Mac OS High Sierra, is there a remote “passwordless root”? (Yes, but unlikely)
Immediately after it became known that it was possible to get root without a password, I wondered if it could be done remotely.
After much experimentation, the next unlikely, but still feasible, scenario turned out. First I will describe how to reproduce it, and then why each of the points is important.
Circumstances should be such that:
The attack looks like this:
Now we analyze why everything is so difficult.
Finally:
After much experimentation, the next unlikely, but still feasible, scenario turned out. First I will describe how to reproduce it, and then why each of the points is important.
Circumstances should be such that:
- The victim uses the vulnerable version 10.13.1
')
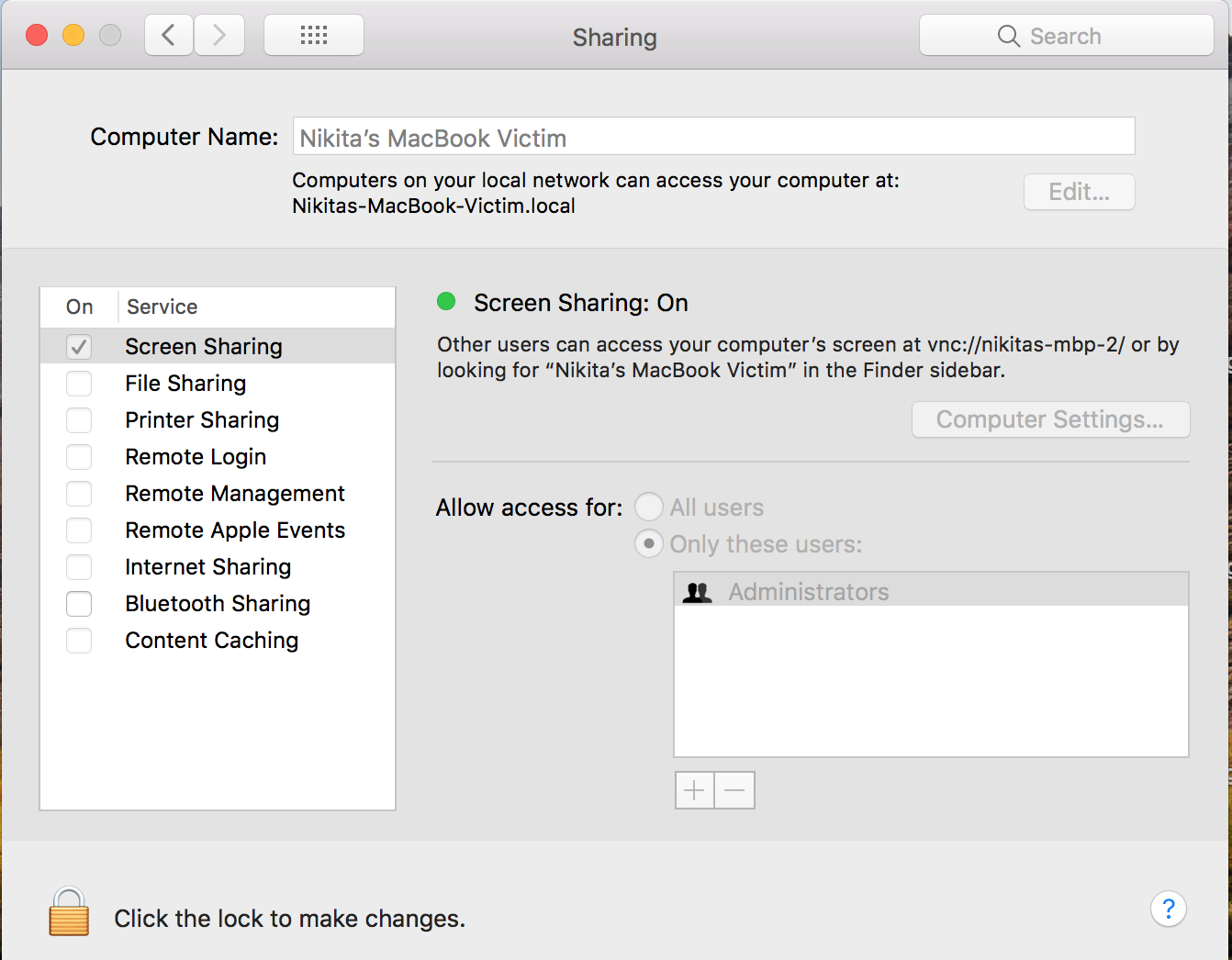
- The victim has Screen Sharing enabled.
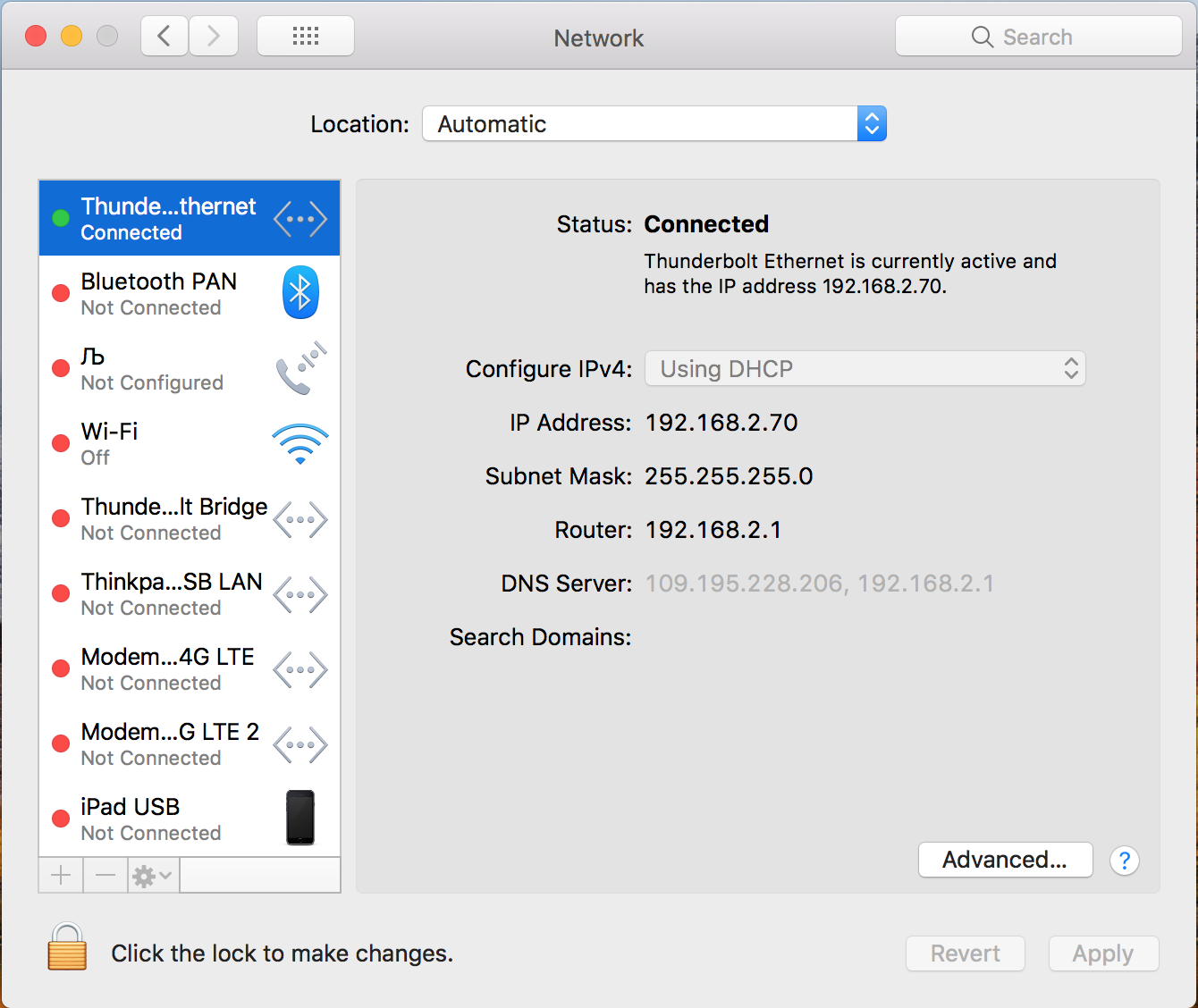
- The victim is wired to the network (with Internet access or not - it does not matter).
- The victim read on the Internet about the existence of a vulnerability, tried it on her Mac, and did not take any action to eliminate it.

- The attacker must know the victim's ip address or find it in the list of devices on the network.
The attack looks like this:
- Attacker connects via VNC (Finder → Cmd + K → vnc: // victim → root without password)
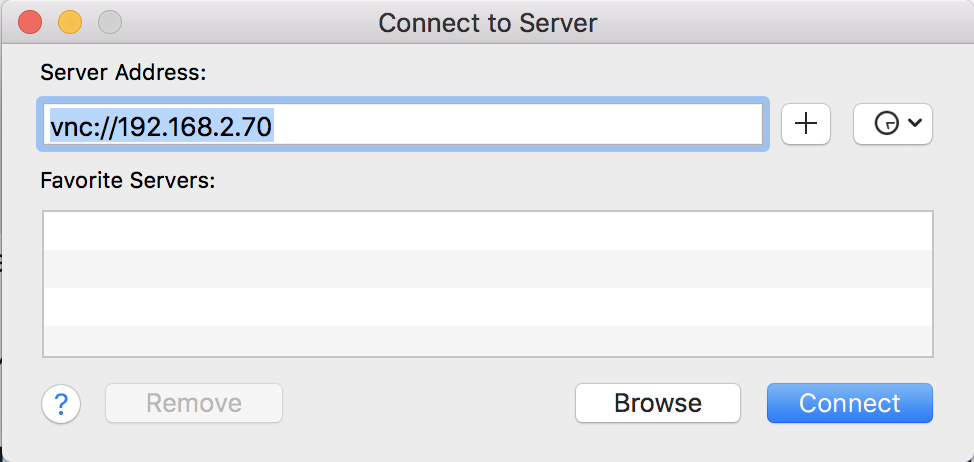
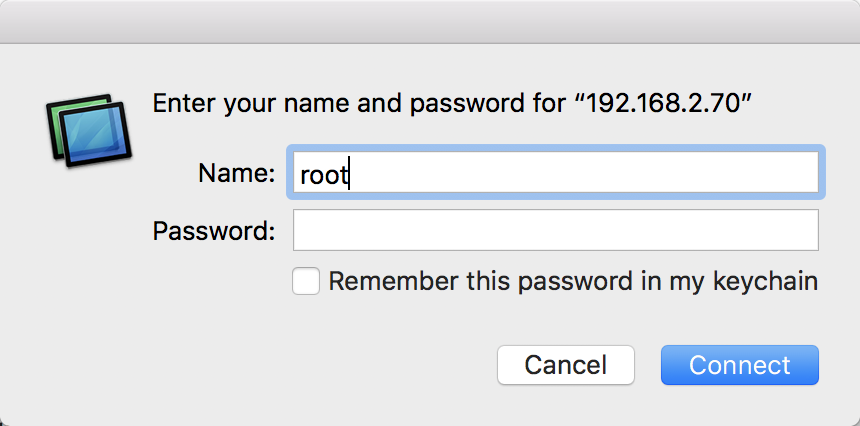
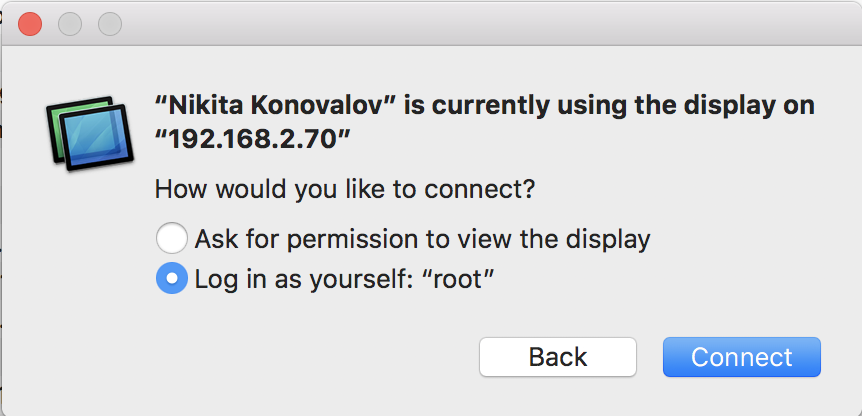
- Attacking the Login Screen of the victim chooses Other ...
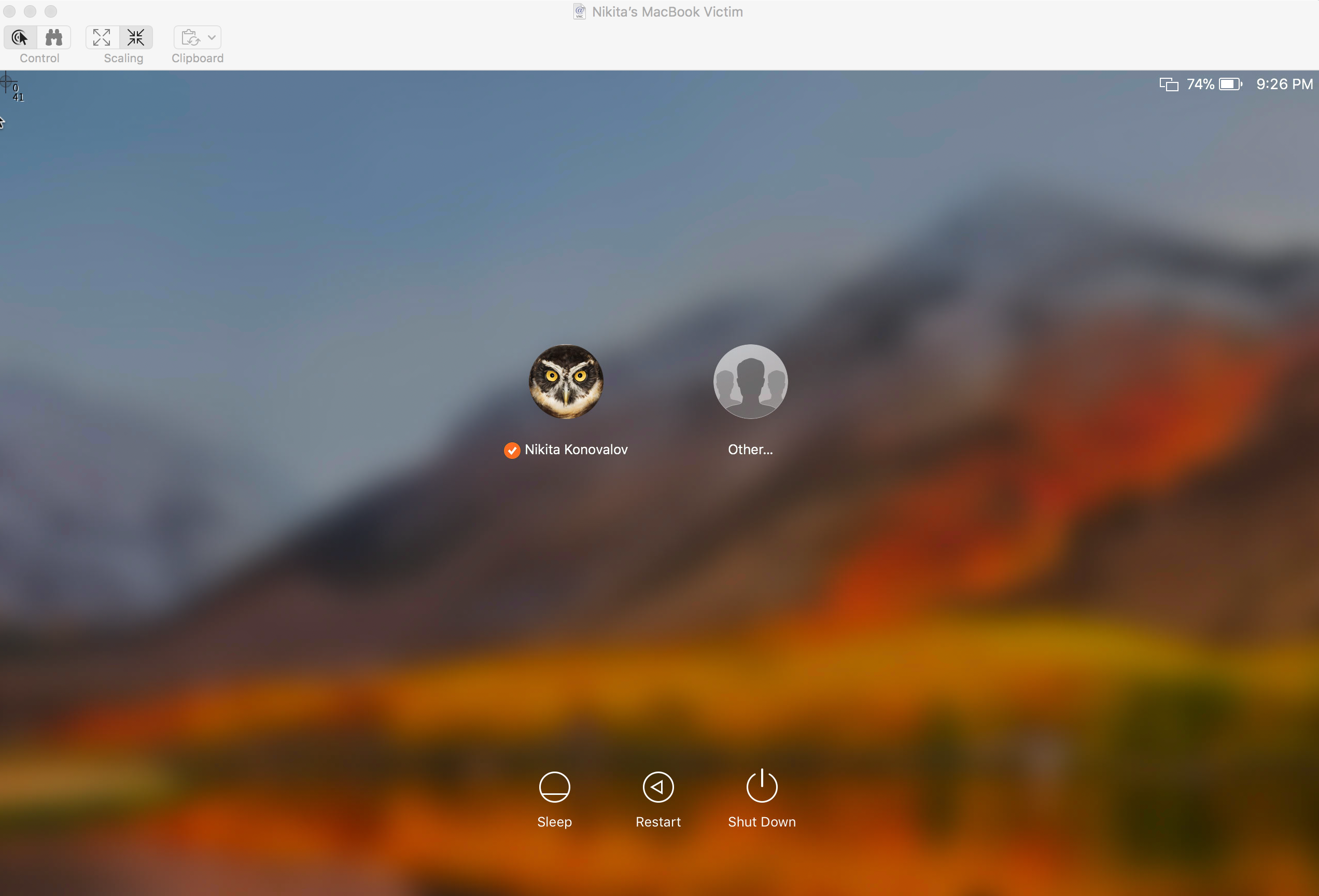
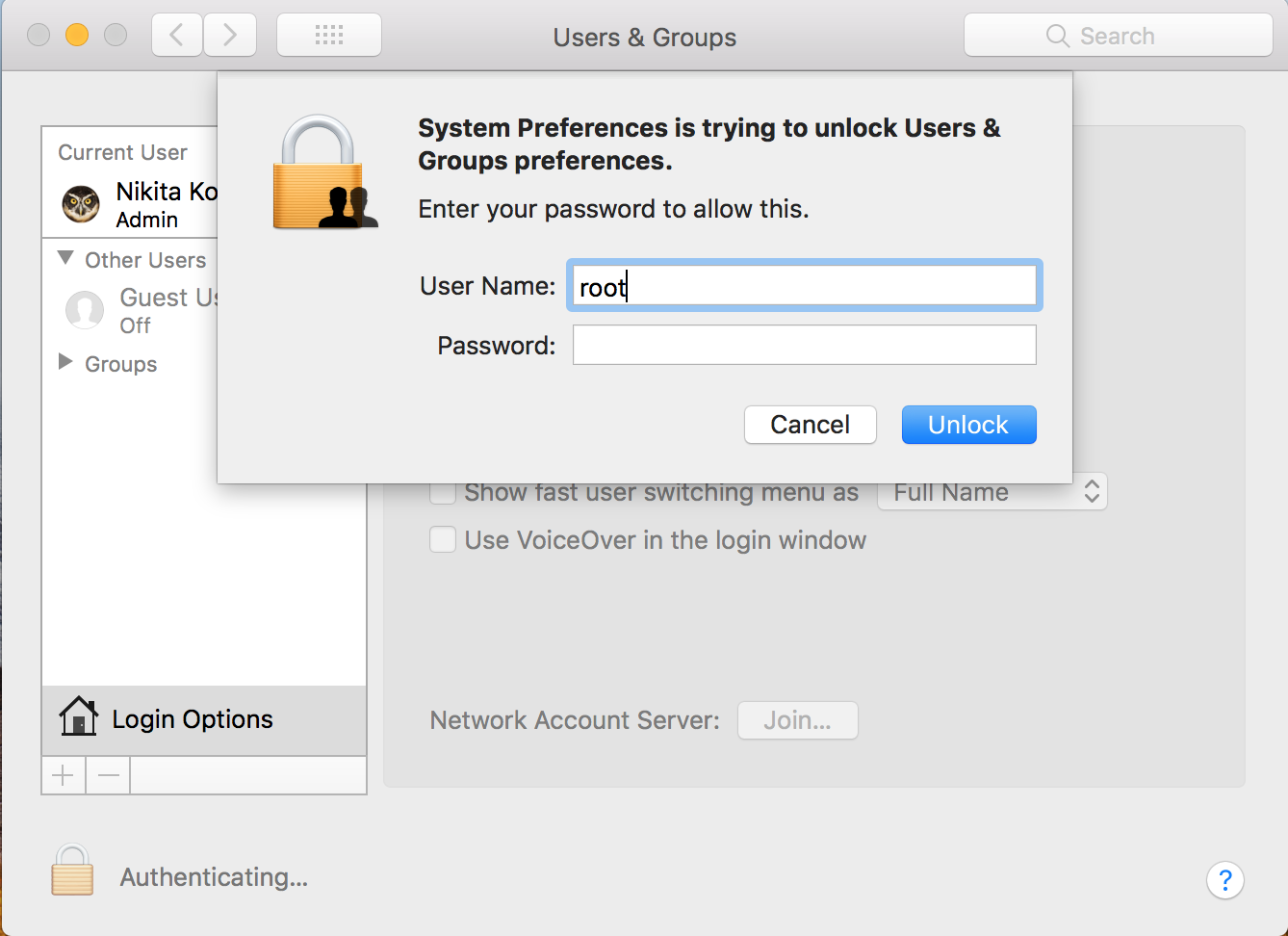
- The attacker enters root without a password.
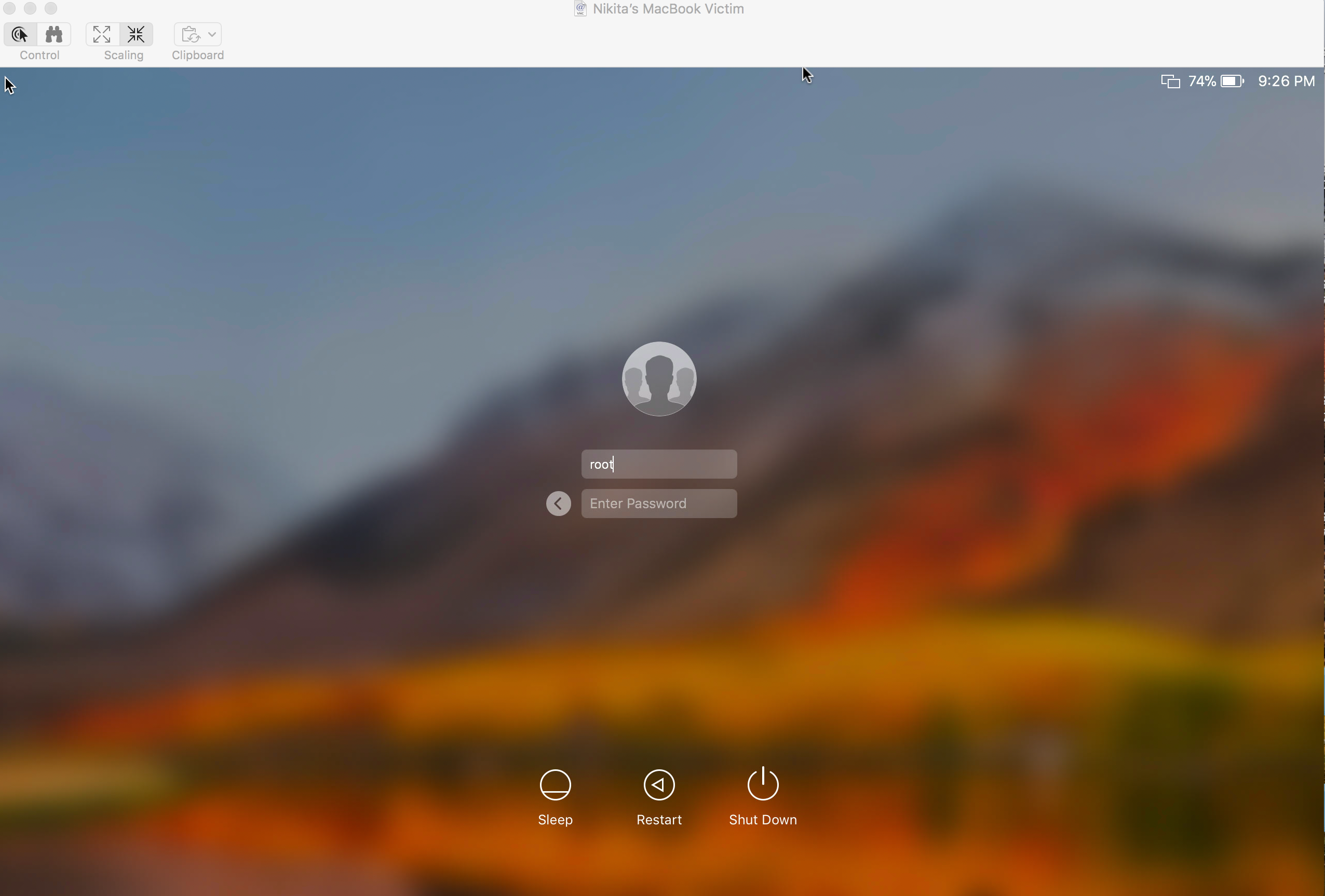
- Is done.
Now we analyze why everything is so difficult.
- This is obvious.
- Screen sharing allows access via vnc. By default, it is turned off, but the probability that the user once used it and left it on is still there.
- Wire connection is important. By Wifi VNC, the connection is terminated at the moment when the root user is just starting to log in. Apparently, this is due to the fact that root does not have access to the keychain of the normal admin. For some reason, the already working Wifi connection terminates the root connection, but it cannot reconnect. The wire does not break the connection.
- The most unlikely. It is necessary that a login for root-a be available on the victim's computer. And without a password. This effect, at the moment you can achieve the only way I know - to exploit that very, original vulnerability. It is necessary that the victim at least once opened the very “lock” of the root with an empty password.
- The attacker's Mac will find the victim himself with Screen Sharing turned on in his subnet. However, the usual methods of detecting an open vnc port will also work. nmap you help.
During a root attack, an empty password essentially works twice. The first time vnc connection is just established. Second time on the Login Screen of the victim.
Finally:
- The victim sees an indicator that Screen Sharing is active and can disable the attacker at any time. Although this is unlikely to help her.
- If you try to rotate the attack via wifi, the root of the victim will remain on the victim's Mac. It will need to be unlocked for later reboot or shutdown.
- At the logged root, the “lock” is immediately open and does not want to close at all.
- When establishing a VNC connection, there is an option “Ask the screen of the current user”. The user can put you behind your screen. What to do with it - think for yourself.
Source: https://habr.com/ru/post/344058/
All Articles