In the footsteps of CyberCrimeCon 2017: Trends and development of high-tech crime
On October 10, the annual Group-IB CyberCrimeCon 2017 conference was held in Moscow. This year, industry experts - cybersecurity experts from the banking sector, Interpol, and European police - discussed new hacker targets, talked about the evolution of attacks, and studied practical cases.
At the conference, we also presented our report on cyber threat trends for the financial sector. Today’s post is a summary of what we’ve been talking about : trends in high-tech crime.
 CyberCrimeCon 2017 / Group-IB
CyberCrimeCon 2017 / Group-IB
')
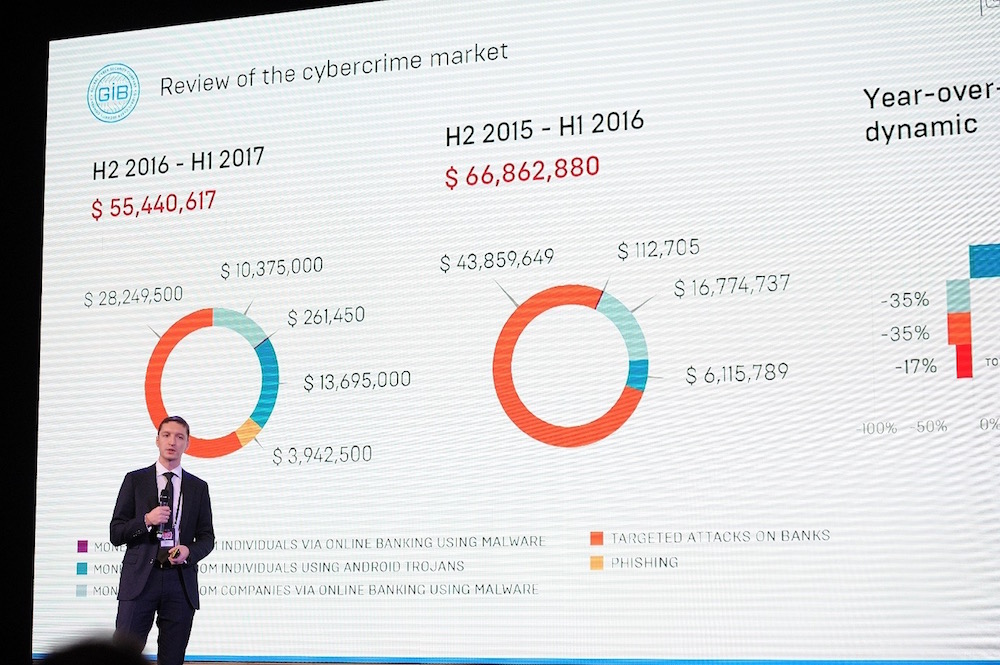
The cybercrime market is developing - with each year the number of attacks grows and the amounts stolen increase. According to our data, in Russia, the number of embezzlements in Internet banking from individuals increased by 144% compared to last year. The number of thefts using android trojans increased by 136% over the same period. In total, in the second half of 2016 and the first half of 2017, attackers stole 4.7 billion rubles.
Regarding the situation in the world, in 2015 the damage done by cybercriminals amounted to 3 trillion dollars. According to some estimates , this figure will increase to 6 trillion by 2021.
CyberCrimeCon 2017 / Group-IB
As soon as hackers discover a new “vector” of attacks (safer or more profitable), they immediately begin to create tools, write scripts, think over schemes to effectively exploit the detected vulnerabilities.
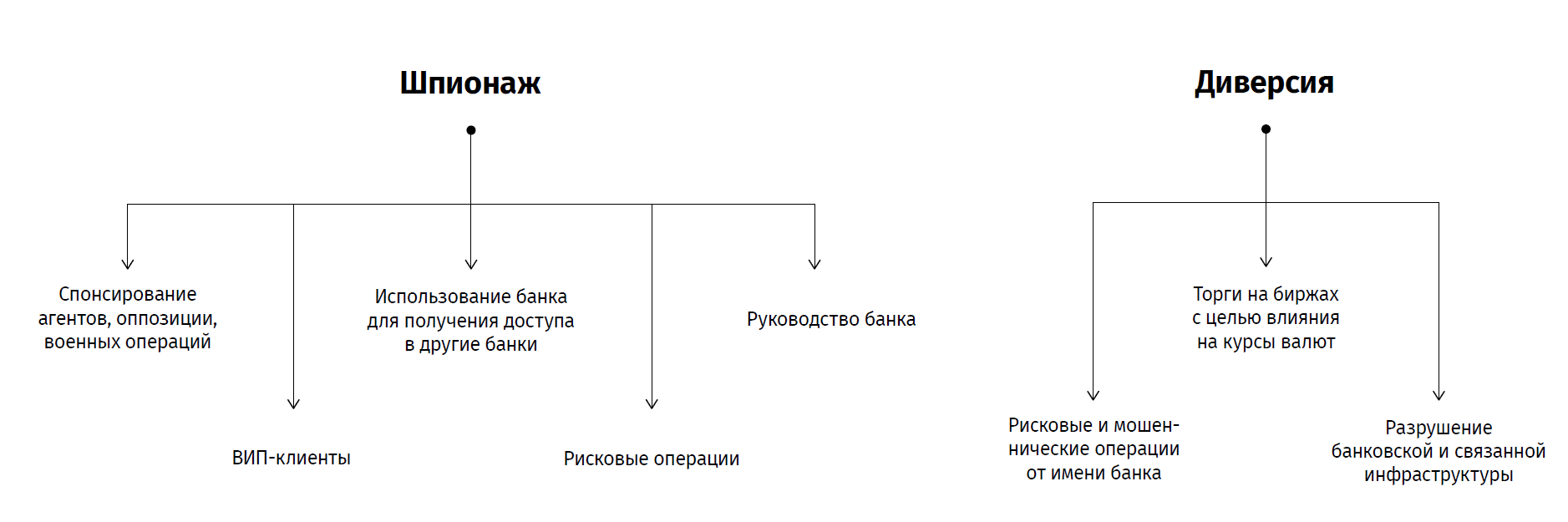
All this activity today is manifested in the development of two trends.
Some hackers are engaged in attacks on banks and accounts of their clients in order to steal money. Last year, $ 10.4 million was stolen from legal entities using viruses. At the same time, targeted attacks against financial institutions continue to bring the greatest income to cybercriminals.
However, in recent years, cybercrime, not connected with direct financial gain , has become more frequent. We are talking about sabotage attacks on critical infrastructure and espionage. This is due to the fact that the damage from idle time in the banking (and not only) sphere turns out to be much more tangible compared to the ordinary theft of money.
“Obtaining control over the IT infrastructure of large strategic banks or putting it out of operation makes it possible to influence the national economy, the exchange rate and leads to other large-scale consequences in which financially-motivated hackers are not always interested,” says Dmitry Volkov, CTO Group -IB and Threat Intelligence Cyber Intelligence Service Manager.
News about attacks on industrial plants and the detection of vulnerabilities are becoming more frequent. The purpose of these attacks is spying on the company's management, VIP clients or conducting sabotage. To attack critical infrastructure elements and disable it, simply getting remote access to the network using stolen passwords is not enough. Hackers need to understand how the systems of the organization function in order to think through the logic of malware operation aimed at their destruction.
One of the first cases of sabotage attacks - the activities of the American Equation Group. In 2010, the purpose of their attacks was a uranium enrichment plant in Iraq. Hackers introduced Stuxnet malware into the Industrial Control Systems (ICS) of the enterprise, which imperceptibly changed the rotation speed of Siemens centrifuges, which destroyed them.
Another attack on critical infrastructure with real damage occurred at the end of 2015, when attackers, using Black Energy 3, overloaded the network of three Ukrainian energy companies and disconnected uninterruptible power supplies.
However, stopping business processes threatens not only industrial enterprises. In a number of countries, the banking system is considered an object of critical infrastructure.
It was also attacked using ciphers. A year ago, we predicted that hackers would teach Trojans to spread themselves and use them to paralyze companies.
And so, on May 12, 2017, the WannaCry cipher machine appeared, and on June 27, 2017, NotPetya began to spread. It is highly likely that the target of the WannaCry attack was specific infrastructure facilities. All the other victims were “under the hot hand” by accident. In the case of NotPetya, the attack was more focused. The companies that use the MEDoc workflow system became its object.
In both cases, the purpose of the attacks was not to obtain financial benefits, but to stop business processes. Hackers managed to stop production at a number of enterprises and disrupt work in companies in the oil and gas and financial sectors.
“Thus, the use of encryptors in the financial sphere is more likely a tool of influence than financial gain,” said Dmitry Volkov.
The second trend, which also continues to gain momentum, is an attack on banks for financial gain. The main method of work of hackers in this area remains phishing: this year we found 1.4 million phishing links to 657 thousand domains. Five percent of them used HTTPS. Eighty percent of all phishing resources fall into three categories: financial companies (31%), cloud storage (24%), and postal services (24%).
Today, banks use anti-phishing protection methods, but the “social factor” does not work in their favor: many employees, for example, check personal mail in the workplace. Therefore, for attacks on banks, hackers collect addresses of employees of the organization and send them letters with malicious attachments during working hours.

CyberCrimeCon 2017 / Group-IB
Therefore, as Ilya Sachkov, the CEO and founder of Group-IB, noted during the conference, it is important to conduct explanatory conversations with employees, to teach them the basics of cyberhygiene, so that they always exercise caution. And not only while working on corporate technology.
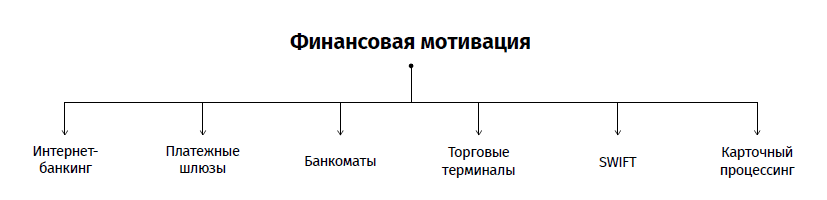
Malefactors are interested in a wide range of banking systems: they conduct attacks on SWIFT, card processing, payment gateways, terminals and ATMs. At the same time, “disembodiedness” is considered a new trend among hackers. They create programs that leave no footprints after the computer is restarted, as they work in RAM. Such scripts are poorly detected by standard means of protection and make it difficult to investigate incidents: you cannot restore file attributes, set the time of appearance of the virus, and identify triggers.
Imagine the situation: the bank was robbed. And on one of the computers among the scheduled tasks remained the task of running a script that loads the file from the legitimate repository. It is difficult to find it - in our practice we even came across a situation where the bank because of this twice became the victim of the same attack.
Attacks to payment gateways are rare, but they occur annually. The first such attacks were launched by members of the Anunak gang. Then they were joined by independent hackers and grouping Cobalt. So far we have recorded these attacks only in Russia, however, in our experience, the Russian Federation often acts as a testing ground. The tools and practices developed here then begin to be applied in other countries. Moreover, the goal is not only banks, but also companies that manage payment terminals.
In this case, the attacker's tactics are as follows:
The most common type of attack is attacks on the SWIFT system. SWIFT allows organizations to send transactions in the form of "financial messages". Attackers manipulate these messages, thereby stealing money. In May 2016, an attack was made on a bank in Hong Kong, in June - on SWIFT in Ukraine, and in December - on SWIFT in Turkey.
The logic of the attack is simple. First, servers with SWIFT are detected and messages are tracked. Outgoing messages replace payment information. Incoming confirmation messages are also intercepted, and the original details are changed to fraudulent ones.
However, the main purpose of cybercriminals this year was card processing. It is protected to a lesser extent than the system SWIFT, so through it you can steal a much larger amount. This type of crime was tested in Russia, and then applied in the United States and the CIS countries. The “secret of popularity” is that getting access to processing does not differ from hacking into the bank’s financial system.
The hackers obtained control over the banking network, legally opened cards, removed money withdrawal limits from them and connected overdraft. They used these cards to withdraw cash from one ATM, then move on to the next one, and so on. Often, attackers cashed in another country so that the bank’s security service could not promptly transfer information to the police. The average damage from one such attack was half a million dollars.
After successful attacks on banks, attackers sought to destroy the traces of their presence. To do this, they used the tools SDelete, MBRKiller and other samopisnye utilities for mashing data. Cryptographers (for example, Petya - PetrWrap) were also used for this purpose.
Cryptocurrencies and related services are a dynamic and highly profitable market. With such a speed of development and the inflow of money, security issues often become secondary to blockchain startups. What hackers use.
According to our data, the total damage from targeted hacker attacks on the crypto industry amounted to 168 million dollars, while attacks on banks bring about 1.5 million dollars to attackers. In addition to high profitability, hackers are attracted by anonymity, which is one of the principles of the cryptocurrency industry.
“There was a leak of user databases, domain name theft. The owners of botnets track the circulation of infected devices to applications of wallets, exchanges, funds. Creation and promotion of phishing clone sites to intercept access to client accounts is already put on stream, ”said Dmitry Volkov.
ICO phishing is becoming very popular due to its effectiveness. The tactics of attacking is simple. They track new ICO projects and create phishing sites that request secret keys. All entered keys are automatically connected to the wallets of the attackers, and the funds are displayed on the specified accounts.
Last year, the Hong Kong cryptocurrency exchange Bitfinex was compromised. The attackers stole 120 thousand bitcoins, which caused the fluctuation of the cryptocurrency rate. Hackers gained control over the corporate infrastructure of the exchange, so the three-key multi-signature technology used to protect the funds was powerless.
At the same time, in order to gain access to wallets, it is not necessary to create a phishing page for each exchange. Hackers use password recovery features by email or mobile phone number. And now phishing pages for popular mail services are used to access email.

CyberCrimeCon 2017 / Group-IB
Phishing is not the only threat to ICO. Attackers also use blackmail to prevent sales of tokens. As Ilya Remizov, director of technology at Blackmoon Crypto, noted, before the start of ICO, their company received threats to launch a DDoS attack on the servers if they did not transfer the “ransom” to a certain account. And many companies agree to such "requests", because a delay at the start can lead to the death of the project. By the way, Blackmoon Crypto did not meet the requirements of the blackmailers, and the company's ICO was successful.
Note that before conducting an ICO, it is necessary to ensure the safety of three components: the team, IT infrastructure and communication processes. In the first case, it is worth monitoring the manifestations of social engineering, when hackers are trying to find out from the company's employees details about the fundraising or the intricacies of the process.
With regard to infrastructure preparation, there is a need to take a number of measures, namely, to remove all nodes for ICO into a separate infrastructure, conduct stress tests with the cloud service’s technical service, prepare for scaling and organize “combat exercises” with working out possible emergency situations.
Spying on communication processes allows you to detect fraudulent schemes, phishing attempts and detect fake pages of the company's management in social networks where false information can be published (for example, about the beginning of ICO with modified wallet addresses).
“Thus, blockchain startups need to establish clear roles in the ICO team and be prepared for the rapid flow of the project and changes to the rules of the game,” said Ilya Remizov. In this case, the attackers will be difficult to prevent the collection of cryptographic tools.
During the conference CyberCrimeCon 2017, we talked about the main trends that can be traced in the cybercrime world, and the techniques used by hackers.
1. In the hacker community, two trends are clearly visible. Some criminals are engaged in attacks on banks in order to steal money. Another part - conducts sabotage attacks on critical infrastructure.
2. The purpose of attacks on critical infrastructure is to disable the key components of the systems and interrupt business processes, since the damage from downtime can be much more tangible than the simple theft of funds. Recently, such attacks are carried out using encryption viruses.
3. Financially motivated hackers are interested in a wide range of banking systems: they conduct attacks on SWIFT, card processing, payment gateways, terminals and ATMs. However, some of their programs do not leave traces in the system after restarting the computer. The main method of work of hackers in this area is phishing. And the main goal is card processing.
4. The excitement around cryptocurrency, blockchain and ICO caused increased attention from cybercriminals. Hacking cryptocurrency exchanges are carried out in the same way as targeted attacks on banks. Similar tools and tactics are used. Including phishing, blackmail and social engineering.
5. In order to prevent hackers from undermining the conduct of ICOs, it is necessary to ensure the safety of three components: the team, IT infrastructure and communication processes. Being ready for a quick change in the rules of the game, any destructive activity can be prevented.
CyberCrimeCon 2017 - Group-IB conference on cyber threats / Group-IB
At the conference, we also presented our report on cyber threat trends for the financial sector. Today’s post is a summary of what we’ve been talking about : trends in high-tech crime.
 CyberCrimeCon 2017 / Group-IB
CyberCrimeCon 2017 / Group-IB')
High-tech cybercrime market
The cybercrime market is developing - with each year the number of attacks grows and the amounts stolen increase. According to our data, in Russia, the number of embezzlements in Internet banking from individuals increased by 144% compared to last year. The number of thefts using android trojans increased by 136% over the same period. In total, in the second half of 2016 and the first half of 2017, attackers stole 4.7 billion rubles.
Regarding the situation in the world, in 2015 the damage done by cybercriminals amounted to 3 trillion dollars. According to some estimates , this figure will increase to 6 trillion by 2021.

CyberCrimeCon 2017 / Group-IB
Cybercriminals Motivation
As soon as hackers discover a new “vector” of attacks (safer or more profitable), they immediately begin to create tools, write scripts, think over schemes to effectively exploit the detected vulnerabilities.
All this activity today is manifested in the development of two trends.
Some hackers are engaged in attacks on banks and accounts of their clients in order to steal money. Last year, $ 10.4 million was stolen from legal entities using viruses. At the same time, targeted attacks against financial institutions continue to bring the greatest income to cybercriminals.
However, in recent years, cybercrime, not connected with direct financial gain , has become more frequent. We are talking about sabotage attacks on critical infrastructure and espionage. This is due to the fact that the damage from idle time in the banking (and not only) sphere turns out to be much more tangible compared to the ordinary theft of money.
“Obtaining control over the IT infrastructure of large strategic banks or putting it out of operation makes it possible to influence the national economy, the exchange rate and leads to other large-scale consequences in which financially-motivated hackers are not always interested,” says Dmitry Volkov, CTO Group -IB and Threat Intelligence Cyber Intelligence Service Manager.
Those who do not need money
News about attacks on industrial plants and the detection of vulnerabilities are becoming more frequent. The purpose of these attacks is spying on the company's management, VIP clients or conducting sabotage. To attack critical infrastructure elements and disable it, simply getting remote access to the network using stolen passwords is not enough. Hackers need to understand how the systems of the organization function in order to think through the logic of malware operation aimed at their destruction.

One of the first cases of sabotage attacks - the activities of the American Equation Group. In 2010, the purpose of their attacks was a uranium enrichment plant in Iraq. Hackers introduced Stuxnet malware into the Industrial Control Systems (ICS) of the enterprise, which imperceptibly changed the rotation speed of Siemens centrifuges, which destroyed them.
Another attack on critical infrastructure with real damage occurred at the end of 2015, when attackers, using Black Energy 3, overloaded the network of three Ukrainian energy companies and disconnected uninterruptible power supplies.
However, stopping business processes threatens not only industrial enterprises. In a number of countries, the banking system is considered an object of critical infrastructure.
It was also attacked using ciphers. A year ago, we predicted that hackers would teach Trojans to spread themselves and use them to paralyze companies.
And so, on May 12, 2017, the WannaCry cipher machine appeared, and on June 27, 2017, NotPetya began to spread. It is highly likely that the target of the WannaCry attack was specific infrastructure facilities. All the other victims were “under the hot hand” by accident. In the case of NotPetya, the attack was more focused. The companies that use the MEDoc workflow system became its object.
In both cases, the purpose of the attacks was not to obtain financial benefits, but to stop business processes. Hackers managed to stop production at a number of enterprises and disrupt work in companies in the oil and gas and financial sectors.
“Thus, the use of encryptors in the financial sphere is more likely a tool of influence than financial gain,” said Dmitry Volkov.
Financially motivated hackers
The second trend, which also continues to gain momentum, is an attack on banks for financial gain. The main method of work of hackers in this area remains phishing: this year we found 1.4 million phishing links to 657 thousand domains. Five percent of them used HTTPS. Eighty percent of all phishing resources fall into three categories: financial companies (31%), cloud storage (24%), and postal services (24%).
Today, banks use anti-phishing protection methods, but the “social factor” does not work in their favor: many employees, for example, check personal mail in the workplace. Therefore, for attacks on banks, hackers collect addresses of employees of the organization and send them letters with malicious attachments during working hours.

CyberCrimeCon 2017 / Group-IB
Therefore, as Ilya Sachkov, the CEO and founder of Group-IB, noted during the conference, it is important to conduct explanatory conversations with employees, to teach them the basics of cyberhygiene, so that they always exercise caution. And not only while working on corporate technology.

Malefactors are interested in a wide range of banking systems: they conduct attacks on SWIFT, card processing, payment gateways, terminals and ATMs. At the same time, “disembodiedness” is considered a new trend among hackers. They create programs that leave no footprints after the computer is restarted, as they work in RAM. Such scripts are poorly detected by standard means of protection and make it difficult to investigate incidents: you cannot restore file attributes, set the time of appearance of the virus, and identify triggers.
Imagine the situation: the bank was robbed. And on one of the computers among the scheduled tasks remained the task of running a script that loads the file from the legitimate repository. It is difficult to find it - in our practice we even came across a situation where the bank because of this twice became the victim of the same attack.
Attacks to payment gateways are rare, but they occur annually. The first such attacks were launched by members of the Anunak gang. Then they were joined by independent hackers and grouping Cobalt. So far we have recorded these attacks only in Russia, however, in our experience, the Russian Federation often acts as a testing ground. The tools and practices developed here then begin to be applied in other countries. Moreover, the goal is not only banks, but also companies that manage payment terminals.
In this case, the attacker's tactics are as follows:
- Attackers get remote access to the network and look for payment gateways.
- After looking for scripts or logs to understand the format of the message transfer.
- Communication with payment gateways is established using SOCKS proxies, etc.
- Runs a script that generates thousands of transactions for small amounts to replenish the cards of intruders. Every day through the gateways passes a huge number of such transactions, because the scam operations are lost in the total amount.
- Next comes the money laundering process.
The most common type of attack is attacks on the SWIFT system. SWIFT allows organizations to send transactions in the form of "financial messages". Attackers manipulate these messages, thereby stealing money. In May 2016, an attack was made on a bank in Hong Kong, in June - on SWIFT in Ukraine, and in December - on SWIFT in Turkey.
The logic of the attack is simple. First, servers with SWIFT are detected and messages are tracked. Outgoing messages replace payment information. Incoming confirmation messages are also intercepted, and the original details are changed to fraudulent ones.
However, the main purpose of cybercriminals this year was card processing. It is protected to a lesser extent than the system SWIFT, so through it you can steal a much larger amount. This type of crime was tested in Russia, and then applied in the United States and the CIS countries. The “secret of popularity” is that getting access to processing does not differ from hacking into the bank’s financial system.
The hackers obtained control over the banking network, legally opened cards, removed money withdrawal limits from them and connected overdraft. They used these cards to withdraw cash from one ATM, then move on to the next one, and so on. Often, attackers cashed in another country so that the bank’s security service could not promptly transfer information to the police. The average damage from one such attack was half a million dollars.
After successful attacks on banks, attackers sought to destroy the traces of their presence. To do this, they used the tools SDelete, MBRKiller and other samopisnye utilities for mashing data. Cryptographers (for example, Petya - PetrWrap) were also used for this purpose.
New trend in financially-oriented crime
Cryptocurrencies and related services are a dynamic and highly profitable market. With such a speed of development and the inflow of money, security issues often become secondary to blockchain startups. What hackers use.
According to our data, the total damage from targeted hacker attacks on the crypto industry amounted to 168 million dollars, while attacks on banks bring about 1.5 million dollars to attackers. In addition to high profitability, hackers are attracted by anonymity, which is one of the principles of the cryptocurrency industry.
“There was a leak of user databases, domain name theft. The owners of botnets track the circulation of infected devices to applications of wallets, exchanges, funds. Creation and promotion of phishing clone sites to intercept access to client accounts is already put on stream, ”said Dmitry Volkov.
ICO phishing is becoming very popular due to its effectiveness. The tactics of attacking is simple. They track new ICO projects and create phishing sites that request secret keys. All entered keys are automatically connected to the wallets of the attackers, and the funds are displayed on the specified accounts.
Last year, the Hong Kong cryptocurrency exchange Bitfinex was compromised. The attackers stole 120 thousand bitcoins, which caused the fluctuation of the cryptocurrency rate. Hackers gained control over the corporate infrastructure of the exchange, so the three-key multi-signature technology used to protect the funds was powerless.
At the same time, in order to gain access to wallets, it is not necessary to create a phishing page for each exchange. Hackers use password recovery features by email or mobile phone number. And now phishing pages for popular mail services are used to access email.

CyberCrimeCon 2017 / Group-IB
Phishing is not the only threat to ICO. Attackers also use blackmail to prevent sales of tokens. As Ilya Remizov, director of technology at Blackmoon Crypto, noted, before the start of ICO, their company received threats to launch a DDoS attack on the servers if they did not transfer the “ransom” to a certain account. And many companies agree to such "requests", because a delay at the start can lead to the death of the project. By the way, Blackmoon Crypto did not meet the requirements of the blackmailers, and the company's ICO was successful.
Note that before conducting an ICO, it is necessary to ensure the safety of three components: the team, IT infrastructure and communication processes. In the first case, it is worth monitoring the manifestations of social engineering, when hackers are trying to find out from the company's employees details about the fundraising or the intricacies of the process.
With regard to infrastructure preparation, there is a need to take a number of measures, namely, to remove all nodes for ICO into a separate infrastructure, conduct stress tests with the cloud service’s technical service, prepare for scaling and organize “combat exercises” with working out possible emergency situations.
Spying on communication processes allows you to detect fraudulent schemes, phishing attempts and detect fake pages of the company's management in social networks where false information can be published (for example, about the beginning of ICO with modified wallet addresses).
“Thus, blockchain startups need to establish clear roles in the ICO team and be prepared for the rapid flow of the project and changes to the rules of the game,” said Ilya Remizov. In this case, the attackers will be difficult to prevent the collection of cryptographic tools.
Key findings
During the conference CyberCrimeCon 2017, we talked about the main trends that can be traced in the cybercrime world, and the techniques used by hackers.
1. In the hacker community, two trends are clearly visible. Some criminals are engaged in attacks on banks in order to steal money. Another part - conducts sabotage attacks on critical infrastructure.
2. The purpose of attacks on critical infrastructure is to disable the key components of the systems and interrupt business processes, since the damage from downtime can be much more tangible than the simple theft of funds. Recently, such attacks are carried out using encryption viruses.
3. Financially motivated hackers are interested in a wide range of banking systems: they conduct attacks on SWIFT, card processing, payment gateways, terminals and ATMs. However, some of their programs do not leave traces in the system after restarting the computer. The main method of work of hackers in this area is phishing. And the main goal is card processing.
4. The excitement around cryptocurrency, blockchain and ICO caused increased attention from cybercriminals. Hacking cryptocurrency exchanges are carried out in the same way as targeted attacks on banks. Similar tools and tactics are used. Including phishing, blackmail and social engineering.
5. In order to prevent hackers from undermining the conduct of ICOs, it is necessary to ensure the safety of three components: the team, IT infrastructure and communication processes. Being ready for a quick change in the rules of the game, any destructive activity can be prevented.
CyberCrimeCon 2017 - Group-IB conference on cyber threats / Group-IB
Source: https://habr.com/ru/post/341812/
All Articles