Playing with Nextgen-antivirus from Palo Alto Networks: it injects its dll into executable processes like * .exe

Naturally, we undertook to test it, because such a beast had not yet been seen.
Once upon a time, there was the Palo Alto company, which made quite good enterprise-level firewalls. Further, in accordance with the technological trend, the sandbox, both cloudy and private, was included in the vendor’s line of solutions. Up to a certain point, both streaming firewalls and sandboxes at the entrance closed the task of providing information security. But over time, and this was not enough - the concept of "continuous protection" appeared, which, in order to be completely happy, also required the protection of end machines, the so-called end-point solutions. “Palo Alto” bought the company Cyvera and finished its product for themselves. This is how Traps, the “antivirus of the new generation”, appeared.
')
Traps injects its code into executable processes (for example, * .exe), which allows you to run everything in the mode of a kind of small hypervisor, and looks at the memory usage. He does not check signatures, only catches strange behavior of the software under control.
There is nothing funnier than an antivirus that behaves like a virus and works even under WinXP. This thing is Traps.
Here is how it looks from the process explorer:

In total, there are 300 types of processes out of the box, where the solution can inject its modules, plus you can make customization for other types of processes using a fairly simple designer.
This is how the agent interface on the Win-machine looks like:

So, Traps "is registered" in the exe-file and begins to follow what the "sibiotic" process is doing. At the OS level, Traps can log suspicious events from a memory management point of view. For the most part, privilege acquisition is due to buffer overflow and other anomalies. Such events "Palo Alto" and calculates.

The advantage is that this antivirus has no signatures in essence. There is a set of countermeasures and known events of failures, plus a set of heuristics. That is, updates may be useful, but in general they are optional (until viruses appear that specifically bypass Traps). This can be very useful in isolated networks and on certified sites.
Even by virtue of an elegant, like a blow with a crowbar, solution with “infecting” executable files, Traps runs on WinXP. And this is no longer a joke in the corporate segment: many ATMs and cash desks still work under embed versions of WinXP, and patches for them are not issued. Every time about the height of the next epidemic, everyone can learn, for example, from terminal screens at train stations.
It is installed on servers, VDI machines and physical workstations. It is undemanding enough resources:

The product can coexist with other anti-virus solutions, but not with all. Information is open, the list can be taken in release notes.
If you have another Palo Alto infrastructure, then you should know that Traps is built with a bang. Echeloned protection looks like this: their screen, their sandbox, their own protection on the endpoint. If an unknown executable file (with an unknown reputation) comes to the traps machine, you can disable its execution until the solution of the “big” corporate sandbox. Previously, only the firewall was integrated with the sandbox - it was possible to catch horses only after the fact - after running the file on the endpoint. And Traps allows you to block the execution before the proceedings. And when synchronizing with their cloud service, all the hashes that come to Traps go there - and if it’s known that they are not the same, then they are immediately decided to refuse execution.
It works in the opposite direction. As soon as an epidemic began in the world and the global sandbox detected a specific instance as malicious, this signature is instantly accessible to all Palo Alto subscribers. And from the experience of previous epidemics such as WannaCry, we see that the peak of infection falls on the first day, while no one has come to their senses. It is very important to have protection during this period, and Palo Alto provides it.
When there are attacks, there are so-called killchains - sequences of actions that lead to the compromise of the machine.
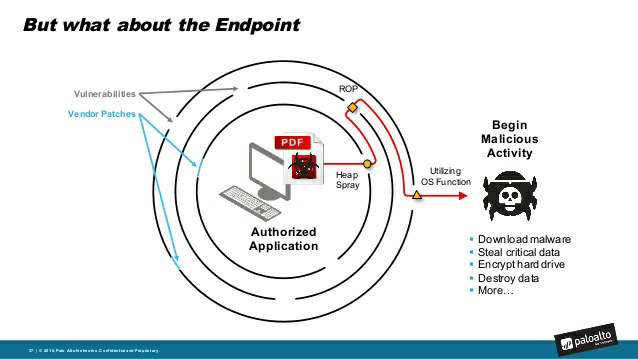
If at least one element is blocked in this chain, then the attack will not take place.

Known vulnerabilities and technologies that Traps uses to counter attacks.

Naturally, this software cannot scan folders as usual antivirus software - there is no static analyzer, only hardcore. The classic antivirus approach to detecting known threats no longer works. "Antivirus is dead," said Symantec vice president in 2014.
Traps is also good at collecting forsica. When triggered, a memory dump is generated, which you can analyze as much as you like (the dump can be copied to your analysis server).
The result - we will put this solution where the protection of workstations is needed. Traps does not replace or displace antiviruses (at least for now), but complements them. Now the vendor is already saying that antiviruses, besides Traps, are no longer needed - there are examples when customers passed PCI DSS and HIPAA compliance, with Traps in their infrastructure.
If we talk about vulnerability in SMBv1 (WannaCry, Petya), then it existed for a very long time, and anyone who had information about her could have exploited it imperceptibly. But Traps users were protected.
And here is an example of the fact that the release of patches does not guarantee that a new threat will not be found in the near future.

On July 5, 2015, a vulnerability was discovered, the patch was released only on the 8th. Accordingly, the users were not protected for 3 days, on the 10th - a new vulnerability, the patch - on the 14th. Had Traps, the problems would be much less.
Naturally, I wanted to test it. I took the distributions of viruses and trojans ( repository , carefully , all the samples are working, do not kill yourself the machine). The VMWare Fusion Professional Version 10.0.1 (6754183) hypervisor created a new virtual machine using the original MSDN image of Windows XP SP3 VL, the English version (md5 5bf476e2fc445b8d06b3c2a6091fe3aa). A virtual machine is allocated 1 core and 512 MB of memory. The .NET Framework v3.5.1 is installed (necessary for installing Traps), Traps itself is installed on top, network interaction with the ESM management server is organized, which is organized on Windows Server 2016 from the database to SQL-Express (vendor's recommendation for PoC-deployment). Neither the client nor the server had access to the Internet to communicate with the WildFire cloud sandbox. That is, we simulate a full offline - a fairly frequent story for a banking machine. Version ESM 4.1.1.28779, version of Traps Agent 3.4.4.24430.
After installing the agent on WinXP, a snapshot was taken, to which I rolled back after testing each sample. The transfer of the sample took place simply by dragging the executable file to the target machine (drag'n'drop), after which, depending on the file type, it was launched. Either by double clicking or through the console.
List of tested samples:
1. Win32.Alina.3.4.B
2. Trojan.Asprox
3. Win32.Avatar
4. Trojan.Bladabindi
5. Win32.Boaxxe.BB
6. Win32.Carberp
7. Win32.Cridex
8. Ransomware.CryptoLocker
9. Ransomware.Cryptowall
10. Win32.Cutwail
11. Trojan.Dropper.Gen
12. Win32.Emotet
13. Win32.Fareit
14. Win32.Hupigon
15. Win32.Infostealer.Dexter
16. Ransomware.Jigsaw
17. Trojan.Kovter
18. Trojan.Loadmoney
19. Ransomware.Locky
20. Ransomware.Matsnu
21. Trojan.NSIS.Win32
22. Ransomware.Petrwrap
23. Ransomware.Petya
24. Ransomware.Radamant
25. Ransomware.Satana
26. Trojan.Stabuniq
27. Trojan.Sinowal
28. Ransomware.TeslaCrypt
29. Ransomware.Vipasana
30. Ransomware.WannaCry
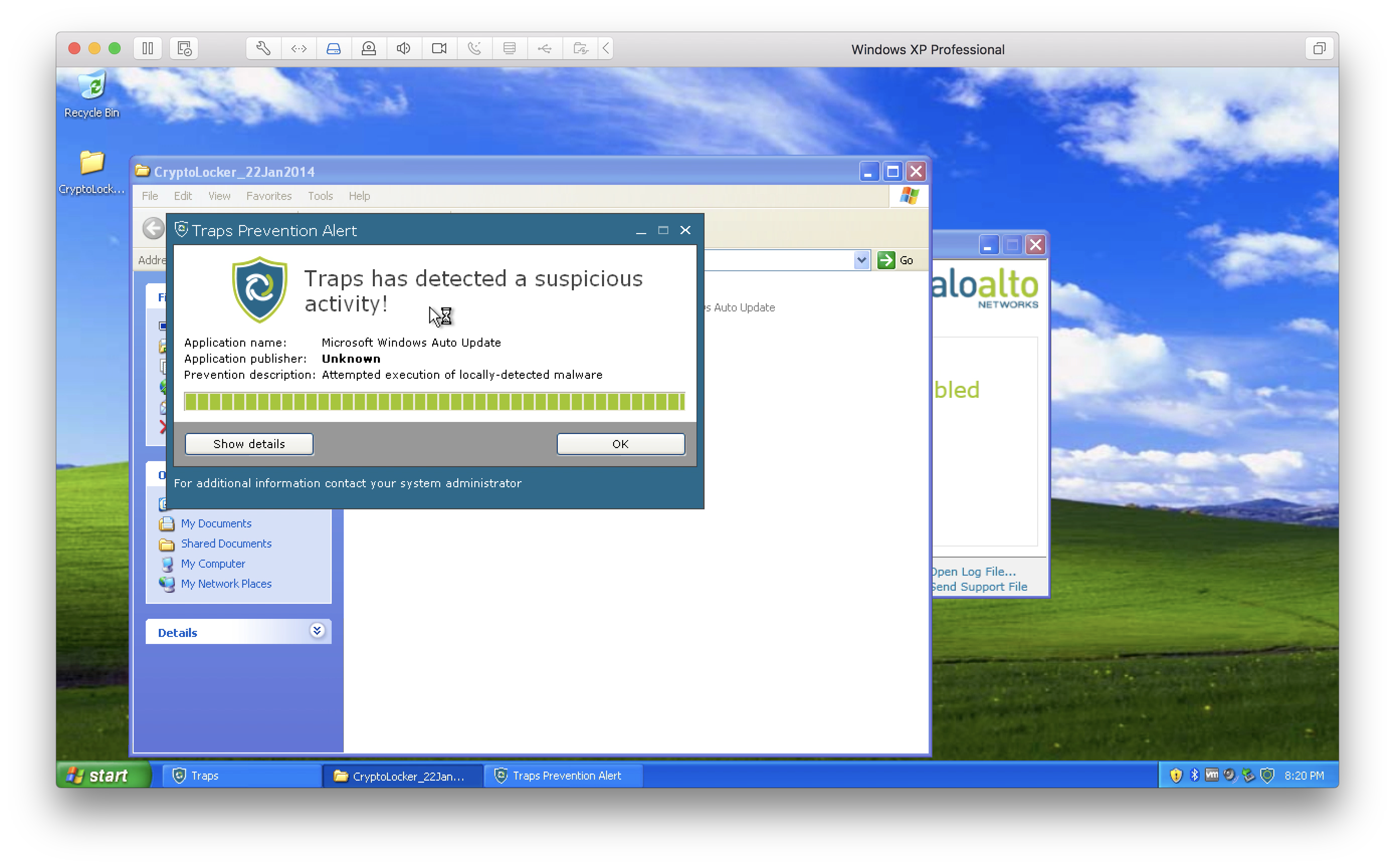
Only TeslaCrypt's malware passed through Traps. At the same time, we deliberately ignored the vendor's best practitioner to test the capabilities of Traps local analysis. In particular, we have disabled all interaction with the sandbox, which is highly undesirable. In normal mode, even if the server’s connection to the sandbox disappears, when the connection is restored, it will send unknown files for analysis, and we still know that the machine was infected, for that there is a point in the management server - malware post-detection ( see screenshot). And even hashes of known files, just in case, with a certain periodicity are still checked by the sandbox in case the sandbox's verdict has changed. And by clicking on the WildFire report button, we will receive a detailed info on why this file was considered malicious. The specific teslacrypt report here .

All unprotected malware was detected locally by the agent itself without communication with the external server and signatures (there was communication with the local server, but the tested machine itself and the management server did not have Internet access).
It looked like this:
As a result, I think the fight against known viruses by signatures is already the last century, given that the malware hash is easy to change. The Traps approach offers ways to deal with unknown threats, with a focus on preventing the threat. It works well enough to replace antiviruses in the future. Already now ideal for isolated environments (process control systems, etc.).
Links
- PDF manual from Palo Alto
- Virustotal added the engine to the scan, it is called Palo Alto Networks, but this is not Traps, but a firewall. If you want the results of tests on Traps, then they are on the link .
- Here is another interesting link from the vendor about the replacement of "old" antiviruses
- My mail: DDrozhzhin@croc.ru
Source: https://habr.com/ru/post/342314/
All Articles