Hacking a site using another site. Trust but check
The client addressed us to the company, the next mountain of developers. I can’t understand why this site doesn’t work. The hosting seemed to be paid for, the domain is extended, and I don’t know what's wrong with the site
After a more detailed conversation, it turned out:
We wondered what was happening there with the site, that it was already failing for the second time. We asked the client to contact his friend, on whom the hosting was registered, and to find out from him that he had access to the control panel, and we contacted the hosting technical support service to clarify the reasons for the site’s inoperability.
For those who went to read directly about hacking, you can safely zhmakat here . Well, for those who are interested in the whole story entirely, as everything was discovered, read in full.
')
After the response from the support service, it became clear that access to the control panel was blocked, as was the account itself, for distributing spam emails and accessing it is possible only by providing login data and the IP to which temporary access will be associated.
Yes, that's right, the same rake. The difference this time was only that, according to a friend who agreed to provide data from the hosting, the site on the account is no longer there and it will not be possible to recover. So he said the very developers who are very " effectively " solved the problem last time.
After a bit of speculation, we decided to try our luck and try to restore the site from the backups that were supposed to be kept by the hosting provider. Provided all the necessary information and the IP address from which the entry will be made. We went into the account and first decided to see the history of requests to the support service, on the previous case of blocking.
The correspondence was small and we managed to find out that:
Checking the files in the root directory, we found that the site exists and no one deleted it, as a friend of the client informed us earlier . Moreover, the last entry into the account was made just after the previous hacking incident. Nobody logged in anymore.
We created a new request for technical support, with a request to clarify in which files the malicious script was found, in order to have at least some idea what to look for.
Having received the answer from the support service, we found the necessary file and saw it there:
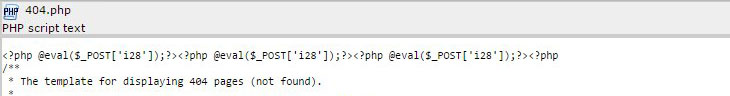
Walking through all the files on the site, the same content was found in another 74 template files. After analyzing the code, checking all the ways, we realized that:
We cleaned all the files, cleared the database, changed all access from the site and hosting, and also told technical support that the problem was fixed. The account was unlocked and the site became available again.
The script, which was encrypted in base64 encoding and was stored in the database as text, not only performed the function of recovering all deleted lines of malicious code, but was also a bruteforce script.
The main function that he performed was to send POST and GET requests to the addresses of admins of various sites, with logins and passwords, also stored in one of the database tables. After a successful selection operation, he wrote down the correct pair of login: password in another table, access to which could be obtained by contacting the correct request to one of 74 infected files, right from the browser window.
By such manipulations, the attackers not only accelerated the process of collecting passwords, but also increased the base of sites from which spam was sent and other passwords were picked.
Such a cycle can continue indefinitely. If one of the site owners finds a virus and removes it, then this is a small loss for intruders, because they have a huge base of such loopholes at their disposal, which is increasing every day.
PS: for those who want to see the script . Screenshots and examples of the malicious script were not uploaded due to the fact that there are always individuals who use the sample code as the basis for their offspring, and I don’t want to be the reason for creating and distributing the next malicious script.
After a more detailed conversation, it turned out:
- The hosting account on which the site was located was previously blocked for spamming.
- According to the client, the problem was solved when he turned to the previous developers, they restored access and everything began to work as before.
- What kind of manipulations were carried out by the developers, he does not know, since the hosting was not registered to him, but to some of his friends, who advised him on these guys.
- The site does not work again, but it cannot contact any of those who fixed the problem last time, at the moment.
We wondered what was happening there with the site, that it was already failing for the second time. We asked the client to contact his friend, on whom the hosting was registered, and to find out from him that he had access to the control panel, and we contacted the hosting technical support service to clarify the reasons for the site’s inoperability.
For those who went to read directly about hacking, you can safely zhmakat here . Well, for those who are interested in the whole story entirely, as everything was discovered, read in full.
')
After the response from the support service, it became clear that access to the control panel was blocked, as was the account itself, for distributing spam emails and accessing it is possible only by providing login data and the IP to which temporary access will be associated.
Yes, that's right, the same rake. The difference this time was only that, according to a friend who agreed to provide data from the hosting, the site on the account is no longer there and it will not be possible to recover. So he said the very developers who are very " effectively " solved the problem last time.
After a bit of speculation, we decided to try our luck and try to restore the site from the backups that were supposed to be kept by the hosting provider. Provided all the necessary information and the IP address from which the entry will be made. We went into the account and first decided to see the history of requests to the support service, on the previous case of blocking.
The correspondence was small and we managed to find out that:
- A password was chosen for the admin site.
- Through the plug-in installation module, a spam mailing script was embedded.
- The guys didn’t take any preventive work, but simply decided to restore the site from the backup, while not touching the database and without changing the password to it and the admin panel of the site.
- After some time, the account was again blocked, due to the fact that they did not eliminate the script.
Screenshot chat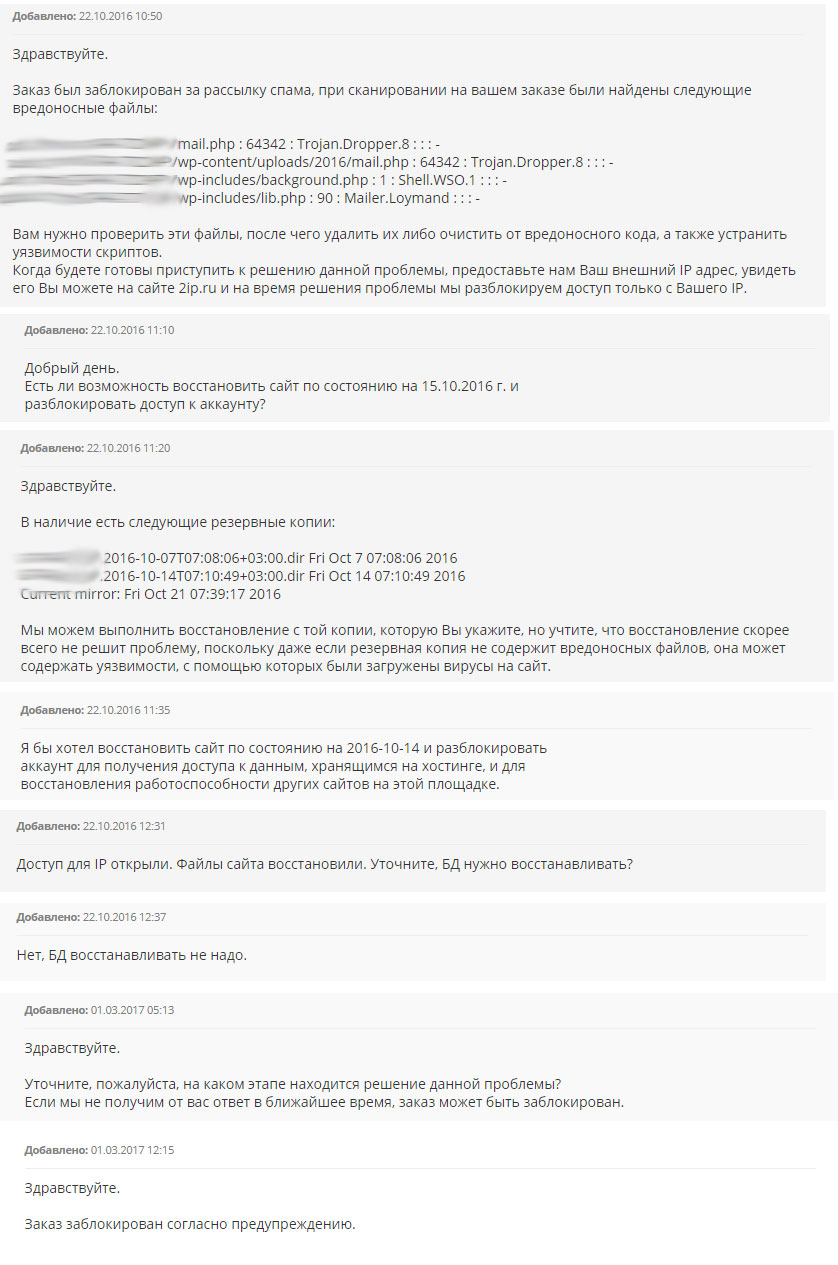

Checking the files in the root directory, we found that the site exists and no one deleted it, as a friend of the client informed us earlier . Moreover, the last entry into the account was made just after the previous hacking incident. Nobody logged in anymore.
We created a new request for technical support, with a request to clarify in which files the malicious script was found, in order to have at least some idea what to look for.
How did hacking and mailing
Having received the answer from the support service, we found the necessary file and saw it there:

Walking through all the files on the site, the same content was found in another 74 template files. After analyzing the code, checking all the ways, we realized that:
- After hacking the site’s admin panel, a malicious script was installed using the plugin installation tool.
- Through the $ _POST variable, a request was sent to the address of the site containing an execution code that was executed in all the files that had this string, and in this case there were 74 such files.
- After the script was executed, spam emails were sent from the account, whose addresses were stored in the same site database, in a separate table, which the previous developers did not bother to check.
- Also, another unrelated table was found in the database, in which the encrypted base64 code was stored, which not only recovered deleted malicious strings in all files, but also did more interesting things (more on this below ).
- Woe to the geniuses who allegedly did the cleaning last time, apparently did not want to go into the problem and do the hard work of cleaning all the files manually in order to avoid re-infection. Or they were directly related to this script ( as cleaning the site from viruses, according to the price listed on their site, was worth a small amount ).
We cleaned all the files, cleared the database, changed all access from the site and hosting, and also told technical support that the problem was fixed. The account was unlocked and the site became available again.
About the script found in the hacked site database
The script, which was encrypted in base64 encoding and was stored in the database as text, not only performed the function of recovering all deleted lines of malicious code, but was also a bruteforce script.
The main function that he performed was to send POST and GET requests to the addresses of admins of various sites, with logins and passwords, also stored in one of the database tables. After a successful selection operation, he wrote down the correct pair of login: password in another table, access to which could be obtained by contacting the correct request to one of 74 infected files, right from the browser window.
By such manipulations, the attackers not only accelerated the process of collecting passwords, but also increased the base of sites from which spam was sent and other passwords were picked.
Such a cycle can continue indefinitely. If one of the site owners finds a virus and removes it, then this is a small loss for intruders, because they have a huge base of such loopholes at their disposal, which is increasing every day.
PS: for those who want to see the script . Screenshots and examples of the malicious script were not uploaded due to the fact that there are always individuals who use the sample code as the basis for their offspring, and I don’t want to be the reason for creating and distributing the next malicious script.
Source: https://habr.com/ru/post/344012/
All Articles