How much slower will your system after patches for Specter-Meltdown?

Earlier this week, Intel released a microcode update for a large number of current and outdated processor models. The update is available as packages for Red Hat Enterprise Linux, SUSE Linux Enterprise Server, CentOS, Fedora, Ubuntu, Debian, and Chrome OS, allowing you to update the microcode without updating the BIOS. Updating the microcode does not eliminate the need to apply KPTI patches to the Linux kernel (the microcode is necessary for the complete closure of Specter's vulnerability);
Intel also published data on changes in the performance of systems with 6th, 7th, and 8th generation processors after security updates related to the shutdown of Specter and Meltdown vulnerabilities, collected both from users and using synthetic tests.
')
Under the cut there are several interesting conclusions from the data published by Intel, as well as the impact of patches on Linux systems:
Intel research results for client systems
- The result obtained for the SYSMark 2014 SE Data / Finance Analysis test turned out to be very encouraging for business users.
- Gamers should also be relieved, as the 3DMark Sky Diver test shows that the performance of DX11 games is almost unaffected by security updates.
- The test that showed the greatest performance decrease is SYSMark 2014 SE Responsiveness. He showed that performance is reduced by up to 21% for workloads such as launching applications, launching files, browsing web pages with multiple tabs, multitasking, copying files, encrypting and compressing files, and installing a background application.
The impact of updates on platforms with 8th generation processors (Kaby Lake, Coffee Lake) with solid-state drives is small — less than 6 percent. In some cases, users may see a more noticeable effect. For example, users who use web applications that are associated with complex JavaScript operations may have a slightly higher performance loss — up to 10 percent.
The performance impact of Skylake is slightly higher, but generally corresponds to observations on 8th and 7th generation platforms (approximately 8 percent in the SYSMark2014SE test). Performance was also measured on a single platform with Windows 7. The observed impact is less significant (approximately 6% in the SYSMark2014SE test). The effect is even lower on systems with hard drives instead of SSDs. Thus, the PC with Windows 7 and HDD practically do not lose performance.
Results are available in the table below.

In pdf-format is available by reference .
More about tests
BAPCo SYSmark 2014 SE
The following applications (grouped by scenario) are installed and / or used in SYSmark 2014 SE.
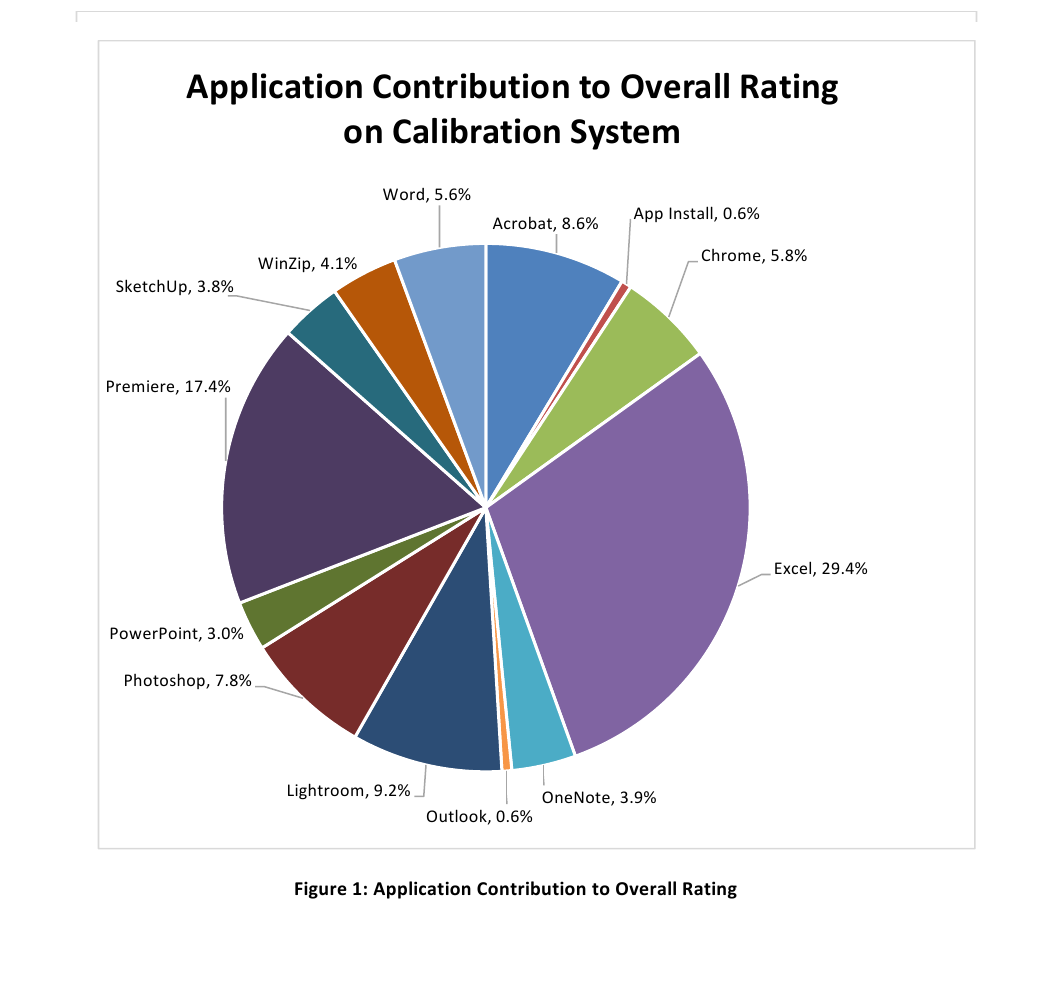



PCMark 10
PCMark 10 contains tests that cover a wide range of work found in a modern office: from everyday needs and applications to demanding work with media content.

3DMark Sky Diver
WebXPRT 2015
Based on which of the scenarios is more similar to the scenario of the users of the systems you administer, you will be able to assess the likely decline in performance after installing the updates.
If the effect of the updates does not suit you, the Microsoft website contains information on how you can disable the latest fix. More on the link .
Linux server performance
Currently, the efforts of vendors to protect aimed at eliminating the three vectors of possible attacks.
The Meltdown patches are implemented by KPTI (Kernel Page Table Isolation - Isolation of the Kernel Page Table) and KAISER (Kernel Address Efficiency Removed - Isolation of the Kernel Address Space in order to avoid third-party channel) techniques.
Prior to the updates from Intel, which were mentioned at the beginning of the article, last Thursday, Google experts talked about the retpoline software design they created to protect against Specter attacks.
Read more about Retpoline
"The Retpoline technique is currently being introduced into the Clang / LLVM compiler as a means of protecting against one of the Specter-Vulnerability options," said Jeff Tang, senior analyst at Cylance. “However, the LLVM compiler is primarily used in Apple macOS, some Linux and BSD distributions, and also in Google Chrome. This list does not include Microsoft Windows and other popular Microsoft Windows programs that typically use the Microsoft C / C ++ compiler. ”
Google reports that the retpoline technique is already deployed in the cloud infrastructure and its impact on performance is “negligible.” Michael Larabel founder Phoronix.com tested Linux systems with Retpoline Patch . In general, his research confirms this.
KPTI Patche for Linux is expected to result in performance degradation from 5% to 30%.
VM Performance Showing Mixed Impact With Linux 4.15 KPTI Patches
Finally, the combined effect of Retpoline + KPTI on Ubuntu Linux
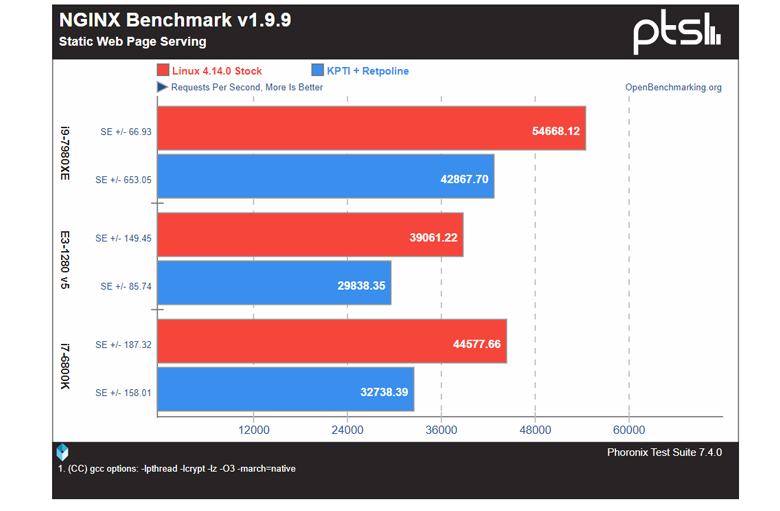
The result of one of the tests
According to information from Red Hat, using patches to fix CVE-2017-5754, CVE-2017-5753 and CVE-2017-5715 vulnerabilities in Red Hat Enterprise Linux 7 slows down the execution of tasks by 1-20%:
- The highest performance drop (8–20%) is observed in the DBMS operation on OLTP loads, with random access to the cached memory, with active buffered I / O, with a high intensity of context switching between the kernel and the user level (system calls). Large losses are observed in tpc, sysbench, pgbench, netperf (up to 256 bytes) and fio (random access to NvME memory) tests.
- A drop in performance of 3-7% is noted when performing analytical queries in the DBMS, in decision support systems (DSS) and in the Java VM, at times of intensive information exchange over the network or when accessing the disk.
- A decrease in performance of 2-5% is observed in HPC (High Performance Computing) solutions with a large computational load on the CPU, if most of the work is done in user space using binding to the CPU cores or using numa-control (for example, Linpack NxN and SPECcpu2006 tests) ;
- The minimal impact on performance (less than 2%) manifests itself in systems that use methods of direct access to resources, bypassing kernel functions and various offload-acceleration techniques. For example, tests DPDK (VsPERF 64 bytes) and OpenOnload (STAC-N).
More information about updates and performance tests related to Meltdown and Specter vulnerabilities can be found here .
Source: https://habr.com/ru/post/346518/
All Articles