Check Point Instructions and Useful Documentation

Relatively recently, we published the article “ Which firewall is the best? Leaders among UTM and Enterprise Firewalls (Gartner 2017) ”. Of course, such comparisons are very important and it is interesting to know the market leaders. This information is very useful when choosing a solution. But most engineers / sysadmins pay attention to another point - the documentation . The more documentation and the larger the online community, the easier it is to administer the chosen solution. How about Check Point? Below we provide the most useful Check Point resources where you can find all the necessary documentation or the answer to any technical question. These resources will be especially useful to those who already use Check Point.
I would like to start with a small thesis - Check Point is a complex and high-tech product. This is due primarily to the fact that he is able to perform a huge number of functions. As we have described earlier , Check Point functionality is divided into blades: Firewall, IPSec VPN, Moblie Access, Application Control, URL Filtering, Data Loss Prevention, IPS, Anti-Bot, Anti-Virus, Threat Emulation, Threat Extraction, Anti -Spam, Identity Awareness, Content Awareness, QoS, Monitoring, Smart Event, etc. Therefore, if you are looking for one big book on Check Point, then you will not find it. Instead, all Check Point documentation is divided into several categories. We write out the most important.
Check Point Support Center
This is the most important resource Check Point . And you should come here not only when you want to contact technical support, but also when looking for any documentation.
')
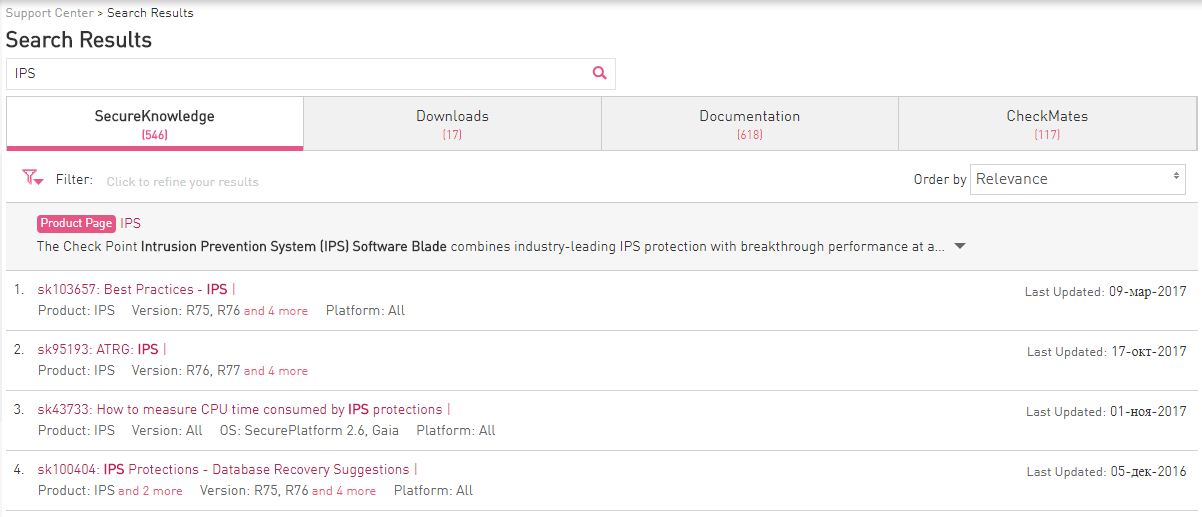
As you can see in the picture, any search query (in our case IPS) returns results in four sections:
- SecureKnowledge (shortly called sk) is the Check Point global knowledge base. It describes almost all the problems encountered, their symptoms, and most importantly - solutions. If you have a problem, then with a 98% probability sk already exists, which describes its solution.
- Downloads - downloads section. Here hotfixes (patches) or other files available for download (vpn-clients, scripts, etc.) can be posted.
- Documentation - all documentation related to your request is reflected here. These are usually PDF files.
- CheckMates (Formerly Forums) - information from the Check Point forums related to your request.
In general, this is a very powerful portal, which contains a huge amount of information about Check Point. But back to our documentation issue. What to look for?
Check Point Administration Guide
The name speaks for itself. I think this is the first documentation to start with when you encounter problems or issues related to Check Point. “Administrator guides” are usually divided by blades and operating system versions, for example: R80.10 Mobile Access Administration Guide or R77 Mobile Access Administration Guide .
Such guides contain not only the description of the blade, but also the setup procedure. The search for such guides is naturally carried out through the Support Center in the Documentation section. When searching, indicate the name of the blade of interest and the phrase “ administration guide ”. It is noteworthy that since version R80.10 most of the documentation is available not only in pdf form, but also in web format. Example :
In addition, it is possible to download the “collection” of admin guides for a specific software version. For example:
This “collection” includes a huge amount of documentation. Example of the content of the “collection” for R77:
Documentation for R77
CP_CPView_R77_Guide.pdf
CP_R77.10_QoS_AdminGuide.pdf
CP_R77.20_EndpointSecurity_AdminGuide.pdf
CP_R77.30_Appendix_ReleaseNotes.pdf
CP_R77.30_ReleaseNotes.pdf
CP_R77_ApplicationControlURLFiltering_AdminGuide.pdf
CP_R77_CLI_ReferenceGuide.pdf
CP_R77_ClusterXL_AdminGuide.pdf
CP_R77_Compliance_AdminGuide.pdf
CP_R77_CPcodeDLP_ReferenceGuide.pdf
CP_R77_DataLossPrevention_AdminGuide.pdf
CP_R77_Firewall_AdminGuide.pdf
CP_R77_Gaia_AdminGuide.pdf
CP_R77_Gaia_Advanced_Routing_AdminGuide.pdf
CP_R77_Gaia_Installation_and_Upgrade_Guide.pdf
CP_R77_IdentityAwareness_AdminGuide.pdf
CP_R77_IPS_AdminGuide.pdf
CP_R77_MobileAccess_AdminGuide.pdf
CP_R77_Multi-DomainSecurityManagement_AdminGuide.pdf
CP_R77_Non_Gaia_Installation_and_Upgrade_Guide.pdf
CP_R77_PerformanceTuning_AdminGuide.pdf
CP_R77_QoS_AdminGuide.pdf
CP_R77_SecurePlatform_AdminGuide.pdf
CP_R77_SecurePlatform_AdvancedRoutingSuite_CLI.pdf
CP_R77_SecurityGatewayVE_NM_AdminGuide.pdf
CP_R77_SecurityGateway_TechAdminGuide.pdf
CP_R77_SecurityManagement_AdminGuide.pdf
CP_R77_SmartEvent_AdminGuide.pdf
CP_R77_SmartLog_AdminGuide.pdf
CP_R77_SmartProvisioning_AdminGuide.pdf
CP_R77_SmartReporter_AdminGuide.pdf
CP_R77_SmartViewMonitor_AdminGuide.pdf
CP_R77_SmartViewTracker_AdminGuide.pdf
CP_R77_SmartWorkflow_AdminGuide.pdf
CP_R77_ThreatPrevention_AdminGuide.pdf
CP_R77_VoIP_AdministrationGuide.pdf
CP_R77_VPN_AdminGuide.pdf
CP_R77_VSX_AdminGuide.pdf
CP_R77.10_QoS_AdminGuide.pdf
CP_R77.20_EndpointSecurity_AdminGuide.pdf
CP_R77.30_Appendix_ReleaseNotes.pdf
CP_R77.30_ReleaseNotes.pdf
CP_R77_ApplicationControlURLFiltering_AdminGuide.pdf
CP_R77_CLI_ReferenceGuide.pdf
CP_R77_ClusterXL_AdminGuide.pdf
CP_R77_Compliance_AdminGuide.pdf
CP_R77_CPcodeDLP_ReferenceGuide.pdf
CP_R77_DataLossPrevention_AdminGuide.pdf
CP_R77_Firewall_AdminGuide.pdf
CP_R77_Gaia_AdminGuide.pdf
CP_R77_Gaia_Advanced_Routing_AdminGuide.pdf
CP_R77_Gaia_Installation_and_Upgrade_Guide.pdf
CP_R77_IdentityAwareness_AdminGuide.pdf
CP_R77_IPS_AdminGuide.pdf
CP_R77_MobileAccess_AdminGuide.pdf
CP_R77_Multi-DomainSecurityManagement_AdminGuide.pdf
CP_R77_Non_Gaia_Installation_and_Upgrade_Guide.pdf
CP_R77_PerformanceTuning_AdminGuide.pdf
CP_R77_QoS_AdminGuide.pdf
CP_R77_SecurePlatform_AdminGuide.pdf
CP_R77_SecurePlatform_AdvancedRoutingSuite_CLI.pdf
CP_R77_SecurityGatewayVE_NM_AdminGuide.pdf
CP_R77_SecurityGateway_TechAdminGuide.pdf
CP_R77_SecurityManagement_AdminGuide.pdf
CP_R77_SmartEvent_AdminGuide.pdf
CP_R77_SmartLog_AdminGuide.pdf
CP_R77_SmartProvisioning_AdminGuide.pdf
CP_R77_SmartReporter_AdminGuide.pdf
CP_R77_SmartViewMonitor_AdminGuide.pdf
CP_R77_SmartViewTracker_AdminGuide.pdf
CP_R77_SmartWorkflow_AdminGuide.pdf
CP_R77_ThreatPrevention_AdminGuide.pdf
CP_R77_VoIP_AdministrationGuide.pdf
CP_R77_VPN_AdminGuide.pdf
CP_R77_VSX_AdminGuide.pdf
Check Point Technical Reference Guides (ATRGs)
There are situations when the information in the standard “admin guides” is not enough. In this case, you should refer to the documents with the tag “ATRG” - Advanced Technical Reference Guides . As the name suggests, these are more in-depth technical guides that allow you to thoroughly understand the work of a Check Point function. As with the admin guide, you can search for ATRG documents in the Support Center by adding the name of the blade to the request, for example: atrg threat emulation .
In addition, a page recently appeared where all ATRG guides are listed. There are already more than 35 of them.
Check Point “How To” Guides
In addition to standard and extended (ATRG) guides, there are also so-called “How To”. These documents contain instructions on the most common tasks encountered by Check Point users. All guides are divided into categories:

A list of all “How To” can be found in sk65385 . The collection of instructions is just awesome. I recommend always keeping them “at hand”.
Check Point Processes and Daemons
In order to effectively solve problems with Check Point, it is very important to understand how it works in principle. Here another SK comes to the rescue - sk97638 . It describes all the processes and Checkpoint daemons, including such information as:
- Description of the process / daemon;
- Where it is located in the file system;
- What is the name and location of its log file;
- How to stop it;
- How to run it;
- How to run debug mode for it;
- Etc.
All this is collected in a convenient table that reflects to which blade the “demon” belongs and which sub-processes it creates. I would refer this documentation to the Must Have category for any Check Point administrator.
What ports does Check Point use?
Another very useful Check Point document is sk52421 . Here you will find all the ports that Check Point uses, with a detailed description of what and which blade. The document is especially useful if Check Point is located behind another ME.
Check Point Performance Optimization (Best Practices)
In sk98348, you will find the main recommendations for setting up and improving the performance of such things as: Security Gateway, ClusterXL, Cluster - 3rd party, VSX, CoreXL, SecureXL, Application Control, URL Filtering, Anti-Virus, Anti-Bot, IPS. Do not neglect these documents, especially if your Check Point is loaded more than 50%.
Check Point CheckMates
The last resource I would like to talk about is CheckMates . This is a community portal for a huge number of Check Point users. It is also supported by the vendor itself. It regularly publishes educational materials, webinars, interesting articles from experts and much more. But most importantly - here you can ask a question to which you could not find the answer in the documentation (which is unlikely). The community is very lively and most likely you will be answered very quickly.
English vs Russian
Unfortunately, almost all the submitted documentation and resources in English (which is highly expected). Some Russian-language documentation can be found on the portal of our colleagues from the RRC, something in our blog or YouTube channel . But naturally this is not enough. Here you can make only one conclusion - without English anywhere. As for the authorized training, then fortunately in Russia they teach courses in Russian .
Conclusion
I tried to reflect the Check Point key documents and resources (in fact, there are many more). As you can see, the vendor is very responsible approach to the issue and understands its seriousness. If for some reason you could not find the document you need or solve your problem with Check Point, then feel free to contact us . As they say, "we will help you with what we can." Thanks for attention!
Source: https://habr.com/ru/post/344370/
All Articles