How I hacked into cryptocurrency companies and earned $ 60,000 from it

Bitcoin and cryptocurrencies in general are now widely known. My acquaintance with cryptocurrencies happened about 5 months ago, that was when I started investing in bitcoin and ethereum, the rate at that time was $ 1,900 per btc and $ 89 per broadcast. In order for you to understand what kind of profit I received, I will say that at the time of this writing, Bitcoin costs $ 18,100, and the broadcast price is $ 830 and continues to go into orbit along with the rest of the cryptocurrencies. I thought it would be great to see how secure the services are, in which I keep my cryptocurrency savings, trade them or give them to trust management.
Back in late spring, I bought access for an insider of one investment club for $ 500. I bought more coins for myself, except for ether and bitcoin, and at the end of August I received a recommendation that I could give my bitcoins to traders at% 15 per month, which is why I started my way from sites that trust.
The first company - example1.com (banned from disclosing the names associated with their websites) is very popular and known to many investors. Before investing money there, I decided to check my personal account for vulnerabilities. I registered, but surprisingly I didn’t find anything, filtering everywhere, csrf tokens, and so on. Then I registered another account, but instead of the name I entered a sniffer script. I didn’t receive anything for a long time, I had already come to terms with the fact that the project is doing well with security, there are no BLIND XSS and other things, but only until the moment when the logs came to me (source code, administrator ip, local storage, etc.)
JS was executed when the admin checked the page with information about the user admin.example1.com/user/default/index?page=75 . Similar vulnerabilities are increasingly found on hackerone, an example of https://hackerone.com/reports/251224 .
')
After reviewing the logs, I was upset that all the cookies with the httponly flag and could not get any, in the end, I could not get access to the admin panel, but when I clicked the link admin.example1.com/user/default / index? page = 75 , I saw that the admin panel can be used without authorization - this is a gross developer error.
In total, it was possible to view and change information about 2010 users (email, phone, links to social networks, wallet for outputting bitcoin, login, balance, referrer). In the screenshot, one of the richest investors in the club, he has a large number of subscribers and I constantly follow his blog. He recommended to all his subscribers to invest their money in this control, of course, by referral link, but not more than% 20 of capital. After a short period of time, he managed to earn 20 Bitcoins, which is equal to $ 360,000 today.

An attacker without any preparation or experience could easily go into the admin area and change the email addresses of all investors to their own (or simply change the wallets for withdrawal, so as not to cause undue suspicion when the victim decides to withdraw money, because when withdrawing the wallet for some reason displayed). Investors there are quite large, many have deposits> 0.5btc. It is very strange that open passwords are not indicated in the admin panel, -
I have a feeling that the developers of this remote control are capable of anything in terms of worsening the security of their service.
After the discovery of the vulnerability, I sent a report to the developers, they, in turn, contacted the creator and removed the vulnerability ... I was offered to accrue the reward to the account in my account, where I will receive% and in six months I will be able to go to breakeven, and in a year I will take body. A month later, when I found a similar blind xss in their service and received another bounty for it, it became known that the DU developers were fired (and the money for their work seemed not to be paid for at that time), other people began to work on the development.
A little later, after the first recommendation, the second one came ( example2.com ). This is also a top, popular trust management service, it has alexarank <50,000, as well as the first company.
Having carefully checked everything, I did not find anything
Immediately after the discovery, I wrote to the developers of the site, also asked my friends from the club to write to the owner. I was told that, ostensibly, due to the fact that the user needs to follow the link - the vulnerability is absolutely not dangerous. It looked funny. After that, I wrote a couple more letters with evidence that the bug is still worth attention and should be fixed immediately, but, alas, I was ignored.
A bit later, quite predictable things happened for projects of this kind - the user details began to be massively changed, I found out about it from their developer, who wrote to me just a couple of days ago (as I understood from his words - the users themselves concluded, and the funds began to disappear) . It is terrible to imagine the loss in the event that hackers exploited the vulnerability in the withdrawal of funds. The developer asked once again to send a report about the vulnerability, after that google recaptcha and confirmation by SMS were added to the form for changing the details (to be sure).
After that, I decided to look for vulnerabilities on cryptocurrency exchanges .
I decided not to touch Poloniex, they don’t pay for vulnerabilities, and I don’t keep capital there. It is because of their ignoring security problems - the vulnerability of circumventing two-factor authentication was sold on the darknet, the link is https://t.me/vulns/43 .
I used to have $ 6000 on my account, I accidentally logged into my vpn account in Moldova, as a result, the account was immediately blocked. I had to wait for the unlocking for half a month, after this incident I took out all my money from there. It is good that they simply did not take them away, as they did with many clients.
I decided to start with livecoin.net . The exchange turned out to be well protected, found only a low-impact SELF XSS vulnerability (it remained self, there is no clickjacking on the site and csrf in the post request). Poc video
Then he decided to go to okex.com . This exchange is very popular not only in China, but throughout the world. Some function was not fully translated into English, it is in Chinese, but this did not become a problem, the google translator extension helped me quickly select the text and translate it without leaving the page. As in all other cases - I carefully checked the security, including subdomains and directories. It turned out that https://www.okcoin.com/ (6000 alexa china), https://www.okcoin.cn/ (9000 in the world, 2000 in China) have exactly the same design and functionality as okex. This means that if I find a vulnerability on one of their sites, the rest will also be exposed to it. Later I looked into the customer support service (I fantasized a little about how I poured the shell into the ticket and it was running) and discovered many vulnerabilities, I will tell about them below:
1. Vulnerability iDOR www.okex.com/question/questionDetail.do?workOrderId=2550 , allowed to view all 2500 okex tickets at that time; to date, the number has increased to 4898, and these are tickets on the exchange alone. The ticket contains the full phone number, email, real name, the text of the correspondence between the user and support and the full path to the attached attachment.
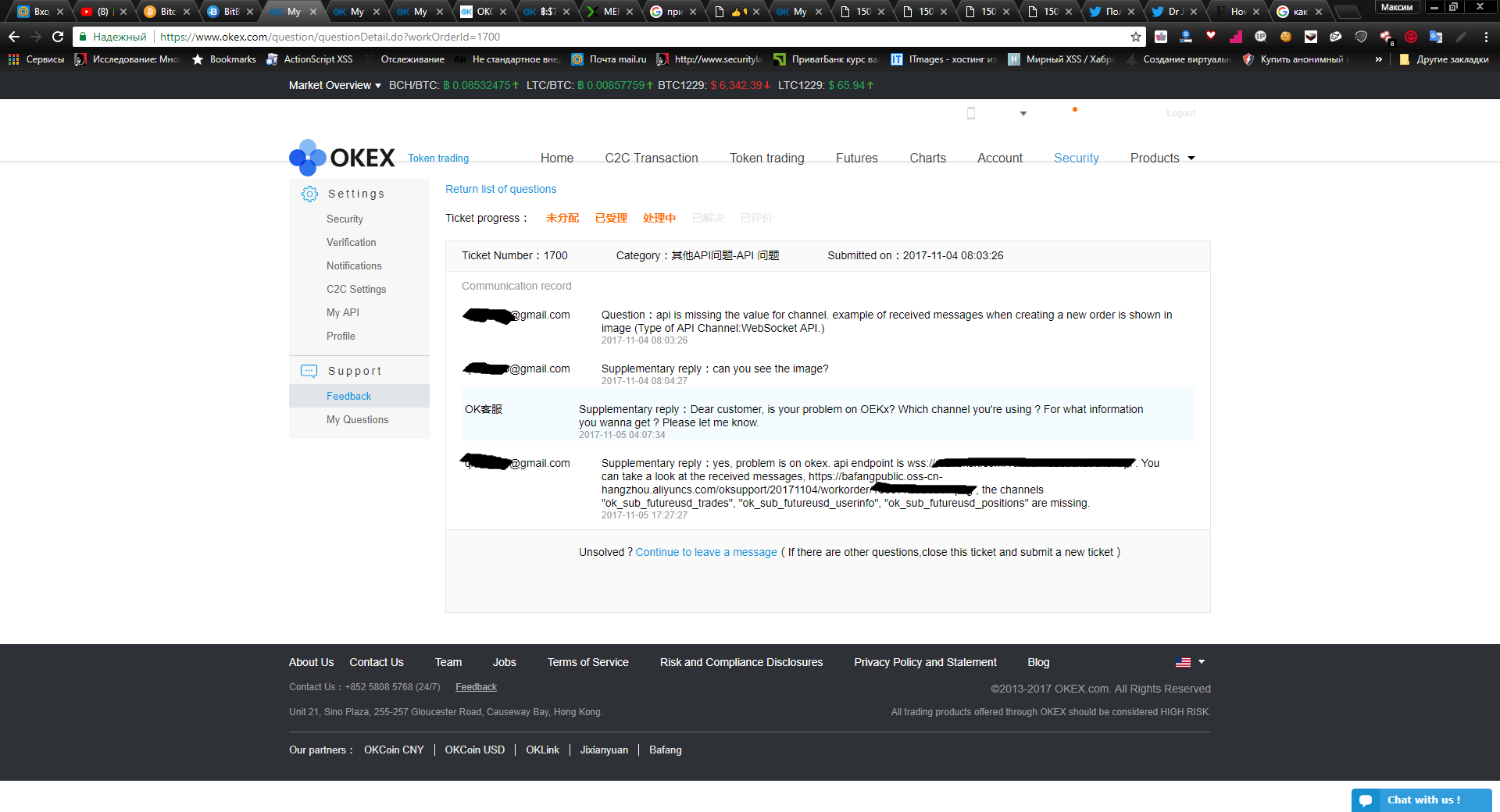
As it turned out later, many users go through the verification procedure in the support service in order to increase their withdrawal limit. It is necessary to attach a selfie along with a passport, or just a passport photo.
Here are some of these photos (Data is hidden)




In addition to passports, there are also many photos and screenshots from device screens.
I started downloading all the tickets (used as proof of the criticality of this problem). Used Burp Intruder, launched and set from 1 to 2549 on url / questionstion / questionsDetail.do?workOrderId=2550. Found that no information was loaded. I decided to go back to the support and still intercept requests, at that moment I found out that the page is loaded via get www.okex.com/v2/support/cs/work/order/2550/replies . I threw this request into the intruder and downloaded all the tickets, - now they could be freely sent to the developers of the exchanges.
2. Stored XSS in api. Our js is not displayed in the ticket /question/questionDetail.do?workOrderId=2550, apparently, there was filtering on forbidden characters. But in api / v2 / support / cs / work-order / 2550 / replies everything worked fine, even js from third-party domains were loaded.
If you combine 1 and 2 vulnerabilities, you could successfully steal a lot of money. The attack should have proceeded according to this scenario:
1) Parsim all email addresses.
2) On our page we embed a js / html redirect to the phishing site of the exchange itself (in this case, there are several exchanges, and each will need to make a form), Myetherwallet, blockchain.info, etc.
Some craftsmen have come to the point that immediately after entering the username and password at poloniex.com/bittrex.com/blockchain.info they request its victim 2FA code every 15 seconds (for logging in to the account, for withdrawal of funds) - to respond to entering 2FA you need to very quickly, because it expires after a short period of time. Thus, using unicode characters , replacing some letters, for example i with L (BlTTREX.com, POIONIEX.COm), registering an exchanger on another domain (for example poloniex.com.ua), creating applications for android and advertising in search engines , attackers for the year were able to steal more than $ 80 million from users.
3) We send to email addresses of letters that we agreed in advance with a person who is knowledgeable in social engineering. Users must believe in the letter and follow the link, as it leads not to a third-party site, but to the exchange.
4) ??
5) We receive data for an input, we deduce means.
PoC of this XSS in video
3. iDOR in adding a comment, we can add a message on behalf of the user who created the ticket.
Short request
POST /v2/support/cs/work-order/reply HTTP/1.1
Host: http://www.okcoin.com
workId=718&content=test_message4. Stored XSS in the html file that was attached to the ticket, but on the domain bafangpublic.oss-cn-hangzhou.aliyuncs.com. The domain is no longer available and whois says it is owned by Hangzhou Alibaba Advertising Co., Ltd.
5. Disclosure information. I noticed that the developers of the exchanges want to hide the user's phone number as much as possible when hacking the account. On the security page, the phone is displayed as 636819 ****, it is 6 * 6 in cookies. But in the answer, the support service api / v2 / support / cs / work-order / 2550 / replies fully displays it, so it is not suitable.
As I understand it, all the exchanges have one owner and there is no point in writing everything separately, so I sent the report to the chat and to the email of the okex exchange. Very quickly received a message from the official account of okex on Twitter, and the vulnerabilities were quickly eliminated.
Then I started testing example3.com . The exchange has forbidden to disclose information about vulnerabilities, I quote:
Regarding posting on your blog, we would appreciate it at the moment. Our site is still not 100% secured.
I found XSS in my wallet, namely, in the affiliate program department, I managed to pick it up from self into an exploit stored with the csrf, it was possible to steal cookies because there was no httponly flag. I could now attach a video that has already been recorded, but, alas, the name of the exchange is revealed there.
For it, the support service offered me $ 100, but almost at the same moment logs from their domain for employees came to the sniffer.
There was only a cookie in the logs.
AWSELB=2B3B1851EC08CCFEEC18E2DB93AE1EF2A69A2A2F9D65DCC84AB785C7C7773319F1F769CCF35CA8F430D5785D5AE4AB2C48C46EE6BE8F33C293D40F3CCA9F92E38E62AA65 ) I carefully checked the report and found in the source code administrator login and password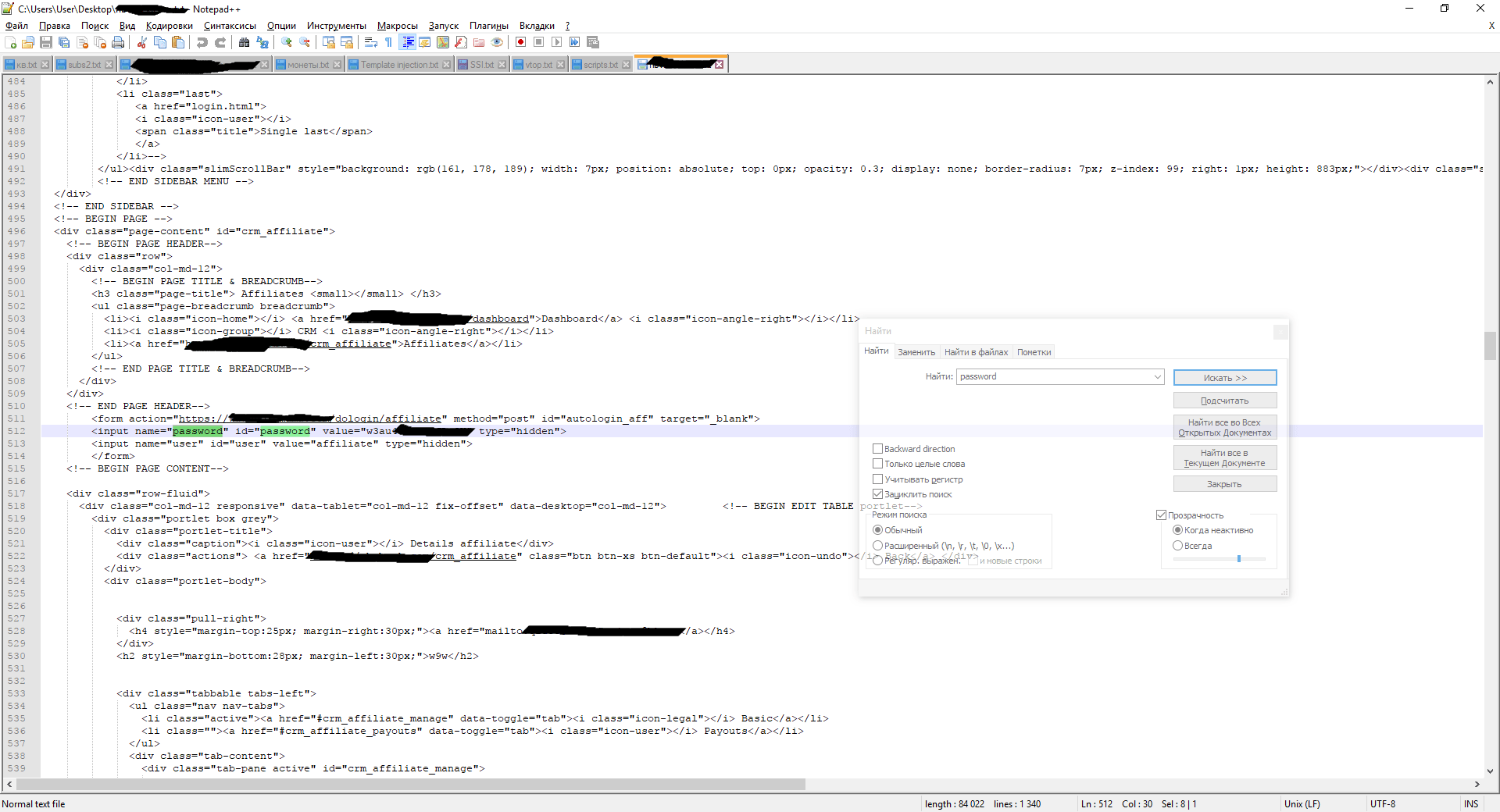

But when I went to the login page, I saw it.

In the admin panel through the login; we cannot get the password, it is necessary to crack the google account and get access to the authenticator, or redirect to the phishing site directly from the admin panel, steal its code and enter it quickly. The second option is fully implementable.
While writing a report on blind xss in the admin panel, I found another:
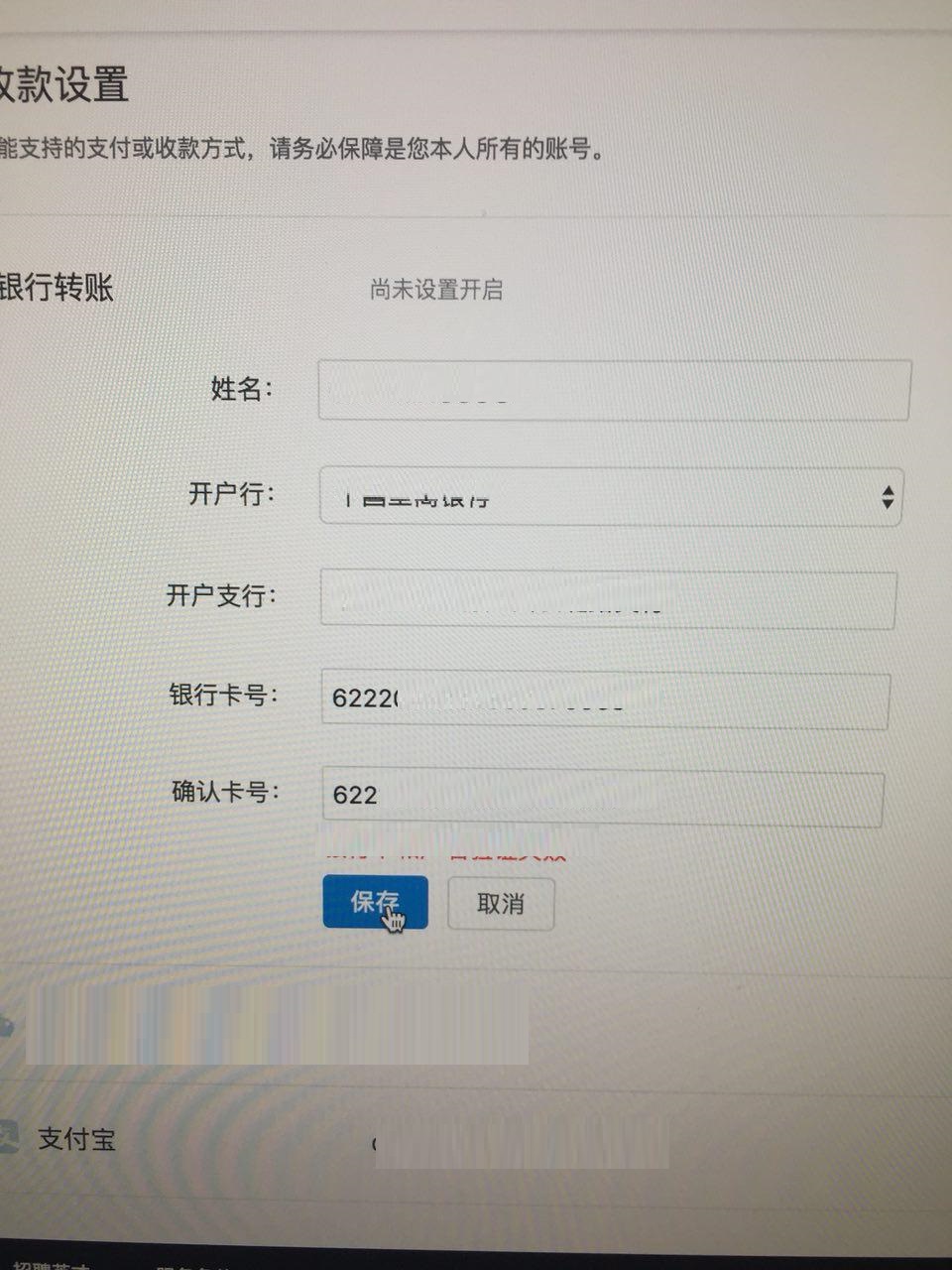
1) CSRF vulnerability in changing details for withdrawal of partner funds, a brief query:
POST /affiliate_program HTTP/1.1 Host: www.example3.com wallet=my_wallet&act=wallet security token no, an exploit was written.
2) iDOR in order removal, sensitive request example3.com/account?act=cancel&order=ID_of_order . The essence of the vulnerability is that if the user has already created an order and wants to transfer their bitcoins to the exchange wallet, we can cancel this action. At best, his order will simply be removed from the system, at worst, he will transfer bitcoins and lose his money. This vulnerability is mainly useful only for competing exchanges, and not for hackers.
After I sent a new report in support, the chief security officer contacted me to discuss vulnerabilities. They wanted to call me on Skype or by phone, but at the moment my knowledge of English is average, so we decided to limit myself to chat. For the vulnerability I was offered 0.1 btc ($ 1130):
After consulting with our situation and we can pay you $ 1000. This is the highest amount we paid for. It is a hand for the situation.
My thanks for the bounty. They are responsible for security, it was nice to communicate with their CTO.
I got a total of searching for vulnerabilities on these cryptocurrency sites:
Trust management example1.com: 1 btc .
Trust management example2.com: 0,122 btc.
Exchange livecoin.net: $ 200 fiatnym funds.
Exchange okex.com: 2 btc , I am grateful to okex for bounty, CTO Exchange allowed to publicly reveal the vulnerability.
Exchange example3.com: 0,1 btc .
1 + 0.122 + 2 + 0.1 + $ 200 = $ 58,200 and with the growth rate of bitcoin, this amount will grow.
Conclusion from the article: Always hire highly qualified programmers for your projects, especially if your budget allows you to do this. In the first two cases, the companies are quite large, they can afford to hire high-quality specialists, but they save, and because of this, users and reputation may suffer - they leave the admin panel completely "naked" and ignore the problems pointed to by the security specialist.
PS: There is also interesting information on how I discovered a vulnerability on gearbest.com, which allows to find out the login and password from any account, as well as about the vulnerability on webmoney.ru (I can tell about it only with the permission of the administration), with using which one could send a message with js / html to 35,000,000 users, but this is a completely different story. To keep abreast of my latest articles, I recommend to subscribe to telegram / twitter / vk, links below.
Source: https://habr.com/ru/post/343152/
All Articles