Who in medicine ISPDN in accordance with the law, he does not laugh in a circus

This article would like to somehow help medical organizations cope with the implementation of the primary measures to ensure the security of personal data when processing them in information systems.
So, what needs to be done first. In short, to bring our systems in an orderly manner, that is, to decide on what we have and carefully document this.
')
Roskomnadzor, carrying out inspections, primarily controls the implementation of the provisions of the law from a legal point of view, and not the technical part. Therefore, the absence of at least one organizational and administrative document required by law will mean a violation for them. Do you need to document a lot?
Model list of organizational and administrative documents: about 9 orders, 19 instructions and regulations, 3 provisions, including lists and rules, 5 forms and 12 journals, threat model, technical passport, acts, and so on
1. The following documents are recommended to be included in the package of organizational and administrative documents for the protection of information defining the procedure for the implementation of organizational and technical measures for the protection of personal data and information processed in information systems of the MI:
- Order on the organization of work on the protection of personal data in the enterprise (including, if necessary, on the organization of cryptographic protection of information).
- Order on the appointment of the Commission to determine the required level of security PD, processed in information systems MO.
- Acts of determining the required level of personal data protection processed in the information systems of MO.-
- Order on the creation of a structural unit responsible for ensuring the safety of personal data.
- The order approving the list of persons allowed to process PDN.
- Order on the appointment of a responsible user SKZI.
- Order on approval of the list of persons allowed to work with the SKZI.
- The order to appoint those responsible for identifying and responding to incidents.
- Order on the appointment of persons who are allowed to act on changes in the configuration of the information system and personal data protection system.
- Order on the appointment of the Commission for the destruction of key documents.
- Model of information security threats.
- Regulations on the organization and conduct of work to ensure the security of information, including but not limited to:
- Regulations on the organization of security regime premises.
- Permissive access system (access matrix).
2. The following documents are recommended to be included in the package of organizational and administrative documents on the protection of information defining the procedure for recording, storing and operating information protection tools (hereinafter referred to as SRII) MO:
- The procedure for obtaining admission (access) to PD processing.
- Consent form for the processing of personal data.
- Application form for access to PD processing.
- Form of the obligation of an employee to stop processing personal data that has become known to him in connection with the performance of official duties.
- The form of clarification to the subject of personal data of the legal consequences of failure to provide personal data.
- The form of the act of the destruction of key documents.
- A list of security events, the composition and content of information about security events to be registered and the time frame for their storage.
- The procedure for access of employees of the state or municipal authority to the premises where personal data is being processed (separately or as part of the “Regulations on the organization of the security regime for the premises”).
- Instructions to staff:
- Regulations on the use of wireless access technologies in the information system.
- Regulations for use in the information system of mobile technical means.
- Logs of accounting, storage and operation of ISPDn:
- The list of approved software.
- Technical passport ISPDn.
- Operational documentation on SKZI.
- Licenses and certificates of compliance with the requirements for the security of information on the CPA (including CIPP).
- Documents on the delivery of CPA (including CPP).
- Conclusion on the possibility of operating SZI based on the results of testing their readiness for use.
- Acts of entering SKZI in operation.
- Program and test methods.
- Conformity assessment (certificate of conformity) to information security requirements.
- Order on the organization of work on the protection of personal data in the enterprise (including, if necessary, on the organization of cryptographic protection of information).
- Order on the appointment of the Commission to determine the required level of security PD, processed in information systems MO.
- Acts of determining the required level of personal data protection processed in the information systems of MO.-
- Order on the creation of a structural unit responsible for ensuring the safety of personal data.
- The order approving the list of persons allowed to process PDN.
- Order on the appointment of a responsible user SKZI.
- Order on approval of the list of persons allowed to work with the SKZI.
- The order to appoint those responsible for identifying and responding to incidents.
- Order on the appointment of persons who are allowed to act on changes in the configuration of the information system and personal data protection system.
- Order on the appointment of the Commission for the destruction of key documents.
- Model of information security threats.
- Regulations on the organization and conduct of work to ensure the security of information, including but not limited to:
- the list of positions of employees of the state or municipal body, the replacement of which involves the processing of personal data or access to personal data;
- rules for the processing of personal data, establishing procedures aimed at identifying and preventing violations of the legislation of the Russian Federation in the field of personal data, as well as determining for each purpose of personal data processing the content of personal data, the categories of subjects whose personal data are processed, the processing and storage terms, the order of destruction when processing purposes or upon the occurrence of other legal grounds;
- rules for the consideration of requests of personal data subjects or their representatives;
- the rules for exercising internal control over the compliance of PD processing with the requirements for the protection of personal data established by the Federal Law “On Personal Data”, the regulatory legal acts adopted in accordance with it and the local acts of the operator
- rules of working with anonymous data;
- the list of positions of employees of the state or municipal body responsible for the implementation of measures for the depersonalization of PD processed.
- Regulations on the organization of security regime premises.
- Permissive access system (access matrix).
2. The following documents are recommended to be included in the package of organizational and administrative documents on the protection of information defining the procedure for recording, storing and operating information protection tools (hereinafter referred to as SRII) MO:
- The procedure for obtaining admission (access) to PD processing.
- Consent form for the processing of personal data.
- Application form for access to PD processing.
- Form of the obligation of an employee to stop processing personal data that has become known to him in connection with the performance of official duties.
- The form of clarification to the subject of personal data of the legal consequences of failure to provide personal data.
- The form of the act of the destruction of key documents.
- A list of security events, the composition and content of information about security events to be registered and the time frame for their storage.
- The procedure for access of employees of the state or municipal authority to the premises where personal data is being processed (separately or as part of the “Regulations on the organization of the security regime for the premises”).
- Instructions to staff:
- instructions of the official (security administrator) responsible for the security of information;
- user manual ISPDn;
- instructions for backing up data, hardware, software, virtual infrastructure, as well as communication channels within the virtual infrastructure;
- instructions for backup PD on backup machine media
- instructions for the destruction (deletion) or depersonalization of confidential information on computer carriers when they are transferred between users, to third-party organizations for repair or disposal;
- instruction on the organization of accounting of personal protective equipment and operational and technical documentation to them;
- instructions for organizing password protection;
- instructions of the person responsible for identifying and responding to incidents;
- instructions (regulations) on the implementation of remote access through external information networks;
- instructions on the exchange of PD with third parties;
- instructions for placement of information output (display) devices;
- instructions on how to store and destroy PD carriers;
- the instruction of the person responsible for the use of the CIPF;
- user manual SKZI;
- instructions for the restoration of communication in the event of the compromise of the valid keys to the SKZI;
- instructions for the destruction of key documents;
- Regulations on the use of wireless access technologies in the information system.
- Regulations for use in the information system of mobile technical means.
- Logs of accounting, storage and operation of ISPDn:
- register of magnetic, optical and other confidential information;
- log of user access to PDN (electronic form);
- a log of individual accounting of cryptographic tools used, operational and technical documentation for them;
- journal of accounting and issuance of media with key information;
- cryptographic users accounting log;
- personal accounts for users of cryptographic funds;
- security event log (possibly in electronic form or embedded SRMS);
- event log in the virtual infrastructure (possibly in electronic form or built-in capabilities of the SRVI);
- register of violations, the elimination of their causes and consequences;
- log book of storages, keys from storages of key documents and technical documentation;
- log of health checks for alarms;
- security log.
- The list of approved software.
- Technical passport ISPDn.
- Operational documentation on SKZI.
- Licenses and certificates of compliance with the requirements for the security of information on the CPA (including CIPP).
- Documents on the delivery of CPA (including CPP).
- Conclusion on the possibility of operating SZI based on the results of testing their readiness for use.
- Acts of entering SKZI in operation.
- Program and test methods.
- Conformity assessment (certificate of conformity) to information security requirements.
It should be remembered that according to
Regulations on the peculiarities of personal data processing carried out without the use of automation equipment (approved by the Decree of the Government of the Russian Federation of September 15, 2008 N 687)
... 6. Persons engaged in the processing of personal data without the use of automation (including employees of the operator organization or persons engaged in such processing under an agreement with the operator), note. For example, in our case, doctors should be informed about the fact that they process personal data processed by the operator without using automation tools, the categories of personal data processed, as well as the features and rules for performing such processing established by regulatory acts of federal executive bodies, executive authorities of the constituent entities of the Russian Federation, as well as local legal acts of the organization (if any).and
TK RF Article 22. Basic rights and obligations of the employer
... The employer must:
... to acquaint workers under painting with accepted local regulations directly related to their work activities;
As a result, such paper work, or rather its absence, in part or in full, can lead to problems with Roskomnadzor. One of the most striking cases is the planned on-site inspection for the Department of Health of the Ivanovo Region on December 1, 2011. At the end of the test, 14 prescriptions were issued. That was absent and has been broken in more detail under the link 37.rkn.gov.ru/news/news31219.htm
What should be done in medical organizations (hereinafter - MO) to ensure the security of our personal data?
The leaders of the Ministry of Defense by order of the Ministry of Defense determine (appoint) an official responsible for ensuring the security of personal data (PD) processed in the information systems of the Ministry of Defense.
Who will they be? There is no exact answer, but if there is no information security service in the MO, then a system administrator may be appointed as responsible. Further, the text is rather dry and difficult to read, but if you are appointed, have patience.
Employees responsible for ensuring the safety of PD in MI need to determine:
- the list and composition of the restricted access information to be protected, not constituting a state secret, processed in the information systems of the MO, including processed in an automated form (using computer equipment) at the workplaces of MO employees;
- a list of information systems of the Ministry of Defense, in which PD processing is carried out (hereinafter - personal data information systems, SPID);
- a list of state and / or municipal information systems of the Ministry of Defense, in which other information is processed (non-personal data) of limited access that does not constitute a state secret - confidential information (hereinafter - state information systems, GIS);
- boundaries of the controlled zones (in the form of perimeter schemes of protected areas and / or buildings and premises) with a description of the modes (order and rules) of access;
- data on the MO network infrastructure (communication schemes, characteristics of network equipment, parameters of connections to external networks, including public networks of providers (telecom operators) and the Internet);
- the composition of the software and software and hardware of information systems MO involved in the processing of PD;
- the list and types of actual threats, potential violators of PD security processed in the information systems of the Ministry of Defense, in accordance with [1] and [2].
1. Employees responsible for ensuring the safety of personal data in the local authorities to increase the initial level of security of the facility, determine, if necessary, measures to modernize the network structure and / or make changes in technology and procedures for processing and accessing information to be protected in information systems MO
2. To the heads of the municipality, by order of the municipality to determine (appoint) a commission to determine the required level of personal data protection processed in the mi information systems and on the classification of state and municipal information systems. Measures to determine the required levels of personal data protection processed in the MI information systems and the classification of state and municipal information systems in accordance with [3] and [4].
3. The staff responsible for ensuring the safety of PD in the MI, determine the basic set of measures to ensure the required levels of security in the MI information systems, in accordance with [4] and [5].
4. Employees responsible for ensuring the safety of PD in the MI, develop an action plan for the implementation of basic measures to protect information and work on the creation of a PD protection system (hereinafter - an action plan), in accordance with [4] and [5], including including calculation-cost assessment for the implementation of measures.
5. On the basis of the action plan, the staff responsible for the safety of personal data in a medical district shall organize the preparation of a technical task for creating a personal data protection system.
6. Prior to the commencement of work on creating an information protection system, organize and conduct the following activities:
- determine and approve by the order of the Ministry of Defense a list of persons allowed to process PD in the Ministry of Defense;
- determine the rules for processing personal data, establishing procedures aimed at identifying and preventing violations of the legislation of the Russian Federation in the field of personal data, as well as determining for each purpose of personal data processing the content of personal data, categories of subjects whose personal data are processed, terms of their processing and storage, order of destruction upon reaching the processing objectives or upon the occurrence of other legal grounds;
- determine the rules for considering requests of personal data subjects or their representatives;
- determine the rules for working with anonymous data;
- to approve the list of positions of employees of the MI, responsible for carrying out activities on the depersonalization of processed PD;
- carry out measures for the accounting, storage and organization of operation of cryptographic information protection tools (CIPP). Note These activities are carried out in the MI, which have software and / or software and technical SKZI.
7. In order to achieve results, in carrying out the work of primary measures to ensure the safety of PD when processing them in the information systems of the Ministry of Defense, legal entities licensed to carry out activities for specific types of work in accordance with Federal Law of 04.05 are allowed to be involved . 2011 № 99- “On licensing certain types of activities”.
Recommendations for the development of technical specifications for the creation of a system for the protection of PD, processed in information systems MO
1. The terms of reference for the creation of a PD protection system (NW PD) must contain requirements for the following measures for the creation of a NW PD:
- formation of requirements for SZ PDn processed in PD information systems;
- development (design) of NW PD;
- introduction of NW PD;
- performance evaluation (certification) of measures taken to protect PD and its entry into force;
- ensuring the protection of information during the operation of SZ PDN;
- ensuring the protection of information during the decommissioning of the NW PD or after a decision is made to finish the information processing.
2. Recommendations on the formation of requirements for the NW PD.
2.1. Terms of Reference for the creation of SZ PDN should display the necessary set of requirements, formed taking into account [6] and [7], including:
- determination of the required level of personal data protection processed in the MI information systems (hereinafter - the classification of the information system);
- identification of information security threats, the implementation of which may lead to the violation of information security in the information system, and the development on their basis of a model of information security threats;
- Determination of requirements for NW PD.
3. Recommendations for the development (design) of NW PD.
3.1. When designing NW PDN, the following activities should be performed:
- types of subjects of access (users, processes and other subjects of access) and objects of access, which are objects of protection (devices, filesystem objects, launched and executable modules, objects of database management system, objects created by application software, other objects of access) ;
- defined access control methods (discretionary, mandatory, role-playing or other methods), access types (read, write, execute, or other types of access) and rules for delimiting the access of subjects of access to access objects (based on lists, security labels, roles and other rules ), subject to implementation in the information system;
- selected measures to protect information to be implemented in the system of information security information system;
- the types and types of information security tools are identified that ensure the implementation of technical measures to protect information;
- the structure of the NW PDS was determined, including the composition (quantity) and location of its elements;
- selection of information security tools certified for compliance with information security requirements, taking into account their cost, compatibility with information technologies and hardware, security functions of these tools and their implementation features, as well as the level of information system security;
- software settings are defined, including software for information security tools, ensuring the implementation of information protection measures, as well as the elimination of possible information system vulnerabilities leading to information security threats;
- the measures of information protection are defined for information interaction with other information systems and information and telecommunication networks, including information systems of an authorized person, as well as when using computing resources (capacities) provided by an authorized person for information processing.
3.2. The results of the NW PDS design should be displayed in the project documentation (draft (technical) project and (or) in the working documentation)) on the NW PD, developed taking into account [8].
Project documentation should contain including:
- analysis of information processing in the designed system;
- descriptions of information flows and the network structure of the object;
- analysis of information resources requiring protection. Lists of protected information;
- model of information security threats;
- classification of the designed system according to the information security requirements
- list of information security requirements for objects of protection of the designed system
- description of technical solutions for the implementation of information security subsystems (subsystem of protection against unauthorized access, subsystem of antivirus protection, subsystem of cryptographic protection, subsystem of firewall, security analysis subsystem, backup subsystem, intrusion detection subsystem);
- consolidated list of information security tools
- a complex of organizational measures, with an indication of the list of necessary organizational and administrative documentation (PSA);
- set of templates ORD.
3.3. When designing the NW PD, the operational documentation for the information protection system of the information system should be developed taking into account [7], [8] and [9] and should, among other things, contain a description:
- the structure of the information security system information system;
- composition, installation sites, parameters and order of setting the means of information protection, software and hardware;
- rules of operation of the information system information protection system.
4. Recommendations for the implementation of NW PD.
4.1. It is recommended to implement SZ PDN in the following order:
- installation and adjustment of information security tools SZ PDN;
- development of documents defining the rules and procedures implemented by the operator to ensure the protection of information during its operation NWS (hereinafter - OSA);
- introduction of organizational measures to protect information;
- conducting preliminary tests of SZ PD;
- carrying out trial operation of SZ PD;
- conducting an analysis of vulnerabilities and taking measures to protect information to eliminate them;
- Conduct acceptance tests SZ PDN.
5. Recommendations for the conduct of conformity assessment (attestation) of ISPDN and putting it into operation
5.1. Conformity assessment (certification) ISPD should be carried out in accordance with the program and methods of certification tests prior to the processing of information to be protected in the information system.
According to the results of certification tests, protocols of certification tests are drawn up, a conclusion on the conformity of ISPDn information protection requirements and a conformity assessment (certificate of conformity) in case of positive results of certification tests.
Re-assessment of conformity (certification) of ISPDn should be carried out in case of expiry of the validity of the certificate of conformity or increase of the level of personal data protection processed in the information systems of MO. When increasing the number of threats to the security of information or changes in design solutions implemented when creating a NW PD, additional tests should be conducted as part of the current conformity assessment (certificate of conformity).
5.2. The introduction of ISPDN should be carried out in accordance with [9] and the legislation of the Russian Federation on information, information technologies and information protection and taking into account conformity assessment (certificate of conformity).
6. Recommendations for ensuring the protection of information during the operation of ISPDN.
6.1 Ensuring the protection of information during the operation of an ISPD should be carried out by the operator in accordance with the operational documentation on the NW PD and the organizational and administrative documents on the protection of information, including including:
- management (administration) of the information system information protection system;
- identification of incidents and response to them;
- configuration management of certified information system and its information security system;
- control (monitoring) of ensuring the level of security of information contained in the information system.
7. Recommendations for ensuring the protection of information when withdrawing from an ISPD operation, or after we have made a decision about the end of information processing
7.1. The protection of information during the decommissioning of the ISPD or after the decision to complete the processing of information must be carried out by the operator in accordance with the operational documentation on the NW PD and organizational and administrative documents on the protection of information, including including:
- archiving the information contained in the information system;
- destruction (erasure) of data and residual information from computer storage media and (or) destruction of computer storage media.
- formation of requirements for SZ PDn processed in PD information systems;
- development (design) of NW PD;
- introduction of NW PD;
- performance evaluation (certification) of measures taken to protect PD and its entry into force;
- ensuring the protection of information during the operation of SZ PDN;
- ensuring the protection of information during the decommissioning of the NW PD or after a decision is made to finish the information processing.
2. Recommendations on the formation of requirements for the NW PD.
2.1. Terms of Reference for the creation of SZ PDN should display the necessary set of requirements, formed taking into account [6] and [7], including:
- determination of the required level of personal data protection processed in the MI information systems (hereinafter - the classification of the information system);
- identification of information security threats, the implementation of which may lead to the violation of information security in the information system, and the development on their basis of a model of information security threats;
- Determination of requirements for NW PD.
3. Recommendations for the development (design) of NW PD.
3.1. When designing NW PDN, the following activities should be performed:
- types of subjects of access (users, processes and other subjects of access) and objects of access, which are objects of protection (devices, filesystem objects, launched and executable modules, objects of database management system, objects created by application software, other objects of access) ;
- defined access control methods (discretionary, mandatory, role-playing or other methods), access types (read, write, execute, or other types of access) and rules for delimiting the access of subjects of access to access objects (based on lists, security labels, roles and other rules ), subject to implementation in the information system;
- selected measures to protect information to be implemented in the system of information security information system;
- the types and types of information security tools are identified that ensure the implementation of technical measures to protect information;
- the structure of the NW PDS was determined, including the composition (quantity) and location of its elements;
- selection of information security tools certified for compliance with information security requirements, taking into account their cost, compatibility with information technologies and hardware, security functions of these tools and their implementation features, as well as the level of information system security;
- software settings are defined, including software for information security tools, ensuring the implementation of information protection measures, as well as the elimination of possible information system vulnerabilities leading to information security threats;
- the measures of information protection are defined for information interaction with other information systems and information and telecommunication networks, including information systems of an authorized person, as well as when using computing resources (capacities) provided by an authorized person for information processing.
3.2. The results of the NW PDS design should be displayed in the project documentation (draft (technical) project and (or) in the working documentation)) on the NW PD, developed taking into account [8].
Project documentation should contain including:
- analysis of information processing in the designed system;
- descriptions of information flows and the network structure of the object;
- analysis of information resources requiring protection. Lists of protected information;
- model of information security threats;
- classification of the designed system according to the information security requirements
- list of information security requirements for objects of protection of the designed system
- description of technical solutions for the implementation of information security subsystems (subsystem of protection against unauthorized access, subsystem of antivirus protection, subsystem of cryptographic protection, subsystem of firewall, security analysis subsystem, backup subsystem, intrusion detection subsystem);
- consolidated list of information security tools
- a complex of organizational measures, with an indication of the list of necessary organizational and administrative documentation (PSA);
- set of templates ORD.
3.3. When designing the NW PD, the operational documentation for the information protection system of the information system should be developed taking into account [7], [8] and [9] and should, among other things, contain a description:
- the structure of the information security system information system;
- composition, installation sites, parameters and order of setting the means of information protection, software and hardware;
- rules of operation of the information system information protection system.
4. Recommendations for the implementation of NW PD.
4.1. It is recommended to implement SZ PDN in the following order:
- installation and adjustment of information security tools SZ PDN;
- development of documents defining the rules and procedures implemented by the operator to ensure the protection of information during its operation NWS (hereinafter - OSA);
- introduction of organizational measures to protect information;
- conducting preliminary tests of SZ PD;
- carrying out trial operation of SZ PD;
- conducting an analysis of vulnerabilities and taking measures to protect information to eliminate them;
- Conduct acceptance tests SZ PDN.
5. Recommendations for the conduct of conformity assessment (attestation) of ISPDN and putting it into operation
5.1. Conformity assessment (certification) ISPD should be carried out in accordance with the program and methods of certification tests prior to the processing of information to be protected in the information system.
According to the results of certification tests, protocols of certification tests are drawn up, a conclusion on the conformity of ISPDn information protection requirements and a conformity assessment (certificate of conformity) in case of positive results of certification tests.
Re-assessment of conformity (certification) of ISPDn should be carried out in case of expiry of the validity of the certificate of conformity or increase of the level of personal data protection processed in the information systems of MO. When increasing the number of threats to the security of information or changes in design solutions implemented when creating a NW PD, additional tests should be conducted as part of the current conformity assessment (certificate of conformity).
5.2. The introduction of ISPDN should be carried out in accordance with [9] and the legislation of the Russian Federation on information, information technologies and information protection and taking into account conformity assessment (certificate of conformity).
6. Recommendations for ensuring the protection of information during the operation of ISPDN.
6.1 Ensuring the protection of information during the operation of an ISPD should be carried out by the operator in accordance with the operational documentation on the NW PD and the organizational and administrative documents on the protection of information, including including:
- management (administration) of the information system information protection system;
- identification of incidents and response to them;
- configuration management of certified information system and its information security system;
- control (monitoring) of ensuring the level of security of information contained in the information system.
7. Recommendations for ensuring the protection of information when withdrawing from an ISPD operation, or after we have made a decision about the end of information processing
7.1. The protection of information during the decommissioning of the ISPD or after the decision to complete the processing of information must be carried out by the operator in accordance with the operational documentation on the NW PD and organizational and administrative documents on the protection of information, including including:
- archiving the information contained in the information system;
- destruction (erasure) of data and residual information from computer storage media and (or) destruction of computer storage media.
Some technical stuff
Currently, medical and preventive treatment facilities (MPI) use the Unified State Health Information System (EGISZ). Each health care facility has its own database, it is synchronized with a common database located in the data center (MIAC). All this happens through the channels protected by PAK ViPNet. PAK ViPNet were distributed throughout the Russian Federation to organize connection to this system.
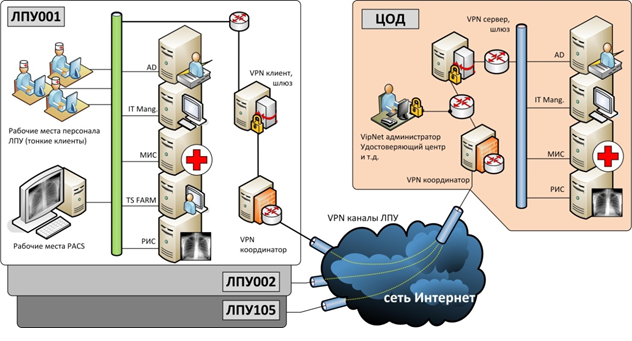
Many details can be found at portal.egisz.rosminzdrav.ru/materials
Summing up the results of the “basic informatization”, the former director of the IT department of the Ministry, Roman Ivakin, noted that it was possible to ensure “a sufficiently high level of infrastructure development”.
“As for the connection of health facilities to the Internet, then, according to our data, this task is 100% completed at the level of legal entities. Perhaps their local subdivisions, for example, FAPs (first-aid and obstetric points), remained partially uncovered. But we should not forget that there are more than 40 thousand of such facilities, and the connection work actually began only in June 2012. For comparison: it took about 1.5 years to connect 52 thousand schools to the network. ”
However, even now, not everyone has managed to bring information systems of all subordinate institutions and even more so the information protection system into a uniform form. Medical institutions can still meet the zoo of medical systems, including self-written software. Requirements for the technical part largely depend on what level of personal data protection is determined for a specific SPD. More information about the systems for processing personal data of a special category (information about the state of health), biometric PD, depersonalization, obtaining consent for processing and other features will be described in one of the following articles of our blog.
Source: https://habr.com/ru/post/343588/
All Articles