Network visibility and Ixia solutions
When designing a security architecture, IT departments in many enterprises rely mainly on what their hardware and software security and monitoring tools can do. Much less thinking (or not thinking at all) about how to provide these tools with a complete picture of the data moving within the enterprise. In the corporate network segment this was the first time that Ixia did it.

It is difficult to refute the fact that it is impossible to control what is impossible to see. Evaluating incoming / outgoing corporate network traffic is the best defense against attacks and errors that can lead to network disruption, loss of important data, and further to customer dissatisfaction, and this is a direct loss of money.
Therefore, CIOs and “security guards” of enterprises should firmly understand that buying and deploying an ever-growing array of modern security tools is nothing more than a start.
')
For reliable network security, appropriate solutions must implement all their capabilities. This requires visibility tools that have access to all network traffic and provide accurate real-time data. Requires a flexible visibility architecture that is optimized for continuous network monitoring.
Security Improvement
The network perimeter, once clearly delineated by a firewall between the corporate network and the Internet, is being erased today - as users become increasingly mobile, and organizations are increasingly using cloud solutions. Without a clearly defined perimeter, it becomes difficult (or impossible at all) to identify all traffic flows.
Gartner predicts that by 2018, up to 25% of the corporate data flow will bypass traditional security tools and flow directly between mobile devices and the cloud.
A study of Sandvine in early 2016 showed that almost three-quarters of all Internet traffic is encrypted using SSL technology. Google in the same year called the figure in almost 80% of international traffic. However, attackers also use SSL encryption to hide their traffic and threats.
As a result, IT departments now routinely decrypt inbound and outbound traffic beyond the boundary of the firewall, before sending it to the destination. To some extent, this allows identifying risks and threats, such as breaches of regulatory compliance, data leaks, malware, intrusion attempts, etc.
Network traffic is now mainly composed of structured and unstructured data, which includes voice and video. Its volume often exceeds the processing capacity.
Virtualization has become one of the most "subversive" IT innovations in the modern computing era. Virtualization technology allows IT to use standard low-cost servers. However, traditional monitoring methods are not sufficient to control virtual traffic. Virtualization also brought private, public and hybrid clouds, infrastructure as a service (Infrastructure-as-a-Service, IaaS) and platform as a service (Platform-as-a-Service, PaaS).
Scalability and control over the distribution of resources are the main advantages of both virtualization and cloud technologies. On the other hand, organizations migrate workloads from their local data centers to a public cloud, and it is becoming increasingly difficult to monitor and control data flows, that is, new invisibility zones, “blind zones” are being created.
Verizon's 2016 State of the Market: Enterprise Cloud 2016 study found that more than 40% of companies already use five or more cloud providers. The Okta "2016 Business @ Work" study found that companies in most cases use from 10 to 16 applications running in the public cloud.
Indeed, the cloud offers unprecedented IT infrastructure flexibility, but it also forces companies to expand their traditional network perimeter — often to places where they have no visibility or control. These blind spots can quickly become shelters for security threats lurking in the shadows.
The first users of SaaS were mostly small and medium-sized businesses (SMB). Now that SaaS solutions are becoming more complex and functional, they are also used by larger enterprises, including distributed ones. Accordingly, the growing use of cloud applications makes them a target for cyber attacks. Cisco's 2015-2020 Visual Networking Index predicts that by 2019, cloud applications will provide up to 90% of global mobile traffic.
Finally, the “Internet of Things” trend (Internet of Thing, IoT) has created a new market for billions of “smart connections” of devices and products — from surveillance cameras and “smart thermostats” to cars — that are connected to the Internet, collect, store, transmit and share a huge amount of information.
For them, new computational models appear, such as mobile access computing (Mobile Edge Computing, MEC) and “fog computing” (fog computing), which moves organizations' network perimeter even further. And, unfortunately, in the market race, the security of many new devices, products and solutions is often overlooked or, at best, late.
IoT has also become a powerful data generator. Gartner predicts that by 2020 IoT will include 26 billion units, and the income of manufacturers of IoT components and service providers will reach $ 300 billion, mainly due to the services provided.
But in order for IoT to become truly successful, users will have to use open standards that regulate data access, security monitoring and runtime analytics.
Digital Wars
The attacker uses increasingly sophisticated methods to overcome the protection of enterprises. The main “weapon” in the arsenal of modern intruders includes the following.
Advanced persistent threat (APT) . A deliberate, well-focused attack that may remain undetected for several years. This requires a large criminal organization, with extensive resources, including money, people, time and modern tools (electronic tracking equipment and satellite systems). In addition to stealing data, APT can be used to progressively destroy physical assets (such as integrated circuits and even nuclear centrifuges).
Botnet . It is a network of infected endpoints (for example, client devices) that work together and are managed by the attacker through command center servers (command-and-control, C2 servers).
Distributed denial of service (DDoS) . A coordinated attack, often from hundreds of thousands or millions of endpoints, used to flood a target system or network with excessive traffic so as to obstruct the processing of legitimate traffic.
Exploit . Exploit (English exploit, exploit) - a computer program, a piece of software code or a sequence of commands that exploit vulnerabilities in a software or application. It is used to conduct an attack on a computing system. Causes their unpredictable behavior or intercepts control in remote mode.
Stolen IP ranges (Hijacked IP address ranges) . Captured ranges, as a rule, damage the routing tables of Internet routers. After that, they are used for phishing and distribution of malware.
Malware . Malicious software or code (malicious software), which, as a rule, damages, disables, takes control or steals information from a computer system. The generic term “malware” includes adware, anti-AV software, backdoors, bootkits, logic bombs, RATs, rootkits, spyware, trojan horses, viruses and worms. The most advanced malware uses metamorphism and polymorphism to avoid detection with signature analyzers.
Phishing . It is used, as a rule, in social networks and e-mail. Replaces the original data in the message. Clicking the link downloads malware or exploit. The browser is redirected to the attacker's website in order to obtain the user's personal information, for example, information about his accounts. In other cases, is used to download malware.
New generation tools
The introduction of next-generation firewalls (next-generation firewalls, NGFW) or intrusion prevention systems (IPS) implies a visibility architecture that can improve security systems.
Geographical expansion of a network or data center leads to problems of visibility in new network segments. Good results are obtained by using “tapa” (test access port, tap) - an external hardware device that is connected to a specific point in the network in order to monitor traffic in the network segment. Tapas have several advantages for achieving network visibility, monitoring work and network security. Tapes work at line speed, do not introduce delay, do not change the content or structure of data.
Requirements for standards compliance and network auditing are becoming more common for organizations in virtually every industry. Many of these requirements are related to ensuring the visibility of data in the corporate network.
Ixia, a leading provider of visibility and security solutions for networks, announced in September 2017 that it will further expand its visibility platform in the cloud, the CloudLens Visibility Platform. It adds support for Microsoft Azure, the Google Cloud Platform, IBM Bluemix and Alibaba Cloud, in addition to existing support for Amazon Web Services (AWS), for both Windows and Linux.
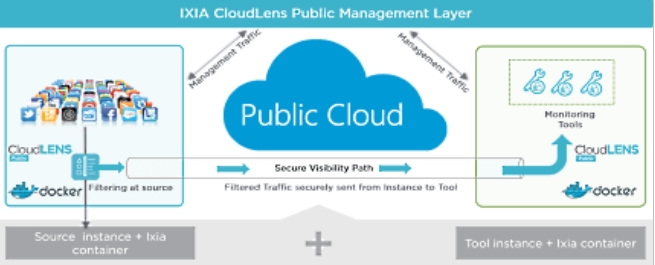
As a result, Ixia CloudLens is now the first visibility solution that supports all leading cloud platforms with different operating systems. The IT infrastructure is transformed into a combination of separately hosted applications and cloud services on several cloud platforms.
In modern corporate solutions, data is often exchanged between local (on-premises) applications in private data centers and applications running in numerous public clouds. Full visibility of the processes taking place in such a hybrid environment is a long-standing problem.
Blind spots on the network, regardless of the cloud service provider, create a lack of granular access to cloud traffic. This can jeopardize network performance or security, which in turn leads to a deterioration in customer service and increases the risk of network security breaches.
Ixia CloudLens provides full visibility in the cloud, supports any type of cloud (public, private and hybrid) and is the industry's first pure software (Software-as-a-Service, SaaS) solution.
CloudLens was designed from scratch to preserve all the benefits of the cloud - simple scaling, flexibility and performance, while allowing security and analytics to obtain the necessary data regardless of where the tool is deployed - in a local data center, at the client’s site or in a public cloud.
Both hybrid and multi-cloud environments pose problems for security services who need to manage multiple network segments. They have no visibility of traffic to secure the network. Ixia CloudLens solves this problem with an agnostic cloud platform that supports AWS, Azure, IBM, and others on Windows and Linux. This flexibility allows CloudLens to provide data access to the package level, along with simple central platform management. CloudLens Public allows customers to:
- Easily deploy and manage any type of cloud environment — public, private or hybrid.
- Use Windows or Linux on any platform.
- Ensure the work of tools and applications working in a public cloud environment, supporting fast elastic scaling.
- Optimize security and provide advanced analytics.
CloudLens software is built on the serverless basis, based on microservices. This allows it to function easily in any public cloud. This software can be installed by the client independently, without involving representatives of the cloud provider.
CloudLens works without network restrictions and does not rely on the hypervisor or specific application software of the cloud provider in public and private clouds, for virtual and physical networks.
CloudLens integrates well with other tools, including open source. Ixia technology partners include AppNeta, The Bro Project, CA Technologies, Dynatrace, Eastwind Networks, FireEye, Jask, LogRhythm, NetFort Technologies, NTOP, ProtectWise, Perch Security, RSA Security, Savvius, Sinefa, Suricata, Wireshark and VoIPmonitor.
To conclude, let us mention the words of Bethany Mayer, President of Ixia, and Vice President of Keysight, under whose wing Ixia Solutions Group is working today.
“Ixia understands that IT decision makers must deploy and manage hybrid networks. They operate in a business environment where application performance is crucial for generating revenue and maintaining customer relationships.
That is why we developed CloudLens - the only cloud-based platform for visibility today that eliminates blind spots everywhere - from the cloud to the physical environment. This allows our clients to increase the effectiveness of monitoring tools, provide better analytics, and, ultimately, reduce downtime when solving responsible tasks. ”

It is difficult to refute the fact that it is impossible to control what is impossible to see. Evaluating incoming / outgoing corporate network traffic is the best defense against attacks and errors that can lead to network disruption, loss of important data, and further to customer dissatisfaction, and this is a direct loss of money.
Therefore, CIOs and “security guards” of enterprises should firmly understand that buying and deploying an ever-growing array of modern security tools is nothing more than a start.
')
For reliable network security, appropriate solutions must implement all their capabilities. This requires visibility tools that have access to all network traffic and provide accurate real-time data. Requires a flexible visibility architecture that is optimized for continuous network monitoring.
Security Improvement
The network perimeter, once clearly delineated by a firewall between the corporate network and the Internet, is being erased today - as users become increasingly mobile, and organizations are increasingly using cloud solutions. Without a clearly defined perimeter, it becomes difficult (or impossible at all) to identify all traffic flows.
Gartner predicts that by 2018, up to 25% of the corporate data flow will bypass traditional security tools and flow directly between mobile devices and the cloud.
A study of Sandvine in early 2016 showed that almost three-quarters of all Internet traffic is encrypted using SSL technology. Google in the same year called the figure in almost 80% of international traffic. However, attackers also use SSL encryption to hide their traffic and threats.
As a result, IT departments now routinely decrypt inbound and outbound traffic beyond the boundary of the firewall, before sending it to the destination. To some extent, this allows identifying risks and threats, such as breaches of regulatory compliance, data leaks, malware, intrusion attempts, etc.
Network traffic is now mainly composed of structured and unstructured data, which includes voice and video. Its volume often exceeds the processing capacity.
Virtualization has become one of the most "subversive" IT innovations in the modern computing era. Virtualization technology allows IT to use standard low-cost servers. However, traditional monitoring methods are not sufficient to control virtual traffic. Virtualization also brought private, public and hybrid clouds, infrastructure as a service (Infrastructure-as-a-Service, IaaS) and platform as a service (Platform-as-a-Service, PaaS).
Scalability and control over the distribution of resources are the main advantages of both virtualization and cloud technologies. On the other hand, organizations migrate workloads from their local data centers to a public cloud, and it is becoming increasingly difficult to monitor and control data flows, that is, new invisibility zones, “blind zones” are being created.
Verizon's 2016 State of the Market: Enterprise Cloud 2016 study found that more than 40% of companies already use five or more cloud providers. The Okta "2016 Business @ Work" study found that companies in most cases use from 10 to 16 applications running in the public cloud.
Indeed, the cloud offers unprecedented IT infrastructure flexibility, but it also forces companies to expand their traditional network perimeter — often to places where they have no visibility or control. These blind spots can quickly become shelters for security threats lurking in the shadows.
The first users of SaaS were mostly small and medium-sized businesses (SMB). Now that SaaS solutions are becoming more complex and functional, they are also used by larger enterprises, including distributed ones. Accordingly, the growing use of cloud applications makes them a target for cyber attacks. Cisco's 2015-2020 Visual Networking Index predicts that by 2019, cloud applications will provide up to 90% of global mobile traffic.
Finally, the “Internet of Things” trend (Internet of Thing, IoT) has created a new market for billions of “smart connections” of devices and products — from surveillance cameras and “smart thermostats” to cars — that are connected to the Internet, collect, store, transmit and share a huge amount of information.
For them, new computational models appear, such as mobile access computing (Mobile Edge Computing, MEC) and “fog computing” (fog computing), which moves organizations' network perimeter even further. And, unfortunately, in the market race, the security of many new devices, products and solutions is often overlooked or, at best, late.
IoT has also become a powerful data generator. Gartner predicts that by 2020 IoT will include 26 billion units, and the income of manufacturers of IoT components and service providers will reach $ 300 billion, mainly due to the services provided.
But in order for IoT to become truly successful, users will have to use open standards that regulate data access, security monitoring and runtime analytics.
Digital Wars
The attacker uses increasingly sophisticated methods to overcome the protection of enterprises. The main “weapon” in the arsenal of modern intruders includes the following.
Advanced persistent threat (APT) . A deliberate, well-focused attack that may remain undetected for several years. This requires a large criminal organization, with extensive resources, including money, people, time and modern tools (electronic tracking equipment and satellite systems). In addition to stealing data, APT can be used to progressively destroy physical assets (such as integrated circuits and even nuclear centrifuges).
Botnet . It is a network of infected endpoints (for example, client devices) that work together and are managed by the attacker through command center servers (command-and-control, C2 servers).
Distributed denial of service (DDoS) . A coordinated attack, often from hundreds of thousands or millions of endpoints, used to flood a target system or network with excessive traffic so as to obstruct the processing of legitimate traffic.
Exploit . Exploit (English exploit, exploit) - a computer program, a piece of software code or a sequence of commands that exploit vulnerabilities in a software or application. It is used to conduct an attack on a computing system. Causes their unpredictable behavior or intercepts control in remote mode.
Stolen IP ranges (Hijacked IP address ranges) . Captured ranges, as a rule, damage the routing tables of Internet routers. After that, they are used for phishing and distribution of malware.
Malware . Malicious software or code (malicious software), which, as a rule, damages, disables, takes control or steals information from a computer system. The generic term “malware” includes adware, anti-AV software, backdoors, bootkits, logic bombs, RATs, rootkits, spyware, trojan horses, viruses and worms. The most advanced malware uses metamorphism and polymorphism to avoid detection with signature analyzers.
Phishing . It is used, as a rule, in social networks and e-mail. Replaces the original data in the message. Clicking the link downloads malware or exploit. The browser is redirected to the attacker's website in order to obtain the user's personal information, for example, information about his accounts. In other cases, is used to download malware.
New generation tools
The introduction of next-generation firewalls (next-generation firewalls, NGFW) or intrusion prevention systems (IPS) implies a visibility architecture that can improve security systems.
Geographical expansion of a network or data center leads to problems of visibility in new network segments. Good results are obtained by using “tapa” (test access port, tap) - an external hardware device that is connected to a specific point in the network in order to monitor traffic in the network segment. Tapas have several advantages for achieving network visibility, monitoring work and network security. Tapes work at line speed, do not introduce delay, do not change the content or structure of data.
Requirements for standards compliance and network auditing are becoming more common for organizations in virtually every industry. Many of these requirements are related to ensuring the visibility of data in the corporate network.
Ixia, a leading provider of visibility and security solutions for networks, announced in September 2017 that it will further expand its visibility platform in the cloud, the CloudLens Visibility Platform. It adds support for Microsoft Azure, the Google Cloud Platform, IBM Bluemix and Alibaba Cloud, in addition to existing support for Amazon Web Services (AWS), for both Windows and Linux.

As a result, Ixia CloudLens is now the first visibility solution that supports all leading cloud platforms with different operating systems. The IT infrastructure is transformed into a combination of separately hosted applications and cloud services on several cloud platforms.
In modern corporate solutions, data is often exchanged between local (on-premises) applications in private data centers and applications running in numerous public clouds. Full visibility of the processes taking place in such a hybrid environment is a long-standing problem.
Blind spots on the network, regardless of the cloud service provider, create a lack of granular access to cloud traffic. This can jeopardize network performance or security, which in turn leads to a deterioration in customer service and increases the risk of network security breaches.
Ixia CloudLens provides full visibility in the cloud, supports any type of cloud (public, private and hybrid) and is the industry's first pure software (Software-as-a-Service, SaaS) solution.
CloudLens was designed from scratch to preserve all the benefits of the cloud - simple scaling, flexibility and performance, while allowing security and analytics to obtain the necessary data regardless of where the tool is deployed - in a local data center, at the client’s site or in a public cloud.
Both hybrid and multi-cloud environments pose problems for security services who need to manage multiple network segments. They have no visibility of traffic to secure the network. Ixia CloudLens solves this problem with an agnostic cloud platform that supports AWS, Azure, IBM, and others on Windows and Linux. This flexibility allows CloudLens to provide data access to the package level, along with simple central platform management. CloudLens Public allows customers to:
- Easily deploy and manage any type of cloud environment — public, private or hybrid.
- Use Windows or Linux on any platform.
- Ensure the work of tools and applications working in a public cloud environment, supporting fast elastic scaling.
- Optimize security and provide advanced analytics.
CloudLens software is built on the serverless basis, based on microservices. This allows it to function easily in any public cloud. This software can be installed by the client independently, without involving representatives of the cloud provider.
CloudLens works without network restrictions and does not rely on the hypervisor or specific application software of the cloud provider in public and private clouds, for virtual and physical networks.
CloudLens integrates well with other tools, including open source. Ixia technology partners include AppNeta, The Bro Project, CA Technologies, Dynatrace, Eastwind Networks, FireEye, Jask, LogRhythm, NetFort Technologies, NTOP, ProtectWise, Perch Security, RSA Security, Savvius, Sinefa, Suricata, Wireshark and VoIPmonitor.
To conclude, let us mention the words of Bethany Mayer, President of Ixia, and Vice President of Keysight, under whose wing Ixia Solutions Group is working today.
“Ixia understands that IT decision makers must deploy and manage hybrid networks. They operate in a business environment where application performance is crucial for generating revenue and maintaining customer relationships.
That is why we developed CloudLens - the only cloud-based platform for visibility today that eliminates blind spots everywhere - from the cloud to the physical environment. This allows our clients to increase the effectiveness of monitoring tools, provide better analytics, and, ultimately, reduce downtime when solving responsible tasks. ”
Source: https://habr.com/ru/post/341492/
All Articles