SOC for beginners. SOC tasks: security control
We continue the cycle of our articles on cyber attack centers for beginners. In the last article, we talked about Security Monitoring, the SIEM tools and the Use Case.
The term Security Operations Center for many is associated exclusively with the monitoring of incidents. For many service providers, this is, in principle, at hand, so few people say that monitoring has a number of serious limitations in terms of protection against cyber attacks.
In this article, we will demonstrate with examples the weak points of monitoring information security incidents, tell you what to do about it, and in the end, as usual, we will give some practical recommendations on how to conduct an infrastructure security audit using our own resources.
')

What are the strengths and weaknesses of Security Monitoring? The fact that in the first place he handles security events. These are either events and triggering of information protection rules, or logs and log files: operating system, database, application software.
At the same time, there are a large number of situations in which either the activity is not explicitly recorded in the logs, or the flow of events or the capabilities of the systems do not effectively organize the monitoring process.
Let's look at examples.
1. Operation of system vulnerabilities
Consider a fairly typical situation: there is a substantially secure perimeter, a separate DMZ segment and a rather weakly segmented office network of computers. And so, in this network we have a “new” host. Whether this machine belongs to an insider, or is it an ordinary employee’s laptop infected by social engineering, is not so important. The attacker begins to engage in exploiting the vulnerability of the RCE on the operating systems of servers and workstations that are accessible to him within the segment.
How can I fix this problem? The lack of network segmentation leaves us hopeless of detecting from network security tools, be it IPS or other systems. In the logs of the operating system itself, the exploitation of the RCE vulnerability does not carry any special code, and therefore there is no way to distinguish it from the usual authentication attempt in the OS. One way or another, the logs will launch the svchost.exe system process from the system user.
Our only hope remains IDS-modules of host protection, but, as our practice shows, having a working and regularly updated IDS on all infrastructure hosts is a rarity.
This is how the exploitation of the “painful” EternalBlue SMB Remote Windows Kernel Pool Corruption vulnerability (fixed by security update MS17-010) looks like. Please note that the absence of any of the three sources given in the example will not give us a complete picture and a chance to understand whether there was an attack or not.
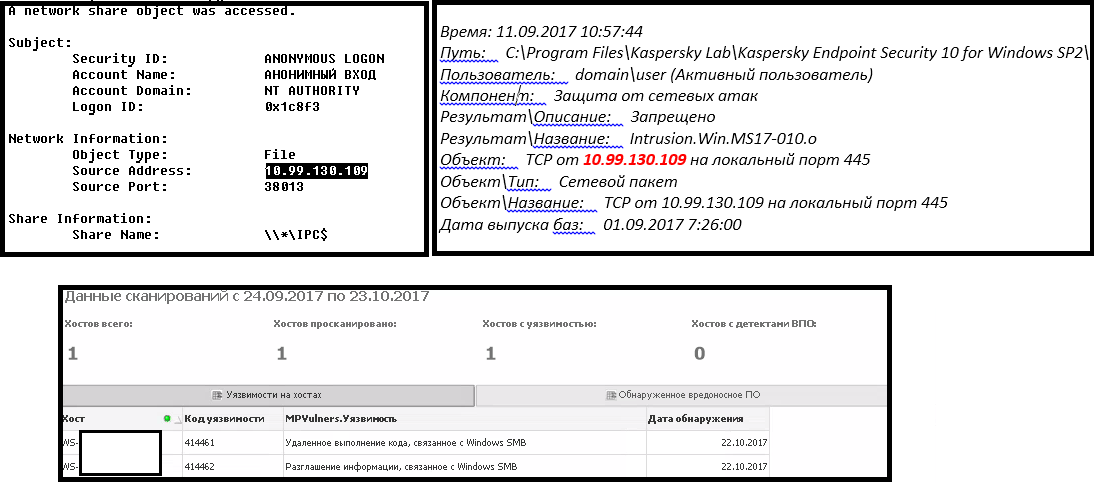
As a result, you can hope for a miracle, or you can begin to build the process of managing vulnerabilities and try to localize the problem before it occurs .
There are quite a lot of specialized materials on this issue, so we will not focus on it. Let's designate only a few theses.
“Winning the race” with vulnerabilities and building an infrastructure with up-to-date security updates is a task almost impossible to implement in a large corporate client. The number of vulnerabilities is growing from year to year, most of which are of medium and high severity level (according to the CVSS v2 rating system).
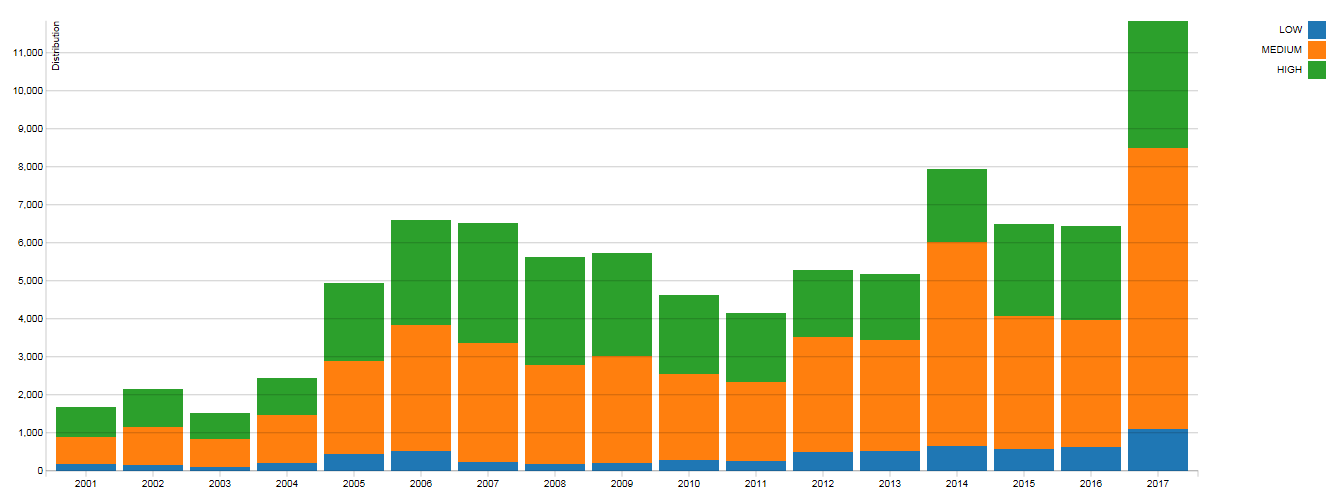
Distribution of the number of vulnerabilities by year in terms of their criticality ( reference to the source ).
When reviewing and compiling a vulnerability elimination map, you must not only adhere to the Pareto principle (i.e., select only the most critical part to eliminate), but also work very carefully with compensating measures — with accessibility of vulnerability due to adjustments of protection tools, analysis of possible vectors of etc.
But this is not the only task left to the monitoring capabilities.
2. Profiling Direct Internet Access
Periodically, in the eyes of the security service, SIEM turns into a powerful tool that is able to handle any events or data streams. In this case, the following problem may arise, for example: within the company there is a certain agreed number of routes allowed for direct access to the Internet bypassing proxy servers. And in order to control the work of network specialists, SIEM is assigned the task: to control all previously uncoordinated opening of direct access by analyzing sessions from the corporate network.
It would seem that the task is simple and logical. But there are several limitations:
As a result, this question is primarily concerned with configuration management and change control. And, despite the theoretical possibility of solving this problem with the help of monitoring, it is many times more efficient to operate with specialized means and already in the SIEM to monitor the operation of the process.
Collectively, these examples lead us to a more global task: SOC needs to understand the company's infrastructure, its vulnerabilities and processes in a “broad sense” in detail and decide how to most effectively monitor this infrastructure and how quickly to find out what is in it something has changed - that is, at each moment in time to objectively assess the actual security of the infrastructure from attack.
Security Control - Tasks and Technologies
In our opinion, the following tasks fall within the scope of security control:
For each of the designated tasks has its own toolkit:
But one of the most important and at the same time most undervalued security resources is its language and communication. From our practice of working in clients, with a built-in human communication with IT and applied people, even during a conversation in a smoking room, you can learn about future or past changes much more than during a long technical analysis of settings (which, nevertheless, does not negate the importance of this process) .
Monitoring and control of security => Monitoring + control of security
One of the important advantages of running parallel monitoring and security monitoring processes in a SOC is the ability to “pereopylny” one process information from another, thereby increasing overall security. Let us take an example of how this works.
Monitoring as a tool for identifying new hosts and assets
If the company does not build an asset inventory process or IT does not share its results, the emergence of a new system with critical functionality or critical data may pass by information security. But the situation changes significantly when there is a monitoring process.
In 99% of cases, a newly appeared host will “show” itself without fail:
If these sources are connected to monitoring, then using a fairly simple report or script, you can identify such “spyware” hosts.
Example: Windows authentication events with filters by known host names. As a rule, the company has criteria for naming hosts that can be caught.
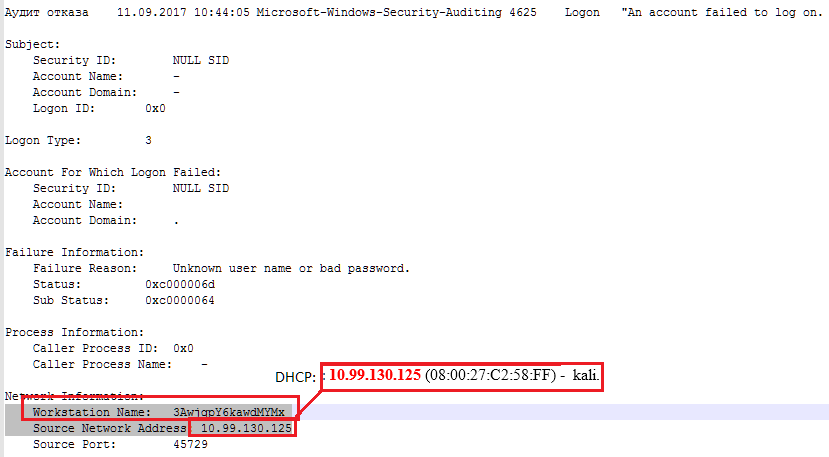
And, already possessing the information that new entities have appeared in the company's network, it is quite possible to sort out their tasks, legitimacy or take them into account in the general threat model.
Conversely, if it is not possible to close any process or technological vulnerability forever, additional signatures and scenarios that control the exploitation of this vulnerability can be developed as a compensating measure.
An example is the process of setting up and servicing technological equipment at a plant (or, for example, a state district power station — in other words, in almost any production). To work with such equipment, as a rule, engineers from the manufacturer are involved, and often these are foreign specialists who need to somehow organize remote access to the site. Quite often, due to the limitations of the existing network architecture and technology segments, remote access is opened directly from the Internet (via RDP, SSH) to terminal servers, from which equipment is already being set up using specialized software. And in another way to organize this access is simply not possible. Yes, it is possible to open access by request and to a strictly defined technological window, limit the addresses from which connections to the terminal server will be allowed, but still there is a risk of interception of the RDP / SSH session, exploitation of OS vulnerabilities from the Internet, penetration into the technological network through AWS commissioning engineer, backdoor infection of this terminal server, etc.
Since there is no possibility to “close” this process vulnerability, as a compensating measure, we can offer enhanced monitoring of terminal server data and activity on them, namely:
These measures, although they will not prevent the fact of hacking or illegitimate actions within the framework of the considered process, but will help in time to identify them and respond.
Security control - where to start
We suggest starting the approach to security control tasks with the following actions:
Even this not very laborious slice of information will allow you to make the first approach to understanding the actual security of your infrastructure. Well, then the road will be mastered by going ... or wait for our next articles :)
The term Security Operations Center for many is associated exclusively with the monitoring of incidents. For many service providers, this is, in principle, at hand, so few people say that monitoring has a number of serious limitations in terms of protection against cyber attacks.
In this article, we will demonstrate with examples the weak points of monitoring information security incidents, tell you what to do about it, and in the end, as usual, we will give some practical recommendations on how to conduct an infrastructure security audit using our own resources.
')

Vulnerability Security Monitoring
What are the strengths and weaknesses of Security Monitoring? The fact that in the first place he handles security events. These are either events and triggering of information protection rules, or logs and log files: operating system, database, application software.
At the same time, there are a large number of situations in which either the activity is not explicitly recorded in the logs, or the flow of events or the capabilities of the systems do not effectively organize the monitoring process.
Let's look at examples.
1. Operation of system vulnerabilities
Consider a fairly typical situation: there is a substantially secure perimeter, a separate DMZ segment and a rather weakly segmented office network of computers. And so, in this network we have a “new” host. Whether this machine belongs to an insider, or is it an ordinary employee’s laptop infected by social engineering, is not so important. The attacker begins to engage in exploiting the vulnerability of the RCE on the operating systems of servers and workstations that are accessible to him within the segment.
How can I fix this problem? The lack of network segmentation leaves us hopeless of detecting from network security tools, be it IPS or other systems. In the logs of the operating system itself, the exploitation of the RCE vulnerability does not carry any special code, and therefore there is no way to distinguish it from the usual authentication attempt in the OS. One way or another, the logs will launch the svchost.exe system process from the system user.
Our only hope remains IDS-modules of host protection, but, as our practice shows, having a working and regularly updated IDS on all infrastructure hosts is a rarity.
This is how the exploitation of the “painful” EternalBlue SMB Remote Windows Kernel Pool Corruption vulnerability (fixed by security update MS17-010) looks like. Please note that the absence of any of the three sources given in the example will not give us a complete picture and a chance to understand whether there was an attack or not.

As a result, you can hope for a miracle, or you can begin to build the process of managing vulnerabilities and try to localize the problem before it occurs .
There are quite a lot of specialized materials on this issue, so we will not focus on it. Let's designate only a few theses.
“Winning the race” with vulnerabilities and building an infrastructure with up-to-date security updates is a task almost impossible to implement in a large corporate client. The number of vulnerabilities is growing from year to year, most of which are of medium and high severity level (according to the CVSS v2 rating system).

Distribution of the number of vulnerabilities by year in terms of their criticality ( reference to the source ).
When reviewing and compiling a vulnerability elimination map, you must not only adhere to the Pareto principle (i.e., select only the most critical part to eliminate), but also work very carefully with compensating measures — with accessibility of vulnerability due to adjustments of protection tools, analysis of possible vectors of etc.
But this is not the only task left to the monitoring capabilities.
2. Profiling Direct Internet Access
Periodically, in the eyes of the security service, SIEM turns into a powerful tool that is able to handle any events or data streams. In this case, the following problem may arise, for example: within the company there is a certain agreed number of routes allowed for direct access to the Internet bypassing proxy servers. And in order to control the work of network specialists, SIEM is assigned the task: to control all previously uncoordinated opening of direct access by analyzing sessions from the corporate network.
It would seem that the task is simple and logical. But there are several limitations:
- In an average company, the number of ACL rules that allow direct access to the Internet, for various reasons (limiting the work of a proxy, specialized software, etc.) is several hundred. Creating a profile of such a characteristic in SIEM is not difficult, but here we are faced with the second problem.
- These rules are constantly changing on a daily basis. As the current test systems disappear, new ones appear, some of the accesses are opened for testing or maintenance work. As a result, it creates such a huge flow of incidents every day that it is difficult to handle it.
- It should be noted that such a rule itself, with all its apparent simplicity, is very “heavy” for the classical correlation in the SIEM. First of all, this is due to the huge flow of events passing through the firewall towards the Internet.
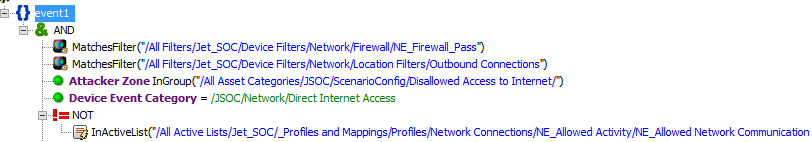
As a result, this question is primarily concerned with configuration management and change control. And, despite the theoretical possibility of solving this problem with the help of monitoring, it is many times more efficient to operate with specialized means and already in the SIEM to monitor the operation of the process.
Collectively, these examples lead us to a more global task: SOC needs to understand the company's infrastructure, its vulnerabilities and processes in a “broad sense” in detail and decide how to most effectively monitor this infrastructure and how quickly to find out what is in it something has changed - that is, at each moment in time to objectively assess the actual security of the infrastructure from attack.
Security Control - Tasks and Technologies
In our opinion, the following tasks fall within the scope of security control:
- Determination of the perimeter and services of the company available from the Internet.
- Analysis of external perimeter vulnerabilities and internal infrastructure.
- Analysis of critical network and infrastructure equipment configurations.
- Analysis of server and workstations security policies.
- Evaluation of the effectiveness of policies implemented on the means of protection, in terms of completeness and functionality.
- Detection of vulnerabilities in the program code of the applied software.
- And ideally, an analysis of key business processes for process vulnerabilities that may entail financial losses.
For each of the designated tasks has its own toolkit:
- security scanners;
- firewall management systems that effectively manage network equipment;
- integrity monitoring systems;
- configuration management systems;
- code analysis systems;
- manual checks of overall security using penetration tests.
But one of the most important and at the same time most undervalued security resources is its language and communication. From our practice of working in clients, with a built-in human communication with IT and applied people, even during a conversation in a smoking room, you can learn about future or past changes much more than during a long technical analysis of settings (which, nevertheless, does not negate the importance of this process) .
Monitoring and control of security => Monitoring + control of security
One of the important advantages of running parallel monitoring and security monitoring processes in a SOC is the ability to “pereopylny” one process information from another, thereby increasing overall security. Let us take an example of how this works.
Monitoring as a tool for identifying new hosts and assets
If the company does not build an asset inventory process or IT does not share its results, the emergence of a new system with critical functionality or critical data may pass by information security. But the situation changes significantly when there is a monitoring process.
In 99% of cases, a newly appeared host will “show” itself without fail:
- Attempts to access the Internet directly or through a proxy.
- Will try to contact the domain controller.
- Will attempt to access the DNS.
If these sources are connected to monitoring, then using a fairly simple report or script, you can identify such “spyware” hosts.
Example: Windows authentication events with filters by known host names. As a rule, the company has criteria for naming hosts that can be caught.

And, already possessing the information that new entities have appeared in the company's network, it is quite possible to sort out their tasks, legitimacy or take them into account in the general threat model.
Conversely, if it is not possible to close any process or technological vulnerability forever, additional signatures and scenarios that control the exploitation of this vulnerability can be developed as a compensating measure.
An example is the process of setting up and servicing technological equipment at a plant (or, for example, a state district power station — in other words, in almost any production). To work with such equipment, as a rule, engineers from the manufacturer are involved, and often these are foreign specialists who need to somehow organize remote access to the site. Quite often, due to the limitations of the existing network architecture and technology segments, remote access is opened directly from the Internet (via RDP, SSH) to terminal servers, from which equipment is already being set up using specialized software. And in another way to organize this access is simply not possible. Yes, it is possible to open access by request and to a strictly defined technological window, limit the addresses from which connections to the terminal server will be allowed, but still there is a risk of interception of the RDP / SSH session, exploitation of OS vulnerabilities from the Internet, penetration into the technological network through AWS commissioning engineer, backdoor infection of this terminal server, etc.
Since there is no possibility to “close” this process vulnerability, as a compensating measure, we can offer enhanced monitoring of terminal server data and activity on them, namely:
- Monitor any activity (including network activity in the OS in the software) outside the agreed technological windows.
- To configure network activity, and also to collect an authentication profile on these terminal servers, in order to see deviations from the usual process in terms of new connections, authentication from unresolved addresses or accounts.
- Identify previously unknown / non-profiled processes, installation of services and new software.
- Monitor changes in critical system directories and registry keys.
- Detect suspicious and malicious objects through AVPO, correlating them with activity on the host in the vicinity of its launch.
- Monitor external connections, including unsuccessful attempts to access the host from the outside.
- Detect events that change the settings of the host firewall, as well as ACL changes on the network firewall, which restricts access to and from this terminal server.
- Control local account creation, privilege escalation for existing accounts, etc.
These measures, although they will not prevent the fact of hacking or illegitimate actions within the framework of the considered process, but will help in time to identify them and respond.
Security control - where to start
We suggest starting the approach to security control tasks with the following actions:
- Perform a comprehensive perimeter inventory - methods and channels of access to the Internet, used external addresses, systems accessible from the Internet, services and protocols. Even at this step, it is often possible to fix a certain number of forgotten vulnerable services and administrative ports opened from the Internet.
For example, for the outer perimeter, you can conduct an inventory scan and add the results to the SIEM. In this case, it will immediately be clear what and how is recorded in the logs, and, comparing the results with the output of the scanner, it remains to just fill in the descriptions.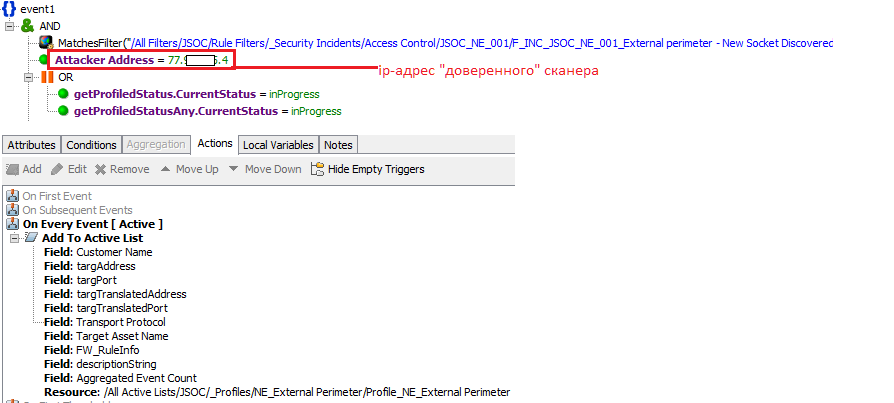
- Evaluate the general state of basic protection (antivirus, FW, Proxy) in terms of the width of their coverage: do they cover the entire infrastructure, are the policies and signatures used, etc. relevant?
- In the “large cell” draw the network infrastructure of the company - the division by subnets in a functional sense, the presence of segmentation, the possibility of monitoring interactions and separating one segment from another.
For example, we primarily try to highlight the following network segments:- DMZ.
- External addressing.
- Guest Wifi and other networks in which there are hosts that are not controlled by the company's security.
- Local VPN address pool.
- Separate closed segments (we have, for example, the Solar JSOC ARM segment, a client bank and a segment for testing Malvari).
- Scan both the perimeter and internal infrastructure for vulnerabilities, look at the general condition, highlight the most critical problems that need to be either closed or put on monitoring.
- To put on regular control and update the specified information slices. Alternatively, for starters, you can focus on the reports. And, gradually analyzing the information and improving the process, come to the alerts.
Even this not very laborious slice of information will allow you to make the first approach to understanding the actual security of your infrastructure. Well, then the road will be mastered by going ... or wait for our next articles :)
Source: https://habr.com/ru/post/341530/
All Articles