How to deal with miners cryptocurrency in the corporate network
The problem of using corporate IT resources for mining cryptocurrency is becoming increasingly common ( Transneft recently mentioned them). And the other day, the FSB descended on Vnukovo Airport and detained the administrator, who mined cryptocurrency at the computing capacity of the aviation harbor. I will immediately answer the frequently asked question: “And where is the FSB?” Everything is very simple. Vnukovo is not only an airport for ordinary passengers; the President of Russia and members of the Government flies from Vnukovo-2, which makes this air port a critical object for national security. And when, for some unknown reason, power surges occur in it, which can lead to the shutdown of individual air traffic control systems, then the FSB takes up the matter. But back to the mining. Recently, we have received several requests from customers with a request to explain how to detect the fact of using miners in a corporate or departmental network? Given the growing number of such issues, we decided to write this note.
To begin with, mining is not a typical threat to information security. Mining software cryptocurrency does not directly harm your information assets. No data theft or modification (usually). Interception management of technological or production processes, too. Accessibility violations? Probably too. But there is a braking computer, the load on the grid (and the company pays for electricity), the cost of Internet traffic (may be an actual problem with limited traffic) and a laptop battery dropping to zero, which you can try to translate into financial damage for the company (although this and not easy). The most annoying thing is that someone at your expense can profit and get fabulous profits (just look at the course of cryptocurrency to nervously bite your elbows and regret that conscience does not allow itself to be minted on corporate resources). But ... it also happens that mining accompanies malicious software, which makes it a more serious problem for information security specialists. In any case, one of the tasks of information security (and IT too) is to know what is happening on its farm and have the tools to control any activity, whether legal or not. Therefore, the issue of detection and, often, blocking miners, is becoming increasingly important.
If you read a lot of notes on the Internet about how to find a miner on your computer, then usually all the recommendations are reduced to one main thing - to pay attention to the inhibition of your PC, which is determined by the sensations or by using visual analysis of the task scheduler (Task manager in Windows or Activity monitor on MacOS), which displays CPU utilization for various applications and processes. However, this recommendation is more suitable for home users than for corporate users who cannot track the processor load of hundreds or thousands of computers. Therefore, we will try to look at the mining problem from a slightly different angle, or rather from the point of view of the so-called kill chain, which displays the set of steps that the intruder performs (his user, installing the miner to his PC, is also such) in the process of launching the mining software yourself on the site. If this is your user, then usually the sequence will be like this:
')
Unauthorized installation of the miner on the computer of an unsuspecting user looks a little different in the first and last stages of the kill chain:
In addition to the usual loading of the miner or the inclusion of mining functionality, for example, in the torrent client, various multi-pass schemes are also possible. For example, a non-malicious software first gets to the user's computer (and therefore it may not be detected by antivirus or security tools), which is loaded by a special downloader, which downloads the miner from the Internet and secretly installs it on an unsuspecting user’s computer. Please note that instead of the file being downloaded, this may be the script on the site you are visiting (the Coin Hive script is very popular).
A less popular, but also possible way is to get a miner on a computer through an attachment to an e-mail or a link in a letter, as well as through an advertising banner or a fake button on the site, clicking on which leads to downloading the miner to the computer. I would like to again draw your attention to the fact that the miner itself does not have malicious functions. Moreover, the user himself could legally install it. For this reason, in traditional antivirus software, this type of software is not blocked by default, but can only be detected (if the antivirus has the corresponding set of signatures).

Another important point is that the miner does not work alone. He is usually part of a whole botnet (pool of miners), with the command center of which he interacts - receiving commands or sending the results of his work. Therefore, a miner can be detected not only by its activity on the host, but also in the process of network interaction — after sending hashes or receiving new commands or data for calculations.
How does the Cisco company offer to fight with the mining software? Following our classic “ BEFORE - DURING - AFTER ” strategy, which takes into account the life cycle of an attack or other controlled activity, we propose to split all the control and protection measures into three parts:
At the first stage, in addition to standard recommendations for protecting end devices from malicious software, we advise you to configure network equipment, firewalls or Internet access controls to block access to mining sites. For example, to coin-hive.com or minergate.com. This can be done using Cisco ISR , Cisco Firepower , Cisco Web Security Appliance , Cisco Umbrella , Cisco ASA , etc. I will not give a ready list of such domains, since today there are already over a thousand mining pools and, given the increasing complexity of computational tasks, they will become more and more. Therefore, I would recommend to regularly monitor mining pools ratings, which can be freely found on the Internet. I will name only a few names:
You can track lists of pools at btc [.] Com and blockchain [.] Info. By the way, workers' access control to the last two domains (can be implemented via Firepower, Umbrella or Web Security Appliance with reference to user accounts) will let you know which of your users are interested in the subject of mining and are willing to try their hand at working with cryptocurrency, And this is important information to enhance future control.
Blocking access to the above-described domains will allow not only to prevent downloading of mining software (stage “TO”), but also to block interaction with pools in the case when the corresponding software somehow got on the user's computer (via attachment to e-mail , via a USB flash drive, with the help of malware or functionality in conditionally free software, in which mining is an imperceptible “load” or “price” for free) and tries to interact with them (stage “DURING”).
Unfortunately, we must admit that we cannot eliminate blocking access to mining pools - they appear all the time and keep track of them is not easy (remember, these are not malicious resources, the control of which is a top priority for Cisco Talos ). In addition, a user or malware can use tunneling (for example, SSH) or other methods of communication (for example, Tor) with appropriate pools. Therefore, we should be able to track the work of miners in real time (stage “IN TIME”). This can be done either by using the aforementioned interaction tracking with the relevant domains, or by tracking the ports that mining software uses to interact with pools and command centers. These ports include:
, . -, 8080 8081 — (Cisco Stealthwatch), HTTP ( Cisco Firepower, Cisco Cognitive Threat Analytics, Cisco AVC) DNS ( Cisco Umbrella). -, . -, . , Zotob 3333, , , . Cisco Firepower, Cisco ASA, Cisco Stealthwatch, Cisco ISR , , , , .
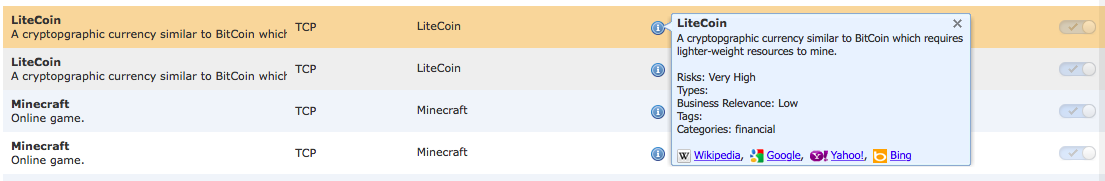
, Cisco Firepower , , , Bitcoin Litecoin. , ( , ), , . Cisco ISR AVC (Application Visibility and Control), , .
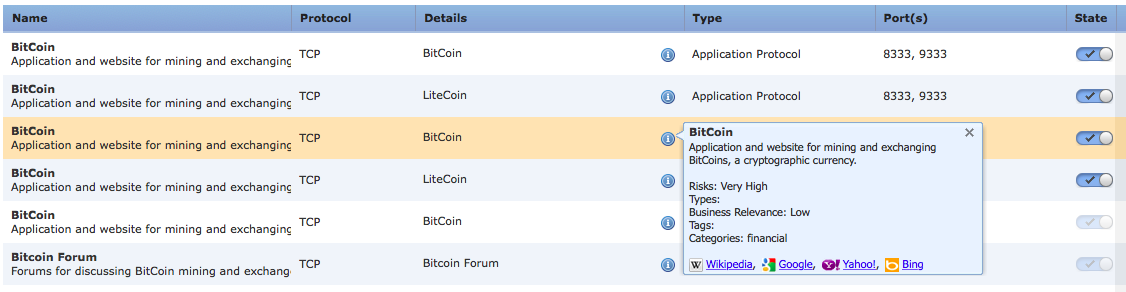
Cisco NGIPS , , . , SID 1-40840, 1-40841, 1-40842, Stratum . SID 1-31273 1-20057 , , (CoinMiner Win.Trojan.Vestecoin), . . , :
, . “ -? ? ?” .
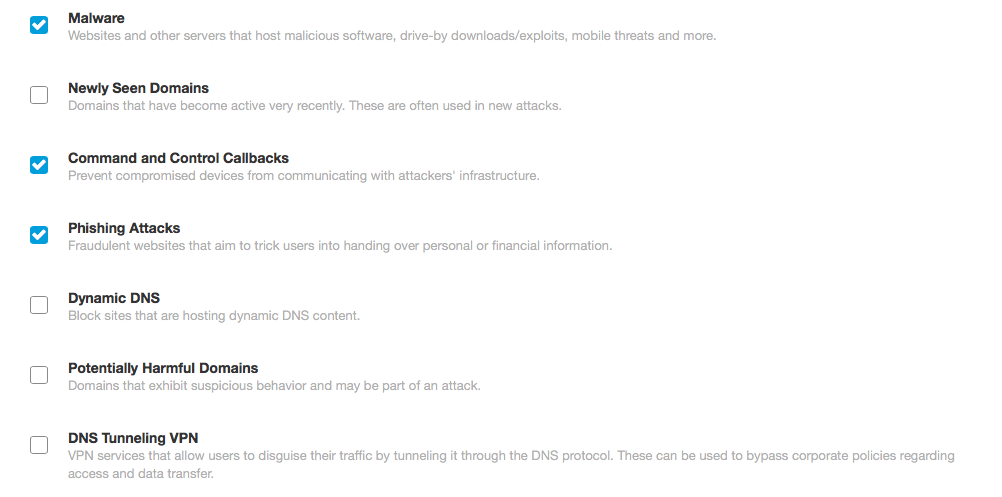
, , Cisco Cognitive Threat Analytics, Cisco Umbrella Cisco Web Security Appliance, . Cisco Umbrella / , IPS . Umbrella Potentially Harmful Domains.
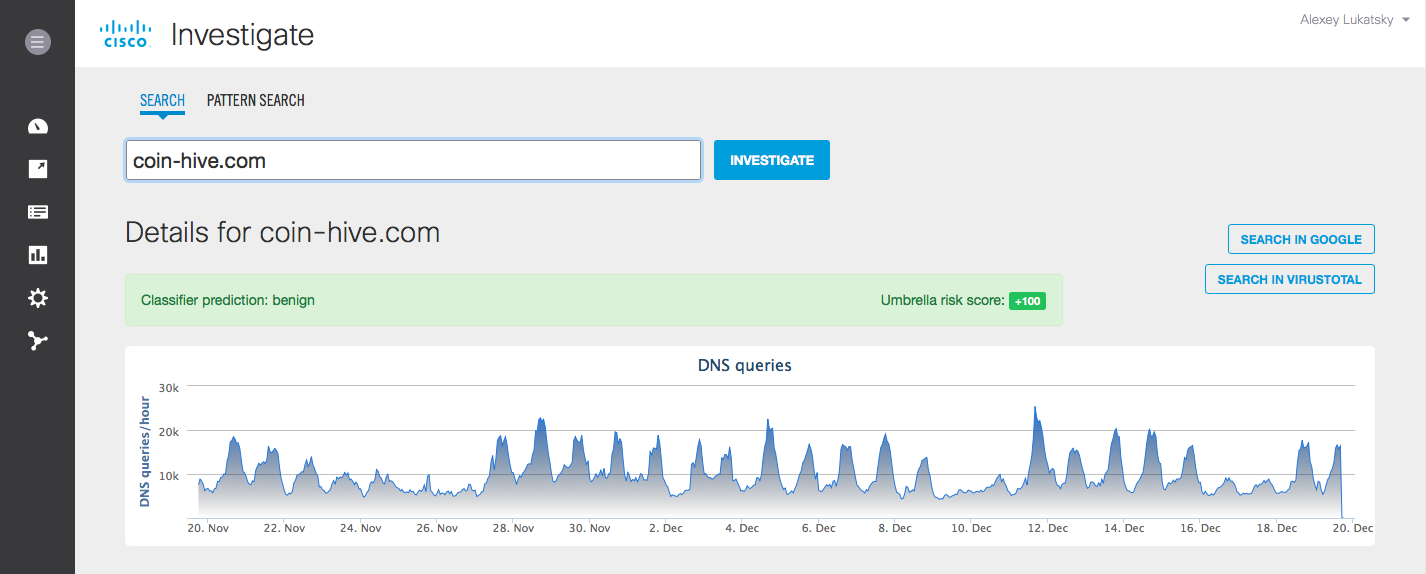
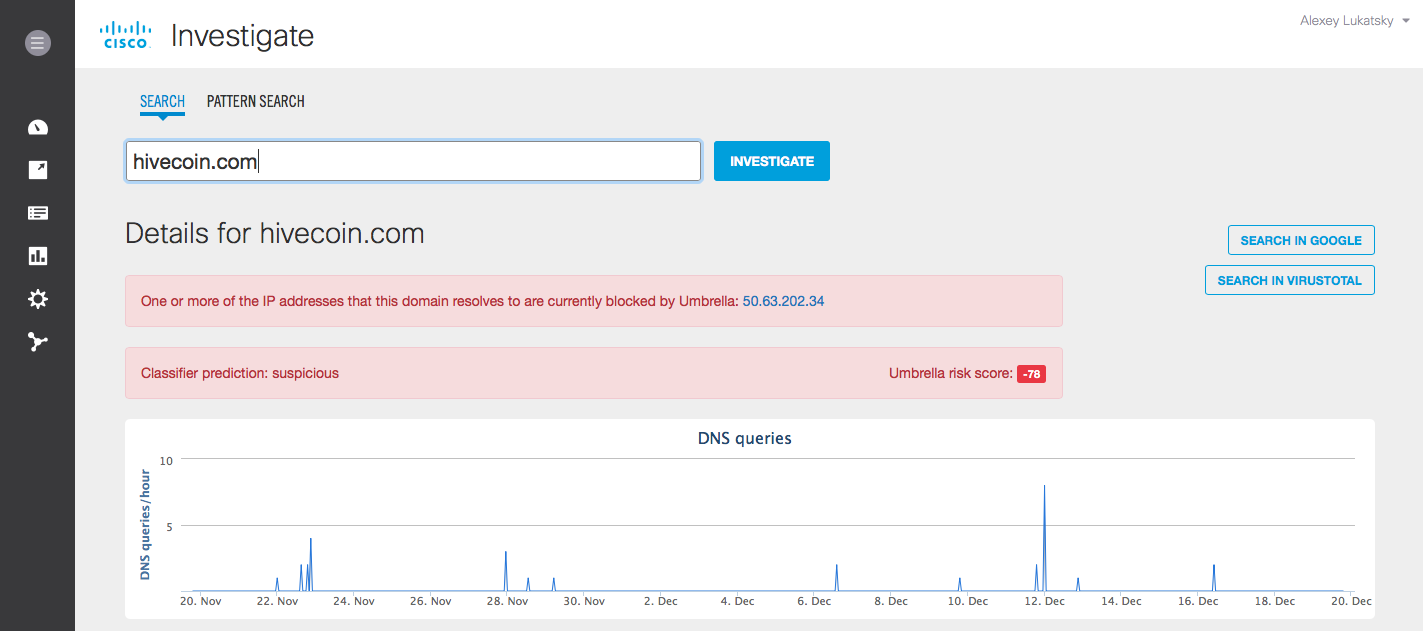
, , , , «» . , Cisco Umbrella Investigate , coin-hive, :
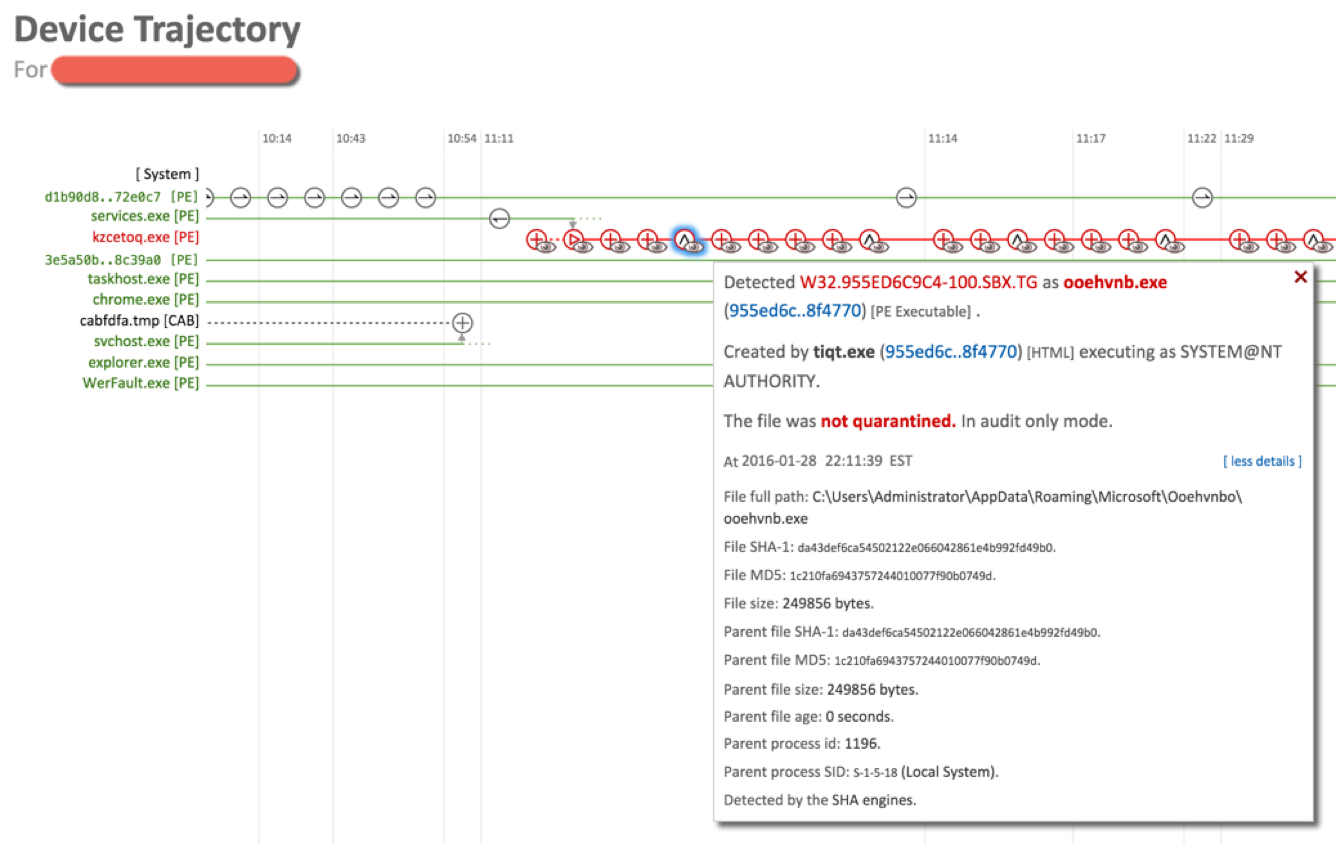
, , AMP for Endpoints, . , , — svchost.exe, chrome.exe steam.exe ( ). AMP4E, , , .
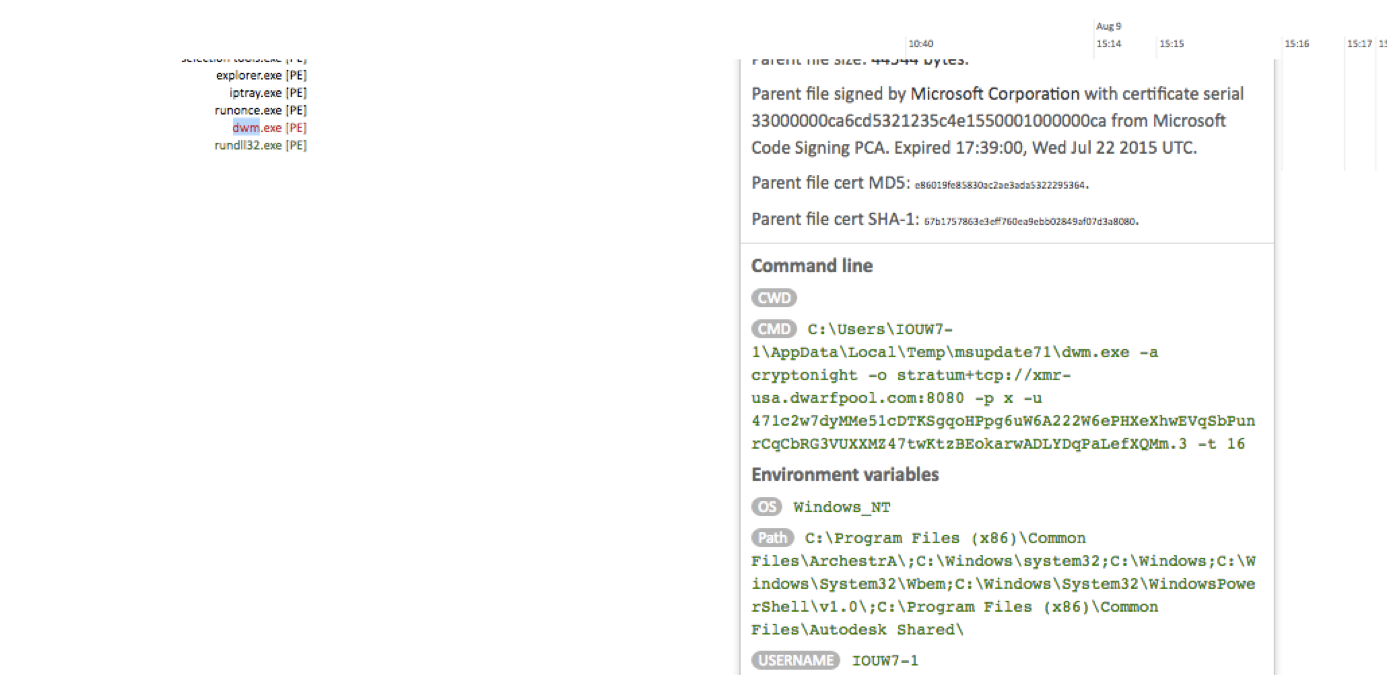
, W32.Cryptocurrencyminer, . , , , Virus Total, “ ”. , AMP4E , . “ ” (application white listening, AWL) “ ”, , . AMP4E , , .
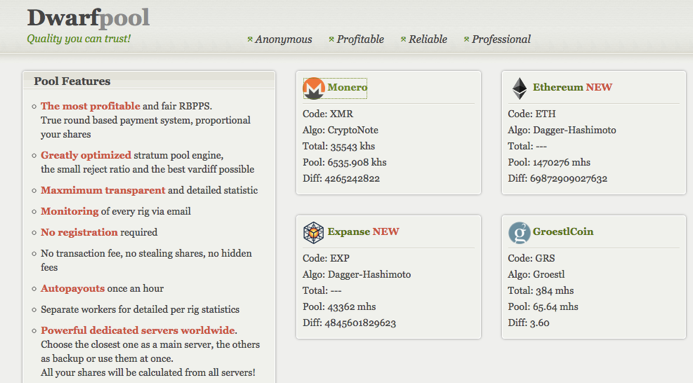
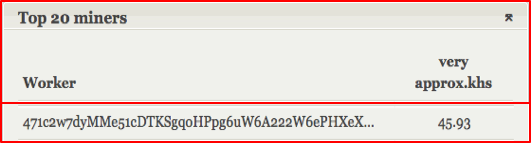
“”, , - - . , , Cisco AMP Threat Grid, , ( , Web, , , FTP ..), 700 . cryptominer-detected, cryptominer-network-detected cryptominer-pool-contacted, AMP Threat Grid :
, , . ? . , . — . , , , , , . . , . Cisco Cisco Talos, , , / , , , , , — Cisco Firepower, Cisco Umbrella, Cisco Stealthwatch, Cisco Web Security Appliance, Cisco AMP for Endpoints, Cisco Cognitive Threat Analytics, Cisco AMP Threat Grid .
, , , ( )- , (, NoScript Firefox, minerBlock No Coin Chrome), (, AdBlock), , , .
To begin with, mining is not a typical threat to information security. Mining software cryptocurrency does not directly harm your information assets. No data theft or modification (usually). Interception management of technological or production processes, too. Accessibility violations? Probably too. But there is a braking computer, the load on the grid (and the company pays for electricity), the cost of Internet traffic (may be an actual problem with limited traffic) and a laptop battery dropping to zero, which you can try to translate into financial damage for the company (although this and not easy). The most annoying thing is that someone at your expense can profit and get fabulous profits (just look at the course of cryptocurrency to nervously bite your elbows and regret that conscience does not allow itself to be minted on corporate resources). But ... it also happens that mining accompanies malicious software, which makes it a more serious problem for information security specialists. In any case, one of the tasks of information security (and IT too) is to know what is happening on its farm and have the tools to control any activity, whether legal or not. Therefore, the issue of detection and, often, blocking miners, is becoming increasingly important.
If you read a lot of notes on the Internet about how to find a miner on your computer, then usually all the recommendations are reduced to one main thing - to pay attention to the inhibition of your PC, which is determined by the sensations or by using visual analysis of the task scheduler (Task manager in Windows or Activity monitor on MacOS), which displays CPU utilization for various applications and processes. However, this recommendation is more suitable for home users than for corporate users who cannot track the processor load of hundreds or thousands of computers. Therefore, we will try to look at the mining problem from a slightly different angle, or rather from the point of view of the so-called kill chain, which displays the set of steps that the intruder performs (his user, installing the miner to his PC, is also such) in the process of launching the mining software yourself on the site. If this is your user, then usually the sequence will be like this:
')
- visiting mining sites
- downloading mining software
- installation software for mining
- running mining software
- mining
- interaction with miners' pools to exchange information on blocks and hashes received
- Remuneration
Unauthorized installation of the miner on the computer of an unsuspecting user looks a little different in the first and last stages of the kill chain:
- victim search
- preparing a bridgehead (introducing a mining script to the site, creating mining software, introducing mining software into any free or conditionally free or pirated software, introducing mining functionality into malware)
- “Infection” of the user by the mining software (via a script on the site, by downloading it from the Internet, by receiving it as an attachment to an email or on a flash drive)
- miner launch
- mining
- interaction with miners' pools or with the command center for the transfer of information obtained as a result of calculations.
In addition to the usual loading of the miner or the inclusion of mining functionality, for example, in the torrent client, various multi-pass schemes are also possible. For example, a non-malicious software first gets to the user's computer (and therefore it may not be detected by antivirus or security tools), which is loaded by a special downloader, which downloads the miner from the Internet and secretly installs it on an unsuspecting user’s computer. Please note that instead of the file being downloaded, this may be the script on the site you are visiting (the Coin Hive script is very popular).

A less popular, but also possible way is to get a miner on a computer through an attachment to an e-mail or a link in a letter, as well as through an advertising banner or a fake button on the site, clicking on which leads to downloading the miner to the computer. I would like to again draw your attention to the fact that the miner itself does not have malicious functions. Moreover, the user himself could legally install it. For this reason, in traditional antivirus software, this type of software is not blocked by default, but can only be detected (if the antivirus has the corresponding set of signatures).

Another important point is that the miner does not work alone. He is usually part of a whole botnet (pool of miners), with the command center of which he interacts - receiving commands or sending the results of his work. Therefore, a miner can be detected not only by its activity on the host, but also in the process of network interaction — after sending hashes or receiving new commands or data for calculations.
How does the Cisco company offer to fight with the mining software? Following our classic “ BEFORE - DURING - AFTER ” strategy, which takes into account the life cycle of an attack or other controlled activity, we propose to split all the control and protection measures into three parts:
- BEFORE - preventing interaction with sites for mining or miners getting into the network through various channels
- DURING - detection of installation and operation of mining software
- AFTER - conduct a retrospective analysis of the behavior of files that fall inside a corporate or departmental network.
At the first stage, in addition to standard recommendations for protecting end devices from malicious software, we advise you to configure network equipment, firewalls or Internet access controls to block access to mining sites. For example, to coin-hive.com or minergate.com. This can be done using Cisco ISR , Cisco Firepower , Cisco Web Security Appliance , Cisco Umbrella , Cisco ASA , etc. I will not give a ready list of such domains, since today there are already over a thousand mining pools and, given the increasing complexity of computational tasks, they will become more and more. Therefore, I would recommend to regularly monitor mining pools ratings, which can be freely found on the Internet. I will name only a few names:
- suprnova [.] cc,
- nanopool [.] org,
- zpool [.] ca,
- coinmime [.] pl,
- eth.pp [.] ua,
- zcash.flypool [.] org,
- dwarfpool [.] org,
- p2pool [.] org,
- bitclubnetwork [.] com,
- miningrigrentals [.] com,
- minergate [.] com,
- nicecash [.] com,
- hashing24 [.] com,
- hashcoin [.] io,
- hashflare [.] io,
- eobot [.] com,
- antpool [.] com,
- pool.btcchina [.] com,
- bw [.] com,
- mining.bitcoin [.] cz,
- eligius [.] st,
- ghash [.] io,
- bitminter [.] com,
- bitfury [.] org,
- kncminer [.] com,
- 21 [.] Co,
- slushpool [.] com, etc.
You can track lists of pools at btc [.] Com and blockchain [.] Info. By the way, workers' access control to the last two domains (can be implemented via Firepower, Umbrella or Web Security Appliance with reference to user accounts) will let you know which of your users are interested in the subject of mining and are willing to try their hand at working with cryptocurrency, And this is important information to enhance future control.
Blocking access to the above-described domains will allow not only to prevent downloading of mining software (stage “TO”), but also to block interaction with pools in the case when the corresponding software somehow got on the user's computer (via attachment to e-mail , via a USB flash drive, with the help of malware or functionality in conditionally free software, in which mining is an imperceptible “load” or “price” for free) and tries to interact with them (stage “DURING”).
Unfortunately, we must admit that we cannot eliminate blocking access to mining pools - they appear all the time and keep track of them is not easy (remember, these are not malicious resources, the control of which is a top priority for Cisco Talos ). In addition, a user or malware can use tunneling (for example, SSH) or other methods of communication (for example, Tor) with appropriate pools. Therefore, we should be able to track the work of miners in real time (stage “IN TIME”). This can be done either by using the aforementioned interaction tracking with the relevant domains, or by tracking the ports that mining software uses to interact with pools and command centers. These ports include:
- 3333 (bitcoin)
- 3336 (litecoin)
- 8333 (bitcoin)
- 8545 (Ethereum),
- 9333 (litecoin)
- 9999 (Dashcoin),
- 10034 (ypool.net)
- 22556 (Dogecoin),
- 30301 (Ethereum),
- 30303 (Ethereum),
- 45550 (bytecoin),
- 45560 (monero),
- 45620 (DigitalNote),
- 45570 (QuazarCoin),
- 45610 (Fantomcoin),
- 45640 (MonetaVerde),
- 45690 (Aeoncoin),
- 45720 (Dashcoin),
- 45750 (Infinium-8).
, . -, 8080 8081 — (Cisco Stealthwatch), HTTP ( Cisco Firepower, Cisco Cognitive Threat Analytics, Cisco AVC) DNS ( Cisco Umbrella). -, . -, . , Zotob 3333, , , . Cisco Firepower, Cisco ASA, Cisco Stealthwatch, Cisco ISR , , , , .

, Cisco Firepower , , , Bitcoin Litecoin. , ( , ), , . Cisco ISR AVC (Application Visibility and Control), , .

Cisco NGIPS , , . , SID 1-40840, 1-40841, 1-40842, Stratum . SID 1-31273 1-20057 , , (CoinMiner Win.Trojan.Vestecoin), . . , :
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"Possible Bitcoin/LiteCoin Mining"; flow:established; content:"|7B 22 70 61 72 61 6D 73 22 3A 20 5B 22|"; Depth:15; classtype:bad-unknown; reference:url,mining.bitcoin.cz/stratum-mining; sid:1000500; rev:1;)alert tcp $HOME_NET any -> $EXTERNAL_NET any (msg:"ET TROJAN W32/BitCoinMiner.MultiThreat Subscribe/Authorize Stratum Protocol Message"; flow:established,to_server; content:"{|22|id|22|"; depth:10; content:"|22|method|22 3A| |22|mining."; within:100; content:"|22|params|22|"; within:50; pcre:"/\x22mining\x2E(subscribe|authorize)\x22/"; classtype:trojan-activity; reference:url,talosintelligence.com/; reference:url,www.btcguild.com/new_protocol.php; reference:url,mining.bitcoin.cz/stratum-mining; sid:1000501; rev:1;), . “ -? ? ?” .
, , Cisco Cognitive Threat Analytics, Cisco Umbrella Cisco Web Security Appliance, . Cisco Umbrella / , IPS . Umbrella Potentially Harmful Domains.

, , , , «» . , Cisco Umbrella Investigate , coin-hive, :

, , AMP for Endpoints, . , , — svchost.exe, chrome.exe steam.exe ( ). AMP4E, , , .

, W32.Cryptocurrencyminer, . , , , Virus Total, “ ”. , AMP4E , . “ ” (application white listening, AWL) “ ”, , . AMP4E , , .



“”, , - - . , , Cisco AMP Threat Grid, , ( , Web, , , FTP ..), 700 . cryptominer-detected, cryptominer-network-detected cryptominer-pool-contacted, AMP Threat Grid :
- -
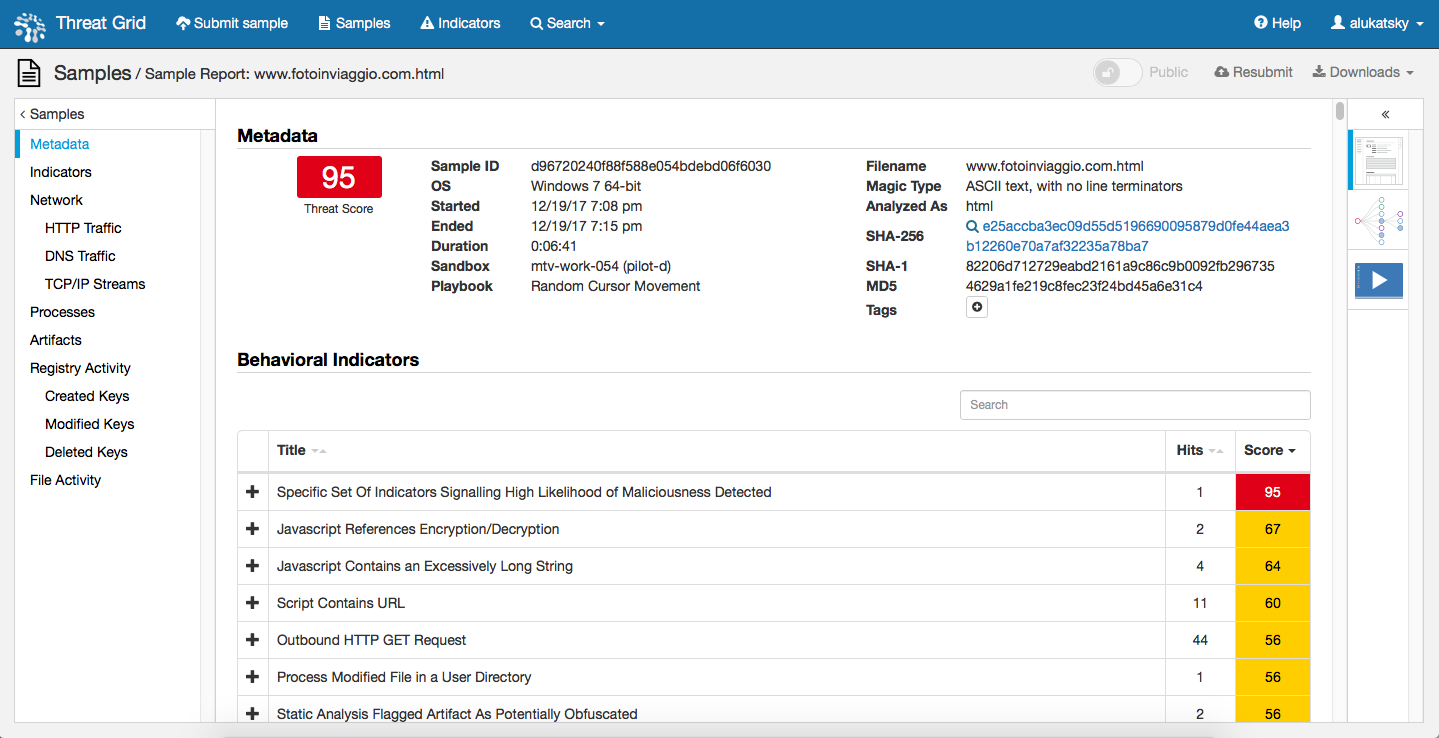
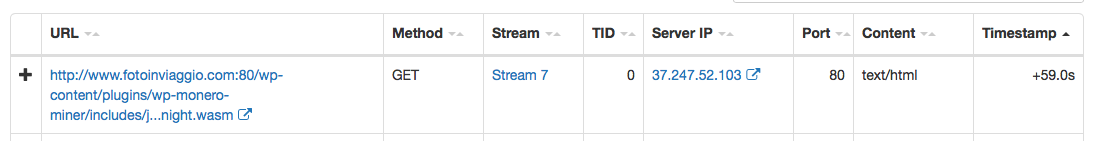
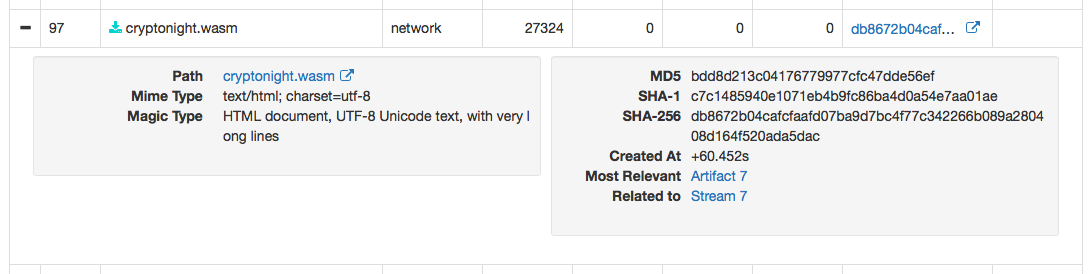
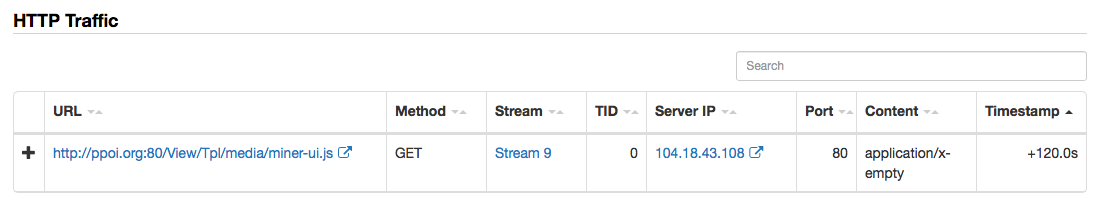

- .
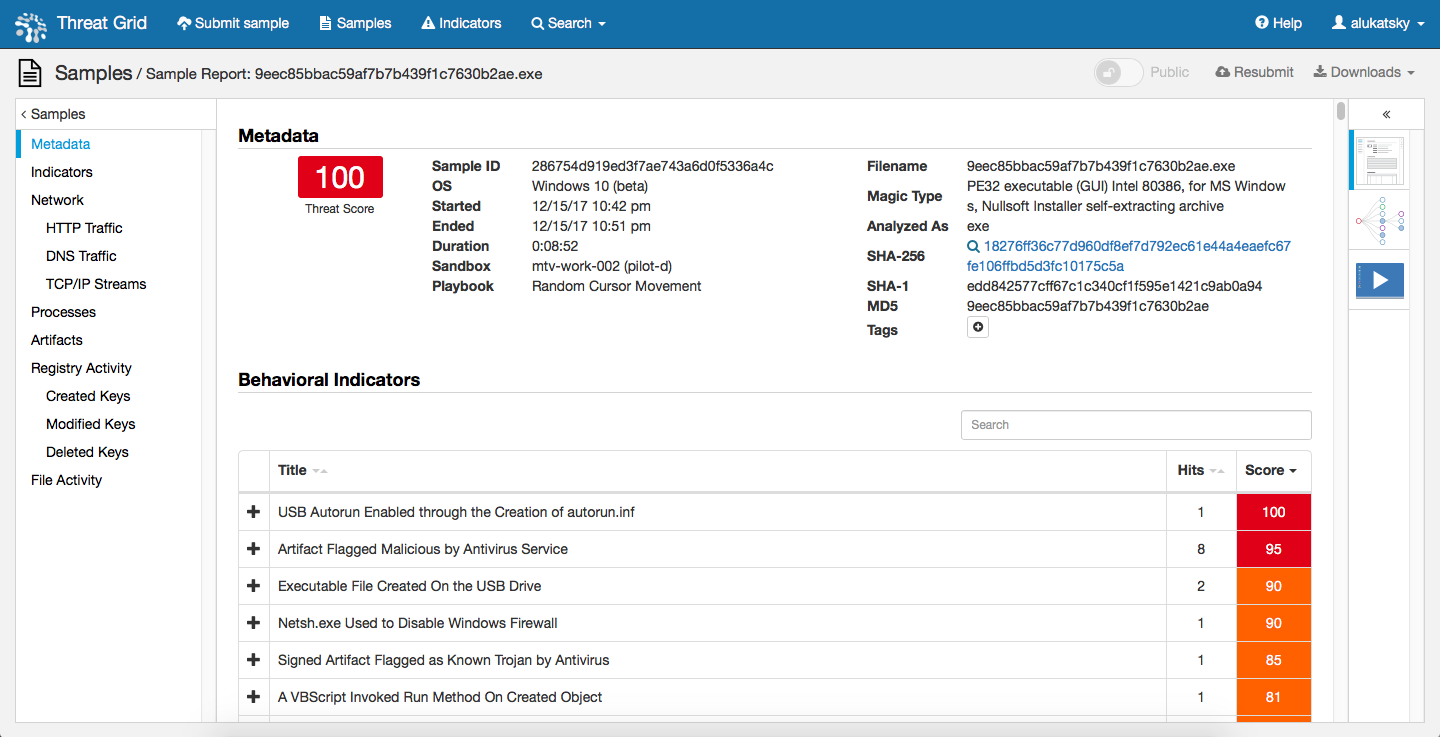
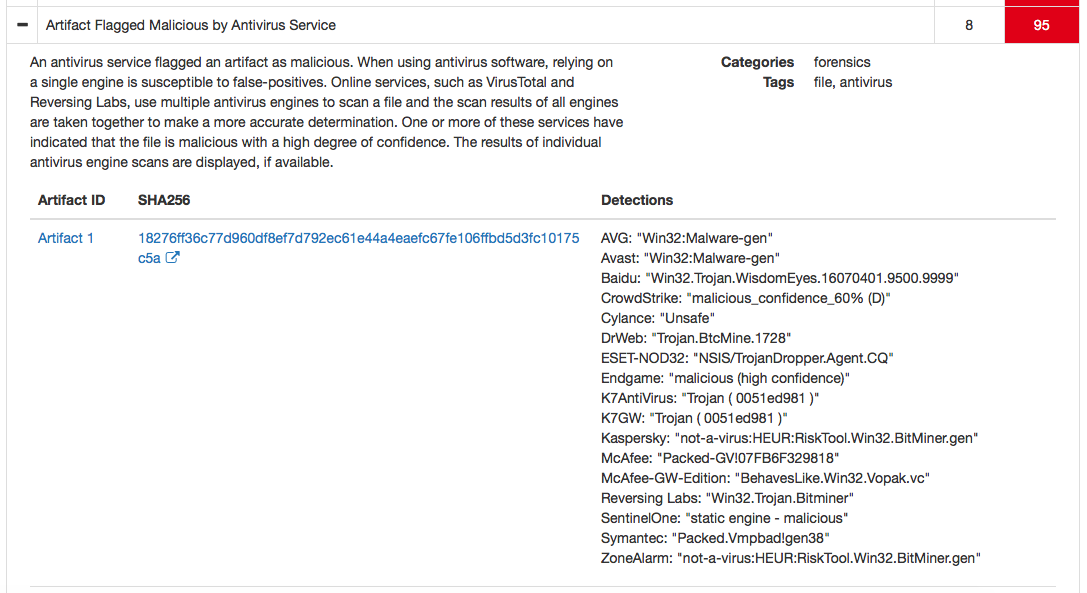
, , . ? . , . — . , , , , , . . , . Cisco Cisco Talos, , , / , , , , , — Cisco Firepower, Cisco Umbrella, Cisco Stealthwatch, Cisco Web Security Appliance, Cisco AMP for Endpoints, Cisco Cognitive Threat Analytics, Cisco AMP Threat Grid .
, , , ( )- , (, NoScript Firefox, minerBlock No Coin Chrome), (, AdBlock), , , .
Source: https://habr.com/ru/post/345200/
All Articles