METRO IS
Today it is impossible to imagine a large city without the metro with its lines, rules and stations, sights and its history, sometimes even known all over the world and attracting special attention. Metro functions as a separate organism, but at the same time is an integral part of the city. Similarly, information security tools in our country can no longer be imagined without the decisions of domestic manufacturers (metro stations) of various classes of systems (metro lines).
We offer a ride with us on our subway under the name "Information Security" and in detail, if you wish, stop at known or not so, or maybe just your favorite stations ....
PS The IB metro map is only an informative tool, is not responsible for the performance of metro stations and is relevant at the end of 2017. The functionality and quality of the work of the stations does not depend on their location on the map, inside the ring or outside, there is no analogy with the reports of global analytical agencies, we are in the capital of Russia! Specify the work schedule and other functioning details in an independent order.
')
Any suggestions for the restoration of stations, their closure or suggestions for making unrecorded stations are welcome! After all, the metro lines are extended, and the ICC is being built at a rapid pace ...
See you in 2018!

Metro lines














ICC
The Moscow Central Ring is also an integral part of the modern transport system of the city, which distributes the passenger traffic of the city. It is not marked on our map, but we are happy to list the most significant stations.
We offer a ride with us on our subway under the name "Information Security" and in detail, if you wish, stop at known or not so, or maybe just your favorite stations ....
PS The IB metro map is only an informative tool, is not responsible for the performance of metro stations and is relevant at the end of 2017. The functionality and quality of the work of the stations does not depend on their location on the map, inside the ring or outside, there is no analogy with the reports of global analytical agencies, we are in the capital of Russia! Specify the work schedule and other functioning details in an independent order.
')
Any suggestions for the restoration of stations, their closure or suggestions for making unrecorded stations are welcome! After all, the metro lines are extended, and the ICC is being built at a rapid pace ...
See you in 2018!

Metro lines

SIEM
Security Information and Event Management
A tool to automate the process of identifying and responding to information security incidents, collects and analyzes information security events, and as a result identifies and signals the occurrence of incidents.
A tool to automate the process of identifying and responding to information security incidents, collects and analyzes information security events, and as a result identifies and signals the occurrence of incidents.
| No | Company / Website | Product / Description |
|---|---|---|
| one | SearchInform / SearchInform LLC searchinform.ru | SearchInform SIEM searchinform.ru/products/siem |
| 2 | RUSIEM / First Russian SIEM rusiem.com | RUSIEM rusiem.com/node/135 |
| 3 | NPO Echelon / NPO Echelon npo-echelon.ru | Comrad npo-echelon.ru/production/65/11174 |
| four | Positive Technologies / Positive Technologies www.ptsecurity.com | MaxPatrol SIEM www.ptsecurity.com/ru-ru/products/mpsiem |
| five | ITB / ITB LLC www.itb.spb.ru | Security Capsule SIEM www.itb.spb.ru/products/Security_Capsule_SIEM |

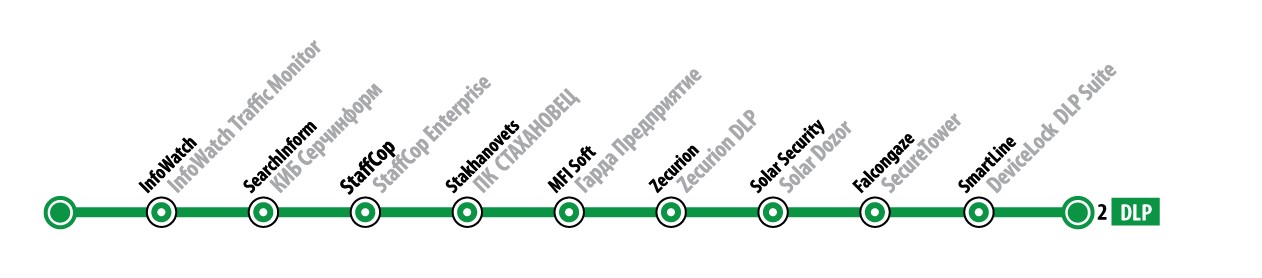
DLP
Data Loss Prevention
Information leakage protection systems are designed to track and block unauthorized data transfer attempts outside the corporate network. In addition to preventing information leaks, DLP can perform functions of tracking user actions, recording and analyzing their communications.
Data Loss Prevention
Information leakage protection systems are designed to track and block unauthorized data transfer attempts outside the corporate network. In addition to preventing information leaks, DLP can perform functions of tracking user actions, recording and analyzing their communications.
| No | Company / Website | Product / Description |
|---|---|---|
| one | InfoWatch / Infofotch Group www.infowatch.ru | InfoWatch Traffic Monitor www.infowatch.ru/products/traffic_monitor |
| 2 | SearchInform / SearchInform LLC searchinform.ru | KIB Serchinform searchinform.ru/products/kib |
| 3 | StaffCop / Atom Security LLC www.staffcop.ru | StaffCop Enterprise www.staffcop.ru/uchet-rabochego-vremeni |
| four | Stakhanovets / Stakhanovets LLC stakhanovets.ru | PC STAKHANOVETS stakhanovets.ru/kontrol-sotrudnikov |
| five | MFI Soft / MFI Soft LLC www.mfisoft.ru | Garda Enterprise www.mfisoft.ru/direction/ib/garda-predpriyatie |
| 6 | Zecurion / Company Zecurion www.zecurion.ru | Zecurion DLP www.zecurion.ru/solution/dlp/data-loss-prevention |
| 7 | Solar Security / Solar Security Ltd. www.solarsecurity.ru | Solar dozor www.solarsecurity.ru/products/solar_dozor |
| eight | Falcongaze / Falcongeys LLC falcongaze.ru | SecureTower falcongaze.ru/product/capabilities/data-leaks.html |
| 9 | SmartLine / Smart Line Inc. www.devicelock.com | DeviceLock DLP Suite www.devicelock.com/ru/products |

PKI
Public Key Infrastructure
Control system of cryptographic protection. The purpose of a PKI is to define a policy for issuing digital certificates, issuing and revoking them, storing the information necessary for subsequent verification of the validity of certificates.
Control system of cryptographic protection. The purpose of a PKI is to define a policy for issuing digital certificates, issuing and revoking them, storing the information necessary for subsequent verification of the validity of certificates.
| No | Company / Website | Product / Description |
|---|---|---|
| one | Avanpost / Avanpost LLC www.avanpost.ru | Avanpost PKI www.avanpost.ru/products/avanpost_pki.php |
| 2 | Aladdin-rd / Aladdin R.D. www.aladdin-rd.ru | JaCarta Management System www.aladdin-rd.ru/catalog/jms |
| 3 | Aktiv Co. / Company Active www.rutoken.ru | KeyBox Rutoken www.rutoken.ru/products/all/rutoken-keybox |
| four | Infotecs / OAO InfoTeKS infotecs.ru | ViPNet PKI Client infotecs.ru/product/vipnet-pki-client.html |
| five | Indeed Identity / Company Indid indeed-id.ru | Indeed card management indeed-id.ru/smart_card_management.html |

IDM
Identity management
The main task of IDM systems is the centralized management of accounts and access rights to information resources.
The main task of IDM systems is the centralized management of accounts and access rights to information resources.
| No | Company / Website | Product / Description |
|---|---|---|
| one | Informzaschita / GK Informzaschita www.infosec.ru | Kub www.cube-system.ru/ru/products/O%20producte |
| 2 | Solar Security / Solar Security Ltd. www.solarsecurity.ru | Solar inRights www.solarsecurity.ru/products/solar_inrights |
| 3 | Avanpost / Avanpost LLC www.avanpost.ru | Avanpost IDM www.avanpost.ru/products/avanpost_idm.php |
| four | 1IDM / Odin Idyem LLC 1idm.ru | 1IDM 1idm.ru/opportunities |

SSO
Single sign-on
Single sign-on technology allows users to log in to systems or applications with a single identifier, without having to re-enter their account information.
Single sign-on technology allows users to log in to systems or applications with a single identifier, without having to re-enter their account information.
| No | Company / Website | Product / Description |
|---|---|---|
| one | Avanpost / Avanpost LLC www.avanpost.ru | Avanpost SSO, WEB SSO www.avanpost.ru/products/avanpost_sso.php |
| 2 | Indeed Identity / Indeed Identity Company indeed-id.ru | Indeed Enterprise SSO indeed-id.ru/sso_login.html |
| 3 | REAK SOFT / REAK SOFT LLC identityblitz.ru | Blitz Identity Provider identityblitz.ru/products/blitz-identity-provider |

Sgrc
Security Governance, Risk, Compliance
Control system, automation and measurement of information security processes.
Control system, automation and measurement of information security processes.
| No | Company / Website | Product / Description |
|---|---|---|
| one | R-Vision / R-Vision LLC rvision.pro | R-Vision Security GRC Platform rvision.pro/sgrc |
| 2 | ePlat4m / KIT LLC www.eplat4m.ru | EPLAT4M SECURITY GRC www.eplat4m.ru/catalog/id/3 |
| 3 | Security Vision / GK Intellectual Security www.securityvision.ru | ASIMS Security Vision www.securityvision.ru/overview/video |

Waf
Web Application Firewall
Application level protective screen designed to detect and block modern attacks on web applications.
Application level protective screen designed to detect and block modern attacks on web applications.
| No | Company / Website | Product / Description |
|---|---|---|
| one | Positive Technologies / Positive Technologies www.ptsecurity.com | PT Application Firewall www.ptsecurity.com/ru-ru/products/af |
| 2 | InfoWatch / Infofotch Group www.infowatch.ru | InfoWatch Attack Killer WAF www.infowatch.ru/products/attack_killer/waf |
| 3 | Security Code www.securitycode.ru | WAF Continent www.securitycode.ru/products/kontinent-waf |
| four | SolidSoft / SolidSoft LLC solidwall.ru | Solidwall WAF solidwall.ru/datasheets/SolidWall_WAF_DS_ru.pdf |
| five | Qrator Labs / LLC El-El El qrator.net/ru | Qrator WAF qrator.net/ru/solutions/waf |

Code analysis
Automated process of reviewing code, identifying errors, flaws and vulnerabilities in the source code of programs.
| No | Company / Website | Product / Description |
|---|---|---|
| one | Positive Technologies / Positive Technologies www.ptsecurity.com | PT Application Inspector www.ptsecurity.com/ru-ru/products/ai |
| 2 | Solar Security / Solar Security Ltd. www.solarsecurity.ru | Solar incode solarsecurity.ru/products/solar_inCode |
| 3 | InfoWatch / Infofotch Group www.infowatch.ru | InfoWatch Appercut www.infowatch.ru/products/appercut |

SKZI
Means of cryptographic protection of information
It allows you to store information in encrypted form by means of a special security program that encrypts and decrypts data based on a digital signature issued by the certification authority.
It allows you to store information in encrypted form by means of a special security program that encrypts and decrypts data based on a digital signature issued by the certification authority.
| No | Company / Website | Product / Description |
|---|---|---|
| one | ISBC Group / ISBC Group www.isbc.ru | ESMART Token www.esmart.ru/product |
| 2 | Aktiv Co. / Company Active www.rutoken.ru | RUTOKEN EDS 2.0 www.rutoken.ru/products/all/rutoken-ecp |
| 3 | Security Code www.securitycode.ru | Jinn client www.securitycode.ru/products/jinn-client |
| four | Cryptopro / CRYPTO-PRO LLC www.cryptopro.ru | CryptoPro CSP www.cryptopro.ru/products/csp |

PUM
Privileged User Management
Solutions to control privileged users allow you to centrally manage privileged accounts, monitor the actions of internal system administrators, as well as external contractors, preventing possible leakage of critical data through access control, recording sessions, and auditing actions performed by users with advanced powers.
Solutions to control privileged users allow you to centrally manage privileged accounts, monitor the actions of internal system administrators, as well as external contractors, preventing possible leakage of critical data through access control, recording sessions, and auditing actions performed by users with advanced powers.
| No | Company / Website | Product / Description |
|---|---|---|
| one | IT Bastion / IT BASTI LLC it-bastion.com | SKDPU it-bastion.com/production/skdpu |
| 2 | NewInfosec / New Security Technologies LLC www.newinfosec.ru | Safeinspect www.newinfosec.ru/content/safeinspect |
| 3 | Zecurion / Company Zecurion www.zecurion.ru | Zecurion PAM www.zecurion.ru/products/pam |

Anti-apt
Anti-Advanced Persistent Threat
Protection against targeted attacks, detection of nonstandard external attacks carried out by attackers using specialized software.
Protection against targeted attacks, detection of nonstandard external attacks carried out by attackers using specialized software.
| No | Company / Website | Product / Description |
|---|---|---|
| one | InfoWatch / Infofotch Group www.infowatch.ru | InfoWatch ASAP www.infowatch.ru/products/asap |
| 2 | Group-IB / Information Security Group www.group-ib.ru | TDS complex www.group-ib.ru/tds.html |
| 3 | Kaspersky Lab / JSC Kaspersky Lab www.kaspersky.ru | KATA Platform www.kaspersky.ru/enterprise-security/anti-targeted-attacks |

Anti-DDos
Anti-Distributed Denial of Service
DDoS attacks, distributed denial of service attacks, which result in the disruption or total blocking of users' access to a site or network resource. DDoS protection solutions analyze traffic and detect anomalies in real time. In the event of an attack, traffic clearing is turned on, only legitimate users are skipped, so there is no loss of clients who cannot connect to the Internet resource.
DDoS attacks, distributed denial of service attacks, which result in the disruption or total blocking of users' access to a site or network resource. DDoS protection solutions analyze traffic and detect anomalies in real time. In the event of an attack, traffic clearing is turned on, only legitimate users are skipped, so there is no loss of clients who cannot connect to the Internet resource.
| No | Company / Website | Product / Description |
|---|---|---|
| one | InfoWatch / Infofotch Group www.infowatch.ru | InfoWatch Attack Killer AntiDDoS www.infowatch.ru/products/attack_killer |
| 2 | Variti / Variti Ltd. variti.com | Active Bot Protection variti.com/ru-ru/innovations/#protection-against-ddos-attacks-without-ip-address-blocking |
| 3 | Qrator Labs / LLC El-El El qrator.net/ru | Qrator DDoS Protection qrator.net/ru/solutions/ddos/how-qrator-works |
| four | Kaspersky Lab / JSC Kaspersky Lab www.kaspersky.ru | Kaspersky DDoS Protection www.kaspersky.ru/enterprise-security/ddos-protection |

Edr
Endpoint Detection and Response
The system of detection of new threats of high complexity in the workplace and rapid response to them.
The system of detection of new threats of high complexity in the workplace and rapid response to them.
| No | Company / Website | Product / Description |
|---|---|---|
| one | Kaspersky Lab / Kaspersky Lab www.kaspersky.ru | Kaspersky EDR www.kaspersky.ru/enterprise-security/endpoint-detection-response-edr |

UTM
Unified Threat Management
Universal solution in the field of computer security, providing powerful comprehensive protection against network threats.
Universal solution in the field of computer security, providing powerful comprehensive protection against network threats.
| No | Company / Website | Product / Description |
|---|---|---|
| one | Zecurion / Company Zecurion www.zecurion.ru | Zecurion UTM www.zecurion.ru/products/utm |
| 2 | Altell / AltEl www.altell.ru | Altell neo www.altell.ru/products/neo |
| 3 | Entensys / LLC ESL Development www.entensys.com | Userate UTM www.entensys.com/ru/products/usergate-utm/overview |

AntiVirus
The solution for detecting computer viruses, malware and recovering infected (modified) files, preventing the infection (modifying) of files or the operating system by preventing malicious code.
| No | Company / Website | Product / Description |
|---|---|---|
| one | Kaspersky Lab / JSC Kaspersky Lab www.kaspersky.ru | Kaspersky Security for Business www.kaspersky.ru/enterprise-security/endpoint |
| 2 | Dr.Web / Doctor Web www.drweb.ru | Dr.Web Enterprise Security Suite products.drweb.ru/enterprise_security_suite |
ICC
The Moscow Central Ring is also an integral part of the modern transport system of the city, which distributes the passenger traffic of the city. It is not marked on our map, but we are happy to list the most significant stations.
| No | Decision class | Company / Website | Product / Description |
|---|---|---|---|
| one | IRM (Information Right Management) | Perimetrix / Perimetrix perimetrix.ru | Perimetrix SafeSpace perimetrix.ru/content/view/43/154 |
| 2 | Data Classification | Cross Technologies / AO Cross Technologies crosstech.su | Crosstech DSS crosstech.su/catalog/crosstech/crosstech-docs-security-suite-dss |
| 3 | ILD (Information Leaks Detection) | Everytag / EvryTag Company everytag.ru | ILD - document distribution control everytag.ru/produkty/ild.html |
| four | Print protection | Cross Technologies / AO Cross Technologies crosstech.su | Printerguard crosstech.su/catalog/crosstech/printerguard |
| five | Print protection | ARTI / Company ARTI www.arti.ru | ARTI PrintXpert www.arti.ru/services/printxpert |
| 6 | Database Security | MFI Soft / MFI Soft LLC www.mfisoft.ru | Garda DB www.mfisoft.ru/direction/ib/garda-bd |
| 7 | Database Security | DataArmor / Armor LLC www.dataarmor.ru | DataArmor Database Firewall www.dataarmor.ru/products |
Source: https://habr.com/ru/post/344002/
All Articles