Children - ice cream, information system - backup

All people are divided into two categories: those who still do not make backups, and those who already make backups.
I think it is unnecessary to talk about the importance of data backup and the risks associated with the lack thereof. I think everyone will agree on this point - backup copies are needed!
')
In the opinion on this issue, we were joined by the government with its punishing hand, and the regulatory authorities in the field of information protection. We all remember the requirements of the legislation, voiced in the 17th, 21st and 31st Orders of the FSTEC. Also, the regulators of the credit and financial sphere have formed requirements for reserving and backing up.
And from January 1, 2018, they will be added (come into effect) and Federal Law No. 187-FZ of July 26, 2017 “On the Security of the Critical Information Infrastructure of the Russian Federation”, which also tells us that one of the four “Main Security System Tasks A significant object of a critical information infrastructure is: "" restoring the functioning of a significant object of a critical information infrastructure, including through the creation and storage of backup copies of the information necessary for this. "
Thus, these requirements cover virtually legal entities in all areas. What do regulators like most about us?
The correct answer from our practice is the use in our activities of means that have passed the conformity assessment in the prescribed manner (read certified). What could be better in such a situation than using a combination of world best practices in the field of backup and certified product? We found this combination in Veeam Backup & Replication. To understand - a little about this product.
Veeam Backup & Replication provides efficient backup, replication, and recovery of virtualized applications and data. The solution performs fast and reliable backup of VMware and Hyper-V virtual machines without the use of agents inside virtual machines. Veeam Backup & Replication helps to significantly speed up the backup process and reduce storage costs.
The certified version of Veeam Backup & Replication is designed to protect information:
- in state information systems up to class 1 of security inclusive;
- in automated control systems of production and technological processes up to class 1 of security inclusive;
- in personal data information systems (for which threats of type 1, type 2 or type 3 are relevant) up to class 1 of protection, inclusive, when following instructions for use.
Information from the manufacturer on the requirements of their product (the full version of the link: www.veeam.com/ru/fstec-certified-products-requirements.html )
Consider the requirements for information systems that require the use of funds that have passed in the prescribed manner conformity assessment.
State information systems (GIS)
Requirements for the protection of information contained in the GIS are determined by the Order of the FSTEC of Russia of 11.02.2013. №17 "On approval of requirements for the protection of information not constituting a state secret contained in state information systems."
“To ensure the protection of information contained in the information system, information protection means are applied that have undergone conformity assessment in the form of mandatory certification for compliance with information security requirements in accordance with Article 5 of Federal Law No. 184- dated December 27, 2002“ On Technical Regulation ”” - Article 11 of the document.
Personal Data Information Systems (ISPDN)
The requirements for the protection of personal data contained in the ISPDN are determined by the Order of the FSTEC of Russia dated February 18, 2013 No. 21 “On approving the composition and content of organizational and technical measures to ensure the security of personal data when they are processed in personal data information systems”.
For state personal data operators, conformity assessment is always carried out in the form of mandatory certification followed by certification.
“To ensure the security of personal data when processing them in state information systems, in addition to the Requirements approved by order of FSTEC of Russia of February 11, 2013 N 17, it is necessary to be guided by the requirements (including determining the level of personal data protection) established by the Government Of the Russian Federation dated November 1, 2012 N 1119. At the same time, in accordance with clause 27 of the Requirements, approved by order of the FSTEC of Russia dated February 11, 2013, N the general correlation of the security class of the state information system with the level of personal data security. If the personal data security level determined in the established procedure is higher than the established security class of the state information system, the security class is upgraded to a value that meets paragraph 27 of the Requirements approved by order of the FSTEC of Russia of February 11, 2013 N 17. ”
(Information message of FSTEC of July 15, 2013 N 240/22/2637).
For commercial operators of personal data, conformity assessment can be performed both in the form of certification and in another form chosen by the operator, but it should be noted that in some cases, choosing a certified product can reduce the cost of evaluating the information system, since the certificate for the product automatically certifies that conformity assessment has already been carried out by the manufacturer.
Requirements for the use of information security tools that have undergone conformity assessment depending on the level of ISPD security:

Process control system at critical facilities
Requirements for the protection of information contained in the IC of the automated process control system are determined by the Order of the FSTEC of Russia dated March 14, 2014 No. 31 “On approving the requirements for ensuring the protection of information in automated systems for managing production and technological processes at critical facilities, potentially dangerous facilities, as well as representing an increased danger to life and health of people and to the environment ”.
“In an automated control system, information protection means are applied that have passed the conformity assessment in accordance with the legislation of the Russian Federation on technical regulation” (Article 11). The use of certified protection means reduces the cost of implementation of this item, since the certificate certifies that the product has already passed the compliance check. The use of products that do not have a certificate is also possible, but it requires additional costs from the buyer to carry out certification or other measures for conformity assessment provided for by the legislation on technical regulation.
Assessment of possible damage: see the Order of the Government of the Russian Federation of May 21, 2007 N 304 “On the classification of natural and man-made emergencies”
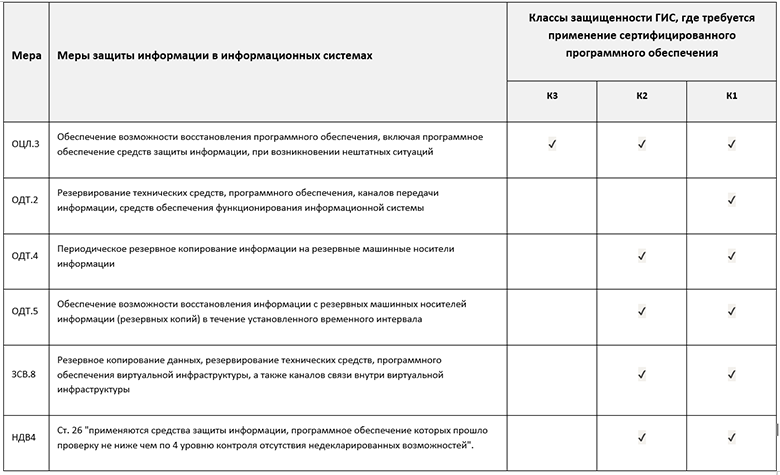
The security class of the automated process control system and the need to use backup tools that have passed the conformity assessment is determined in accordance with the table:

The composition of information security measures of automated control systems and their basic sets for the appropriate class of security (in terms of providing backup information), where the use of means that have undergone conformity assessment is required:

What can the cloud do?
Consider the example of our BACKUP AS A SERVICE. The Cloud4Y backup solution provides a cloud backup feature that ensures reliable storage of any amount of data.
There are at least three options for organizing such a service, and a free VPN with Internet encryption is available for all the listed options:
1. Backup as a Service based on Veeam Backup allows you to get the necessary disk space for storing and restoring backups from storage. In addition, we can provide guaranteed recovery for a given time in the following modes:
1. SLA Basic 10-19 / 5
2. SLA "Priority" 9-21 / 7
3. SLA "Critical" 24/7
4. SLA «VIP» 24/7
2. When using Veeam Endpoint Protection, backup is done to our Veeam, and payment is made according to the plate for the provided disk space.
3. Using the IaaS service, a server (VM) for balls is rented (Linux or Windows depends on preferences), the tenant independently picks up and configures the VM and makes a ball there for storing backups, then independently connects the server (VM) in the cloud with the backup server. All resources can be added or modified through VMware vCloud Director in real time.
Source: https://habr.com/ru/post/343126/
All Articles