Configuring VPN (PPTP) in Ubuntu 17.10 with authorization by JaCarta smart card
In Windows operating systems, setting up VPN access using smart cards is sufficiently simple and trivial. Although, gentlemen from MS clearly broke this feature in Windows 10 version 1709 build 16299.15.
When you try to connect to the VPN server using the pptp protocol using a smart card, Windows simply closes this window without any errors, even without asking for the password from the smart card.
“It was necessary to install Linux !!!”, many will say, and maybe they will be right.
')
In this article, we will look at how to set up a connection to a remote server via VPN using authorization on the JaCarta smart card.
The operating system was chosen OS Ubuntu 17.04 x64 Desktop. Unfortunately, I could not get a quick way to Debian 9, but this is a reason to write the next article under Debian.
1. Next, we put the packages we need.
* pptp version 1.9.0
In addition to the packages from the standard repository, we need drivers and libraries for our smart card.
Download
Unpack the archive
Install the necessary drivers and libraries.
For 64bit systems:
For 32bit systems:
2. Preliminary operations completed. Now the VPN setting itself.
2.1. First we need to check whether the system has seen our smart card. Insert the JaCarta card into the USB port of the computer and execute the command
After that, something like this should appear:
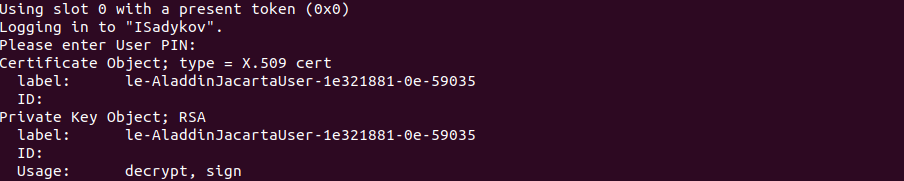
2.2. To create a configuration file, we will need key and certificate identifiers from a token. To do this, enter the command
after entering the PIN code, you will need to remember the values from the ID fields :
2.3. We get the root certificate of the organization in the .pem format from the certificate of the .cer format in the DER encoding.
2.4. Create the file /etc/ppp/openssl.cnf with the following content:
2.5. You must enable EAP-TLS authentication by commenting out the refuse-eap line in /etc/ppp/options.pptp
2.6. Create a file with connection parameters / etc / ppp / peers / any-peer-name, specify your domain login as the “UserName” parameter, then specify the path to the converted root certificate in the PEM format as the “ca” parameter, and “ cert "and" key "specify the stored key and certificate identifiers with the prefix" pkcs11: "
3. Connection establishment:
Connection break:
Enabling debug output during connection setup:
ATTACHMENT:
The instruction is based on the document .
When you try to connect to the VPN server using the pptp protocol using a smart card, Windows simply closes this window without any errors, even without asking for the password from the smart card.
“It was necessary to install Linux !!!”, many will say, and maybe they will be right.
')
In this article, we will look at how to set up a connection to a remote server via VPN using authorization on the JaCarta smart card.
The operating system was chosen OS Ubuntu 17.04 x64 Desktop. Unfortunately, I could not get a quick way to Debian 9, but this is a reason to write the next article under Debian.
$ uname –a Linux VPN-PPTP 4.13.0-16-generic #19-Ubuntu SMP Wed Oct 11 18:35:14 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux 1. Next, we put the packages we need.
$ sudo apt update $ sudo apt install opensc libpcsclite1 pcsc-tools pcscd libengine-pkcs11-openssl ppp pptp-linux * pptp version 1.9.0
In addition to the packages from the standard repository, we need drivers and libraries for our smart card.
Download
$ mkdir ~/tmp $ cd ~/tmp $ wget https://www.aladdin-rd.ru/support/downloads/279f1310-d83d-4858-ba13-ecdbe0d37530/get Unpack the archive
$ unzip get $ cd JaCarta_PKI_Linux/IDProtect\ Client\ 6.37.03/DEB/ $ ls idprotectclient_637.03-0_amd64.deb idprotectclient_637.03-0_i386.deb idprotectclientlib_637.03-0_amd64.deb Install the necessary drivers and libraries.
For 64bit systems:
$ sudo dpkg -i idprotectclient_637.03-0_amd64.deb $ sudo dpkg –i idprotectclientlib_637.03-0_amd64.deb For 32bit systems:
$ sudo dpkg -i idprotectclient_637.03-0_i386.deb 2. Preliminary operations completed. Now the VPN setting itself.
2.1. First we need to check whether the system has seen our smart card. Insert the JaCarta card into the USB port of the computer and execute the command
$ pkcs11-tool --module /lib64/libASEP11.so -L After that, something like this should appear:
[TEXT] Available slots: Slot 0 (0x0): Aladdin RD JaCarta [SCR Interface] (000000000000) 00 00 token label : ISadykov token manufacturer : Aladdin RD token model : JaCarta Laser token flags : login required, rng, token initialized, PIN initialized hardware version : 1.0 firmware version : 1.0 serial num : 4E46001220483933 pin min/max : 4/16 2.2. To create a configuration file, we will need key and certificate identifiers from a token. To do this, enter the command
$ pkcs11-tool --module /lib64/libASEP11.so -l –O after entering the PIN code, you will need to remember the values from the ID fields :
Using slot 0 with a present token (0x0) Logging in to "ISadykov". Please enter User PIN: Certificate Object; type = X.509 cert label: le-AladdinJacartaUser-1e321881-0e-59035 ID: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx Private Key Object; RSA label: le-AladdinJacartaUser-1e321881-0e-59035 ID: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx Usage: decrypt, sign 2.3. We get the root certificate of the organization in the .pem format from the certificate of the .cer format in the DER encoding.
$ openssl x509 -inform der -in ./root_certificate.cer -out ./root_certificate.pem 2.4. Create the file /etc/ppp/openssl.cnf with the following content:
$ sudo nano /etc/ppp/openssl.cnf openssl_conf = openssl_def [ openssl_def ] engines = engine_section [ engine_section ] pkcs11 = pkcs11_section [ pkcs11_section ] engine_id = pkcs11 dynamic_path = /usr/lib/x86_64-linux-gnu/openssl-1.0.2/engines/pkcs11.so MODULE_PATH = /lib64/libASEP11.so init = 0 2.5. You must enable EAP-TLS authentication by commenting out the refuse-eap line in /etc/ppp/options.pptp
$ sudo nano /etc/ppp/options.pptp # refuse-eap 2.6. Create a file with connection parameters / etc / ppp / peers / any-peer-name, specify your domain login as the “UserName” parameter, then specify the path to the converted root certificate in the PEM format as the “ca” parameter, and “ cert "and" key "specify the stored key and certificate identifiers with the prefix" pkcs11: "
pty "pptp ***.aladdin-rd.ru --nolaunchpppd" name isadykov # ( DOMAIN\\username) remotename ***.aladdin-rd.ru # require-mppe-128 file /etc/ppp/options.pptp ipparam any-peer-name need-peer-eap updetach usepeerdns defaultroute replacedefaultroute ca /path/to/root_certificate.pem # root.pem cert pkcs11:xxxxxxxxxxxxxxxxxxxxxxxxxx # certificate ID key pkcs11:xxxxxxxxxxxxxxxxxxxxxxxxxx # key ID 3. Connection establishment:
$ sudo pon any-peer-name Connection break:
$ sudo poff any-peer-name Enabling debug output during connection setup:
$ sudo pon klvpn debug dump logfd 2 ATTACHMENT:
The instruction is based on the document .
Source: https://habr.com/ru/post/345476/
All Articles