How we help quickly certify the requirements of information security to those who move to the cloud

On the Roskomnadzor website, scheduled inspections for next year are posted in December. We started with foreign social networks, now there are banks and a number of companies in the Far East in the queue. Not everything is smooth with everyone, but checks are getting close. As a result, this has generated some interest in moving to a certified cloud, so I would like to tell you more about what can be in accordance with Federal Law 149 and 152.
I also saw how certification for compliance with the Federal Law-152 is done by mistake. Below I will explain why it is not always needed.
')
Now not everyone understands what needs to be done when infrastructure is not deployed in the form of a rack. The Russian market is not very savvy in moving to the cloud. Large government customers intuitively understand that they need cloud technologies (in particular, state govlak), but they do not understand what needs to be done to do this. We are ready for such situations, there is a special competence center for information security. Technoserv Cloud platform is certified for information security requirements and allows you to place GIS and ISPDn, which meet the highest requirements for information security, it remains only to certify the client's decision. With our help, this usually goes away in 2-3 months, which is much faster (on its own, it usually takes 6 months).
Let's look at this procedure with an example. Suppose you are a medical company that very much protects the personal data of patients.
A short educational program about how licensing differs from certification and certification:
- Means of protection are certified (soft and hardware), manufacturers receive certificates from the FSB and FSTEC. Such a certificate, for example, says that cryptography is allowed, there are no bookmarks in the software, standards for Russia are complied with.
- Certified finished object, assembled using certified "parts". Certification is a confirmation that an information object is performing a set of measures, and correctly. That is, the designer is assembled correctly. The certificate is issued by licensees FSTEC.
- Licensed activities on information security. For example, we, Technoserv, are one of the licensees of FSTEC and can issue certificates from the paragraph above.
First, a difficult situation. Suppose you are a big government medical organization. The key word is “state”, that is, you have a GIS case. Federal law 149 obliges the information owner and the information system operator to protect information from unauthorized access, destruction, modification, blocking, copying, provision, dissemination and other illegal actions (article 14, paragraph 9) by taking legal, organizational and technical measures aimed confidentiality of restricted information and the exercise of the right of access to publicly available information (art. 16).
First, the level of significance of information and possible damage, the scale of the information system is assessed. For a medical system, a Security Class (K 1) is assigned - information systems for which a violation of a given security characteristic of personal data processed in them can lead to significant negative consequences for the subjects of personal data.
Personal data is regulated by FZ-152. Organizations that are operators for the processing of personal data of citizens of the Russian Federation are obliged to ensure the recording, systematization, accumulation, storage, refinement (updating, modification), and extraction of personal data using databases located in the territory of the Russian Federation.
There are four categories of PDN: special, biometric, public, other. Security levels look like this:
Processed PD | Volume of PD | Type of actual threats | ||
Type 1 Threats | Type 2 Threats | Type 3 Threats | ||
Special categories PD | More than 100 thousand | Ultrasound 1 | Ultrasound 1 | Ultrasound 2 |
Less than 100 thousand | Ultrasound 1 | Ultrasound 2 | Ultrasound 3 | |
Special categories of PD operator staff | Any | Ultrasound 1 | Ultrasound 2 | Ultrasound 3 |
Biometric PD | Any | Ultrasound 1 | Ultrasound 2 | Ultrasound 3 |
Other categories of PD | More than 100 thousand | Ultrasound 1 | Ultrasound 2 | Ultrasound 3 |
Less than 100 thousand | Ultrasound 1 | Ultrasound 3 | Ultrasound 4 | |
Other categories of PD operator's employees | Any | Ultrasound 1 | Ultrasound 3 | Ultrasound 4 |
Public PD | More than 100 thousand | Ultrasound 2 | Ultrasound 2 | Ultrasound 4 |
Less than 100 thousand | Ultrasound 2 | Ultrasound 3 | Ultrasound 4 | |
Shared PDs | Any | Ultrasound 2 | Ultrasound 3 | Ultrasound 4 |
The higher the level of personal data protection is determined, the more measures to ensure the security of personal data are required to neutralize the security risks of personal data. If by mistake you determine a higher level of security, then, accordingly, you will have to build a more expensive PD protection system. If you define a lower level of security, then this will lead to a violation of the law.
In addition, a number of protective measures are required. Here, for example, the correspondence table of our cloud "out of the box" without completions for a specific client:
Segment parameter | Protected | Closed |
Virtualization environment | OpenStack-KVM, VMware | VMware |
Purpose | Placement of information systems that do not impose specialized requirements for information security. Placement of information systems of companies and organizations, including those participating in the processing of data of bank card holders | Placement of state information systems (GIS) and personal data information systems (ISPDN) with the highest requirements for information security |
Compliance with the legislation of the Russian Federation on information security | ● Order of the FSTEC of Russia No. 21 ● Payment Card Industry Data Security Standard (PCI DSS) - the standard of data security of the payment card industry; ● Bank of Russia Regulation No. 382-p “On the Requirements for Ensuring Information Security in Transfers of Funds and on the Procedure for the Bank of Russia to Control Compliance with Requirements for Ensuring Information Security in Transfers of Funds”; ● Standard of the Bank of Russia (STO BR IBBS) | ● Order of the FSTEC of Russia No. 17 ● Order of the FSTEC of Russia No. 21 ● Law of the Russian Federation No. 149-FZ ● Law of the Russian Federation No. 152-FZ ● RF Law No. 242-FZ |
Certification / Certification | Certificate of Compliance (as a service provider) to the Payment Card Industry Data Security Standard (PCI DSS) | Certificate of compliance of the infrastructure of the segment "Closed" to the requirements for the protection of information for the placement of information systems and systems that process personal data up to class 1 / security level |
Information Security | The protective equipment used allows the following requirements to be met: ● to personal data information systems up to the 3rd level of security inclusive; ● PCI DSS standard; ● Bank of Russia Regulation No. 382-P | The protective equipment used allows you to meet the requirements of: ● to information systems up to 1st class of security inclusive; ● to personal data information systems up to level 1 of security inclusive. Applied hardware and software of information security have certificates of FSTEC of Russia and / or FSB of Russia |
Physical security | Ensuring the physical security of the IT infrastructure: ● control and management of access to the data center; ● fire and security alarm; ● automatic fire extinguishing; ● video surveillance; ● safe racks | Ensuring the physical security of the IT infrastructure: ● control and management of access to the data center; ● fire and security alarm; ● automatic fire extinguishing; ● video surveillance; ● safe racks |
Network access | ● Public Internet; ● Through a secure VPN connection over the public Internet (IPSec VPN — implemented by software of the virtualization platform); ● VPN channel | ● Through a separate, hardware-protected cryptographic protection communication channel; ● Through a secure VPN-connection over the public Internet (IPSec VPN with cryptographic protection according to GOST |
Information security in the cloud begins with perimeter protection, protection against DDoS using an external cleaning center or connecting to providers with the necessary capabilities, and also consists of providing and organizing access and ends with network separation.
Now, if you are a non-state medical organization, everything is much more interesting. First, you need to figure out whether you are processing personal data. The simple formula is:
{F. IO. + Date of birth + address of residence} = personal data
{F. I.O.} or {date of birth} or {address of residence} ≠ personal data
There are more factors and combinations, so you must first make an assessment. Then you need to decide whether you need a certification for the protection of personal data or not. For non-state commercial companies, it is optional, is passed at the request of the operator. But at the same time, FSTEC recalls that FZ-152 should regularly assess the effectiveness of measures to protect personal data. Certification is considered for such an assessment. That is, you can not do it, but you have to do another assessment procedure, so many of her pass to immediately and surely. Another reason - by mistake, without understanding the requirements. The third reason - for self-control, to make sure that the protection is real according to the standard - in the FZ-152 there are, in general, very sound things. Here we sometimes come to us simply because we obviously know how to protect systems with the highest security class and we have the infrastructure for this.
What to do before the move?
Before moving to the cloud infrastructure, special attention should be paid to testing issues. It is at this stage that the customer should have a real idea of how the cloud itself and related services work.
Testing need functional and load. As a result of functional testing, the customer must ensure that everything works as he expects. As a result of load testing, the customer must make sure that all this still does not fall.
At the initial assessment of the infrastructure for testing it is recommended to use 1/10 of the combat. For example, you need to take 10 virtual locks instead of hundreds and try to test. Test scenarios are always discussed with the customer.
What if we hit? In the list for review?
As a rule, if the customer enters the Roskomnadzor list, then either they are notified of an unscheduled inspection, or there is no time for detailed tests. Here are the types of checks:
- Roskomnadzor warns about scheduled inspections in advance. As a rule, a notice with a copy of the order of the upcoming event is sent by mail or fax at least three working days. To learn about the scheduled inspections of legal entities (their branches, representative offices, separate structural units) and individual entrepreneurs, please visit the official website of Roskomnadzor.
- Unscheduled inspections are most often carried out on complaints received from individuals. Roskomnadzor warns about unscheduled inspection in 24 hours.
- Documentary checks. Type of inspections for which Roskomnadzor requests a list of documents, copies of which must be submitted to the territorial body of Roskomnadzor.
- Exit check. When on-site inspection is carried out on-site inspections, when representatives of the ILF come to the organization (as a rule, several people). There is a check for compliance with the requirements of FZ-152.
Especially in the second case - it remains from 30 days to days to fix things. At this point, the customer turns to us and asks for help. Sometimes there is enough time to not just carry out quick work, but really make sure that during the inspections everything will be fine. We are ready to check the procedures, as well as the fact that everything is OK. We will support the customer during the inspection.
Since the platform has already been certified, this greatly reduces the amount of effort required to comply with the requirements of data protection legislation. In our cloud, all necessary perimeter protection measures are used (firewalls, intrusion detection and prevention tools, crypto-gateways) and virtualization protection tools. Accordingly, during verification, the client can indicate that most of the information protection functions are performed by Technoserv, and we are ready to provide everything necessary to confirm this.
In such a situation, we do not get access to the personal data and payment data, so the client needs to independently undergo certification. But we provide all the documents from the platform, as well as helping to quickly develop a set of documentation for the certification of an information system, and therefore this is done relatively simply and the first time. The cloud segment is certified for information systems up to level 1, including the state system. The infrastructure is isolated from the public cloud - in fact, a virtual private cloud is being obtained. All means of protection are certified by FSTEK and FSB.
That is 80% of the work we have already done.
We provide information security competence as an outsourcing. You can do it yourself, but at the expense of a lot of implementation experience, we can provide very short deadlines.
Architecture
Here are two examples of infrastructure location in the cloud. They differ in whether the organization has its own DDoS protection complex or is it ours that comes with the platform. In approximately the same way, one can approach other components and information security protection tools.
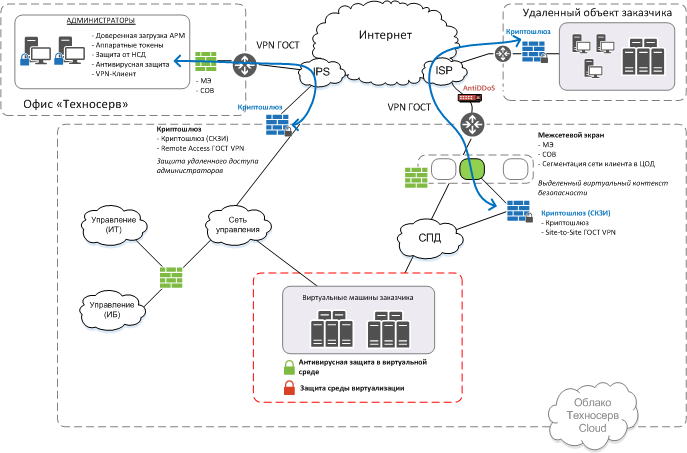
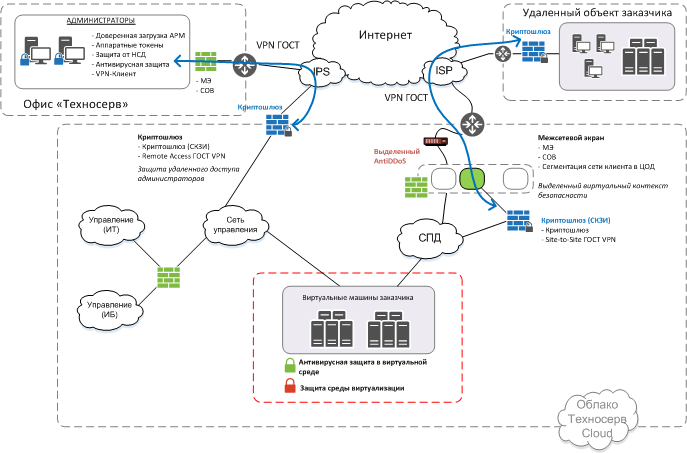
Chronology of work without haste
- Examine customer systems, determine infrastructure requirements and protection measures - 2 weeks.
- Relocation plan and technical documentation - 2-3 weeks.
- New organizational and administrative documentation - 2 weeks.
- System migration - up to 3 weeks.
- Documents on certification and passage of certification - another 2-3 weeks.
If you have practical questions, here is a page with details and contact: security@ts-cloud.ru
Source: https://habr.com/ru/post/344084/
All Articles