DNS tunnel, PsExec, keylogger: parse the scheme and technical tools of attack
There is an opinion that international corporations and large companies, which keep up with the times in providing services to their clients, also precisely build processes in all areas of their activities, including information security. Unfortunately, this is not always the case.
Some time ago, a large company with a developed infrastructure turned to us for help. The problem was strange events in the infrastructure of the company:
')
- Workstations and servers suddenly went to reboot and were removed from the domain.
- Users found that their account is locked.
- Computers of some employees began to "slow down" for no apparent reason.

To analyze the situation, we connected the main infrastructure sources to the SIEM system located in the Solar JSOC cloud. To do this, we placed a collector server to collect logs at the customer’s site and built a site-to-site between the sites. In parallel, the company was sent instructions on how to set up the required level of audit, as well as a detailed description of the preparatory work for connecting the source.
At the first stage, we connected firewalls and proxies, antivirus, logs of domain controllers and DNS. By the evening of the next day we had logs of all the necessary systems.
The first thing that could be detected was an appeal from 12 workstations to Corkow / Metel management servers. It turned out that for more than two years, the client parts of one of the modifications of the Win32 / Corkow virus remained unnoticed by anyone in the company's infrastructure, despite the presence of anti-virus software. The malware sent telemetry to the long-shut down management servers (the domain names of the servers were named after two great Russian artists and are widely known to security analysts). The anti-virus vendor, whose software was used in the company, did not add the known signatures to its databases, therefore, it could not detect the virus.
But the matter turned out to be not in this, albeit a sensational, but no longer a dangerous virus. Literally after several hours of monitoring, for the first time in the actual practice of Solar JSOC, a full-fledged, non-test, DNS tunnel was sent, sending information from several hosts of the company's infrastructure.
DNS-tunnels can be called delights in the daily life of a security guard. They are used quite rarely, but recently they have been highlighted in a number of high-profile cases of international scope as a channel for displaying information outside the company's perimeter.First of all, measures were taken to block external addresses on all edge network devices.
But the danger of DNS tunnels lies not only in the fact that they can stealthily steal data from the infrastructure. DNS tunnels allow you to build a reverse shell with an end host, which allows you to control its actions remotely.
Despite the fact that DNS tunnels are a very old topic, and all IPS and NGFW solutions must detect them, in practice this is far from the case. The slightest change of parameters (for example, the transfer of payload in the key field or another field of the standard DNS format, or outside the standard fields of the DNS query) makes it easy to bypass the standard signatures.
Immediately after the discovery of the company, a request was sent to investigate the detected sources of DNS tunnels. Several machines were connected at the local log level, and the process of taking images was started for further research.
When connecting the hosts, Solar JSOC specialists encountered the first difficulty - the Security Log was empty on all machines. At the same time, the image was investigated, and then a second difficulty arose - USN (Update Sequence Number) and MFT (Master File Table) did not contain any significant information, the latter - due to frequent planned defragmentation of disks.
The first essential information was found in the logs of the domain controllers - access to the hosts under the domain administrator account was detected there. Log in with logon type 3 - network input.
Further, analyzing on all potentially compromised System Log hosts that have not been cleared, we discovered the installation of the it_helpdesk service. After analyzing the MD5 sums, it became clear that this is the renamed PsExec utility. The company's IT department confirmed that this software is not a corporate standard of administration and is not used by employees.
PsExec is part of PsTools, a free utility package developed by Sysinternals and then acquired by Microsoft. They are designed to simplify the administration of Microsoft Windows operating systems. The PsExec utility itself allows you to remotely execute processes.
PsExec allows you to redirect input and output data of a remotely executed executable program by using SMB and the hidden $ ADMIN share on a remote system. Using this resource, PsExec uses the Windows Service control Manager API to start the PsExecsvc service on a remote system, which creates a named pipe, which PsExec runs on.
After that, the information security department of the company, using the centralized infrastructure management system, identified all the hosts on which the service had ever been launched. The total number of such hosts has exceeded 40 units.
Now back to the study of images of workstations. An analysis of the current state of the file system of one of the machines and the reproduction of the infection under laboratory conditions gave a clear chronology of the infection:
Stage I
- Rename the original system_dll.dll library to system_dll2 and create the system_dll.dll malicious object. In doing so, system_dll.dll calls system_dll2 for functions that are not defined in its code. system_dll.dll is a malicious object of the PE type, which serves to load the _________. dll library.
- Creating _________. Dll - is a malicious object of PE type, which is used to establish connection with arbitrary servers using the DNS protocol and execute various commands. This library is loaded by the malicious object system_dll.dll.
- The last time it-helpdesk was started on the machine, the C: \ Windows \ system32 \ shutdown.exe object is supposedly launched to initiate the operating system reboot. This reboot is required for the System Service to load the System_dll.dll malicious library into its address space.
Stage II
- After the operating system has been restarted, error events of the rezolv of the domain random symbols.xxxxx.su appear, which may indicate the functioning of the hidden data channel using the DNS protocol (arbitrary data is transmitted in the domain name of the 3rd level).
- Creation of the Windows / System32 / malware_dll.dll library, which is a malicious object of the PE type, used to intercept data entered from the keyboard. The intercepted data is stored in the% USER% / AppData / LocalLow / NTUSER.DAT file. The data in the file is encoded using byte-coding with subtraction of byte 10H.
- Creation on the attacked host of a malicious object jusched.exe, which serves to reload the malware_dll.dll library. At the same time, the jusched.exe object is registered in the autoload (HKLM \ Software \ Microsoft \ Windows \ CurrentVersion \ Run registry key), this means that the system will load this object at the start of the session from any user.
Stage III
- At the subsequent creation of a user session, his profile is loaded, the keylogger is started, the LocalLow / NTUSER.DAT file is created and the keylogger results are recorded in it for the entire user session.
- Also at this stage, the archiver is launched from the rar.exe command line in order to create the archive C: \ ProgrammData \ 0.0. This archive contains a shadow copy of the SAM file and the registry branch HKLM \ SYSTEM. This file bundle can be used to extract account hashes from a SAM file.
- In some cases, this stage is accompanied by multiple operating system reloads, execution of the wevtutil, gpscript, nslookup, cmdkey, etc. commands, as well as clearing the Application log.
- On one of the studied machines, the creation and multiple launches of the tvnserver.exe object were recorded while the malicious users.exe object appeared on the machine and the keys 000 and 001 were written to the HKLM \ Software \ Corporation registry key with the malware configuration.
The general pattern of infection is as follows:

Description of the tools used to implement the attack
The following malware components were used to launch an attack on the images of workstations and servers studied:
Component name | Component assignment |
Malware_dll.dll | Keylogger (32-bit version) |
Malware_dll64.dll | Keylogger (64-bit version) |
Bach.dll | Renamed the original System_dll.dll library, which is a SystemService service |
System_dll.dll | A library that, when the System_Service service starts, is swapped into svchost.exe. System_dll.dll supports the same calls as system_dll2.dll by redirecting all these functions to system_dll2.dll. Pulls up _________. Dll. Is a 32-bit version |
System_dll.dll_ | 64-bit version of System_dll.dll |
_________. dll | BackDoor, 32-bit version |
_________. dll_ver2 | 64-bit version _________. Dll |
S64 | Analogue System_dll.dll for x64 architecture |
P64 | Analog _________. Dll for x64 architecture |
It_helpdesk.exe | Renamed PsExesvc.exe (a PSExec component that is created and launched on a remote machine in order to perform specified actions |
Users.exe | BackDoor. The functionality is similar to _________. Dll, but disguised as jusched.exe - “Java Update Scheduler” |
Malicious activity
- Malware_dll.dll:
- Creating the file "\% APPDATA% \ LocalLow \ NTUSER.DAT".
- Creating mutex "mbowefvncwiomcowermg32".
- Sets the keystroke capture on the keyboard.
- Encrypt the data and then write to the file from the first paragraph.
- System_dll.dll:
- Autorun via System Service.
- Download _________. Dll.
- _________. dll and users.exe:
- Sending DNS addresses to rezolv:
- www.gf8ealht9d22________________.com
- 832v1hda31sqfcl5bh81lmqk74z.xxxxxxxxx.com
- 13bmvqdr1ju64dqm6n8877hbo0z.xxxxxxxxx.com - Sending DNS packets to the management server (xxxxx.su).
- Execution of commands received from the management server.
- It is possible to create registry keys for storing data between process restarts in HKLM or HKCU branches:
- \ Software \ Corporation \ 000
- \ Software \ Corporation \ 001
- \ Software \ Corporation \ 002
- Sending DNS addresses to rezolv:
Client communication with the server
All server communication with the client is encrypted. Encryption key: 25 d9 01 4c 21 c9 ed 89 86 14 8d 05 _________
The virus sends DNS-packets to the management server for a resolv. The DNS name, starting with the third subdomain, is encoded data.
Packets of the form <27 symbols> .xxxxx.su are sent to the server. The sequence may be more than 27 characters, but the minimum batch of 27 characters. A sequence of 27 characters is the encrypted data that the client sends to the server. This package does not carry any information other than pseudo-random numbers and the hash-sum of the package. Pseudo-ordinal numbers are needed so that after all the transformations the packages do not look like each other. A packet of 27 characters tells the server that it is ready to accept the command for processing. An example of such a package:
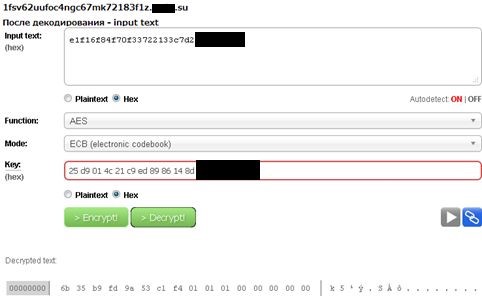
In response, a command comes in the form of 6 ipv4 addresses - 24 bytes of data. These addresses are written sequentially and sorted by the low octet. Rejecting the lower octets, we get a sequence of 18 bytes.
The first byte is the amount of unused data (n = 1-3).
The last n bytes are pseudorand and are not used further.
The remaining bytes are encrypted data with the key above.
The first three bytes are a pseudo-random number and a hash-sum of the packet, which makes one and the same command from the server visually different, which is why ip-addresses seem random. The rest is the team.
Next Steps and Mitigation
At the first stage of the search for indicators, images of four workstations from which active DNS tunnels were recorded were analyzed.
After identifying the host and network indicators, as well as the general scheme of actions of the attackers, it was necessary to check the entire infrastructure both to identify the source of infection and to search for all compromised nodes.
The overall picture of the search for compromise indicators was as follows:
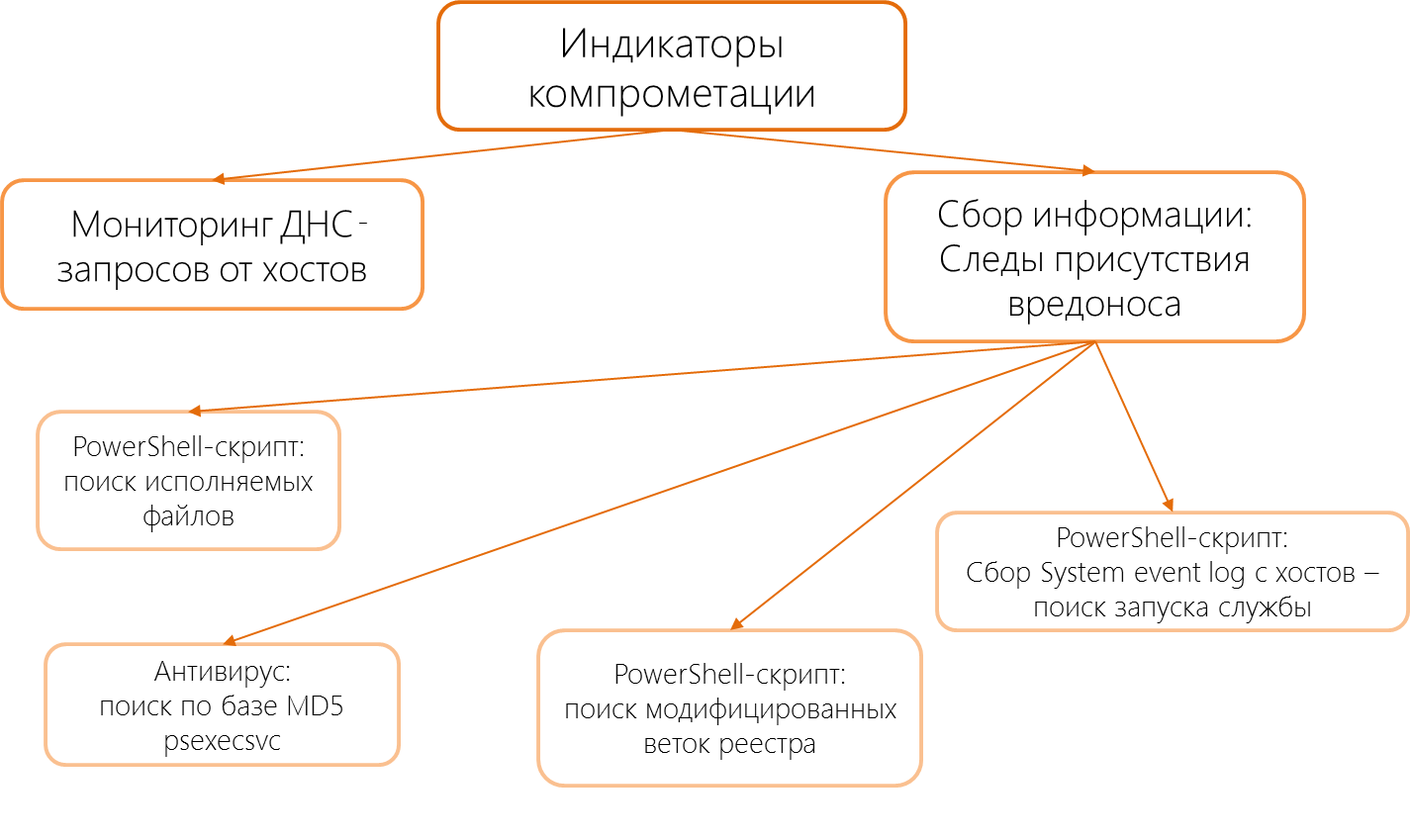
The search was carried out both by Solar JSOC specialists and by company employees. It took a total of 3 days to search. Scope of infected systems grew to 64, the number of compromised accounts potentially increased to the total number of company employees, since one of the compromised machines was a domain controller.
At the second stage, several more machines were chosen for the search for additional indicators of compromise. Images, dumps were removed, and it was possible to begin the process of "reloading" compromised hosts.
In the case of the discovery of such a massive, prolonged and deep infection, the process of cleaning out “tails” is very difficult and long. The sequence of actions was as follows:
- Work with accounts:
- Change passwords for all specified compromised accounts, including accounts from business applications.
- The privileges of service accounts were limited, a ban was imposed on the use of accounts with domain administrator rights for the operation of services.
- At the time of working with accounts, a moratorium was imposed on the use of remote access by employees, with the exception of IT administrators. In parallel, a second authentication factor was launched for them.
- Typical gaps of organizations with developed infrastructure are closed:
- Direct access to the Internet bypassing the proxy.
- Removed software classified as not-a-virus and actively using the Internet.
- The profile of open ports on the perimeter was assembled, the excess was verified and closed for a hot one, since the incident that took place allowed it.
- Administrators of application systems strengthened control over actions and transactions performed in critical business applications, especially those related to financial transactions, transactions within bonus programs and loyalty programs, access to client and partner databases, etc.
- For IT administrators, a total ban was imposed on working with critical business applications from local accounts on their AWPs. Everything was transferred to domain accounts with limited privileges under the control of the monitoring system.
Key recommendations and monitoring measures
Attackers always reserve their access to the infrastructure, therefore, in parallel, full-fledged monitoring of incidents and the profiling of all activities were carried out.
There was a separate difficulty with the latter, since, having collected a profile in two weeks, it is impossible to call it legitimate with complete certainty, because intruders could still be in the infrastructure. Therefore, it was necessary to coordinate all the collected activities with the company and, later on, to fix the collected profiles. General recommendations for identifying backup accesses were as follows:
- To audit the software installed on workstations and servers in order to identify remote management tools and illegitimate software.
- Control the launch of programs on critical computers and company servers, enter “white lists” of allowed software, especially with regard to remote management tools.
At the same time, Solar JSOC monitored activity on critical servers and workstations in the following areas:
- Network requests to known dangerous and malicious resources, as well as attempts to DNS requests to malicious domains.
- Privileged account activity - reports are daily sent to responsible employees and account holders for verification of actions.
- Changes to privileged user groups.
- Running processes on critical servers and workstations.
- Changes in system directories and critical registry branches for illegitimate executables, libraries and parameters.
- Use of remote control systems.
- Anomalies in DNS traffic.
- Virus activity on critical hosts.
- Malicious mailings.
- Anomalies in connection profiles to critical servers.
- Misuse of service accounts.
Key findings and results of the incident investigation
After the adoption of operational measures to block the threat, there was time for the information on the full report of the incident:
- The channel of entry of malware to infected machines was an account already compromised at the time of the infection, with domain administrator privileges, which was used from several machines on the company's LAN.
- The PsExec tool was used to transfer malicious files to the machine, execute remote control commands and terminate the infection of machines with the keylogger.
- Traces of other remote control software found on the infected machines under investigation were found several years ago. Among the RAT were TIghtVNC, WinVNC, Pointdev.
- As a result of the keylogger, as a rule, the user's credentials from the OS and a number of business applications, his email correspondence, critical password information files from the servers of key business applications, and passport data of employees were compromised.
- A channel for further remote control and transmission of information to attackers was a DNS tunnel.
As a final thought, I would like to note that the detection of similar incidents is the task of the Security Operations Center, but even without it, something can be done if we organize the work with the company's ordinary employees and constantly increase their Security Awareness.
Attackers often try to hide their activity from the information security service and IT administrators, since these categories of employees are competent in the field of information security and understand that various anomalies can be caused by external influences. At the same time, hackers often neglect to hide their actions from ordinary users. Increased load on the computer, strange actions on the system, suddenly opened or closed applications, the emergence of new files, icons, installed applications that the user notices can serve as an indicator of the system being compromised. Therefore, security officers need to be attentive to incoming requests, complaints from company personnel and to motivate employees to inform those responsible for the anomalies noted.
Source: https://habr.com/ru/post/343980/
All Articles