Information security of bank non-cash payments. Part 2 - Typical IT infrastructure of the bank
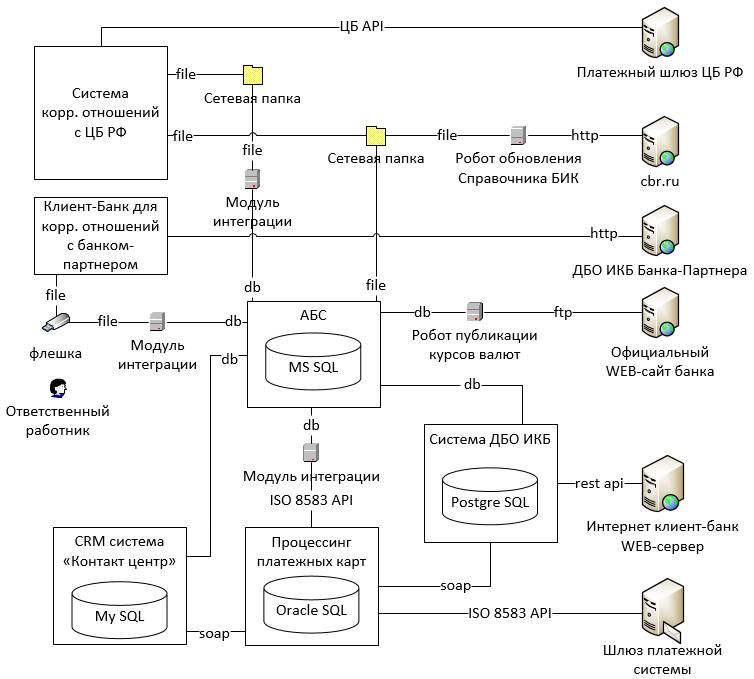
Fig. one.
What research
Links to other parts of the study
- Information security of bank non-cash payments. Part 1 - Economic fundamentals.
- Information security of bank non-cash payments. Part 2 - Typical IT infrastructure of the bank. ( You are here )
- Information security of bank non-cash payments. Part 3 - Formation of requirements for the protection system.
- Information security of bank non-cash payments. Part 4 - Overview of threat modeling standards.
- Information security of bank non-cash payments. Part 5 - 100+ thematic links about hacking banks.
- Information security of bank non-cash payments. Part 6 - Analysis of banking crimes.
- Information security of bank non-cash payments. Part 7 - The basic threat model.
- Information security of bank non-cash payments. Part 8 - Typical threat models.
In the first part of our study, we reviewed the operation of the system of banking non-cash payments from an economic point of view. Now it is time to look at the internal structure of the bank's IT infrastructure, through which these payments are realized.
Disclaimer
The article does not contain confidential information. All materials used are publicly available on the Internet, including on the website of the Bank of Russia.
Chapter 1. General Description of IT Infrastructure
Basic terms
In the 90s of the last century, the term “ automated system ” was often used in GOSTs and regulatory documents of the FSTEC of Russia (then still the State Technical Commission under the President of the Russian Federation). “GOST 34.003-90 Information Technology (IT). Set of standards for automated systems. Automated systems. Terms and definitions ” gives the following definition of this term:
automated system ; AC: A system consisting of personnel and a complex of automation equipment for its activities, implementing information technology for the performance of installed functions.
After some time, a new term came into use - the information system . In paragraph 3 of Art. 2 of the Federal Law of 27.07.2006 N 149- “On Information, Information Technologies and on Information Protection” this term is defined as follows:
information system - a set of information contained in databases and information technologies and technical means ensuring its processing;
As part of this study, both terms will be used interchangeably.
')
The validity of this approach can be proved by the fact that in the Order of the FSTEC of Russia of February 11, 2013 No. 17 “On Approving Requirements to Protect Information Not Containing State Secrets Contained in State Information Systems”, the state regulator to protect information systems requires the state systems to follow automated systems .
In addition to information systems , another type of element can be distinguished in the IT infrastructure of a bank - information services , or, as they are often called, robots.
It is quite difficult to define the concept of an information service , so we simply list its main differences from the information system :
- An information service is much simpler than an information system , but at the same time it cannot be called a component of the latter, since several information systems can use the results of its work simultaneously.
- Information services are designed to automate simple, routine tasks.
- Information services do not contain databases.
- Information services operate automatically without participation (or with minimal participation) of a person.
Automated Banking System
The core of the information infrastructure of any bank is an automated banking system or abbreviated ABS .
Standard of the Bank of Russia STO BR IBBS-1.0-2014 “Ensuring the information security of organizations of the banking system of the Russian Federation. General Provisions ” defines the ABS as follows:
automated system that implements the banking process.
This definition allows you to bring under him almost any IT-system in the bank. At the same time, ordinary bank employees call the ABS the system that deals with accounting for bank accounts, transactions between them (cash flow) and balances. The second definition does not contradict the first and details it more clearly, and we will continue to use it.
In modern Russian banks the most common are the following ABS :
Some, especially large banks use not ABS , but specially designed ABS . But such cases are rare, in fact, as well as especially large banks.
Sometimes banks use several ABS systems from different manufacturers in parallel. Often this happens when a bank tries to switch from one ABS to another, but less trivial reasons are possible.
Applied Information Systems
Despite the fact that the ABS automates a fairly large number of tasks, it does not cover all the needs of the bank. There are tasks that the ABS does not do at all or does not do it the way the bank wants. Therefore, other information systems that automate individual business processes are connected to the ABS . In the future, such information systems will be referred to as applied information systems .
Examples of applied information systems include:
- remote banking services of Internet Client-Bank ( RB RBB , for example, iBank2 , BS-Client , InterBank ),
- payment card processing (for example, TranzWare , SmartVista , Way4 ),
- contact center automation systems (for example, Avaya Call Center , Cisco Unified Contact Center ),
- automatic scoring system for borrowers (for example, FICO ),
- and etc.
Depending on the size of the bank and the services it provides, the number of application information systems can be measured in quantities from units to hundreds.
Infrastructure Information Systems
In addition to the ABS and applied information systems that automate basic business processes, banks also have a decent amount of supporting infrastructure information systems . Examples of such systems can be:
- Active Directory directory service
- Domain Name Service (DNS)
- corporate email,
- Internet access services;
- access control systems (ACS) in the premises;
- IP video surveillance;
- IP telephony;
- and much more.
Information Services
Banks use a huge number of various information services that perform simple, routine functions, for example, downloading BIC and FIAS directories, publishing currency rates on the official website, etc.
Client parts of third-party information systems
Separate mention is made of client parts of information systems external to the bank. I will give as examples:
- modules for integration with state information systems: GIS GMP , GIS Housing and Communal Services ;
- client parts of external payment systems;
- exchange trading terminals;
- and so on.
Typical ways of integrating information systems
The following mechanisms are commonly used to integrate information systems :
- Integration via API (for example, Web services).
- Integration through the DBMS:
- by providing access only to stored procedures;
- by providing access to stored procedures and database tables.
- File sharing:
- through a computer network;
- through alienable computer storage media (OMNI, for example - flash drives).
- Implementing a service oriented architecture (SoA) .
Integration modules
The module of integration is understood as a virtual element of the IT infrastructure that implements the integration of other elements of the IT infrastructure.
We called this element virtual, because its functionality can be implemented both as a separate specialized element of the IT infrastructure (for example, an information service ) and as components of integrable information systems . Moreover, even a person who “manually” transfers information between integrated information systems can act as an integration module.
Bank IT infrastructure example
In Figure 1, you can see a fragment of a typical bank information infrastructure containing the types of elements discussed above.
Chapter 2. Non-cash settlement infrastructure
If you look at this scheme ( Fig. 1 ) from the point of view of cashless payments, you can see that the bank implements them with the help of:
- direct correspondent relations with a partner bank,
- international payment system (MPS) (for example, VISA , MasterCard ).
- correspondent relations with the Bank of Russia.
Technically direct correspondent relations with partner banks can be organized using:
- conventional DBO IKB systems used by banks to serve legal entities (in this example ( Figure 1 ) this method is used);
- interbank payment systems (for example, SWIFT );
- specialized messaging systems (for example, REX400 , TELEX );
- specialized software developed by one of the interacting banks.
Connection to payment systems serving plastic cards is carried out through standard modules included in the processing systems.
For the successful operation of the bank is obliged to ensure the information security of all these methods of making payments. Considering them within the framework of one, even large research is very problematic, and therefore we will concentrate only on one of the most critical, in terms of possible losses, direction - the payment interaction of the bank with the Bank of Russia.
Infrastructure for providing payment interaction with the Bank of Russia
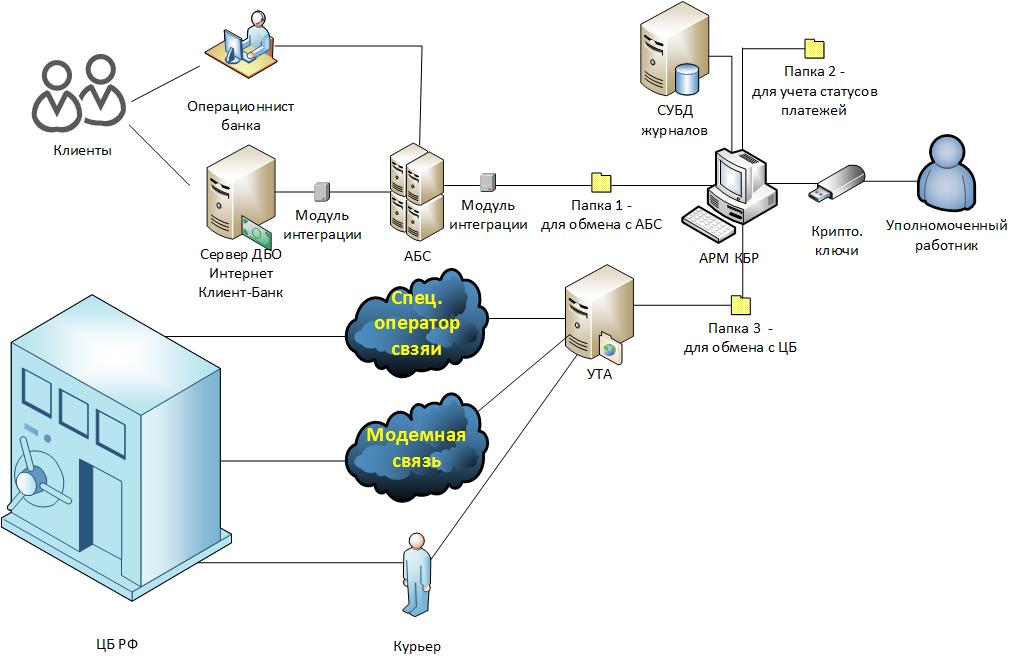
Fig. 2
The IT infrastructure of the bank’s payment interaction with the Bank of Russia will be considered on the basis of the execution of a payment sent to a client of another bank.
As we remember from the first part , the client must first transfer the payment order to the bank. He can do this in two ways:
- To appear in person at the bank and submit the certified payment order on paper.
- Send the payment order through the RB of SB system.
It is important to note here that DBO IKB systems are only systems providing legally significant electronic document flow between a client and a bank; they do not make payments on their own. That is why, when a client opens a bank account, he usually concludes two contracts. The first is a bank account maintenance agreement, the second is an agreement for the implementation of electronic document circulation using the RB of SB system. If the second contract is not concluded, the client will still be able to use his account, but only during a personal visit to a bank branch.
If the client has submitted the payment order on paper, the employee of the bank on its basis makes an electronic payment order in the ABS . If the order was submitted through the DBE IKB , then through the integration module it enters the ABS automatically.
The proof that the client made an order to transfer funds in the first case is a paper document that he personally signed, and in the second, an electronic document in the RB of the IKB , certified in accordance with the agreement.
Usually, for certifying electronic documents of clients - legal entities in the RB of the IKB, a cryptographic electronic signature is used, and for documents of clients - individuals - SMS confirmation codes. From a legal point of view, banks usually use the legal regime of a handwritten signature analogue (HSA) to certify electronic documents in both cases.
Once in the ABS , the payment order in accordance with the internal regulations of the bank is monitored and transmitted for execution to the Bank of Russia payment system.
Technical means of interaction with the payment system of the Bank of Russia
Technical means (software) used to interact with the payment system of the Bank of Russia may vary depending on the territorial institution of the Bank of Russia serving the correspondent. bank account.
For banks serviced in the Moscow region, the following software is applied:
- ARM KBR - automated workplace of the client of the Bank of Russia;
- UTA - special software for file interaction between a client of the Bank of Russia (universal transport adapter);
- SCAD Signature - a means of cryptographic information protection (SKZI) "Signature-client hardware and software complex" version 5, certificates of the Federal Security Service of Russia - SF / 114-2680 (KS1 cryptographic protection level) KS2). SCAD stands for a system of cryptographic authentication of documents.
ARM CBD
The AWS of the CBD is software with the help of which authorized employees of the bank encrypt and digitally sign outgoing payment documents, as well as decrypt and verify the electronic signature of payment documents received from the Bank of Russia. But, to be more precise, the CBD AWP in its work operates not with payment documents, but with electronic messages (ES), which are of two types:
- electronic payment messages (EPS), for example, ED101 “Payment Order”;
- electronic service reports (ESIS), for example, ED201 "Notification of the results of monitoring of ES."
The list and formats of electronic messages are established by the Bank of Russia, through the release of the Album of Unified Forms of Electronic Bank Messages (UFEM) .
In order for the CBD AWP to process a payment, it must be converted to a file containing an electronic billing message of the format of UEFEBS. For such a transformation, the ABS integration module with the Bank of Russia payment system is responsible. From a technical point of view, such transformations are quite simple, since the format of the VEBBS is based on XML .
E-mail files leave the ABS integration module in open form and are placed in a special file system folder (usually a network folder), which is configured in the CBMW for e-mail messages that have the “Entered” status. In the previously presented diagram ( Fig. 2. ) this folder is designated as “Folder 1”.
Then, in the course of processing, electronic messages change their status to “Monitored”, “Sent”, etc., which is technically implemented by moving the file with the electronic message to the appropriate folders that are configured in the AWS of the CBD . In the diagram ( Fig. 2. ) these folders are designated as “Folder 2”.
At a certain moment of technological processing (established by the internal regulations of the bank) outgoing electronic messages they are encrypted and signed with an electronic signature using SCAD Signature and private cryptographic keys of responsible employees.
SCUD Signature
SCAD Signature is a SKZI developed by Validata LLC at the request of the Bank of Russia and intended to protect information in the payment system of the Bank of Russia. This CIPF is not publicly available (except for the documentation posted on the website of the Central Bank of the Russian Federation), and it is distributed by the Bank of Russia only among the participants of its payment system. The distinctive features of this SKZI include:
- This SKPI, in contrast to other SKZI common in Russian business circles (for example, as Crypto-PRO CSP , VIPNET CSP , etc.), implements its own public key infrastructure (PKI), which is isolated from the operating system. This is manifested in the fact that a public key directory containing certificates, a list of trusted certificates, a list of revoked certificates, etc. is cryptographically protected on the user's private key, which prevents an attacker from making changes to it, for example, installing a trusted certificate without the user's knowledge .
Note. SKZI Verba-OW implements a similar key model. - The following feature follows from the previous one. In SKZI, in order to make working keys, you must first create a certificate directory using special registration keys. When the working keys expire, new ones are generated, but in order to generate them, you need to have valid previous working keys. The keys are created according to a decentralized scheme with the participation of the Bank of Russia as a Certification Center .
- SKZI supports work with functionally-key carriers ( vdToken ), which perform the functions of electronic signature and encryption on board, without transferring private keys to computer memory.
- The cryptographic keys used to interact with the payment system of the Bank of Russia are of two types:
- “Encryption only” - allows you to encrypt / decrypt email messages.
- "Encryption and signature" - do the same thing as in the first case, and also allow you to sign e-mails.
UTA
Encrypted and signed e-mails are placed in a special folder, in the diagram ( Fig. 2. ) this is “Folder 3”. UTA continuously monitors this folder and, if it sees new files there, sends them to the CBR in one of the following ways:
- "On the Internet", although in fact it is not quite so. Instead, the Internet is used by a specialized telecom operator that provides dedicated communication channels to the Central Bank of the Russian Federation, but since the IP network is addressable, it is said that the sending is via the Internet.
- "By modem." In case of an accident of the first type of connection, there is a reserve in the form of a modem connection via the public telephone network.
- In case of failure of all communication channels, delivery of electronic messages to OMNI (alienable machine data carrier) is provided by courier. Incidentally, this is one of the ways in which banks with a revoked license make payments during their liquidation.
Having reached the Central Bank (first or second method), the UTA transmits electronic messages through the published Central Bank API. During the communication sessions, the UTA also receives input e-mails from the Central Bank .
It should be noted that all e-mails with which UTA works are encrypted and signed with an electronic signature.
After receiving the encrypted e-mail, UTA shifts it to the folder with the incoming encrypted messages. An authorized worker, using his crypto keys and the CBMWWSD, verifies the electronic signature and decrypts the message.
Further processing is performed depending on the type of e-mail. If this is a payment message, then it is transmitted through the integration module to the ABS , where, on its basis, accounting entries are made that change account balances. It is important to note that the interaction of the ABS (integration module) and the AWS of the CBD uses standard format files in open form.
In the course of its operation, the AWS of the CBD maintains a journal of its work, which can be implemented as text files or with the help of databases that are managed by a DBMS.
Alternative processing schemes
We reviewed the "classic" scheme of the system. In reality, there are many varieties of it. Consider some of them.
Variety 1. Separation of the contours of sending and receiving messages
A scheme with two AWP of the CBD is being implemented. The first works with the participation of a person and only sends messages, the second works in automatic mode and only receives messages.
Variety 2. Full Automatic
ARM CBD is configured to work fully automatically without human intervention.
Variety 3. Isolated AWP CBD
ARM CBD functions as a dedicated computer that is not connected to the bank’s network. Electronic messages are transmitted to him by a human operator using OMNI.
Transfer of electronic signature from ARM CBD to ABS
The Bank of Russia plans to switch to a new technological payment processing scheme, in which electronic messages will be signed not in the AWS of the CBD , as it was before, but in the ABS (more precisely in the ABS integration module - the AWS of the CBD ).
To implement this approach, a new version of the AWS of the CBD has been released , which has become known as the AWP of the CBD-N (new). All major changes can be seen by comparing the schemes of information flows passing through the AWS of the CBD of the old and the new versions.
Consider the scheme of information flows in the classical ARM of the CBD. The source of the scheme is the official documentation on the AWS of the CBD “AUTOMATED WORKING PLACE OF THE CUSTOMER OF THE BANK OF RUSSIA. Programmer's Guide. TsBRF.61209-04 33 01 ".
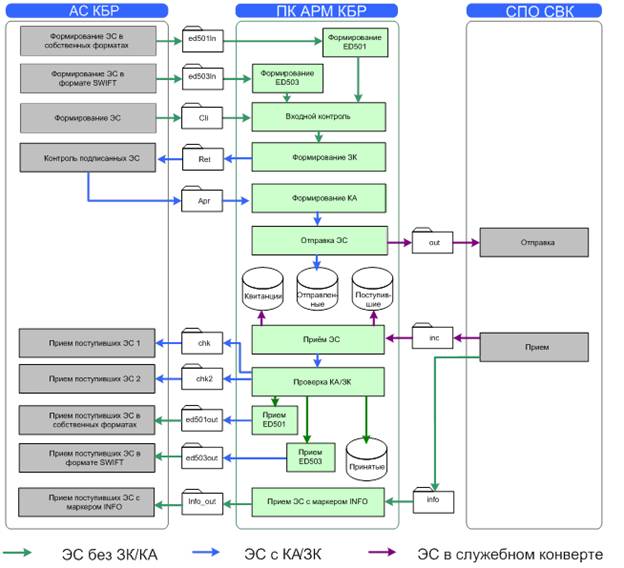
Fig. 3
Notes.
- The symbol "AC KBR" (automated system of the client of the Bank of Russia) corresponds to the symbol ABS in the previous schemes.
- The symbol "SPO SVK" corresponds to the symbol UTA in the previous schemes.
- KA - authentication code (electronic signature) of the electronic message.
- ZK - the security code is another type of electronic signature, but unlike the SC, which is formed by the original message without changes, the ZK is formed only under meaningful data without counting markup. For more information about the technical nuances of the spacecraft and spacecraft, you can read the documentation of the UVEBS "Protection of electronic messages (ES packets)". From a legal point of view, LC is a technological measure of information security, while a satellite, according to the contracts and rules of the payment system of the Bank of Russia, is recognized as an electronic signature.
Now let's take a look at a similar scheme for the new AWP CBD-N. The source “AUTOMATED WORKING PLACE OF THE CUSTOMER OF THE BANK OF RUSSIA NEW. Programmer's Guide. TsBRF.61289-01 33 01 "

Fig. four.
From the point of view of cryptography, the AWS CBD-N is responsible for encrypting / decrypting electronic messages, as well as for verifying electronic signatures on them. Electronic signature generation has been transferred to the ABS integration module.
It is logical to assume that this module will also have to check signatures for messages received from the AWS KBR-N . From a technical point of view, this is not mandatory, but from a safety point of view, it is of critical importance, since it ensures the integrity of messages transmitted between the ABS and the AWS KBR-N .
In addition to the file interface of interaction between the ABS , AWS KBR-N and UTA , the IBM WebSphere MQ interface has been added, which allows building the bank’s service-oriented IT infrastructure and solving the problem of the old scheme with the organization of simultaneous operation of several operators responsible for sending payments.
Conclusion
We reviewed the internal structure of the bank’s IT payment infrastructure. In the following sections, we will look at the information security threats that arise here.
Source: https://habr.com/ru/post/345194/
All Articles