Hippocratic Oath or how to protect information in medical institutions

No wonder someone once said: “Who owns information, he owns the world” - because with the advent of the Internet, information technologies and their development, information has ceased to have borders, and each of us can easily find what is necessary. However, one cannot do without the reverse side of the medal - information can always be used for personal gain, someone wants to own information that does not belong to him and use it either for his own personal gain, or to blackmail or harm other people.
Problem
Sharp digitization of information in the health sector has improved medical services; However, this development has a dangerous side effect: information security risk. In 2016, information security breaches in the health sector affected more than 27 million patient records. In the next few years, the number of thefts will only increase.
Strategies that are designed to protect patient data should not only respond and protect the data, but also anticipate and prevent any offensive actions committed by cybercriminals.
')
Hackers are always busy "pumping" their methods and approaches. They use various ways to identify and use even the smallest loopholes in your systems and networks.
Patient data is very useful for hackers. They can sell stolen data on the black market , use it in fraud, sell it to foreign agencies, sell information about the patient’s identity to other criminals, and use the data in illegal financial transactions.
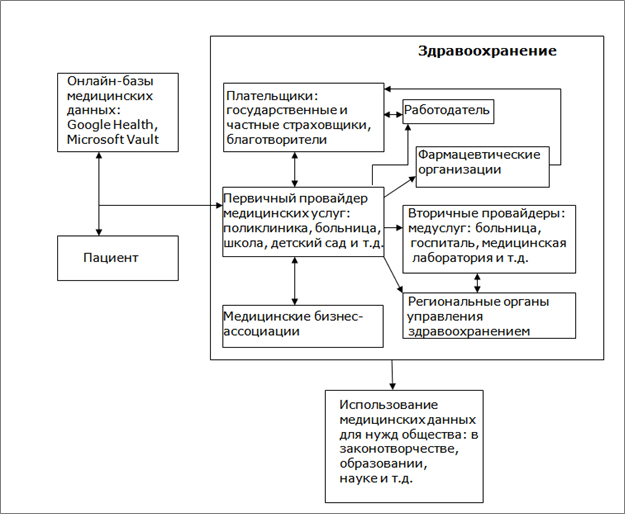
Medical Data Flow Diagram
Cases of theft of personal data
In Israel, there was a massive theft of data from patients in hospitals and clinics.
At one of the sites of the Altai Territory, personal data of patients appeared in open access: names, places of residence, information about the diagnosis.
Lithuanian special services are investigating a computer hacking of a plastic surgery clinic - hackers have stolen photographs and personal data from a database.
But the question is: why should domestic hackers hack Russian hospital systems if they are not interested in tax fraudsters like in the USA? Information such fraudsters will use for phone phishing. The banal blackmailing of the patient is still relevant (the threat of disclosure of information). Organizations can also be blackmailed (the threat of prosecution of a company that has leaked from patients). Unfortunately, stolen medical information, unlike stolen banking information, does not have a statute of limitations.
What to do with it all?
Of course, there is no universal method or program that will protect the information system and fully protect it. However, a complex of methods is more likely to secure information systems located in medical institutions.
Western colleagues offer to hire specialists who will lead the security department, abbreviated CSO (Chief Security Officer). Such specialists must undergo testing and certification for compliance of the protection system with regulatory requirements. In our country, such checks are carried out by the FSTEC - Federal Service for Technical and Export Control.
The use of various strategies also helps prevent breaches and theft of health data. One of the current technologies for information security is VDI technology .
With the help of the program, it is possible to create a virtual IT infrastructure and full-fledged workplaces on the basis of a single server that is running many virtual machines. The main advantage and factor influencing the choice of VDI technology is safety. The security level is so high that the user will not be able to copy patient data onto a flash drive and take it outside VDI. Health care providers can access patient information from the cloud without downloading and saving it directly to a computer.
VDI technology is a foreign development, but for several years now it has been successfully used in our country in various fields, including medicine.
Another method of protection is blockchain technology.
A large number of patients visit medical facilities, tons of papers and medical records are used for this. What if all this information, which is gathering dust on the shelves, would be stored in a single form and place online? Perhaps this would be a big step forward in total healthcare.
Blockchain technology is the way to solve this problem, to provide such an easily accessible and safe online catalog. The technology allows for anonymity in use. In health care, this technology may be applicable for data storage. In this area there is a contradiction between the confidentiality of personal data and the need for access to a doctor in case of emergency. The technology is capable of providing secure database management.
What in practice?
In Russia, there are attempts to create a unified state health information system (EGISZ).
Within the framework of the EGISZ project, work is being done to equip medical institutions with computer, telecommunication equipment and information security tools, create regional healthcare modernization programs, information exchange standards within the system, requirements for medical information systems, and create a federal data center with system-wide and applied components.
Legislative regulation - FZ-152 as the basis
Federal Law No. 152- “On the protection of personal data” is a document that regulates the provision of information security in medicine. Medical institutions are operators of personal data, therefore, ensuring the security of this data is their area of responsibility.
There are also a number of regulatory and procedural documents initiated, for example, by the FSB and the FSTEC of Russia . According to the methods and procedures prescribed in them, the security of personal data is ensured, including in health care.
The financial side of the issue
Abroad, information security costs are significant: hiring information security specialists, installing and maintaining information protection systems against external and internal threats, and staff training. In Russia, a particularly large budget is not allocated, and the municipal hospital alone cannot afford such luxury .
Total
As already mentioned, there is no universal software or technology that will provide 100% data protection, but it is important to understand that leaving the data system without protection is simply impermissible and reckless. The risk of cyber attacks is no longer the concern of just one IT department. Currently, this is a key issue that should be considered by the management of medical institutions.
The scope of medical services should not bypass the protection of patient data, and all that is associated with this specificity. The state, as if it did not want to, should allocate funds for data protection, if it wants the country to automate medicine. As they say: "You love to ride, love and sleigh to carry . " Without this, alas, no way.
Source: https://habr.com/ru/post/345080/
All Articles