We select passwords using Google Chrome
According to numerous computer security studies, the TOP-3 information system vulnerabilities include password guessing.
Almost every information system today has its own default accounts, which are widely distributed on the Internet. For example, they can be taken from here.
If we have a portal where users are people, then most of the vulnerable weak passwords can be assigned to one of 4 groups:
- Passwords included in the top most popular phrases (such as "123456", "password", etc.).
- Passwords that represent keyboard shortcuts - so-called keyboard-walks passwords (for example, “qwerty”, “qazwsx”, etc.).
- Passwords are distorted logins (“user123”, “user321”, etc.).
- Or use as a password of popular Russian words or names in the "inverted" layout ("ljcneg", "fylhtq") .
The trouble is that the majority of people - and both ordinary users and system administrators - tend to use easy-to-remember passwords.
From the selected groups of frequent passwords, it follows that when selecting a password, you can use 4 dictionary creation methods, respectively:
- According to the haveibeenpwned.com service, today the scale of general leaks is approaching the figure of 5 billion (think of myspace, linkedin, adobe, etc.). Based on some of these leaks, you can identify the top 1000 most common passwords. For example:
cat antipublic / exploitin / | sed -rn 's / [^:] + :(. ) / \ 1 / p' | sort | uniq -c | sort -n -r | head 1000> top1000.txt * - Just over a year ago, the wonderful utility kwprocessor appeared from the creator of the hashcat tool. Using it, you can generate all possible keyboard shortcuts for any keyboard layout:
kwp basechars / tiny.base keymaps / en.keymap routes / 2-to-10-max-3-direction-changes.route | len.bin 6 100> keywalks.txt - Obtaining a sufficiently large amount of distortion for a certain user name is most easily done using the hashcat utility rule set:
hashcat -r /usr/share/hashcat/rules/leetspeak.rule logins.txt --stdout> login_mutations.txt - Similar to the first item in the list, you can take as a basis for the dictionary large-scale leaks of Russian-language resources.
The collected password sets can later be fed to utilities such as hydra, medusa, ncrack, or patator, depending on the service being tested.
If authentication is implemented via the web, namely via the http-forms (that is, not http-basic / digest authentication), then it is best to use the intruder functionality from burp suite free (Figure 1).
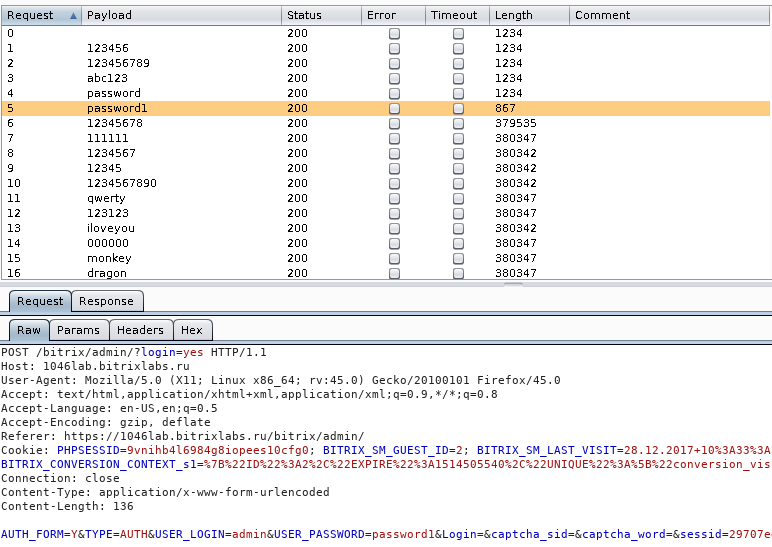
Figure 1 - Bruteforce-attack by improvised means
In the case of a burp, you need to closely monitor the size of the answer: changing the size of the answer can mean that the username or password is present in the system.
Also, with bruteforce attacks on the web, difficulties are possible (and it’s not even about captcha):
- First, a token can be used for each form submitted. And after each unsuccessful attempt, it can change.
- Secondly, there is no exact sample server response in case the password is guessed. Moreover, situations are possible when the answer to the correct and incorrect accounting data will be identical, and the answer will simply be redirected through the Location header, where it will be clear in the future about the success of the login attempt.
- Third, some web services during authentication do not send the entered credentials, as they were entered, in clear text. We are talking about cases when client-side hashing is used, and the hash functions themselves can be unique (not md5, sha-x, etc.).
However, solutions can be proposed for these difficulties:
- Developing a script that will parse the response from the server, find the token there, and then substitute it in the next request.
- Developing a script that performs a redirect with each response and a comparison of the length of the response received.
- Analysis of javascript code that performs certain transformations with the entered data, and after the implementation of this algorithm in its script.
Of course, these cases are not so frequent. However, sometimes, having encountered a similar web form, we only manually enter the default accounts and something trivial like admin: admin.
But what if to make brute force not at the level of http, but above, at the level of the user interface? After all, if we introduce javascript code into the context of the tested web application, which in the cycle will substitute the specified login / passwords into the form and send it, then it will be quite easy to bypass all the previously listed difficulties. After all, in fact, all the work is done by the browser.
You can accomplish this with the help of the greasemonkey browser extension and your own javascript code, which will be tightly sharpened by the markup of this html page. But writing js-code for each new page every time is inconvenient. It would be most convenient to have all this as a separate extension , in this case for Google Chrome.
All you need to use www_brute is to open any site of interest and click on the extension icon. If everything is done correctly, something like this will appear (Figure 2).
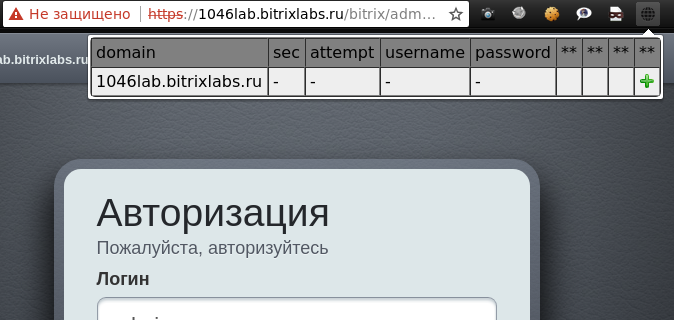
Figure 2 - Adding a new target
To start setting up a brute force, you need to click on a single button - “plus”.
All setup is simple and comes down to two points:
- Select data entry fields - the arrow button.
- Select data to enter - the next button.
Before selecting the fields for entering the login and password on the page of the site with the form to be attacked, a script will be implemented that sequentially catches three clicks on the page elements. These elements must be the username, password fields and the submit button. The listed elements should be selected exactly in this sequence (Figure 3).
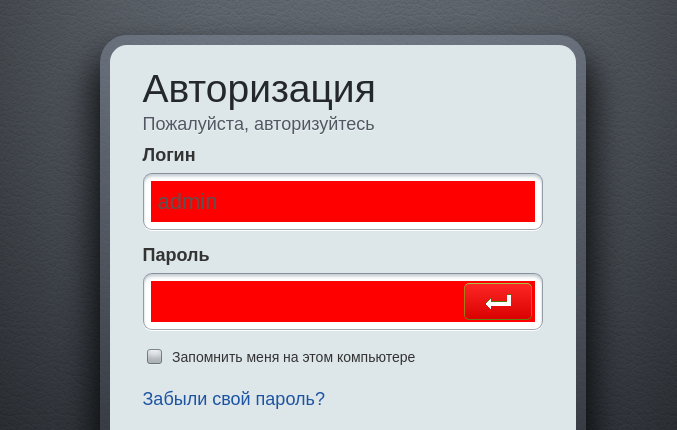
Figure 3 - Selection of fields for input
Each time you click on the corresponding item, it will turn red, which confirms its selection. After selecting the submit button, the page may reload (if it does not use ajax), in which case the red selection will disappear, but this is normal.
It is very important to note that input elements are remembered by html-attributes and their values. Therefore, if after submitting the form, the site “draws” another form, then the next attempt to select the input field will not be found. Although the logic for searching input fields does not allow for full matching of attributes, it is still better to make this setting after at least one unsuccessful sending of credentials. An example is facebook.com (Figures 4 and 5).
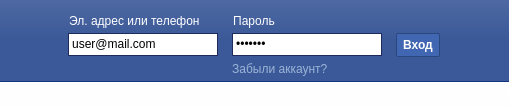
Figure 4 - Form before the first login attempt
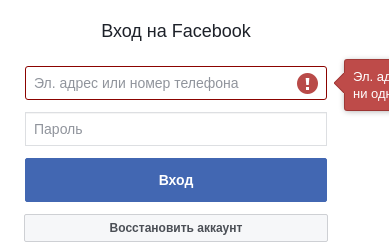
Figure 5 - Form after the first login attempt
Dictionaries are supported for user names, passwords and fixed pairs login: password (combo) (Figure 6).
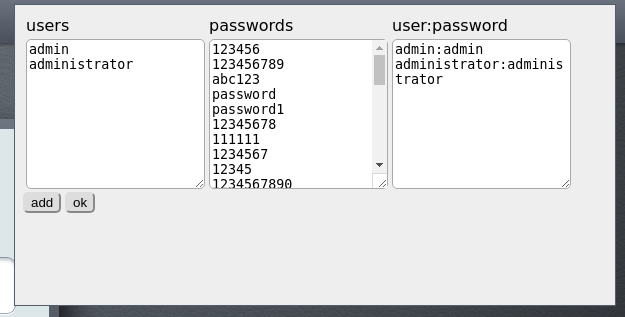
Figure 6 - Dictionaries for bruteforce attacks
Since combo dictionaries are used for default accounts or leaks, they will be selected first. Then it will be performed a complete enumeration of all combinations of usernames and logins. Moreover, all passwords will be searched for each login to minimize the possible blocking of users during unsuccessful attempts. The total number of attempts can be calculated by the formula:
length (combo) + length (passwords) * length (users)
At the end of all the settings you can start:
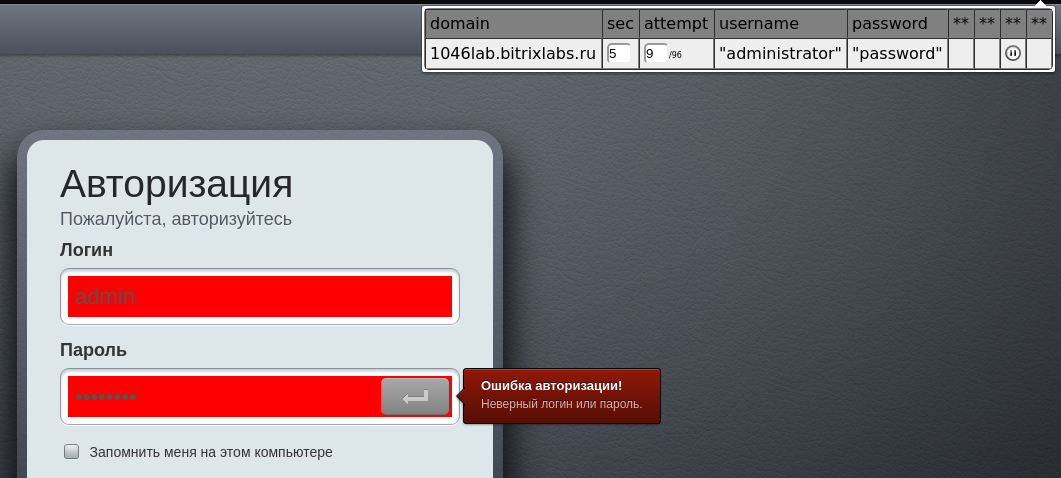
Figure 7 - Bruteforce-attack in action
The username and password values in the popup extension window are the following candidates for input.
The logic of work is quite simple and consists in the enumeration of all the given combinations of login / password, as well as pairs of login: password in a cycle until:
- the dictionary will not end;
- The input field will not disappear - which may indicate the success of the input (or blocking).
All statistics for the selection of the password is displayed in real time:
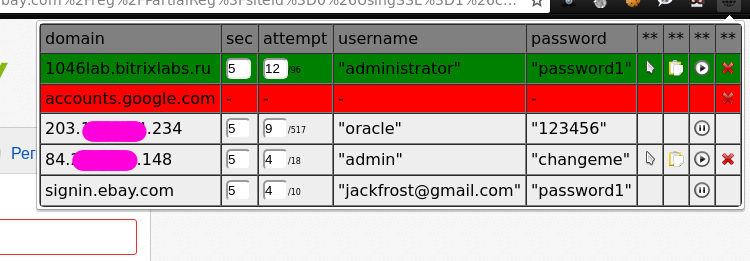
Figure 8 - The process of bruteforce attacks on multiple targets
Green highlighted that managed to pick up, red - an unsuccessful attempt. In the course of work, you can safely switch to another tab or completely minimize the browser window, because as we remember, the browser does bruteforce itself, and we only help it a little.
Passing through the password can be easily "parallelized". To do this, simply open one or more tabs on the same domain.
At any given time, the brute force of any site can be paused. It should be noted that the plugin does not have feedback from the server responses, so (especially in the case of ajax), you need to correctly select the interval between attempts. It is not recommended to set the interval value too small.
Of course, this method does not bypass such a thing as captcha, so the brute force of such things as gmail.com and the like will not last long. However, in combination with proxy / vpn, you can think of something ...
As for such things as brutfors adminok different CMS, monitoring systems, samopisnyh sites and other things that usually dazzle the network perimeters of different companies, this method fits perfectly.
A plugin for chrome, as well as a dictionary for the top 1000 passwords is available here and in the webstore.
')
Source: https://habr.com/ru/post/346284/
All Articles