First meeting with the ss team
In Linux, there are programs that are useful to programmers, information security specialists, administrators ... in short, everyone will find here what he needs.
The

')
Today we will talk about how to use
The
The
If you run
Full list of established connections
Since the
Of course, in any situation, the team in its simplest form is not so useful. What if you only need to list the sockets waiting for connections? To do this is simple - just use the
This command will display a list in which there are only sockets that are listening to the network.
In order to further narrow the range of data output by this command, consider that the

The ss command, executed in Elementary OS, gives a list of UDP connections
By default, using the
TCP sockets will be output to this command:

Note that the last socket is waiting for ssh connections.
In the above example, you can see that the connections (in different states) are established from the IP address of the analyzed computer, and information is displayed on the ports on this computer, as well as on the addresses and ports on remote systems. Unlike the
A very convenient feature of the
In addition,
Working with states is pretty simple. For example, for IPv4, it looks like this:
For IPv6 like this:
In these two examples, the
Suppose you want to see all pending connections for IPv4 sockets. To do this, this command will help:
In response to this command, the system displays something similar to the one shown in the following figure.
Using ss with a connection wait state filter
One of the useful applications of
In response to this command, information will be displayed, including Netid, connection status, data on the local IP address and port, as well as on the remote IP and connection port.

Remote computer has established an ssh connection to our machine.
The
Dear readers! Do you use ss?

The
netstat command-line tool was one of the tools that system administrators often used. However, the netstat team was recognized as outdated and replaced by a faster and more convenient ss command to use.
')
Today we will talk about how to use
ss in order to learn about what is happening with the network on a computer running Linux.About ss command
The
ss command is a tool used to display network statistics in a form similar to that issued by the netstat command. However, ss makes it easier and faster than netstat . In addition, ss provides more information about TCP connections and connection states than most other tools. In particular, ss can output data about entities such as PACKET, TCP, UDP, DCCP, RAW, and Unix domain sockets. The ss command is simpler than netstat . in order to verify this, it is enough to compare the man pages of these two tools. With ss you can get very detailed information about how a machine running Linux communicates with other computers. All this opens up possibilities for diagnosing and fixing various network errors.Basics ss
The
ss command works just like any other Linux command line utility. Namely, the name of the corresponding executable file is entered on the command line, followed by the required combination of options. If you take a look at the ss help page (you can call it with the command man ss ), you will notice that there are much fewer command line keys here than netstat . However, this does not mean scant ss opportunities. In fact, we have a very powerful tool.If you run
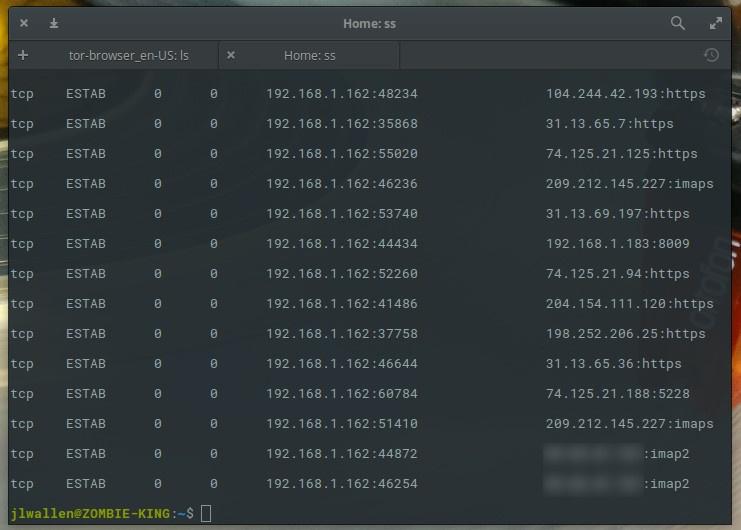
ss with no command line arguments or options, it will display a complete list of working connections.
Full list of established connections
Since the
ss command (without options) shows a lot of data (details on all connections established via TCP, UDP, and using Unix sockets), you can send the output of this command to a file in order to analyze it later. This is done, for example, as follows: ss > ss_output Of course, in any situation, the team in its simplest form is not so useful. What if you only need to list the sockets waiting for connections? To do this is simple - just use the
-l option: ss -l This command will display a list in which there are only sockets that are listening to the network.
In order to further narrow the range of data output by this command, consider that the
-t option allows you to view information on TCP connections, the -u option is used to display data on UDP connections, the -x option displays data on Unix connections. It looks like this: ss -t , ss -u , or ss -x . Any of these commands will display a large amount of data that can be analyzed.
The ss command, executed in Elementary OS, gives a list of UDP connections
By default, using the
-t , -u or -x options will display only the data on the established connections. If you want to select connections that are waiting for connections, you need to add the -a option to the command call: ss -t -a TCP sockets will be output to this command:

Note that the last socket is waiting for ssh connections.
In the above example, you can see that the connections (in different states) are established from the IP address of the analyzed computer, and information is displayed on the ports on this computer, as well as on the addresses and ports on remote systems. Unlike the
netstat command, ss does not display the PID and the name of the command responsible for a particular connection. However, even with this in mind, we have at our disposal a lot of data for searching for network errors. If something is under suspicion, ss will let you know the details of the connection, and therefore, give the administrator information that will be useful in the early stages of solving network problems.Filtering ss output based on TCP states
A very convenient feature of the
ss command is that it can filter the output using TCP states (or connection lifecycle states). By using states, ss output filtering is facilitated. Namely, all standard TCP states are available here:establishedsyn-sentsyn-recvfin-wait-1fin-wait-2time-waitclosedclose-waitlast-acklisteningclosing
In addition,
ss recognizes the following state identifiers:all(all of the above)connected(all states except pending and closed)synchronized(all states corresponding to the established connections, except forsyn-sent)bucket(states representing mini-sockets, for example -time-waitandsyn-recv)big(all except thebucketid)
Working with states is pretty simple. For example, for IPv4, it looks like this:
ss -4 state FILTER For IPv6 like this:
ss -6 state FILTER In these two examples, the
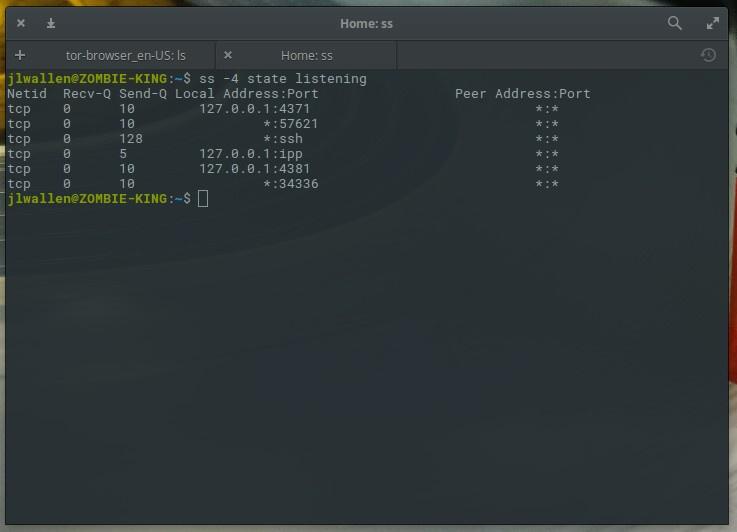
FILTER is a state identifier.Suppose you want to see all pending connections for IPv4 sockets. To do this, this command will help:
ss -4 state listening In response to this command, the system displays something similar to the one shown in the following figure.

Using ss with a connection wait state filter
Show connections from specific addresses
One of the useful applications of
ss is to get information on connections established from certain IP addresses using this command. Suppose you need to find out whether the machine is connected, say, with the IP address 192.168.1.139 to our server, and if this is the case, learn more about it. To solve this problem, this command is suitable: ss dst 192.168.1.139 In response to this command, information will be displayed, including Netid, connection status, data on the local IP address and port, as well as on the remote IP and connection port.

Remote computer has established an ssh connection to our machine.
Results
The
ss utility can be very useful in finding and troubleshooting network problems for Linux servers. Of course, in order to fully master ss , it would be nice to read man and practice. However, you now have an idea of how to use this command, which a modern Linux administrator just needs to know.Dear readers! Do you use ss?

Source: https://habr.com/ru/post/346744/
All Articles