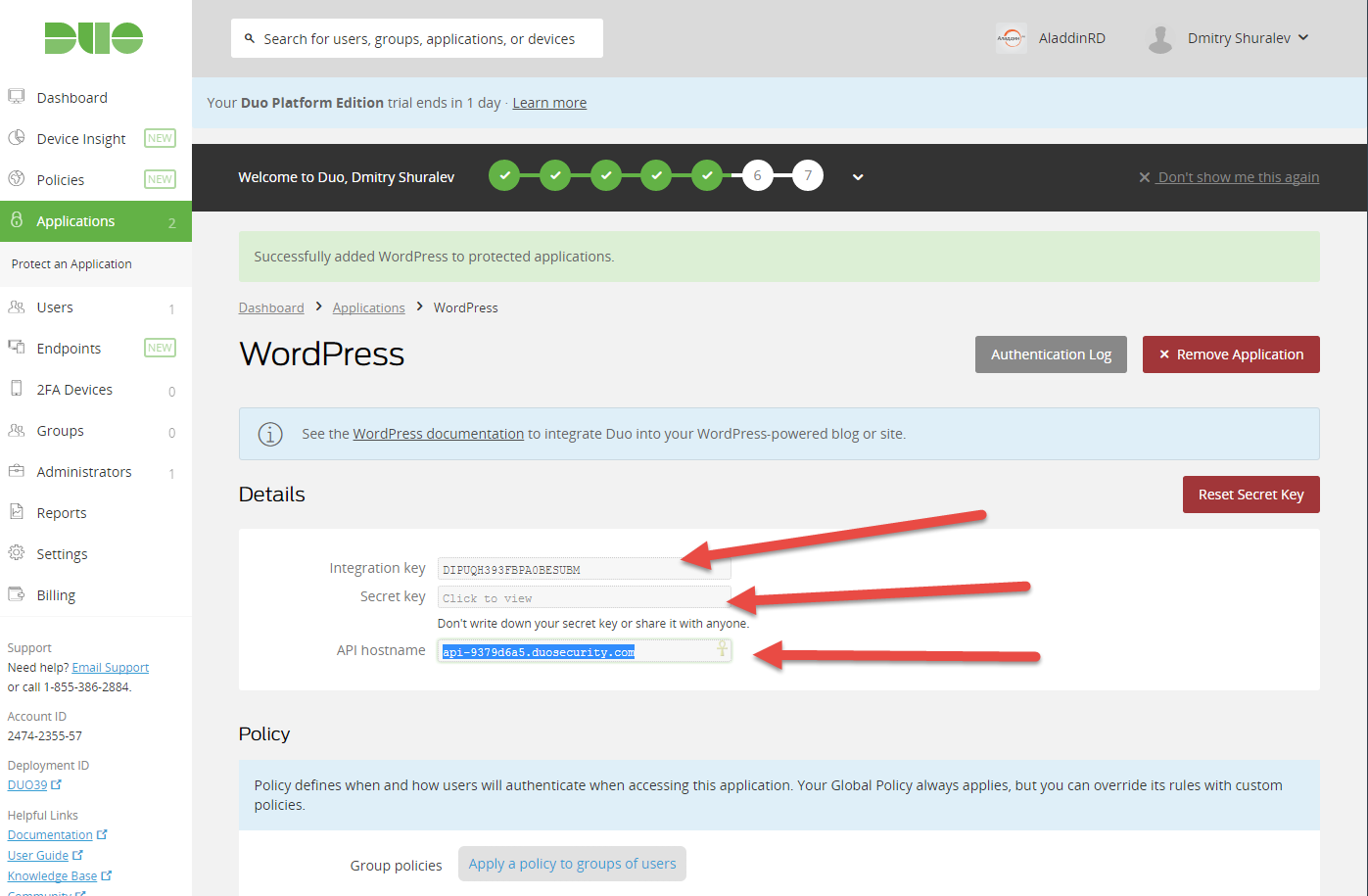
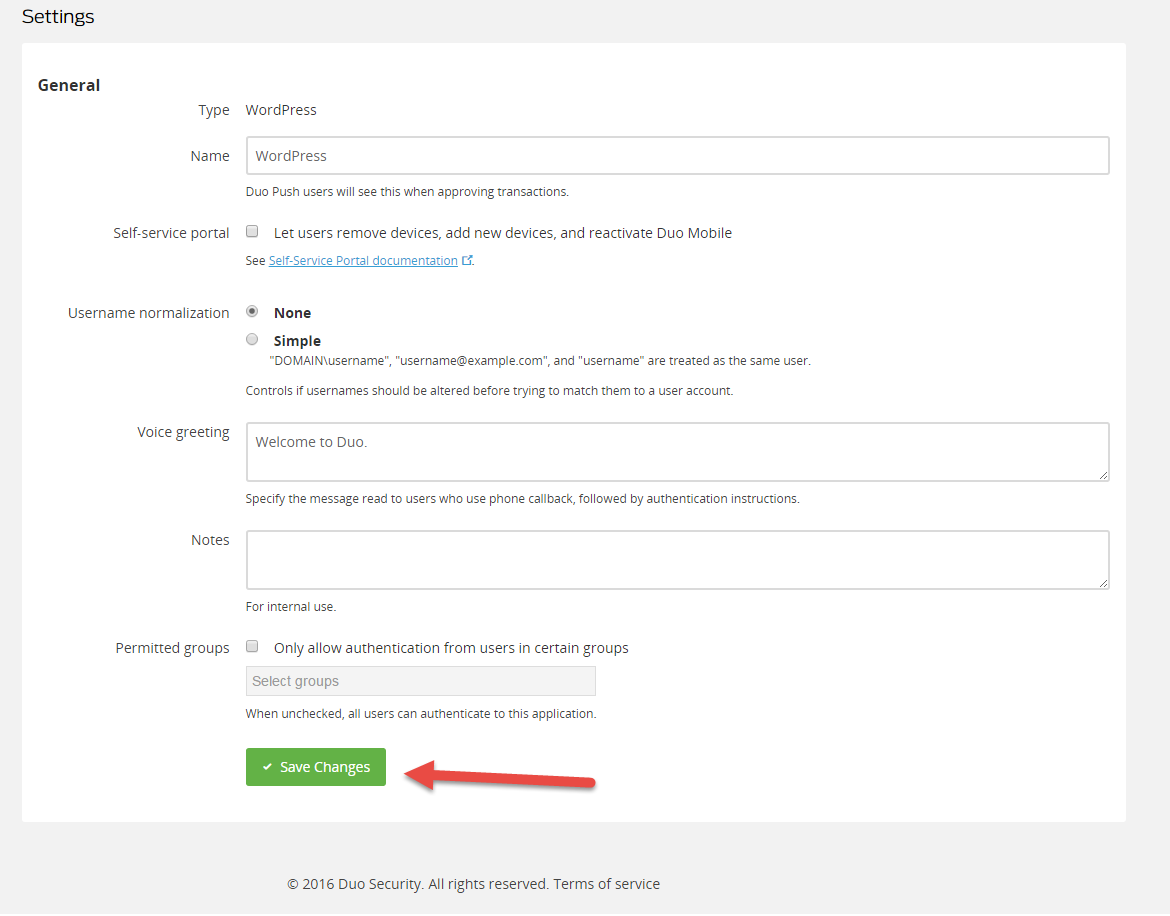
The values of these fields should be transferred to the corresponding fields of the plug-in on the Web site.

This completes the setup for linking the website to the DUO platform. Next, authenticate with a password on the Web site where the Duo platform was previously attached.
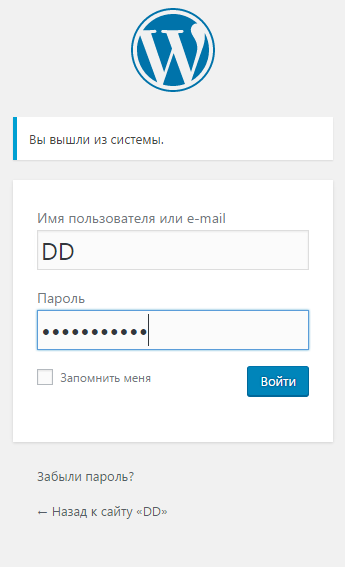
The installed and configured Duo plugin will offer to set up account protection. Click Start Setup.
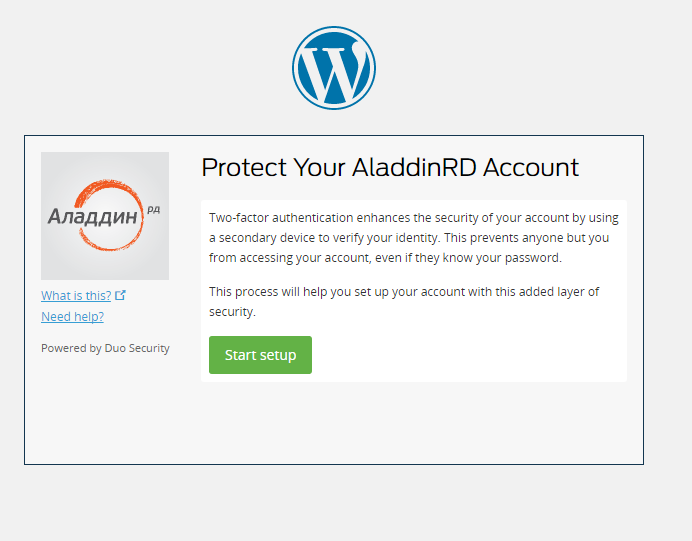
Select U2F-token.
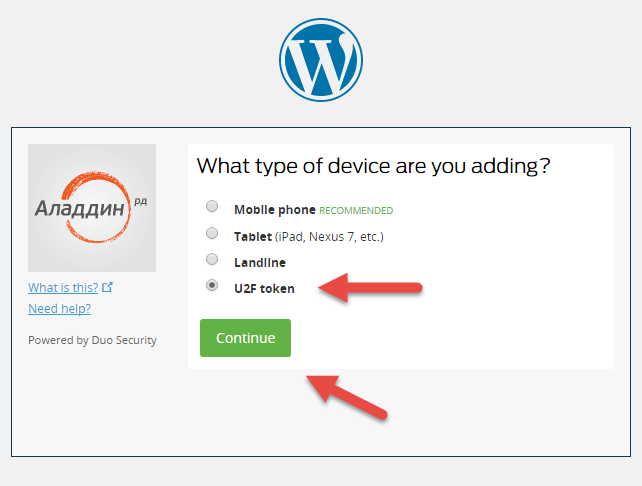
Connect your JaCarta U2F to a USB port and follow the directions.
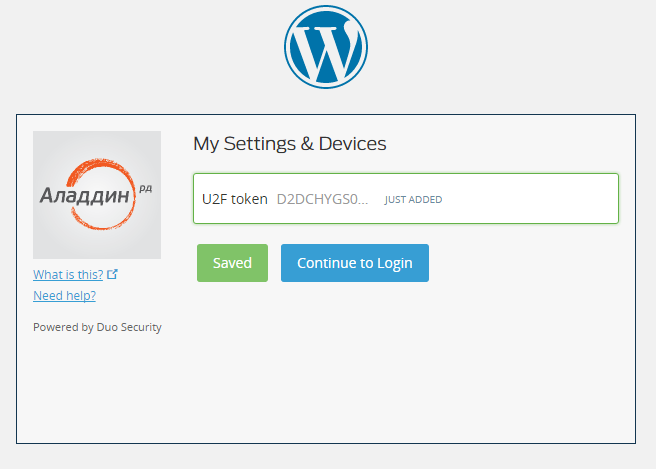
Upon completion, you will be taken to the admin part of the site, having passed authentication using JaCarta U2F.
Services themselves usually have their own instructions for configuring U2F, and they are fairly easy to find, here are some examples.
Facebook
Github
Dropbox
Google
In conclusion, we give some frequently asked questions and answers to them.
How to get access to a resource if the U2F key is lost? Everything is quite simple, there is a backup method of two-factor authentication in the form of a code by SMS or email. And after logging into your account, you can break the link with the lost key and set up a new one.
How many resources can be added to 1 key? Almost unlimited.
What platforms does U2F use? The device with any operating system, with a browser installed that supports U2F (currently this is Google Chrome version 38 and higher, Opera version 40 and above FireFox via a special plug-in), and a free USB port.
What does a person think about when hearing a mention of words like two-factor authentication, dongle, USB-token, smart card? A person who is far from being immersed in information security technologies may remember one-time SMS passwords to enter the bank, and someone will think about public key infrastructure, certificates, chains of trust.
Meanwhile, the U2F protocol, developed by the FIDO alliance, is gaining popularity among Internet companies and shows that two-factor authentication is not only safe, but easy and simple, and most importantly, clear to the end user, a non-technical specialist.
The truth is there is a minus, in contrast to the centralized enterprise use, this very end user himself should attend to strengthening authentication into his favorite services and acquire such a token for himself, and the services, in turn, should support U2F in advance.
')
There are already quite a few such services, and their list is constantly expanding. At first, the standard U2F was supported by Google (gmail, youtube, etc), Dropbox, Github. Now joined by Facebook, Salesforce, Bitbucket, Dashlane and other services and companies. U2F has received great development in a cryptocurrency environment on various crypto-exchanges and crypto-wallets, for example, Bitfinex, Coinbase and others. We will talk about this separately later.
Hacking accounts in social networks, mail and other services is not news, it is always unpleasant, and often associated with financial or reputational losses, and, as a rule, hacked accounts are protected only by a simple, maybe not simple, but still one password, without second authentication factor. Popularization of the second factor in principle, and U2F in particular, leads to an increase in the general level of computer literacy and security.
If the service itself has not yet added the ability to bind the U2F key as an authenticator, it may be possible to do this through two-factor authentication providers, for example, duo security , and the access can be configured not only in web applications. Strictly speaking, such cloud platforms use not only U2F as authenticators, and their capabilities are much broader. But not to mention this opportunity in our review article, we also could not.
We have provided one more way to integrate U2F in our JaCarta Authentication Server (JAS) authentication server, embedding is done by setting up the server and adding the necessary code to the site, access to which must be protected.
Configuration and use examples
As an example of a resource where U2F support is already implemented, let’s take Google as the most popular.
And for an example of authentication using the cloud authentication provider, the service duo.com and a WordPress website.
- Sign in to your google account.
- Go to the account settings page by clicking on the "My Account" button in the upper right corner of the page.
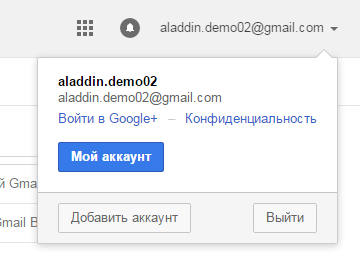
- Go to the "Security and Login" section.

- In the section "Password and method of logging in to your account," click on the link "Two-step authentication."

- Click on the “Proceed to customization” button and follow the instructions.
- In the process of setting, uncheck the box "Trusted computer". Otherwise, the token will not be used when entering the account.
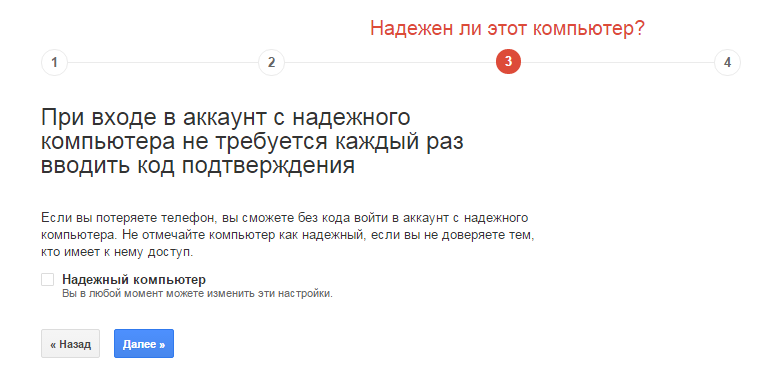
- Go to the “Tokens” tab and click on the “Add hardware token” button.

- Connect the token to the USB port and wait until the indicator light on the token body lights up continuously.
- Click on the "Register" button, after which the indicator light will flash.
- Click the button on the token body.
- Registration token complete.
Now check the input.
To log in to your Google account profile using JaCarta U2F, follow these steps:
- Connect JaCarta U2F to your computer and visit https://www.google.com .
- At the top right of the page click on the Login button.

A page containing the following form will be displayed.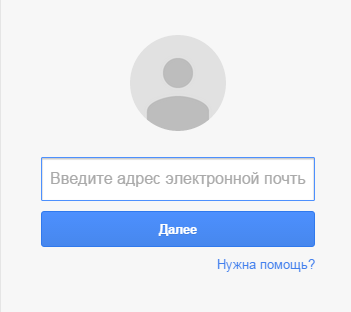
- Enter your email address and click Next.
The following form will be displayed.
- Enter your account password and click Login.
The next page will be displayed.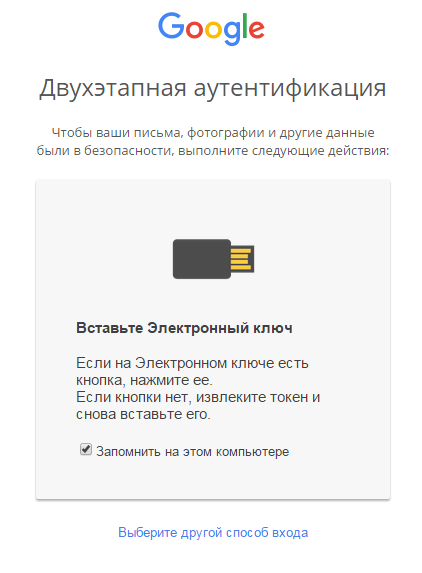
- Uncheck the box Remember on this computer.
If you leave the Save on this computer checkbox selected, two-factor authentication mode for access to the account on this computer will be disabled. To log in you will need to enter only the user password. - Click on the button on the case of JaCarta U2F.
Signed in to your Google Account Profile.
Authenticating to a WordPress Web site using the cloud authentication provider duo.com
To protect any application or protocol by means of the DUO platform, it is necessary to choose what to protect in the platform itself and associate the platform with the protected application.
From the Web site side, add a Duo plugin, to do this, in the Search plugins menu, find Duo-Two-Factor Authentication and click Set. After installation, click Activate.

From the platform side, go to the Applications menu and select Protect an Application.

In the search menu that appears, type WordPress and click Protect this Application.

The 3 key fields, Integration Key, Secret Key and API Hostname are displayed.


The values of these fields should be transferred to the corresponding fields of the plug-in on the Web site.

This completes the setup for linking the website to the DUO platform. Next, authenticate with a password on the Web site where the Duo platform was previously attached.

The installed and configured Duo plugin will offer to set up account protection. Click Start Setup.

Select U2F-token.

Connect your JaCarta U2F to a USB port and follow the directions.

Upon completion, you will be taken to the admin part of the site, having passed authentication using JaCarta U2F.
Services themselves usually have their own instructions for configuring U2F, and they are fairly easy to find, here are some examples.
Github
Dropbox
In conclusion, we give some frequently asked questions and answers to them.
How to get access to a resource if the U2F key is lost? Everything is quite simple, there is a backup method of two-factor authentication in the form of a code by SMS or email. And after logging into your account, you can break the link with the lost key and set up a new one.
How many resources can be added to 1 key? Almost unlimited.
What platforms does U2F use? The device with any operating system, with a browser installed that supports U2F (currently this is Google Chrome version 38 and higher, Opera version 40 and above FireFox via a special plug-in), and a free USB port.
Source: https://habr.com/ru/post/347032/
All Articles