A new Alina has been detected - a malware for POS terminals.

The presence of recorded data on thousands of bank cards makes POS-terminals a critical system, and therefore it is not surprising that they are becoming an increasingly popular target by cyber-criminals. Attacking such devices anonymously from the Internet is relatively simple, and selling data on the black market is very profitable.
Recently, the PandaLabs anti-virus laboratory detected infections in a large number of bars and restaurants in the USA, whose POS-terminals were attacked by two types of malicious program designed to steal data from bank cards.
')
The following malware samples were analyzed (the MD5 file is shown in brackets):
1. Epson.exe (69E361AC1C3F7BCCE844DE43310E5259)
2. Wnhelp.exe (D4A646841663AAC2C35AAB69BEB9CFB3)
Epson.exe is an error certificate:

Both samples were compiled using Microsoft Visual C ++ 8, and they are not packaged or encrypted. As soon as the malicious program is launched in the system, it starts analyzing various system processes for searching information on bank cards.
Below we can see how they “pass” through various processes, searching for only those processes that may contain data on bank cards in memory:

In the case of the sample “Epson.exe”, this program searches for data on bank cards in the following processes:

| The name of the program | Description |
| notepad ++. exe | Text editor |
| CreditCardService.exe | Microsoft |
| DSICardnetIP_Term.exe | NETePay for Mercury |
| DSIMercuryIP_Dial.exe | NETePay for Mercury |
| EdcSvr.exe | Aloha Electronic Draft Capture (EDC) |
| fpos.exe | Future POS |
| mxSlipStream4 / mxSlipStream5 / mxSlipStream.exe / mxSwipeSVC.exe | SlipStream POS System Transaction Processor by mXpress |
| NisSrv.exe | Windows 8 |
| spcwin.exe / Spcwin.exe / SPCWIN.exe / SPCWIN.EXE | POSitouch (POS-system for the food industry and fast food) |
On the other hand, the sample “Wnhelp.exe” contains a list that is used to select processes that should not be analyzed. Those. if the name of the process coincides with the name of the object in this list, then such a process will not be analyzed when searching for data on bank cards:
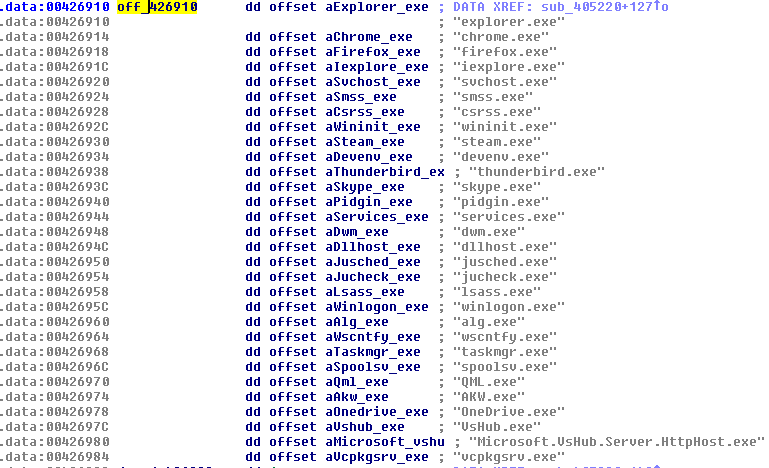
Excluded processes:
explorer.exe
chrome.exe
firefox.exe
iexplore.exe
svchost.exe
smss.exe
csrss.exe
wininit.exe
steam.exe
devenv.exe
thunderbird.exe
skype.exe
pidgin.exe
services.exe
winlogon.exe
alg.exe
wscntfy.exe
taskmgr.exe
spoolsv.exe
QML.exe
AKW.exe
OneDrive.exe
VsHub.exe
Microsoft.VsHub.Server.HttpHost.exe
vcpkgsrv.exe
dwm.exe
dllhost.exe
jusched.exe
jucheck.exe
lsass.exe
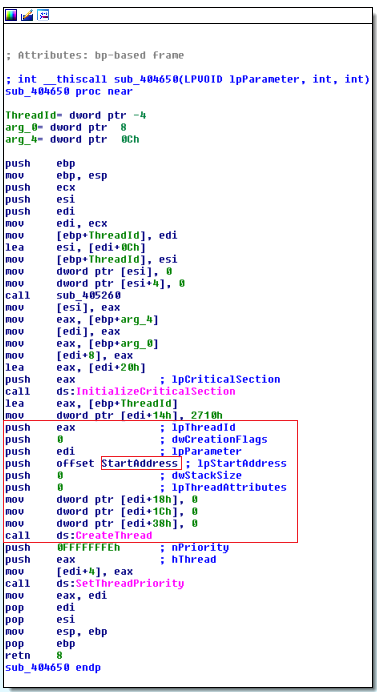
In both samples, as soon as a process is received that needs to be analyzed (because it was contained in the list, as in the case of Epson.exe, or because it was “dropped”, as in the case of Wnhelp.exe), a new thread is created :
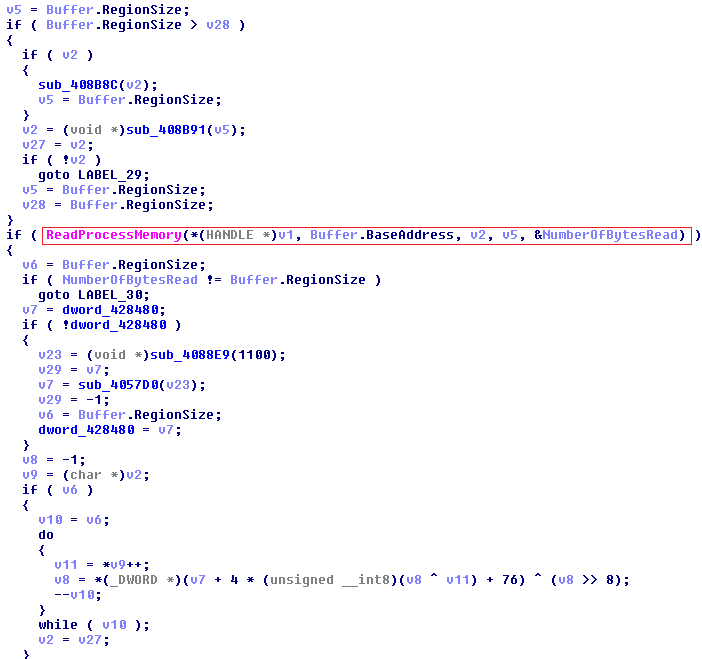
And then a memory analysis is performed using an algorithm specially designed to check whether the information found is data on bank cards:
The sample Wnhelp.exe is executed by attackers using the “install” command, and in such a way that a service is created to ensure its “survivability” in the system:

The service is called “Windows Error Reporting Service Log”.

The Epson.exe sample works in the same way, although attackers can customize the name of the service as they like, using certain parameters:
install [Service name] [Service description] [Third parameter]
Each option connects to its management server (C & C):
| Epson.exe | dropalien.com/wp-admin/gate1.php |
| Wnhelp.exe | www.rdvaer.com wp-admin / gate1.php |
Then they can receive various tasks from hackers:
| Teams | Description |
| update = [URL] | Malware Update |
| dlex = [URL] | Download and upload file |
| chk = [CRC_Checksum] | Updates file checksum |
To connect to the control panel, they use the following UserAgent:
“Mozilla / 5.0 (Windows NT 6.2; WOW64) AppleWebKit / 537.22 (KHTML, like Gecko) Chrome / 25.0.1364.152 Safari / 537.22”
Communications are done over SSL. The malicious program modifies the Internet connection configuration to ignore unknown CA (Certificate Authorities), with the help of which it is possible to use its own certificate.
First, the Internet security flags are received via the InternetQueryOptionA API with the third argument set to the INTERNET_OPTION_SECURITY_FLAGS (31) value. After that, a binary file is executed with the SECURITY_FLAG_IGNORE_UNKNOWN_CA (100h) flag.
Conclusion: How to counter POS-attack
Attacks to POS terminals remain very popular, especially in countries such as the USA, where the use of Chip & PIN is not mandatory. Many of these attacks are aimed at enterprises that do not have specialized personnel in the field of IT, especially in the field of information security, and therefore hackers use such opportunities.
POS terminals are computers that handle critical data, and therefore must be protected at the highest possible level. Cloud solutions with EDR technology help ensure there are no malicious processes on such terminals. Therefore, there is no need to hire experts with special knowledge, because such solutions are serviced by our own development experts, who are responsible for ensuring that all executable processes are safe.
Source: https://habr.com/ru/post/342420/
All Articles