A bit about VPN: protocols for remote access
The first November in Russia began to operate a ban on bypassing locks using a VPN. And many companies, including foreign ones, wondered how to be organizations using technology to create corporate networks.
According to representatives of the State Duma, the law contains a clause according to which network encryption can be used for corporate purposes. This means that companies do not have to spend significant amounts and build private networks between their offices, since setting up a VPN connection is practically (and in some cases it is) free. Therefore, today we decided to consider two ways of organizing a VPN connection in a corporate network and several protocols used for this: PPTP, L2TP / IPsec, SSTP and OpenVPN.

/ Flickr / Johannes Weber / CC
')
The PPTP specification was developed by a consortium based by Microsoft for dial-up VPN. Therefore, PPTP has long remained the standard for corporate networks. For the same reason, it uses the Microsoft Point-to-Point Encryption ( MPPE ) encryption protocol.
It goes "by default" on any VPN-compatible platform and is easily configured without additional software. Another advantage of PPTP is high speed. But unfortunately, PPTP is not secure enough. Since the protocol was included in Windows 95 OSR2 in the late nineties, several vulnerabilities have been revealed.
The most serious is the possibility of unencapsulated MS-CHAP v2 authentication. This exploit allowed you to hack PPTP in two days. Microsoft “patched” the hole by switching to the PEAP authentication protocol, but then they themselves suggested using L2TP / IPsec or SSTP VPN protocols. One more thing - PPTP connections are easy to block because the protocol works with one port number 1723 and uses the GRE protocol .
When the VPN tunnel is established, PPTP supports two types of transmitted messages: these are control messages to maintain and disconnect the VPN connection, and the data packets themselves.
Layer 2 Tunneling Protocol, or L2TP , is also represented in almost all modern operating systems and works with all devices capable of “accepting” a VPN.
L2TP cannot encrypt traffic passing through it, so it is often used in conjunction with IPsec . However, this leads to a negative effect - in L2TP / IPsec double data encapsulation occurs, which negatively affects the performance. L2TP also uses the 500th UDP port, which is easily blocked by the firewall if you are behind NAT.
L2TP / IPsec can work with 3DES or AES ciphers. The first is vulnerable to meet-in-the-middle and sweet32 attacks , so today it is rarely encountered in practice. When working with the AES-cipher, major vulnerabilities are unknown, so in theory this protocol should be safe (if properly implemented). However, John Gilmore, founder of the Electronic Frontier Foundation, pointed out in his post that IPSec could be weakened in a special way.
The most serious problem with L2TP / IPsec is that many VPN services do not implement it well enough. They use pre-shared keys (PSK), which can be downloaded from the site. PSK is needed to establish a connection, because even if the data is compromised, it remains protected by AES. But an attacker can use PSK to impersonate a VPN server and then eavesdrop on encrypted traffic (even injecting malicious code).
Secure Socket Tunneling Protocol, or SSTP , is a VPN protocol developed by Microsoft. It is based on SSL and first launched in Windows Vista SP1. Today, the protocol is available for operating systems such as RouterOS, Linux, SEIL and Mac OS X, but it still finds its main application on the Windows platform. SSTP is a proprietary standard owned by Microsoft, and its code is not available for public viewing.
SSTP itself has no cryptographic functionality with the exception of one function - this is cryptographic binding (MITM). SSL encryption is the same. A description of the procedure for establishing a VPN connection can be found on the Microsoft website.
Tight integration with Windows simplifies working with the protocol and increases its stability on this platform. However, SSTP uses SSL 3.0 , which is vulnerable to a POODLE attack, which in theory affects the security of the VPN protocol.
OpenVPN is an open source project that uses the Open SSL library, TLS and a number of other technologies. Today, it is the industry standard in commercial VPN services and is implemented on any platform using third-party software. Many providers even provide OpenVPN custom clients, but project developers are still working on the code core.
Among the advantages of OpenVPN is its customizability. It can be configured to work on any port. This allows traffic to be sent through port 443 in order to “mask” it under HTTPS, which complicates blocking.
However, the flexibility of this VPN protocol to some extent can be considered a disadvantage. In particular, this leads to the need to download and install additional configuration files when using the standard Windows client. But this problem can be solved by using pre-configured VPN clients that some providers implement.
Another advantage of the protocol is the OpenSSL library. It supports many cryptographic algorithms - these are 3DES, CAST-128, Camelia, AES and Blowfish. The last two are most often used in practice.
Also a plus of OpenVPN can be considered regular audits. The last inspection did not reveal any “holes” affecting the security of user data. Then several vulnerabilities were found that give attackers the ability to conduct DDoS attacks, but the developers patched them in the version of OpenVPN 2.4.2.
OpenVPN is considered one of the most reliable VPN protocols available today and is widely supported by the VPN industry. And although earlier OpenVPN did not work on mobile platforms without root access, today there are third-party applications that have corrected this “misunderstanding”.

/ Flickr / Andrew Hart / CC
In today's article we will talk about the two most commonly used types of VPN connections. It will be about remote access to the corporate network (remote access) and a point-to-point connection (site-to-site)
Remote access allows company employees to securely connect to the corporate network via the Internet. This is especially important in the case when an employee does not work in the office and connects through unprotected access points, such as Wi-Fi in a cafe. To establish this connection, a tunnel is established between the client on the user's gadget and the VPN gateway on the company's network. The gateway authenticates and then provides (or limits) access to network resources.
To protect the connection, IPsec or SSL is most commonly used. It is also possible to use the protocols PPTP and L2TP.

/ Wikimedia / Philippe Belet / PD
Site-to-site VPN serves to combine different local networks. In this case, user devices work without VPN clients — the gateway does all the work.
This type of connection is used when a company has several remote offices that need to be combined into one private network. And also in the event that the organization has a partner to whose network connection is required. This allows companies to work together in a protected common space.
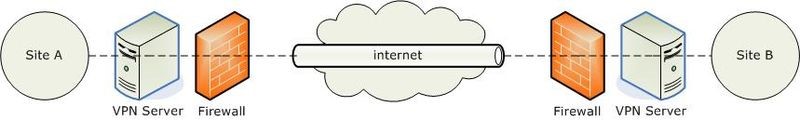
/ Wikimedia / Philippe Belet / PD
IPsec is most often used to protect point-to-point connections. Also the variant of the carrier MPLS-cloud without public networks is used. In this case, it is possible to organize connections Layer3 (MPLS IP VPN) or Layer2 (VPLS).
Finally, I would like to note that there are several other options for using VPN connections:
In more detail about them and the VPLS technology we plan to tell in one of the subsequent materials.
PS What else do we write in our corporate blog:
According to representatives of the State Duma, the law contains a clause according to which network encryption can be used for corporate purposes. This means that companies do not have to spend significant amounts and build private networks between their offices, since setting up a VPN connection is practically (and in some cases it is) free. Therefore, today we decided to consider two ways of organizing a VPN connection in a corporate network and several protocols used for this: PPTP, L2TP / IPsec, SSTP and OpenVPN.

/ Flickr / Johannes Weber / CC
')
PPTP
The PPTP specification was developed by a consortium based by Microsoft for dial-up VPN. Therefore, PPTP has long remained the standard for corporate networks. For the same reason, it uses the Microsoft Point-to-Point Encryption ( MPPE ) encryption protocol.
It goes "by default" on any VPN-compatible platform and is easily configured without additional software. Another advantage of PPTP is high speed. But unfortunately, PPTP is not secure enough. Since the protocol was included in Windows 95 OSR2 in the late nineties, several vulnerabilities have been revealed.
The most serious is the possibility of unencapsulated MS-CHAP v2 authentication. This exploit allowed you to hack PPTP in two days. Microsoft “patched” the hole by switching to the PEAP authentication protocol, but then they themselves suggested using L2TP / IPsec or SSTP VPN protocols. One more thing - PPTP connections are easy to block because the protocol works with one port number 1723 and uses the GRE protocol .
When the VPN tunnel is established, PPTP supports two types of transmitted messages: these are control messages to maintain and disconnect the VPN connection, and the data packets themselves.
L2TP and IPsec
Layer 2 Tunneling Protocol, or L2TP , is also represented in almost all modern operating systems and works with all devices capable of “accepting” a VPN.
L2TP cannot encrypt traffic passing through it, so it is often used in conjunction with IPsec . However, this leads to a negative effect - in L2TP / IPsec double data encapsulation occurs, which negatively affects the performance. L2TP also uses the 500th UDP port, which is easily blocked by the firewall if you are behind NAT.
L2TP / IPsec can work with 3DES or AES ciphers. The first is vulnerable to meet-in-the-middle and sweet32 attacks , so today it is rarely encountered in practice. When working with the AES-cipher, major vulnerabilities are unknown, so in theory this protocol should be safe (if properly implemented). However, John Gilmore, founder of the Electronic Frontier Foundation, pointed out in his post that IPSec could be weakened in a special way.
The most serious problem with L2TP / IPsec is that many VPN services do not implement it well enough. They use pre-shared keys (PSK), which can be downloaded from the site. PSK is needed to establish a connection, because even if the data is compromised, it remains protected by AES. But an attacker can use PSK to impersonate a VPN server and then eavesdrop on encrypted traffic (even injecting malicious code).
Sstp
Secure Socket Tunneling Protocol, or SSTP , is a VPN protocol developed by Microsoft. It is based on SSL and first launched in Windows Vista SP1. Today, the protocol is available for operating systems such as RouterOS, Linux, SEIL and Mac OS X, but it still finds its main application on the Windows platform. SSTP is a proprietary standard owned by Microsoft, and its code is not available for public viewing.
SSTP itself has no cryptographic functionality with the exception of one function - this is cryptographic binding (MITM). SSL encryption is the same. A description of the procedure for establishing a VPN connection can be found on the Microsoft website.
Tight integration with Windows simplifies working with the protocol and increases its stability on this platform. However, SSTP uses SSL 3.0 , which is vulnerable to a POODLE attack, which in theory affects the security of the VPN protocol.
Openvpn
OpenVPN is an open source project that uses the Open SSL library, TLS and a number of other technologies. Today, it is the industry standard in commercial VPN services and is implemented on any platform using third-party software. Many providers even provide OpenVPN custom clients, but project developers are still working on the code core.
Among the advantages of OpenVPN is its customizability. It can be configured to work on any port. This allows traffic to be sent through port 443 in order to “mask” it under HTTPS, which complicates blocking.
However, the flexibility of this VPN protocol to some extent can be considered a disadvantage. In particular, this leads to the need to download and install additional configuration files when using the standard Windows client. But this problem can be solved by using pre-configured VPN clients that some providers implement.
Another advantage of the protocol is the OpenSSL library. It supports many cryptographic algorithms - these are 3DES, CAST-128, Camelia, AES and Blowfish. The last two are most often used in practice.
Also a plus of OpenVPN can be considered regular audits. The last inspection did not reveal any “holes” affecting the security of user data. Then several vulnerabilities were found that give attackers the ability to conduct DDoS attacks, but the developers patched them in the version of OpenVPN 2.4.2.
OpenVPN is considered one of the most reliable VPN protocols available today and is widely supported by the VPN industry. And although earlier OpenVPN did not work on mobile platforms without root access, today there are third-party applications that have corrected this “misunderstanding”.

/ Flickr / Andrew Hart / CC
VPN Connection Types
In today's article we will talk about the two most commonly used types of VPN connections. It will be about remote access to the corporate network (remote access) and a point-to-point connection (site-to-site)
Remote access allows company employees to securely connect to the corporate network via the Internet. This is especially important in the case when an employee does not work in the office and connects through unprotected access points, such as Wi-Fi in a cafe. To establish this connection, a tunnel is established between the client on the user's gadget and the VPN gateway on the company's network. The gateway authenticates and then provides (or limits) access to network resources.
To protect the connection, IPsec or SSL is most commonly used. It is also possible to use the protocols PPTP and L2TP.

/ Wikimedia / Philippe Belet / PD
Site-to-site VPN serves to combine different local networks. In this case, user devices work without VPN clients — the gateway does all the work.
This type of connection is used when a company has several remote offices that need to be combined into one private network. And also in the event that the organization has a partner to whose network connection is required. This allows companies to work together in a protected common space.

/ Wikimedia / Philippe Belet / PD
IPsec is most often used to protect point-to-point connections. Also the variant of the carrier MPLS-cloud without public networks is used. In this case, it is possible to organize connections Layer3 (MPLS IP VPN) or Layer2 (VPLS).
Finally, I would like to note that there are several other options for using VPN connections:
- Establishing a connection between two servers in data centers. It is useful if for some reason it is not possible to establish a secure channel using a standard corporate network.
- Connection to the IaaS service.
- Placing the VPN gateway in the cloud.
In more detail about them and the VPLS technology we plan to tell in one of the subsequent materials.
PS What else do we write in our corporate blog:
Source: https://habr.com/ru/post/341916/
All Articles