Technical details. Meltdown Vulnerability - CVE-2017-5754
From the author
Important! Vulnerability is actually 3 vulnerabilities - Meltdown, Specter 1, Specter 2
Hello habr! Today we have a translation of a note about the vulnerability of Meltdown (CVE-2017-5754). Only the first page and the main part of the note for understanding this vulnerability have been translated.
Meldown
General
The security of a modern computer system (author's note. Smartphones, computers, practically any wearable devices with the ability to run code not from the manufacturer) is based on the isolation of the address space, for example, the kernel memory is marked inaccessible and protected from access by the user. In this post we bring you Meltdown. Meltdown exploits the side-effect of out-of-order execution in modern processors in order to read data from the kernel, including personal information and passwords. Out-of-queue performance greatly affects performance and is included in most modern processors. The attack is independent of the operating system and does not exploit software vulnerabilities. Meltdown breaks all system security based on isolation of the address space including the paravirtualized one.
Meltdown allows you to read part of the memory of other processes and virtual machines. We show that the KAISER system has an important side effect in the form of blocking Meltdown (but is a crutch). We insist on the inclusion of KAISER immediately to prevent information leaks.
Introduction
Security of a modern computer system based on isolation of the address space. Operating systems guarantee isolation of individual processes. In modern processors, state separation between kernel processes (kernel process) and user processes (user process) is provided by the hypervisor bit. The whole concept is that this bit is cleared in the user process and set in the kernel process. The change of processes occurs by interruption (interrupt) and system calls (system call / syscall). Currently, memory addressing does not change during system calls and interrupts. Meltdown runs on Intel processors from the 2010s, and can also potentially affect processors from other manufacturers (author's note: AMD, VIA). Meltdown exploits the side-effect of out-of-order execution in modern processors to read data from the kernel, including personal information and passwords.
The processor, instead of waiting for data from external buses with a long delay and idle, starts executing instructions and fills the parts of the kernel that are idle. But these actions have a side effect - the difference in the execution time of instructions.
Vulnerable processors allow an unprivileged process to execute code out of turn and load data from kernel memory into a temporary register. Even more - the processor performs calculations based on the value of this register, for example, loading data from an array of data depending on the register value. The processor guarantees the correct execution of the code, resetting the execution result, for example, the recorded register, if the prediction result is incorrect. Thus, there are no problems at the architectural level. But, as it was noted, executing out of turn has a side effect - filling the cache depending on the code executed out of turn. Thus, the attacker can read all the data in the address space of the kernel using the micro-architecture feature.
Meltdown works on modern personal computers and laptops, as well as servers in the clouds. Also in the sandboxes based on the division of the kernel - paravirtualization and sandbox inside the process.
The KAISER countermeasure prevents attacks targeting KASLR and inadvertently protects against a Meltdown attack.
Abstract example
raise_exception(); access(probe_array[data * 4096]) The second line will never be executed.
Whatever the error is caused, it translates the execution-out-of-line state in the context of the error — most often the kernel.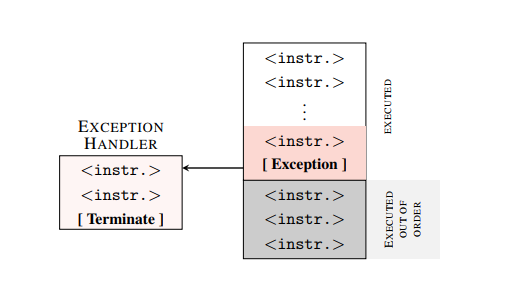
Despite the fact that the second line of code was not executed at the architectural level , it changed the state of the cache at the world architecture level . .
.
As you can see, the access time to different areas of the array is different, since the cache loaded part of the memory that it had access to during the out-of-queue execution.
Thus, we can transfer data from the out-of-queue execution state, which executes instructions in privileged mode, to the attacker's user process.
Further, based on the fact that access to data already in the cache is less than the time during which the processor rolls back the action performed out of turn, the attacker reads the value of the part of the core memory in the processor cache. Sometimes reading attempts end in failure. the processor has time to reset the execution-out-of-queue pipeline before it reads the data (0.003%) and allows reading data at a speed of 503KB / s on the i7 6700K.
The thread that takes advantage of this vulnerability will fail with an error, so in order to exploit the vulnerability, the process must be able to create a child thread, with access to the memory of the child thread.
Vulnerability vulnerability
Linux
We successfully exploited this vulnerability in kernel versions from 2.6.32 to 4.13.0.
KAISER patch eliminates this vulnerability.
Windows
We successfully reproduced this vulnerability in Windows 10 (comment perev. Version is not specified)
Containers
The attack can be played in containers such as OpenVZ, Docker, LXC.
Limitations in AMD and ARM.
We were not able to reproduce this vulnerability on ARM and AMD, but perhaps our implementation is too slow.
BUT! We managed to reproduce the vulnerability associated with running out of turn on both processors.
Important! Operating system patches prevent Meltdown, but not Specter
Important! This vulnerability may be present in other processors!
Sorry for the short note! I will not do this anymore :).
')
Source: https://habr.com/ru/post/346074/
All Articles