Coding with the withdrawal of information. Part 2, Mathematical
Introduction
In the previous part, the principal possibility of coding was considered, in which, in case you can isolate the common part of the key and the message, you can transmit less information than there is in the original message.

Let me tell you a little about where this topic came from. A long time ago, from one good person, I took ivlad to read and now I can’t give (please forgive) an interesting book [1], where it is written: “In turn, the cryptography itself can be divided into two areas, known as permutation and replacement” .
Accordingly, almost immediately the following questions appeared:
- because permutation and replacement preserve the amount of information, is it possible to do so in order to circumvent this restriction, and transfer information less than it is in the message - from here (from “whether it’s not weak”) the first part was born;
- if the problem seems to be solved, then whether there is a solution itself and at least a fraction of the mathematical meaning in it - this question is the theme of this part;
- Is there any practical sense in all this? The question is still open.
What do the crow and the desk have in common?

The picture is taken from here .
The riddle of Carroll in the title is given as an illustration of the problem that needs to be solved. Namely: define a couple of functions - coding and - decoding satisfying the following conditions:
- –The amount of information transmitted by Shannon is less than the amount of information in the original message
- - the decoding function applied to the encoded message will allow to unambiguously restore the original message.
Here - the amount of information on Shannon [2] (assuming that all characters are equally likely, which is not true in general, but is used for simplicity of presentation) in the message , - key, - coded message.
In order to simplify further reasoning, let us restrict ourselves to further messages that can be numerically constrained, which on the one hand does not particularly limit us (since you can assign an appropriate numeric code to any character), and on the other, allow you to use mathematics in the right amount.
So, consider first for example two numbers and and using the main theorem of arithmetic [4] (any natural can be decomposed into a product of simple) we find the following parameters:
- Smallest common factor and - its simple dividers ,
- Private and its simple dividers which we denote as ,
- Decomposition number to prime factors: ,
- Decomposition number to prime factors: .
Let's write all this in tabular form, where the general part of the information between the key and the message is marked in blue, the information is unique for the key in yellow, and the message is unique in orange:
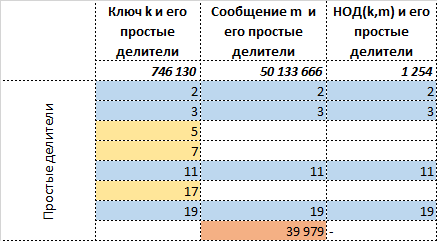
Immediately it becomes clear that is a common part between the key and message that both the sender and the recipient have. Thus, ideally, of course, and not in reality, it is enough to transmit information about:
')
- unique to the message information - that does not apply to those. , namely ,
- the very but so that it cannot be restored.
Mark now the positions of simple dividers common with simple dividers , units, and the rest, except maybe the leading position - zeros.
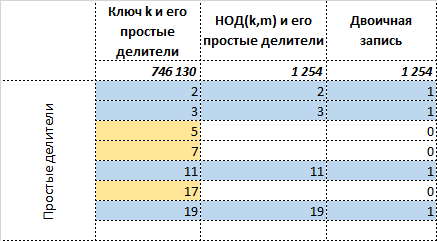
The resulting number sufficiently characterizes , thereby allowing the original message to be restored. Those. getting two numbers to the input you need to do a fairly simple inverse transformation:
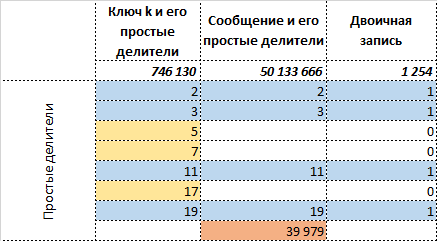
If we now estimate the length of the original message in binary form and messages you can see that you can save the message length in bit, the same with the amount of information bit, bit Here is the function - the length of the number in binary form.
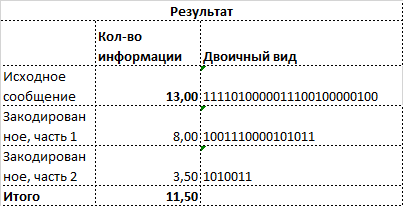
Thus, to put it in words from the well-known anecdote, "in Scotland there is at least one sheep, black at least on one side" [3].
So, at the moment we have - this coding method is suitable, but only for pairs of numbers that have the same divisor in the decomposition. Otherwise, if, for example, we take simple numbers as a key and as a message, we obviously cannot reduce anything, but only increase the length of the message, as well as the amount of information transmitted, which is not what we wanted. The same situation is repeated in the case when, for example, or because savings will be either minimal or absent in principle.
What to do…
in order to increase the likelihood of success with this coding method?
In general, if you look closely at the key, it is clear that it is not bad divided into prime numbers what is done specifically for the success of the operation of finding . Since such an operation can negatively affect the number of keys used, then determining the order of simple factors and making it part of the key information, we obtain, although not radical, an increase in the number of encoding options that positively affect the number of keys. Using a number instead of a key and a couple where the second number represents the order of multiplication and determines the value .
The next problem to be effectively solved is the ratio of the frequencies of the appearance of primes and powers of two, it is easy to notice that the coding efficiency of powers of two rather quickly decreases with increasing length (see the graph of the corresponding sequences if there is one common simple divisor) and depends mainly on the number of key dividers and their values.
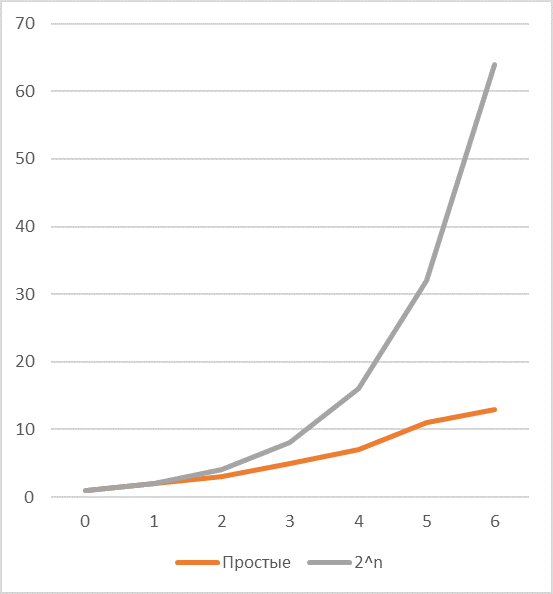
In case, there are two common dividers and one of them, for example, is , then opportunities for savings increase very noticeably.
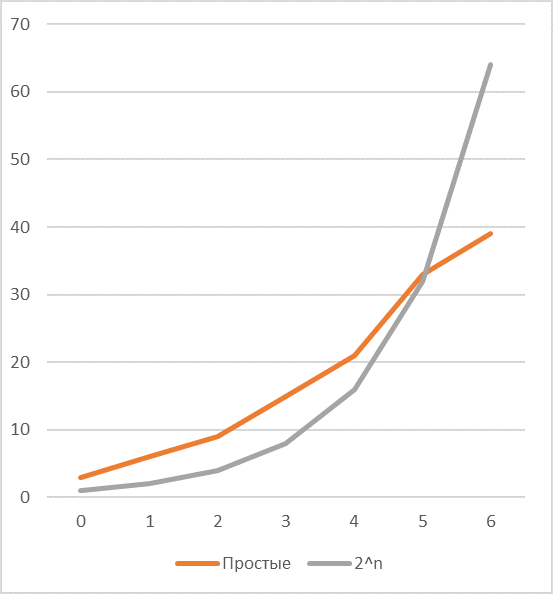
Which means that for efficient coding you need to come up with a more efficient coding method .
That is, it makes sense to continue the subject further.
Example
As usual, they are laid out on github [5] - Excel is used because many have it and there is no need to think about compatibility. There are two bookmarks in the file:
- "Test" - the calculations themselves, because they are quite actively using the Excel function "CASE ()" and the key and message numbers can be mutually simple, then you have to step into some cell and press
enterto get the desired savings (results in lines 31-36); - “Example 1” - examples of ready calculations are given, since chance in excel does not leave them a chance to repeat.
Links
- Singh Simon. Book cipher. The secret history of ciphers and their decryption. M. Astrel 2007.
- https://ru.wikipedia.org/wiki/%D0%98%D0%BD%D1%84%D0%BE%D1%80%D0%BC%D0%B0%D1%86%D0%B8%D0 % BE% D0% BD% D0% BD% D0% B0% D1% 8F_% D1% 8D% D0% BD% D1% 82% D1% 80% D0% BE% D0% BF% D0% B8% D1% 8F
- http://www.gaelic.ru/Biblioteka/Folklore/anekdoty.htm
- https://ru.wikipedia.org/wiki/%D0%9E%D1%81%D0%BD%D0%BE%D0%B2%D0%BD%D0%B0%D1%8F_%D1%82%D0 % B5% D0% BE% D1% 80% D0% B5% D0% BC% D0% B0_% D0% B0% D1% 80% D0% B8% D1% 84% D0% BC% D0% B5% D1% 82 % D0% B8% D0% BA% D0% B8
- https://github.com/rumiantcev/nod_code
Source: https://habr.com/ru/post/345962/
All Articles