January fixing holes in the .NET Framework and Core
Exactly by the end of the New Year holidays in Russia, on January 9th, Microsoft released updates correcting CVE-2018-0786 and CVE-2018-0764 . They repaired it so that they broke it somewhere else. In this short post we will once again remember what it is and what we should do now.
To illustrate this habrapos, I tried to draw a sieve. As you can see, I did not succeed. Unfortunately, making a sieve in a code is much easier than portraying it, for the first time picking up a graphic tablet.
Am I also under threat?
If you are using the .NET Framework, you need to make sure that you have version 4.7.1 installed, and Windows installed the .NET Framework update January 2018 Security and Quality Rollup ( KB4055002 ). Or, at a minimum, Security-Only Update ( KB4054183 ).
If this is not the case, you have problems.
You can check the version of the .NET Framework itself using the link instructions . In order not to check each time with your hands, there is a script for Power Shell .
If you are using .NET Core, then you need to go to the file system and see which version of runtime is installed. If there is no directory 1.0.9 , 1.1.6 or 2.0.5 , then you have a problem!
Where to see:
| Windows | C: \ Program Files \ dotnet \ shared \ Microsoft.NETCore.App \ |
| macOS | /usr/local/share/dotnet/shared/Microsoft.NETCore.App/ |
| GNU / Linux | /usr/share/dotnet/shared/Microsoft.NETCore.App/ |
Exact list of vulnerable .NET Core versions:
| Runtime version | Fixed in version |
|---|---|
| 1.0.0, 1.0.1, 1.0.2, 1.0.3, 1.0.4, 1.0.5, 1.0.7, 1.0.8 | 1.0.9 |
| 1.1.0, 1.1.1, 1.1.2, 1.1.4, 1.1.5 | 1.1.6 |
| 2.0.0, 2.0.3, 2.0.4 | 2.0.5 |
What to do?
Developers will have to update the .NET Framework to 4.7.1 and update Windows with the latest updates . Not on all versions of Windows this update works well (read the article to the end).
The .NET Core SDK must be upgraded to version 2.1.4 or 1.1.7 . Sysadmins need to update .NET Core to version 1.0.9 , 1.1.6 or 2.0.5 .
Self-contained applications will have to be rebuilt; in other cases, runtime update and the SDK are sufficient.
CVE-2018-0764: Denial of Service when parsing XML documents
Official links
What happened?
.NET Framework and Core poorly parse XML, using what a hacker can do with a DDOS attack on your application.
In the update it was fixed. Exploits are not publicly distributed.
CVE-2018-0786: Security Feature Bypass in X509 Certificate Validation
Official links
What happened?
In the public versions of the .NET Framework and Core, there is a vulnerability that allows a hacker to slip a certificate marked invalid for a particular use, and nevertheless use it for this purpose. This allows you to ignore Enhanced Key Usage.
In the update it was fixed. Exploits are not publicly distributed.
Do I need to upgrade packages?
The Microsoft.NETCore.UniversalWindowsPlatform package is vulnerable.
The package version is listed along with its corresponding .NET Native version.
| NuGet / .NET Native | Fixed in version |
|---|---|
| 5.2. * / 1.4. * | 5.2.4 |
| 5.3. * / 1.6. * | 5.3.5 |
| 5.4. * / 1.7. * | 5.4.2 |
| 6.0. * / 2.0. * | 6.0.6 |
How to repair my application if I use .NET Core?
For this bug, the type of application is important:
- Ordinary
- Self-contained
- Native
Regular applications can be repaired by simply installing the correct version of the SDK or runtime you are running on. Download here .
Self-contained applications will have to be rebuilt with the newly updated SDK and redone.
Next, let's talk about native applications. It is necessary to process it again with the native compiler of the updated SDK and re-allocate the result in the Windows Store.
MS recommends upgrading UWP applications to the latest minor version of the Microsoft.NETCore.UniversalWindowsPlatform NuGet package so that you can rebuild the application and understand that it has not collapsed. You can, of course, update immediately and to a more recent major version, but this is not necessary - an update is issued for all major versions that have been affected by the bug.
Regardless of whether you updated your NuGet-packages, all applications filled in to the store after January 9th will be automatically repaired right during the uploading to the store.
If you do not update your application in the store, it will still be automatically processed and sent via Windows Update over the coming weeks. Anyone who hasn't disabled auto-updates will get an updated version without the need for someone to manually intervene. But for sideloaded applications, you will have to update the NuGet packages yourself, rebuild them and deliver them to users.
Updates will break Windows 7 and Windows Server using the .NET Framework
According to this still open bug , the patch not only treats, but also disables it. The problem only occurs when using Windows 7 Service Pack 1 and Windows Server 2008 R2 Service Pack 1.
It is enough to install updates or the .NET Framework 4.7.1, as WPF applications requesting the fallback font (or a character not included in the current font) fall off with the following error:
System.TypeInitializationException “FileFormatException: No FontFamily element found in FontFamilyCollection that matches current OS or greater: Win7SP1”. Inner exception originates from: CompositeFontParser The problem is that the installer incorrectly handles the interaction of the update installer (.NET Framework January 2018 Rollup - KB4055002) and the already installed .NET Framework 4.7.1. The Rollup installer accidentally overwrites the GlobalUserInterface.CompositeFont file that came with version 4.7.1, causing WPF applications to fall.
There are three solutions.
Method one: remove the January updates
You need to remove: "January. NET Framework Security and Quality Rollup ( KB4055002 )".
And instead install: "January .NET Framework Security-Only Update ( KB4054183 )".
To do this, you need to perform the following steps:
- Control Panel → Windows Update → View update history
- In the "Review your update history" list, find and select "Security Update for Microsoft .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1 (KB4055002)". Click Uninstall.
- When asked whether or not to delete - agree.
- Be sure to restart the computer if you are asked to.
- Download and install the security patch of the version you need:
- Do everything you are asked for, and in the end - be sure to restart the computer.
Method two: uninstall .NET Framework 4.7.1, install .NET Framework 4.7
- Control Panel → Programs and Features
- In the "Uninstall or change a program" list, highlight "Microsoft .NET Framework 4.7.1" and click Uninstall / Change.
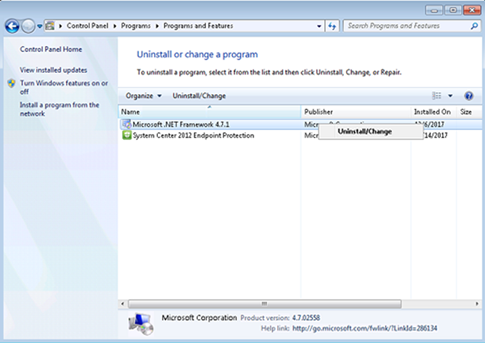
- Select "Remove .NET Framework 4.7.1 from this computer", and click Next.

- Click continue and wait for deletion.
- Click Finish when the removal is complete.

- Be sure to restart the computer if you are asked to.
- Install .NET Framework 4.7 .
Method three: replace GlobalUserInterface.CompositeFont with the correct file
- Download GlobalUserInterface.CompositeFont (for Windows 7, the standard installation path is
%USERPROFILE%\Downloads) - Open
cmd, go to%windir%\Microsoft.NET\Framework\v4.0.30319\WPF\Fontsand run:xcopy /y %USERPROFILE%\Downloads\GlobalUserInterface.CompositeFont.
(or just copy the GlobalUserInterface.Composite file to this place) - Open
cmd, go to%windir%\Microsoft.NET\Framework64\v4.0.30319\WPF\Fontsand run:xcopy /y %USERPROFILE%\Downloads\GlobalUserInterface.CompositeFont.
(or again use the copy-paste file in Explorer). - Restart the WPF application.
- If it still does not work, restart the computer and restart the WPF application again.
Summary
Even very good and quality projects contain mistakes. In order not to be trapped, you need to be updated in time, read official news and study current trends at conferences like DotNext , of course. Salvation of the drowning is the work of the drowning!
')
Source: https://habr.com/ru/post/346764/
All Articles