Basics and methods of information security in 2017
In today's world it is difficult to keep any information in secret. Especially if it is valuable to someone and you need to pass it on. No matter what your reasons for hiding any data, in this article we will look at the main methods and software for keeping information secret.
I will try to explain complex and incomprehensible technologies in a simple and accessible language, so that it is understandable for a beginner.
Important! All programs presented in the article are free. Download them can and should only official sites of developers.
Disclaimer: I, that is, the author of the article is a non-specialist in information security and is operating on data from open sources. I am against the use of the methods described below to conceal illegal actions.
')
First, you should understand the basic, basic concepts.
To begin with the definition:
Encryption is a reversible transformation of information in order to hide from unauthorized persons, with providing, at the same time, authorized users access to it. For the most part, encryption serves the task of maintaining the confidentiality of transmitted information. An important feature of any encryption algorithm is the use of a key that confirms the choice of a specific conversion from the set of possible ones for a given algorithm.
Without going into technical details, we can say that encryption is the transformation of data to hide information.
There are various encryption algorithms, but we will superficially get acquainted with the main actual encryption algorithms.
Encryption algorithms are divided into symmetric algorithms and asymmetric algorithms:
Examples of symmetric algorithms:
DES is a symmetric encryption algorithm developed by IBM and approved by the US government in 1977 as an official standard.
A direct development of DES is currently the Triple DES (3DES) algorithm. In 3DES, encryption / decryption is performed by running the DES algorithm three times.
AES - also known as Rijndael (pronounced [rɛindaːl] (Randal)) is a symmetric block encryption algorithm (block size 128 bits, key 128/192/256 bits), adopted as the encryption standard by the US government according to the results of the AES competition. This algorithm is well analyzed and is now widely used, as it was with its predecessor DES.
Blowfish (pronounced [bloofish]) is a cryptographic algorithm that implements block symmetric encryption with a variable key length. Designed by Bruce Schneier in 1993.
GOST 28147-89 (Magma) - Russian standard of symmetric block encryption, adopted in 1989. It is an example of DES-like cryptosystems.
In 2015, together with the Grasshopper algorithm, one of the variants of the GOST-89 algorithm was published under the name “Magma” as part of the GOST R 34.12-2015 standard.
The Grasshopper block cipher is a symmetric block encryption algorithm with a block size of 128 bits and a key length of 256 bits.
Examples of asymmetric algorithms:
RSA (abbreviation for the names Rivest, Shamir and Adleman) is a public-key cryptographic algorithm based on the computational complexity of the problem of factoring large integers.
RSA cryptosystem became the first system, suitable for both encryption and digital signature. The algorithm is used in a large number of cryptographic applications, including PGP, S / MIME, TLS / SSL, IPSEC / IKE, and others.
GOST R 34.10-2012 is a Russian standard that describes the algorithms for the formation and verification of electronic digital signatures.
SSL (Secure Sockets Layer) is a cryptographic protocol that implies a more secure connection. In fact, this is a method of transmitting information on the Internet, which involves transparent data encryption. The protocol was widely used for instant messaging and voice over IP (English Voice over IP - VoIP) in such applications as e-mail, Internet fax, etc.
Subsequently, based on the SSL 3.0 protocol, an RFC standard was developed and adopted, called TLS.
TLS (English Transport Layer Security), like its predecessor SSL, are cryptographic protocols that provide secure data transmission between nodes on the Internet.
SSL and TLS are used for example to encrypt traffic in working with sites. When data is transmitted via the HTTPS protocol, the traffic (the data that is transmitted and received) is encrypted by a certificate that uses a particular resource.
SSL certificate - contains information about its owner, as well as the public key used to create a secure communication channel. Organizations and individuals receive to confirm that a site or other resource is really represented by them and it is not a fake resource. Certificates are obtained or purchased from authorized trusted certificate authorities.
All this is done so that the person who joins the communication channel in the middle between you and the addressee could not read the information or change it.
Hashing or receiving checksums is a data conversion (be it a string of text or a data archive) of arbitrary length into a (output) string of fixed length, performed by a specific algorithm.
The peculiarity is that if the input data changes even for a bit of information, then the final (output) line will already be different. Thus, you can verify that the file or data has not been changed.
Before installing software downloaded even from official sites, you should compare the checksum of the file that you downloaded with the checksum specified on the site. An attacking person can control your network and when downloading a file, as it seems to you from the official site, a modified installation file with a vulnerability or even a Trojan code can slip.
To ensure the security of information access to it must be blocked with a good password. There are basic principles for creating a strong password:
Two-factor authentication is a method of authentication (proof of identity) which implies the use of two methods of identity verification.
For example, when you log into an account on any site, you first enter your password, and then the code sent via SMS to a trusted phone number.
There are many different authentication methods:
Where possible, use two-factor authentication. Even if your password is found out or picked up, the offender will not be able to pass the second authentication method.
Two-factor authentication can be enabled in many popular services:
If you use a strong, everywhere, but the same password, it threatens all your data at once. After all, if the attackers manage to spy or find out your password, otherwise, they will automatically get access to all the services you use.
It is recommended to use different passwords for different services, it is best to generate them. But then there is the question of remembering all passwords.
And here it is worth using a password manager. There are various services that provide the preservation and management of passwords. Personally, I and various security experts advise using KeePassX .
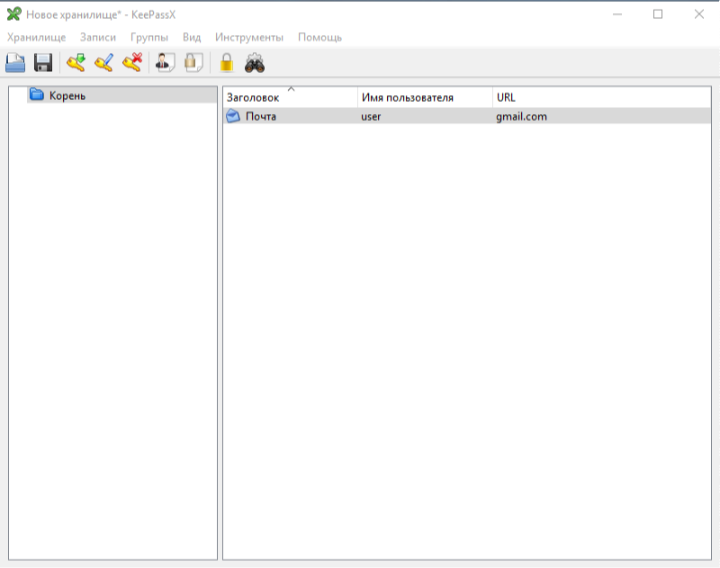
The fact is that this project has a long history. All this time he has open source moves and the developers provide all the data to be sure that the program has no bookmarks.
This program is absolutely free, it has open source code and it runs on all major platforms (Windows, macOS, Linux).
Passwords are stored in special databases that use AES and TwoFish encryption. The database itself (stored in one file) is best stored in a safe place, for example, on a USB drive.
The program has a strong password generator.
Using Internet services to store a password is more convenient and mobile, but much less safer. Your passwords may be requested by special services or there may be a patch in the software that is used on the servers of the password manager service. Passwords can also be intercepted using browser vulnerabilities.
Site - www.keepassx.org
Also worth taking care of safe storage of files on the media. In order to exclude the option that if the device on which you store important data falls into the wrong hands, the data will be opened and accessible to the attacker.
A fairly reliable way is to encrypt data. There are many different programs that allow you to encrypt data. There are paid and free. There are even solutions embedded in the operating system. For example, BitLocker on Windows and FireVault on macOS.
Unfortunately, in the software of this class often embed bookmarks for easy hacking. And to the developers of such software is always the maximum requirements for the safety and security of their product.
Previously, the undisputed leader was the program TrueCrypt . Unfortunately, the developers have stopped the development of this program. The topic with TrueCrypt is generally very confusing, many believe that special services were involved there and it was they who forced them to stop developing the program.

But since the source code of TrueCrypt was open, another team took on further development and support. They have eliminated several vulnerabilities and released a new version called VeraCrypt.
This program is constantly monitored and undergoing security audits.
The meaning of the program is to create encrypted containers (located on a disk in the form of a file), encrypt removable media or full hard disk encryption including a local disk where the operating system is installed.
In cases of creating an encrypted container, a file is created on disk. You specify its name and size. Next, select the encryption method (it is worth noting that the choice is quite large, and there is the ability to encrypt 3 algorithms in a row at once), the password and other parameters.
Then you connect (mount) your container to any available disk. And you can write any data to it. When you stop work, you unmount it. All files that are located in the container will be securely stored in it. Such a file can be transmitted through less secure channels, but still it is not worth keeping it openly.
It is possible to create a hidden container in the container. This is done so that if you get caught and forced to lead the password to the data container, there are dummy data located there, and the basic data that you intended to hide will be located in a hidden container inside this container.
You can encrypt the flash drive and then its contents will also be available to you through a password.
Website - www.veracrypt.fr
For communication at a distance, you can use mail. For example, as did Edward Snowden, who told the world about the total surveillance of US special services.
There are services that provide an encrypted mailbox. The most proven and convenient option at the moment is ProtonMail. ProtonMail itself was created under the influence of those events that occurred with Snowden. This is a free service that provides users to register a free encrypted mailbox.

You will have to pay for additional features and storage expansion, but a free account is enough for the usual transfer of text information and small files.
There is a web version, clients for Android and iOS. The service is translated into many languages, including Russian.
Site - protonmail.com
Sometimes communication through the mail does not fit. Information is needed here and now. Then you can use the format to all of us familiar with instant messengers. And here comes the Signal application. Again, there are a lot of applications that also declare complete security and anonymity, but it is to Signal that there are fewer questions and suspicions. He was also used by Edward Snowden. It is also used by Mat Green, who is quite famous among encryption and security experts.
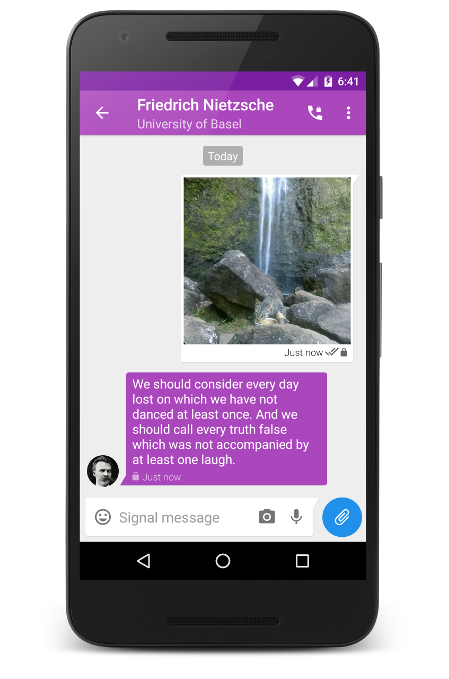
The application has been audited and is constantly being checked.
The application looks like a regular instant messenger. It can transfer text, emoticons, photos, audio, files. There is even a voice and video connection. Information is transmitted fairly quickly. The interface is not overloaded and convenient to all those who at least once sent SMS on a smartphone.
But you need to be careful with this application. The application itself is protected, there is even protection from taking screenshots. But your smartphone is probably not so safe and protected. So, transferring information to the phone memory first is not very safe. But at the same time send text and make audio and video calls is quite safe.
There are clients for Android, iOS, Windows, macOS, Linux.
Site - signal.org
For a safe visit to the sites should use the Tor Browser. You must have heard of him. Tor Browser works on the basis of onion-based networks. The meaning of such a network is that the connection from your device to the destination server passes through a certain number of layers of the network. Each network layer or connection is encrypted separately. And it turns out that the traffic you send is encrypted several times. This affects the connection speed, but is very effective in terms of security.

Tor Browser itself consists not only of the features of onion networks, but also of add-ons that turn off all tracking buttons and scripts, as well as send all traffic through HTTPS.
Website - www.torproject.org
If you need to hide and encrypt all traffic on your device, you can use VPN. VPN stands for virtual personal area network. When connecting to a VPN, all connections of your device go through the selected server.
This allows not only to hide the original source of the request, but also to encrypt the data.
It can also be used to access blocked sites on your network. Since the traffic goes, for example, through the Netherlands, where a Russian local information resource may not be blocked, you can access it.
I use ProtonVPN software, from the creators of ProtonMail. Their email service proved to be excellent, and when he saw the availability of a VPN client from this team, he immediately decided to install and use.

The application is free, but does not yet have a Russian interface. But to understand his work is very simple.
If you choose a paid data plan, then you will have a greater choice of countries to connect. Paid servers are less loaded, so the speed will be higher. It will also be possible to use P2P traffic and TOR networks.
Site - protonvpn.com
Tails is the most ultimatum option. This is an operating system based on the Linux kernel.

Usually it is recorded on a flash drive or DVD disc and downloaded from them. At the same time, the creators themselves recommend first writing the operating system to a flash drive, then boot from it. And already from this carrier with the help of special software, write the operating system to another flash drive or DVD disc.
In this operating system, you can work on the Internet, work with mail and the most important data on your computer.
It uses the most advanced encryption technology. Maximum protection of all data. This OS is constantly checked and investigated.
Site - tails.boum.org
Thank you for reading the article to the end. I hope the things I described have become clear. For more details you can always refer to the Internet.
I would welcome comments, comments and criticism.
I will try to explain complex and incomprehensible technologies in a simple and accessible language, so that it is understandable for a beginner.
Important! All programs presented in the article are free. Download them can and should only official sites of developers.
Disclaimer: I, that is, the author of the article is a non-specialist in information security and is operating on data from open sources. I am against the use of the methods described below to conceal illegal actions.
')
The basics
First, you should understand the basic, basic concepts.
Encryption
To begin with the definition:
Encryption is a reversible transformation of information in order to hide from unauthorized persons, with providing, at the same time, authorized users access to it. For the most part, encryption serves the task of maintaining the confidentiality of transmitted information. An important feature of any encryption algorithm is the use of a key that confirms the choice of a specific conversion from the set of possible ones for a given algorithm.
Without going into technical details, we can say that encryption is the transformation of data to hide information.
There are various encryption algorithms, but we will superficially get acquainted with the main actual encryption algorithms.
Encryption algorithms are divided into symmetric algorithms and asymmetric algorithms:
- Symmetric encryption uses the same key for both encryption and decryption.

- Asymmetric encryption uses two different keys: one for encryption (also called open), the other for decryption (called closed).
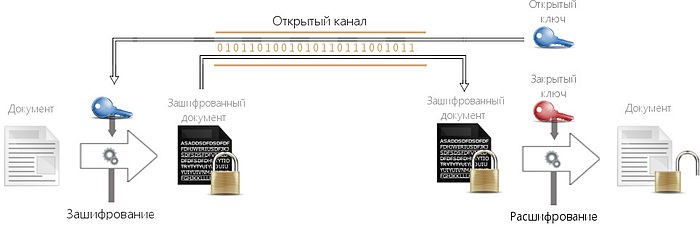
Examples of symmetric algorithms:
DES is a symmetric encryption algorithm developed by IBM and approved by the US government in 1977 as an official standard.
A direct development of DES is currently the Triple DES (3DES) algorithm. In 3DES, encryption / decryption is performed by running the DES algorithm three times.
AES - also known as Rijndael (pronounced [rɛindaːl] (Randal)) is a symmetric block encryption algorithm (block size 128 bits, key 128/192/256 bits), adopted as the encryption standard by the US government according to the results of the AES competition. This algorithm is well analyzed and is now widely used, as it was with its predecessor DES.
Blowfish (pronounced [bloofish]) is a cryptographic algorithm that implements block symmetric encryption with a variable key length. Designed by Bruce Schneier in 1993.
GOST 28147-89 (Magma) - Russian standard of symmetric block encryption, adopted in 1989. It is an example of DES-like cryptosystems.
In 2015, together with the Grasshopper algorithm, one of the variants of the GOST-89 algorithm was published under the name “Magma” as part of the GOST R 34.12-2015 standard.
The Grasshopper block cipher is a symmetric block encryption algorithm with a block size of 128 bits and a key length of 256 bits.
Examples of asymmetric algorithms:
RSA (abbreviation for the names Rivest, Shamir and Adleman) is a public-key cryptographic algorithm based on the computational complexity of the problem of factoring large integers.
RSA cryptosystem became the first system, suitable for both encryption and digital signature. The algorithm is used in a large number of cryptographic applications, including PGP, S / MIME, TLS / SSL, IPSEC / IKE, and others.
GOST R 34.10-2012 is a Russian standard that describes the algorithms for the formation and verification of electronic digital signatures.
SSL encryption
SSL (Secure Sockets Layer) is a cryptographic protocol that implies a more secure connection. In fact, this is a method of transmitting information on the Internet, which involves transparent data encryption. The protocol was widely used for instant messaging and voice over IP (English Voice over IP - VoIP) in such applications as e-mail, Internet fax, etc.
Subsequently, based on the SSL 3.0 protocol, an RFC standard was developed and adopted, called TLS.
TLS (English Transport Layer Security), like its predecessor SSL, are cryptographic protocols that provide secure data transmission between nodes on the Internet.
SSL and TLS are used for example to encrypt traffic in working with sites. When data is transmitted via the HTTPS protocol, the traffic (the data that is transmitted and received) is encrypted by a certificate that uses a particular resource.
SSL certificate - contains information about its owner, as well as the public key used to create a secure communication channel. Organizations and individuals receive to confirm that a site or other resource is really represented by them and it is not a fake resource. Certificates are obtained or purchased from authorized trusted certificate authorities.
All this is done so that the person who joins the communication channel in the middle between you and the addressee could not read the information or change it.
Hashing
Hashing or receiving checksums is a data conversion (be it a string of text or a data archive) of arbitrary length into a (output) string of fixed length, performed by a specific algorithm.
The peculiarity is that if the input data changes even for a bit of information, then the final (output) line will already be different. Thus, you can verify that the file or data has not been changed.
Before installing software downloaded even from official sites, you should compare the checksum of the file that you downloaded with the checksum specified on the site. An attacking person can control your network and when downloading a file, as it seems to you from the official site, a modified installation file with a vulnerability or even a Trojan code can slip.
Basic principles for creating a strong password
To ensure the security of information access to it must be blocked with a good password. There are basic principles for creating a strong password:
- The password should be at least 15 characters long, and the best option is 20. More is better, but you should not overdo it either.
- No words, popular templates (qwerty, and so on), dates and various information related to you in the password itself.
- The password must contain lowercase and uppercase letters, numbers, special characters (#% ^ & * @!).
Two-factor authentication
Two-factor authentication is a method of authentication (proof of identity) which implies the use of two methods of identity verification.
For example, when you log into an account on any site, you first enter your password, and then the code sent via SMS to a trusted phone number.
There are many different authentication methods:
- Password
- Pin
- SMS with code
- Fingerprint
- Flash token (a flash drive with a unique key written)
- Push notifications in the app on the smartphone
Where possible, use two-factor authentication. Even if your password is found out or picked up, the offender will not be able to pass the second authentication method.
Two-factor authentication can be enabled in many popular services:
- Telegram
- In contact with
- Mail.ru
- Yandex
- Dropbox
Data storage
Password Manager KeePassX
If you use a strong, everywhere, but the same password, it threatens all your data at once. After all, if the attackers manage to spy or find out your password, otherwise, they will automatically get access to all the services you use.
It is recommended to use different passwords for different services, it is best to generate them. But then there is the question of remembering all passwords.
And here it is worth using a password manager. There are various services that provide the preservation and management of passwords. Personally, I and various security experts advise using KeePassX .

The fact is that this project has a long history. All this time he has open source moves and the developers provide all the data to be sure that the program has no bookmarks.
This program is absolutely free, it has open source code and it runs on all major platforms (Windows, macOS, Linux).
Passwords are stored in special databases that use AES and TwoFish encryption. The database itself (stored in one file) is best stored in a safe place, for example, on a USB drive.
The program has a strong password generator.
Using Internet services to store a password is more convenient and mobile, but much less safer. Your passwords may be requested by special services or there may be a patch in the software that is used on the servers of the password manager service. Passwords can also be intercepted using browser vulnerabilities.
Site - www.keepassx.org
Data Encryption VeraCrypt
Also worth taking care of safe storage of files on the media. In order to exclude the option that if the device on which you store important data falls into the wrong hands, the data will be opened and accessible to the attacker.
A fairly reliable way is to encrypt data. There are many different programs that allow you to encrypt data. There are paid and free. There are even solutions embedded in the operating system. For example, BitLocker on Windows and FireVault on macOS.
Unfortunately, in the software of this class often embed bookmarks for easy hacking. And to the developers of such software is always the maximum requirements for the safety and security of their product.
Previously, the undisputed leader was the program TrueCrypt . Unfortunately, the developers have stopped the development of this program. The topic with TrueCrypt is generally very confusing, many believe that special services were involved there and it was they who forced them to stop developing the program.

But since the source code of TrueCrypt was open, another team took on further development and support. They have eliminated several vulnerabilities and released a new version called VeraCrypt.
This program is constantly monitored and undergoing security audits.
The meaning of the program is to create encrypted containers (located on a disk in the form of a file), encrypt removable media or full hard disk encryption including a local disk where the operating system is installed.
In cases of creating an encrypted container, a file is created on disk. You specify its name and size. Next, select the encryption method (it is worth noting that the choice is quite large, and there is the ability to encrypt 3 algorithms in a row at once), the password and other parameters.
Then you connect (mount) your container to any available disk. And you can write any data to it. When you stop work, you unmount it. All files that are located in the container will be securely stored in it. Such a file can be transmitted through less secure channels, but still it is not worth keeping it openly.
It is possible to create a hidden container in the container. This is done so that if you get caught and forced to lead the password to the data container, there are dummy data located there, and the basic data that you intended to hide will be located in a hidden container inside this container.
You can encrypt the flash drive and then its contents will also be available to you through a password.
Website - www.veracrypt.fr
Communication
Mail service ProtonMail
For communication at a distance, you can use mail. For example, as did Edward Snowden, who told the world about the total surveillance of US special services.
There are services that provide an encrypted mailbox. The most proven and convenient option at the moment is ProtonMail. ProtonMail itself was created under the influence of those events that occurred with Snowden. This is a free service that provides users to register a free encrypted mailbox.

You will have to pay for additional features and storage expansion, but a free account is enough for the usual transfer of text information and small files.
There is a web version, clients for Android and iOS. The service is translated into many languages, including Russian.
Site - protonmail.com
Signal Protected Messenger
Sometimes communication through the mail does not fit. Information is needed here and now. Then you can use the format to all of us familiar with instant messengers. And here comes the Signal application. Again, there are a lot of applications that also declare complete security and anonymity, but it is to Signal that there are fewer questions and suspicions. He was also used by Edward Snowden. It is also used by Mat Green, who is quite famous among encryption and security experts.

The application has been audited and is constantly being checked.
The application looks like a regular instant messenger. It can transfer text, emoticons, photos, audio, files. There is even a voice and video connection. Information is transmitted fairly quickly. The interface is not overloaded and convenient to all those who at least once sent SMS on a smartphone.
But you need to be careful with this application. The application itself is protected, there is even protection from taking screenshots. But your smartphone is probably not so safe and protected. So, transferring information to the phone memory first is not very safe. But at the same time send text and make audio and video calls is quite safe.
There are clients for Android, iOS, Windows, macOS, Linux.
Site - signal.org
Secure internet access
Safe Tor Browser Browser
For a safe visit to the sites should use the Tor Browser. You must have heard of him. Tor Browser works on the basis of onion-based networks. The meaning of such a network is that the connection from your device to the destination server passes through a certain number of layers of the network. Each network layer or connection is encrypted separately. And it turns out that the traffic you send is encrypted several times. This affects the connection speed, but is very effective in terms of security.

Tor Browser itself consists not only of the features of onion networks, but also of add-ons that turn off all tracking buttons and scripts, as well as send all traffic through HTTPS.
Website - www.torproject.org
ProtonVPN Virtual Private Network
If you need to hide and encrypt all traffic on your device, you can use VPN. VPN stands for virtual personal area network. When connecting to a VPN, all connections of your device go through the selected server.
This allows not only to hide the original source of the request, but also to encrypt the data.
It can also be used to access blocked sites on your network. Since the traffic goes, for example, through the Netherlands, where a Russian local information resource may not be blocked, you can access it.
I use ProtonVPN software, from the creators of ProtonMail. Their email service proved to be excellent, and when he saw the availability of a VPN client from this team, he immediately decided to install and use.

The application is free, but does not yet have a Russian interface. But to understand his work is very simple.
If you choose a paid data plan, then you will have a greater choice of countries to connect. Paid servers are less loaded, so the speed will be higher. It will also be possible to use P2P traffic and TOR networks.
Site - protonvpn.com
Anonymous Tails Operating System
Tails is the most ultimatum option. This is an operating system based on the Linux kernel.

Usually it is recorded on a flash drive or DVD disc and downloaded from them. At the same time, the creators themselves recommend first writing the operating system to a flash drive, then boot from it. And already from this carrier with the help of special software, write the operating system to another flash drive or DVD disc.
In this operating system, you can work on the Internet, work with mail and the most important data on your computer.
It uses the most advanced encryption technology. Maximum protection of all data. This OS is constantly checked and investigated.
Site - tails.boum.org
Conclusion
Thank you for reading the article to the end. I hope the things I described have become clear. For more details you can always refer to the Internet.
I would welcome comments, comments and criticism.
Source: https://habr.com/ru/post/344294/
All Articles