Open Source Cisco Cybersecurity Projects
When it comes to open source projects developed by Cisco in the field of cybersecurity, most experts remember only the popular Snort, perhaps even ClamAV, and the OpenSOC tool described on the Habr pages. In fact, Cisco, being a fairly open company (we have a bunch of APIs to work with our security solutions), is very active in the open source community and offers users a few dozen projects, of which a considerable amount is cybersecurity. In this post I would like to put together all open source projects of Cisco, which are related specifically to this topic.

I would like to start a review from the projects that our information security service uses for its internal purposes, but which it shared for a wide range of specialists:
Much more open source projects were developed not by the Cisco IB service, but by our research division Cisco Talos , which studies various threats and automates many tasks related to collecting evidence, investigating, preparing indicators of compromise, etc .:
')
On this list of our open source projects in the field of cybersecurity could be completed, but not. We constantly have something new, something for the internal activities of the information security service, then for researching malicious code within the Cisco Talos, then for other projects that Cisco leads (for example, joy or TRex). You can track all this on our Internet pages:

I would like to start a review from the projects that our information security service uses for its internal purposes, but which it shared for a wide range of specialists:
- OpenSOC . A platform for analyzing Big Data in terms of cybersecurity, which I already wrote on Habré.
- GOSINT . This is a framework designed to collect, process, sort and export high-quality indicators of compromise. The sources for GOSINT can be either Twitter feeds or various feeds. An indicator may test for malware by using external solutions such as Cisco Umbrella, ThreatCrowd, and VirusTotal. Indicators are exported to CSV or CRITs . You can read more about this solution in our blog .
- netsarlacc . This is a high-performance corporate stub (sinkhole) for HTTP and SMTP, which can be used by IS monitoring centers or enterprise incident response services. This tool works in tandem with existing in the company means blocking, quarantine, captive-portals, solutions to redirect traffic, such as DNS RPZ. In a typical scenario, netsarlacc acts as an IP / CNAME to which the user is redirected, trying to get somewhere not there or trying to do something wrong.

- Malspider . This is the “spider” that inspects your corporate Web sites and portals to determine if they are compromised. Using the built-in algorithms and templates, Malspider detects hidden iframes, script inserts (injection), e-mail disclosures, etc. In addition to searching for compromised sites, Malspider is also used to generate indicators of compromise, which can then be used by other security solutions.
Much more open source projects were developed not by the Cisco IB service, but by our research division Cisco Talos , which studies various threats and automates many tasks related to collecting evidence, investigating, preparing indicators of compromise, etc .:
')
- Snort . A constantly evolving attack detection and network traffic analysis system that has become the de facto standard in the network security industry. On its basis, including built most of the domestic attack detection systems.
- Daemonlogger . Easy and fast sniffer, as well as a software splitter (tap), which can be used for monitoring network traffic.
- joy . A tool that, unlike daemonlogger, captures not individual packets and sessions, but Netflow or IPFIX network streams, which can then be used to monitor information security or investigate network incidents. We actively used this tool to analyze encrypted traffic and search for traces of malicious code without decrypting it.
- TRex . Free stateful and stateless client and server traffic generator L4-L7, scalable to 400 Gbit / s on one server. This tool can be used to test and compare various network solutions, including cybersecurity, - DPI, ITU, IPS, NAT, load balancers, server caching. Joy and TRex projects were not developed by Talos, but I included them in this list, as they fit well into the big picture.
- TAXII Log Adapter . A project that allows you to improve the work of SIEM (now it is Splunk and Arcsight) with TAXII services. Receiving data from them about threats, indicators of compromise, etc., the adapter converts them into SIEM-understood formats, for example, JSON or CEF.
- Clamav Anti-virus engine to detect Trojans, viruses and other types of malicious code. It was originally designed to scan email, but as a engine it can be used for other purposes.
- Moflow . Framework, which includes several tools (FuzzFlow, SliceFlow, ExploitFlow), designed to find and prioritize software vulnerabilities by generating various tests and analyzing answers to them in the context of information security.
- Razorback . Another Talos framework, which is a distributed engine for detecting attacks on client nodes.
- PE-Sig . A tool to automate the process of analyzing PE sections of executable files and generating signatures for known packers of executable code, which can then be loaded into various tools for analyzing malicious code, for example, in ClamAV.
- TeslaCrypt Decryption Tool . A command line utility that allows you to decrypt files encrypted with the extortionate TeslaCrypt software. You can read more about this solution in our blog .

- Synful Knock Scanner . A network scanner that identifies routers infected with the SYNFul Knock malicious code.
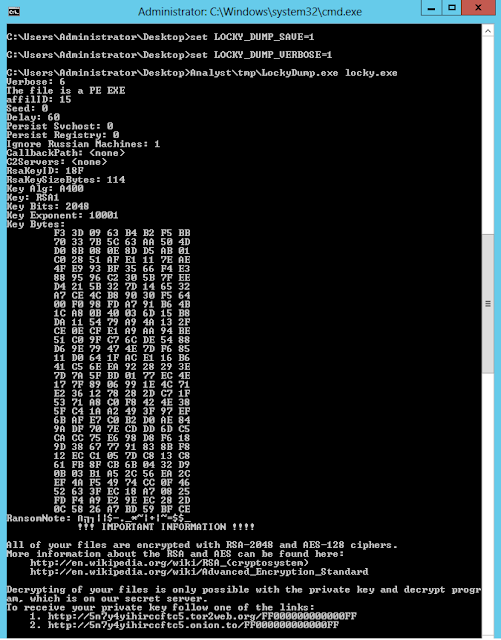
- LockyDump . A utility that allows you to pull configuration parameters from all known modifications of the malicious code Locky. You can read more about this solution in our blog .
- MBR Filter . The simplest utility that prevents recording in the MBR (Master Boot Record). You can read more about this solution in our blog .
- FreeSentry . Plugin for LLVM compiler, which complicates the exploitation of some types of vulnerabilities, for example, some classes of RCE. You can read more about this solution in our blog .
- FIRST . The Function Identification and Recover Signature Tool is a plugin for IDA Pro that allows reverse engineers to perform static analysis more quickly and easily. You can read more about this solution in our blog .
- Flokibot . A set of scripts to automate the analysis of malicious code Flokibot, based on the same code as the well-known Zeus malware. You can read more about this solution in our blog .
- ROPMEMU . A tool, including a plugin for Volatility, for analyzing complex attacks using code reuse. You can read more about this solution in our blog .
- Bass Automated Signature Synthesizer - a framework for the automatic generation of antivirus signatures based on existing samples. Unlike hash-based signatures, BASS generates template-based signatures, freeing up the time and resources of virus analysts and reverse engineers. You can read more about this solution in our blog .

- Pyrebox . It is a QEMU based, Python sandbox for reverse engineering. You can read more about this solution in our blog .

- File2pcap . This utility allows you to convert any input file to pcap, in which the source file as an attachment is transmitted via HTTP / HTTP2 / FTP / SMTP / IMAP / POP3. You can read more about this solution in our blog .
- Mutiny Fuzzer . This is a network fuzzer that allows you to record legitimate traffic (for example, a browser request) in the form of pcap and then repeatedly send it to the target host, modifying the traffic parameters as necessary and studying the host response behavior. You can read more about this solution in our blog .
- Decept . A network proxy written in Python that supports TCP, SSL, UDP, Unix Sockets, Raw Sockets, IPv6 (and any combinations thereof). Allows you to record traffic in .pcap or .fuzzer format (for integration with Mutiny Fuzzer) for its analysis, rewriting on the fly, etc. You can read more about this solution in our blog .
On this list of our open source projects in the field of cybersecurity could be completed, but not. We constantly have something new, something for the internal activities of the information security service, then for researching malicious code within the Cisco Talos, then for other projects that Cisco leads (for example, joy or TRex). You can track all this on our Internet pages:
Source: https://habr.com/ru/post/346160/
All Articles