How did I manage to hack the application
Hello dear% habrauser%. In this article, I will share with you the story of how I hacked the application. The application EXE itself cannot be cracked, but the desired result was obtained in another way. To preserve confidentiality, I will omit some points, cut screenshots strongly. So

It all started well, nothing foreshadowed trouble. In one late evening, one good friend asked me for one favor, using phrases like "well, you have a programmer." He wrote about a request to hack a certain application. To which I replied that I would try, but I cannot guarantee successful hacking. The next day we met, he gave me a disk and explained what kind of application it was.
There is a certain organization that trains people to pass one specific exam. To get this application you need to go to this organization, register and pay for courses. At the end of the course, the organization for an additional fee gives a disk with the installer of the program with an individual activation key. The application allows you to do tests, look at the results. There is a mode "On the exam", which allows you to simulate the exam environment. The application gives random tests from different sections. Everything is good and beautiful.
')
Install the application, run it to see what it is.
This splash screen opens, and the application freezes for a few seconds (this freeze is not casual).
Splash screen opens, and after it, after a few seconds, this window opens:
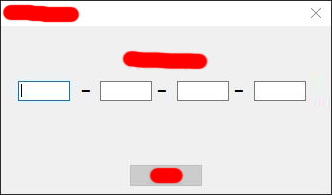
We are required to enter the activation key, which we naturally do not have. The first thing that alerted me was that the activation key input window opens with a noticeable delay, as if the application is connected somewhere via the Internet and the application developer did not take care of the asynchronous connection to the Internet. To make sure that the application climbs to the Internet has disconnected the network connections on the computer,pulled out the ethernet cable and re-launched the application. After some time, thinking about being human, the application still opened the activation window, but after entering a random text there, a message appeared saying that there was no internet connection.
From here we conclude that the application is activated via the Internet and in its source code no activation keys or decryption algorithms are wired.
I climb into the folder of the installed program:
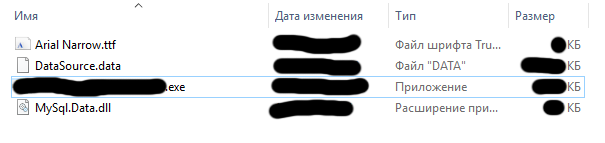
Structure:
The presence of MySql.Data.dll in the program folder suggested that the application is most likely written in C #. Not protected by special utilities, applications written in this programming language are the easiest to decompile. Delighted by this assumption, my brain automatically gave me a signal to start the program IlSpy , which allows me to decompile applications written in C # and open the application in it.
As a result, such a picture opened before me.
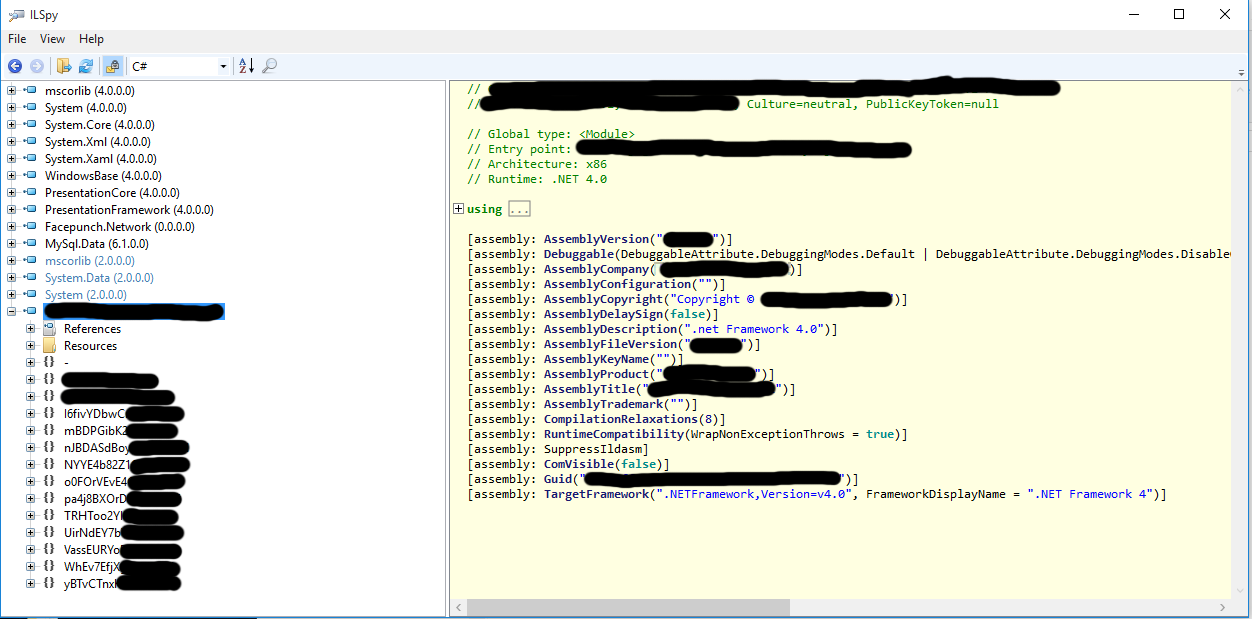
As you can see, the application is really written in C #, it displays information about the developer, the version of .NET used. After opening the structure of the application, disappointment followed.
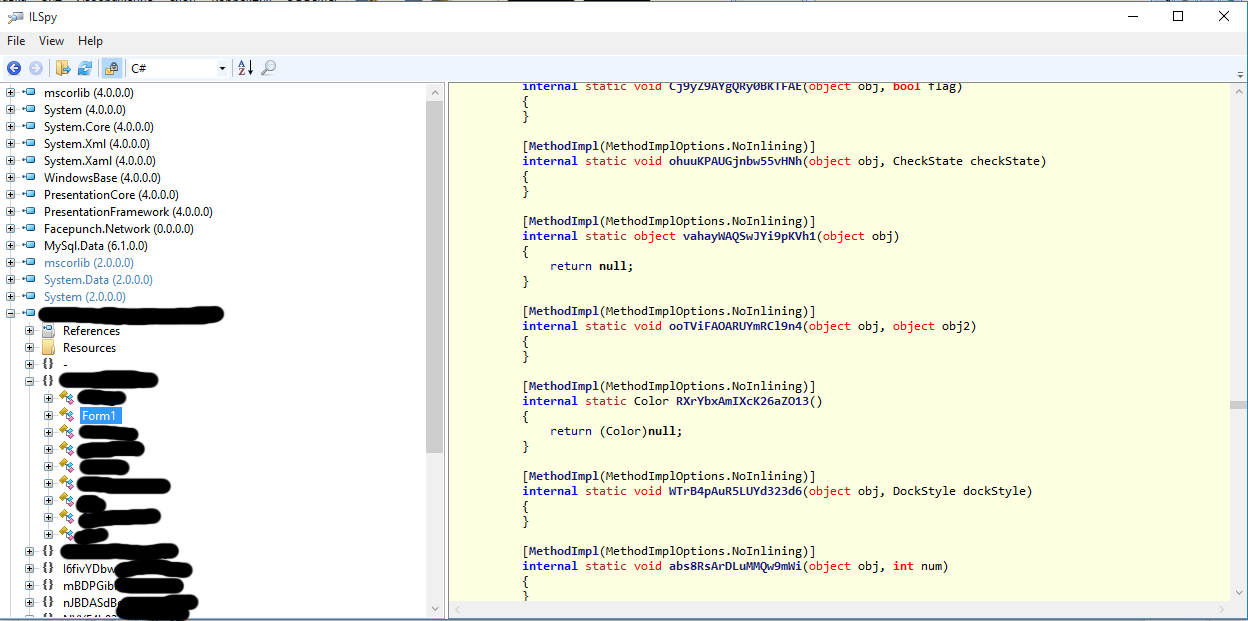
Judging by the incomprehensible signs, empty functions, the application is obfuscated - the code is unreadable. For help, I turned to the search engines and soon I found the free de4dot open-source program, which allows deobfuscating obfuscated applications written in C #.
Let's try to de-fuss and get the following result:
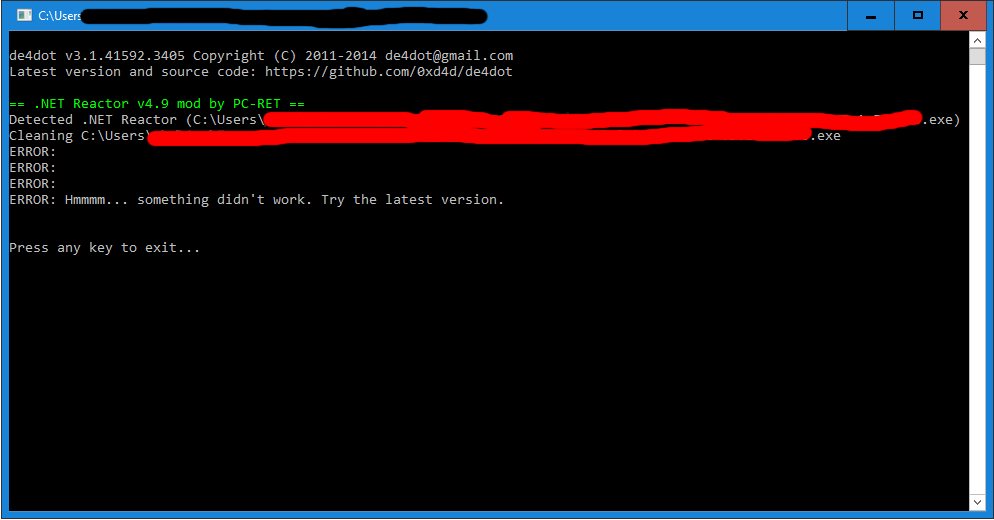
Judging by the message, the application is obfuscated using the .NET Reactor , and it is not possible to decompile it. After a long search for a deobfuscation method against the protection of .Net Reactor was not found.
Then I decided to try to at least open the DataSource.data database file in SQLite .
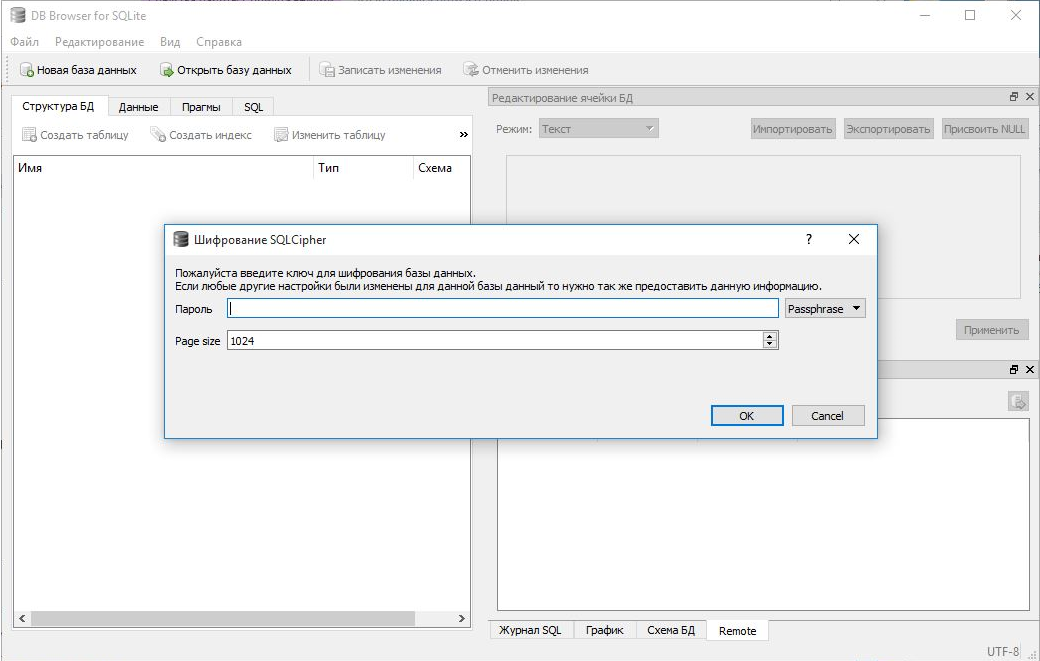
We are required to password from the database.
Disappointed with the failure, I have already surrendered, I left the hack for better times. But the thought that I had missed something did not leave my mind.
Some time has passed. When I delved into the files found this program and drew attention to the file MySql.Data.dll. And what if I change MySql.Data.dll to a modified one so that it displays the connection string to the database. For these purposes there is an opensource program - dnSpy . It allows you to edit the code .net applications and libraries. Load the dll file in the program and find the class MySqlConnection and edit the function .ctor:
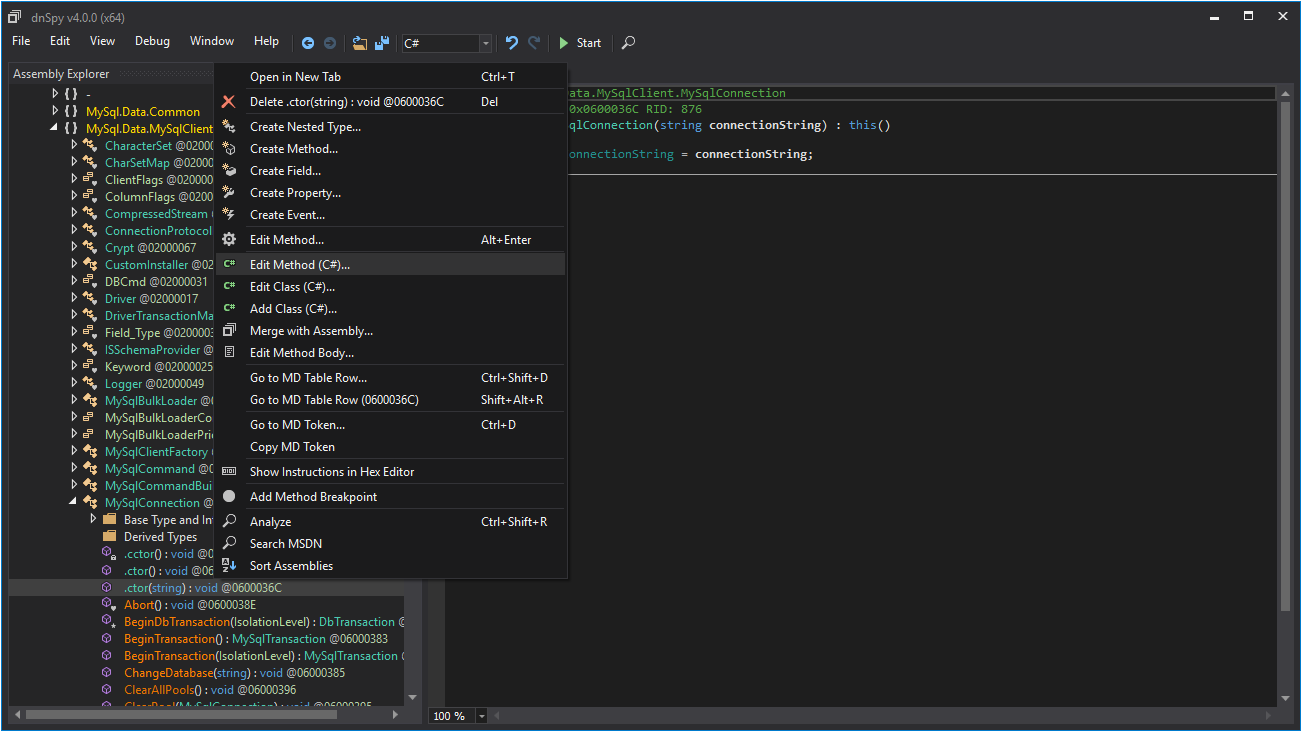
Add a line:
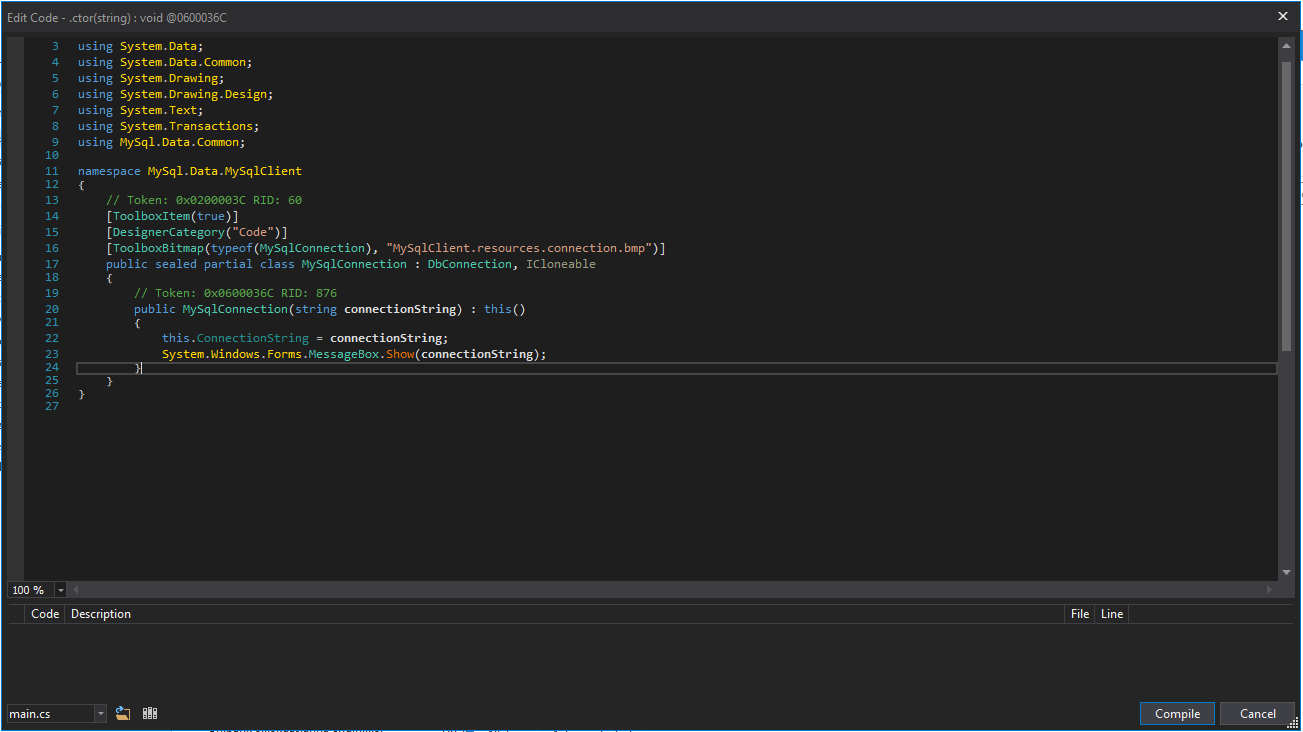
Click "Compile", save the file, replace it with the original one and finally launch the application.
This window will appear:
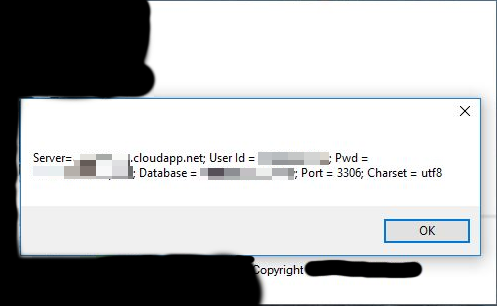
By the name of the cloudapp.net server, we can conclude that the database was created on Azure.
Download any free connection utility to the database , say HeidiSQL . After entering the data connection is opened DB. And here are our activation keys:
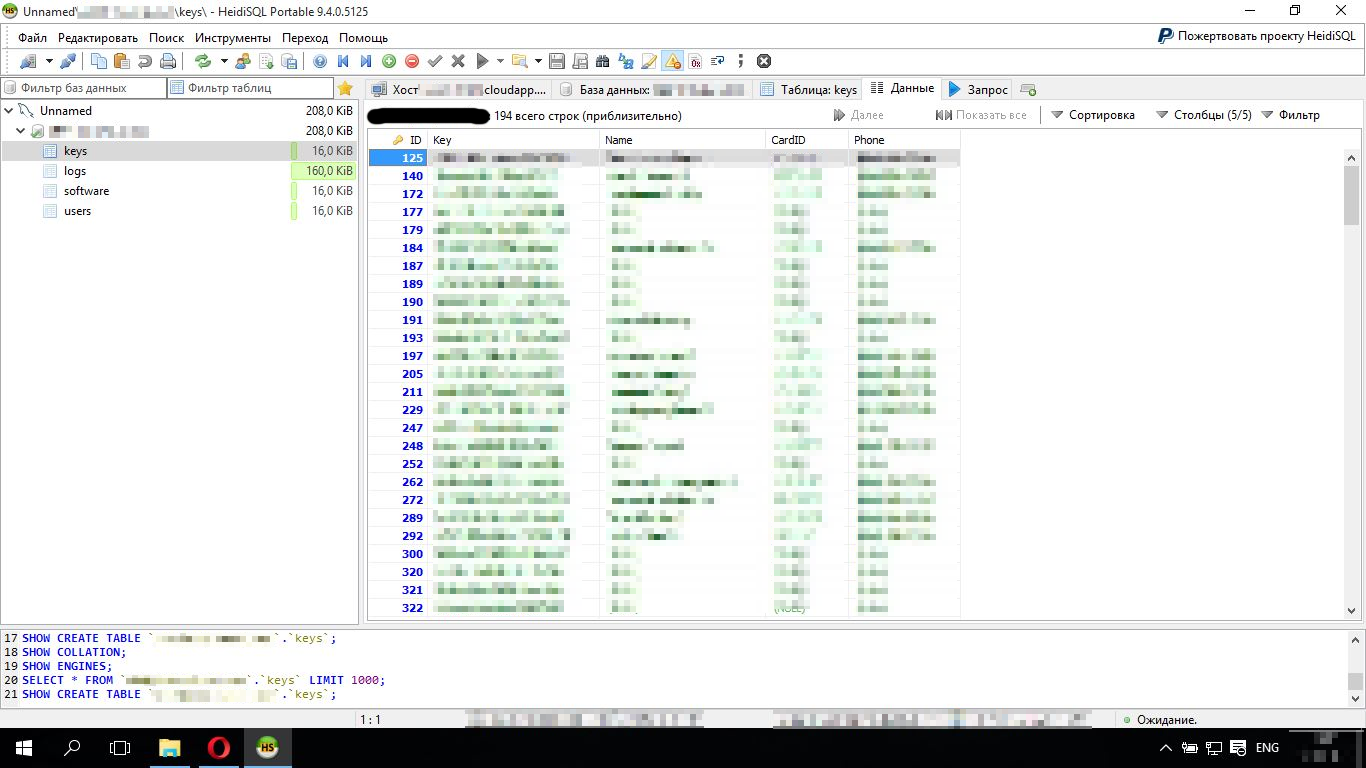
Most of the keys lacked the values of the Name, CardId, Phone fields. Apparently these keys have not yet been sold. Added a 16 digit key and registered the program. The data.dat file appeared in the folder with the installed program and the application issued a message about successful registration. The key created earlier disappeared in the table with keys. After a brief search, I found this key in the logs table. There was my key with a detailed description of the characteristics of my computer such as a model, processor, video card, etc. I deleted this line in order not to leave traces behind.
It is necessary to pay tribute to the developer of the application, he took care of protecting his application. He protected the database, obfuscated the application, the contents of the data.dat file was also encrypted, but he forgot about checking the hash of the library used.
PS: Harm organization hacking applications did not produce. By the time the application was able to be hacked, the friend no longer needed it. I only had an activated copy of the application and it was not transferred to third parties . Due to the uselessness of the application, I also deleted it.

This inanimate and fabulous world
It all started well, nothing foreshadowed trouble. In one late evening, one good friend asked me for one favor, using phrases like "well, you have a programmer." He wrote about a request to hack a certain application. To which I replied that I would try, but I cannot guarantee successful hacking. The next day we met, he gave me a disk and explained what kind of application it was.
Start
There is a certain organization that trains people to pass one specific exam. To get this application you need to go to this organization, register and pay for courses. At the end of the course, the organization for an additional fee gives a disk with the installer of the program with an individual activation key. The application allows you to do tests, look at the results. There is a mode "On the exam", which allows you to simulate the exam environment. The application gives random tests from different sections. Everything is good and beautiful.
')
First steps - experimenting
Install the application, run it to see what it is.
This splash screen opens, and the application freezes for a few seconds (this freeze is not casual).
Splash screen opens, and after it, after a few seconds, this window opens:

We are required to enter the activation key, which we naturally do not have. The first thing that alerted me was that the activation key input window opens with a noticeable delay, as if the application is connected somewhere via the Internet and the application developer did not take care of the asynchronous connection to the Internet. To make sure that the application climbs to the Internet has disconnected the network connections on the computer,
From here we conclude that the application is activated via the Internet and in its source code no activation keys or decryption algorithms are wired.
I climb into the folder of the installed program:

Structure:
- Arial Narrow.ttf - fontKep

- DataSource.data - a database file in which all tests
- **************. exe - application executable
- MySql.Data.dll - free opensource library from MySql
The presence of MySql.Data.dll in the program folder suggested that the application is most likely written in C #. Not protected by special utilities, applications written in this programming language are the easiest to decompile. Delighted by this assumption, my brain automatically gave me a signal to start the program IlSpy , which allows me to decompile applications written in C # and open the application in it.
As a result, such a picture opened before me.

As you can see, the application is really written in C #, it displays information about the developer, the version of .NET used. After opening the structure of the application, disappointment followed.

Judging by the incomprehensible signs, empty functions, the application is obfuscated - the code is unreadable. For help, I turned to the search engines and soon I found the free de4dot open-source program, which allows deobfuscating obfuscated applications written in C #.
Let's try to de-fuss and get the following result:

Judging by the message, the application is obfuscated using the .NET Reactor , and it is not possible to decompile it. After a long search for a deobfuscation method against the protection of .Net Reactor was not found.
Then I decided to try to at least open the DataSource.data database file in SQLite .

We are required to password from the database.
Disappointed with the failure, I have already surrendered, I left the hack for better times. But the thought that I had missed something did not leave my mind.
Dear you healthy?
Sometimes a step forward is the result of a kick in the ass.
Some time has passed. When I delved into the files found this program and drew attention to the file MySql.Data.dll. And what if I change MySql.Data.dll to a modified one so that it displays the connection string to the database. For these purposes there is an opensource program - dnSpy . It allows you to edit the code .net applications and libraries. Load the dll file in the program and find the class MySqlConnection and edit the function .ctor:

Add a line:
System.Windows.Forms.MessageBox.Show (connectionString);

Click "Compile", save the file, replace it with the original one and finally launch the application.
This window will appear:

By the name of the cloudapp.net server, we can conclude that the database was created on Azure.
Download any free connection utility to the database , say HeidiSQL . After entering the data connection is opened DB. And here are our activation keys:

Most of the keys lacked the values of the Name, CardId, Phone fields. Apparently these keys have not yet been sold. Added a 16 digit key and registered the program. The data.dat file appeared in the folder with the installed program and the application issued a message about successful registration. The key created earlier disappeared in the table with keys. After a brief search, I found this key in the logs table. There was my key with a detailed description of the characteristics of my computer such as a model, processor, video card, etc. I deleted this line in order not to leave traces behind.
Total
It is necessary to pay tribute to the developer of the application, he took care of protecting his application. He protected the database, obfuscated the application, the contents of the data.dat file was also encrypted, but he forgot about checking the hash of the library used.
PS: Harm organization hacking applications did not produce. By the time the application was able to be hacked, the friend no longer needed it. I only had an activated copy of the application and it was not transferred to third parties . Due to the uselessness of the application, I also deleted it.
Source: https://habr.com/ru/post/344922/
All Articles