Zimbra with certificate signed by Active Directory

On one, not very beautiful day, we were forced to switch from the already-native Alt-n mDaemon to the Zimbra Collaboration Suite.
All anything, and mDaemon vs. holivar We leave Zimbra beyond the scope of the article, the transition itself went quite smoothly, but users began to worry about browser warnings and email clients about an untrusted certificate. Since the mail exchange is carried out exclusively within the corporation, mDeamon had a certificate issued by the certification authority AD, so everything was smooth there. And then I decided to Zimbra and issue a certificate from ADCS.
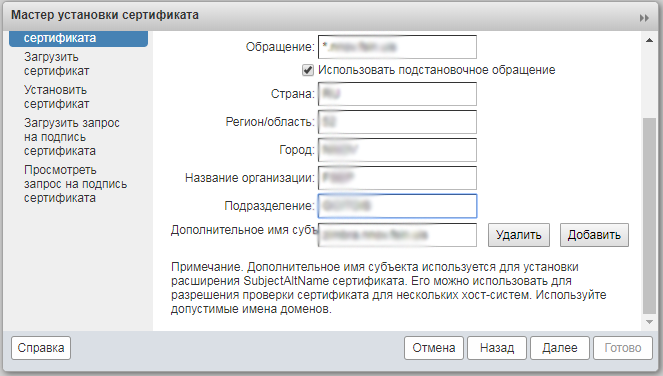
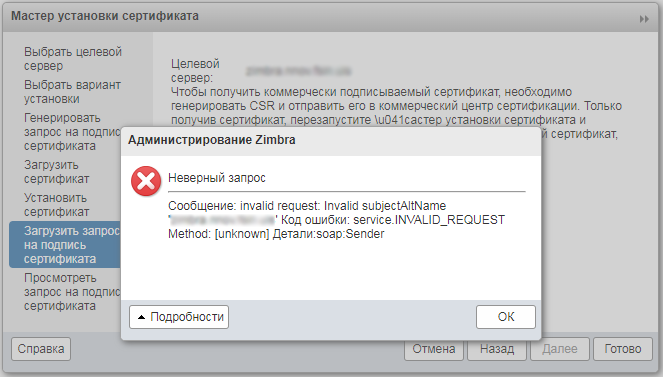
For starters, I tried through a standard web-interface dialog. But there even with standard settings there is an error.
')
True, if the Additional Subject Name field is deleted, the query generation proceeds normally.
Next, either download the commercial.csr file, or go to the SSH console, under the zimbra account and see its contents:
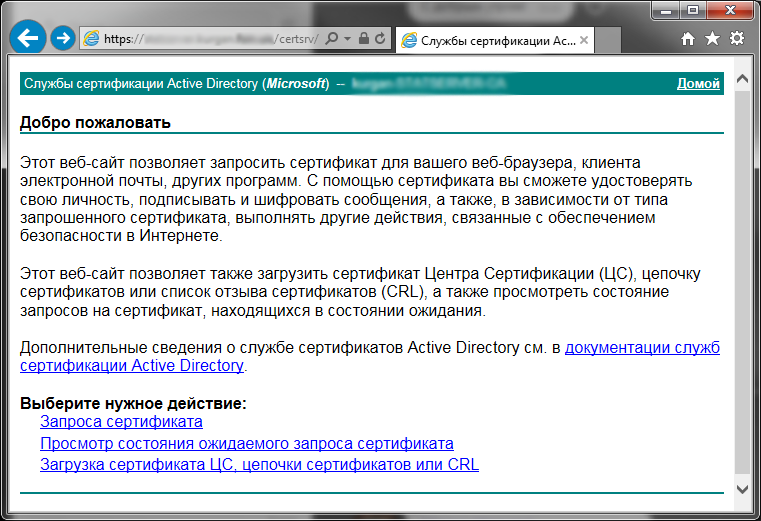
cat /opt/zimbra/ssl/zimbra/commercial/commercial.csr -----BEGIN CERTIFICATE REQUEST----- MIIC8zCCAdsCAQAwZDELMAkGA1UEBhMCUlUxCzAJBgNVBAgMAjUyMQ0wCwYDVQQH <skip> IYTKJfkDPOm5XO4pQBtufMMQnmwUrnqcfrt8LUfCsjWwiImfcUaG -----END CERTIFICATE REQUEST----- Copy its contents and go to the web interface of the certification center Active Directory. Here it is necessary to mention that only Internet Explorer can work with this interface normally.
Zimbra can only work with base-64 certificates, so we select the appropriate options.
Click “Certificate Request”, then “Advanced Certificate Request”, then “Issue request using base-64 encrypted PKCS # 10 file, or issue update request using base-64 encrypted PKCS # 7 file.”
Insert the text of the request into the first field, select the template “Web server”.

After clicking on the "Issue" button, this certificate is issued to us and you can download it (in BASE-64 form, of course).
Using the zimbra web interface, I was not able to install this certificate, so we do it using the console.
In any way we place the received certificate and CA root certificate in the / opt / zimbra / ssl / zimbra / commercial directory
Now we check the certificate for validity with the command:
[zimbra@zimbra commercial]$ zmcertmgr verifycrt comm commercial.key certnew.cer CA.cer ** Verifying 'certnew.cer' against 'commercial.key' Certificate 'certnew.cer' and private key 'commercial.key' match. ** Verifying 'certnew.cer' against 'CA.cer' Valid certificate chain: certnew.cer: OK [zimbra@zimbra commercial]$ If everything is OK, then we implement the certificate:
[zimbra@zimbra commercial]$ zmcertmgr deploycrt comm certnew.cer CA.cer ** Fixing newlines in 'certnew.cer' ** Fixing newlines in 'CA.cer' ** Verifying 'certnew.cer' against '/opt/zimbra/ssl/zimbra/commercial/commercial.key' Certificate 'certnew.cer' and private key '/opt/zimbra/ssl/zimbra/commercial/commercial.key' match. ** Verifying 'certnew.cer' against 'CA.cer' Valid certificate chain: certnew.cer: OK ** Copying 'certnew.cer' to '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' ** Copying 'CA.cer' to '/opt/zimbra/ssl/zimbra/commercial/commercial_ca.crt' ** Appending ca chain 'CA.cer' to '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' ** Importing cert '/opt/zimbra/ssl/zimbra/commercial/commercial_ca.crt' as 'zcs-user-ommercial_ca' into cacerts '/opt/zimbra/common/lib/jvm/java/jre/lib/security/cacerts' ** NOTE: restart mailboxd to use the imported certificate. ** Saving config key 'zimbraSSLCertificate' via zmprov modifyServer zimbra.domain.local...ok ** Saving config key 'zimbraSSLPrivateKey' via zmprov modifyServer zimbra.domain.local...ok ** Installing ldap certificate '/opt/zimbra/conf/slapd.crt' and key '/opt/zimbra/conf/slapd.key' ** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/slapd.crt' ** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/slapd.key' ** Creating file '/opt/zimbra/ssl/zimbra/jetty.pkcs12' ** Creating keystore '/opt/zimbra/mailboxd/etc/keystore' ** Installing mta certificate '/opt/zimbra/conf/smtpd.crt' and key '/opt/zimbra/conf/smtpd.key' ** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/smtpd.crt' ** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/smtpd.key' ** Installing proxy certificate '/opt/zimbra/conf/nginx.crt' and key '/opt/zimbra/conf/nginx.key' ** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/nginx.crt' ** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/nginx.key' ** NOTE: restart services to use the new certificates. ** Cleaning up 3 files from '/opt/zimbra/conf/ca' ** Removing /opt/zimbra/conf/ca/ca.key ** Removing /opt/zimbra/conf/ca/ca.pem ** Removing /opt/zimbra/conf/ca/d8183cc3.0 ** Copying CA to /opt/zimbra/conf/ca ** Copying '/opt/zimbra/ssl/zimbra/ca/ca.key' to '/opt/zimbra/conf/ca/ca.key' ** Copying '/opt/zimbra/ssl/zimbra/ca/ca.pem' to '/opt/zimbra/conf/ca/ca.pem' ** Creating CA hash symlink 'd8183cc3.0' -> 'ca.pem' ** Creating /opt/zimbra/conf/ca/commercial_ca_1.crt ** Creating CA hash symlink '0c6ba62c.0' -> 'commercial_ca_1.crt' [zimbra@zimbra commercial]$ You can view the applied certificate with the command
zmcertmgr viewdeployedcrt After all, restart the service zimbra
zmcontrol restart Check the result:

There are no warnings, the service is visible as valid. As required!
Source: https://habr.com/ru/post/343560/
All Articles