Bitcoin hardware wallets

We continue to deal with various wallets for cryptocurrency. Last time I rummaged a bit in software wallets, but today I’ll tell you a little about hardware. At the beginning of a small reminder.
By wallets in cryptocurrencies understand simultaneously:
- a set of keys to access money;
- programs that control these keys and allow you to conduct transactions on a cryptocurrency network.
In order not to be confused when we talk about keying, I will use the term "private key". Although we all understand that in a key pair there is also an open one, as well as the fact that there can be several pairs.
')
We will talk about the wallet exactly as a means of managing, storing and conducting transactions. Without a wallet, you cannot receive, save or spend your bitcoins or funds in another cryptocurrency. Wallet - your personal interface to the cryptocurrency network, similar to a bank account for fiat currency.
So, hardware wallets. Let's start with the definition. Hardware wallets are physical devices created for the safe storage of cryptocurrency. Some software and online wallets support the storage of funds on hardware wallets.
Before proceeding to a comparison of specific models of hardware wallets, let's see what most of these wallets can do, and we’ll dwell more on the features of each of them.
Spherical hardware wallet
So, any hardware wallet (of those considered):
- It generates and stores the non-recoverable private key of the wallet inside the device.
- All transactions required to complete a transaction are performed inside the device. From the device is issued only the result - the electronic signature of the transaction.
- Has a screen to display various information.
- It has one or more physical buttons to interact with the device.
- When transferring funds from the wallet displays information about the transaction.
- Requires manual confirmation of operations using the physical button on the device.
- Allows you to create a backup copy of the keys in case the device breaks or is lost.
- Requires the installation of additional software from the hardware wallet manufacturer.
- Supported on all modern versions of Windows, Linux, MacOS.
- Supported on Android.
- It does not allow installing any additional software inside the wallet itself.
- To work requires knowledge of a special PIN-code (or even several PIN-codes).
- Worth the money, unlike most other wallets.
- Not all possible cryptocurrencies support, but only the most popular ones.
The main differences
A little more detail on the threats that protect you from the use of hardware wallets, unlike other types of wallets.
From online wallets
Since, in the case of online wallets, your private keys are stored on remote servers, you inevitably put yourself at risk of losing money in the following situations:
- The computer was hacked, which led to the theft of a password from an online-wallet.
- The server on which the online wallet was deployed was hacked and the funds of all users of the wallet were stolen.
- The web wallet company went bankrupt.
- The FBI confiscated the servers, and ultimately the users' funds.
- The owners of the online wallet developer company stole user funds and escaped.
- A program error in the online wallet code led to a loss of funds.
- The attacker stole a mobile phone, which opened a session to work with online wallet, which led to loss of funds.
From software wallets to computer
Hacking or infecting your computer with a virus will steal your wallet's private key.
The computer has a 1000 times greater attack surface than a hardware wallet.
From mobile wallets to smartphone
These wallets for smartphones can be divided into 2 groups:
- Interfaces to online-wallets. In this case, they are subject to the same risks that online wallets are exposed to (see above).
- Full mobile apps. In this case, the situation is very similar to software wallets on the computer. The widespread proliferation of smartphones and tablets has led to the rapid development of viruses for these devices. So your funds are no longer safe.
From USB stick
Obviously, flash drives were never created as a security tool, but not everyone understands this.
- Any software can read or copy private keys from a flash drive.
- Malicious software can replace the recipient's address in a transaction.
- Theft or loss of such a flash drive can lead to complete loss of funds.
By the way, it can be protected from theft or loss if you use special flash drives that require entering a PIN code to gain access to the data.
From an encrypted wallet
Even if you use a complex password to encrypt your wallet, you cannot protect private keys from being compromised. Virus software will simply try to get your password, and using the password you will get access to the wallet. Or just wait until you enter your password and unlock access to private keys. Not to mention the possibility of simply copying the wallet file and then sorting through the code phrase in the dictionaries.
From storing keys on paper
In fact, proper storage of a private key on a piece of paper is fairly safe. That's just very uncomfortable. Plus, to work with such a wallet, you still have to enter your private key into one of the above wallets. And after that sleep in peace will not work.
The risks and potential vulnerabilities of hardware wallets
To date, there has not been a single confirmed case of theft of a cryptocurrency from a hardware wallet. Despite the fact that they appeared not so long ago, they have already proven themselves well.
However, it should be understood that hardware wallets are not a silver bullet to protect your cryptocurrency funds. There are several security risks to which all or some of the wallets are exposed. These risks need to be taken into account when you decide which hardware wallet to purchase and how much cryptocurrency can be stored on it.
- Substitution of the recipient's address in the transaction. A hardware wallet will not protect you from sending your cryptocurrency to a fake address. For example, malware on your computer can monitor transactions with a large number of cryptocurrency, and then replace the recipient's address with the address of the wallet that belongs to the attacker. If the rates are high, then you need to use multi-factor confirmation of the recipient's address - for example, by phone.
- Bad scrappy. Hardware wallets rely on the security of the DSCH, which is inside the device and is used to securely generate your private key. Unfortunately, checking the key for randomness is not the easiest task. A vulnerable RNG can create such wallet keys that can be recreated by an attacker, generating a pseudo-random number that looks like a random number.
- Implementation errors The security of all computer systems, both software and hardware, is based on the quality of their implementation. Hardware wallets are no exception. Errors in software, firmware or at the hardware level can allow an attacker to gain access to the internal structures of the hardware wallet, and then to your secrets. Even if the device was originally designed correctly, it is very difficult to prove the safety of the implementation in a particular device.
- Compromised production process. Even the ideal software and hardware implementation is vulnerable to intentional or unintentional introduction into the production process. Various bookmarks can be embedded in the device, both randomly and under pressure from various special services.
- Compromised delivery process. It is even easier to integrate into the delivery process and remove or modify a part of the protection device in such a way that it is invisible to the user. It is known that various government programs include intercepting and modifying various hardware with the aim of introducing backdoors.
Summarize
Despite the fact that hardware wallets will not protect you from all possible threats, choosing a hardware wallet from a trusted, technically competent manufacturer with a good reputation will allow you to protect yourself from much more threats than using software wallets.
An ideal solution for long-term storage can be a solution based on open source software that uses a common hardware platform (for example, raspberry pi), as well as the use of a trusted source of entropy (such as a regular cube).
However, hardware wallets manufacturers know about these risks and potential vulnerabilities and are trying to propose various solutions. I decided to make a small review of the most popular and interesting hardware wallets, so that you yourself could draw conclusions about their security.
Trezor
The device was introduced in 2014.

So, what Trezor can offer us:
- Currently supports Bitcoin, Ethereum (+ all ERC-20 tokens), Ethereum Classic, ZCash, Litecoin, Namecoin, Dogecoin, Dash and Bitcoin Testnet.
- When the device is manufactured, after its packaging, the box into which it is placed is glued with a holographic safety tape. Its presence confirms that the device is original. And also partially protects you from opening and changing or modifying the device during its delivery.
- Also offers the Password Manager for the browser (no master passwords - each password is encrypted on its key, to enter, simply press a button on the device, if you lose the device, your passwords are not lost, it works through the browser extension mechanism).
- Supports U2F (Universal Second Factor).
- SSH / GPG agent.
- It is supported by a large list of software wallets and online services (a full list can be found here - https://doc.satoshilabs.com/trezor-apps/index.html ).
- Each time you connect your device to a computer or mobile device, you need to enter a PIN. After that, the device enters the unlocked state and allows you to perform operations. After shutdown, the device goes back to the locked state.
The PIN input mechanism itself is quite original. In order not to describe, just give the video:
What is nice, the manufacturer gives you very reasonable recommendations for the safe storage of this password phrase.
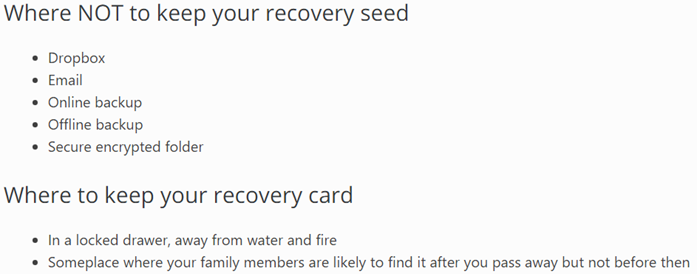
Issue price - $ 99
The main disadvantage is that it supports less cryptocurrency than ledger.
Ledger nano s

- Supports Ark, Bitcoin, Bitcoin Cash, Dash, Dogecoin, Ethereum, Ethereum Classic, Komodo, Litecoin, PoSW, Ripple, Stratis, Zcash, and all ERC20 tokens.
- Supports U2F, GPG and SSH.
- Uses 2 microcontrollers inside: ST31H320 (protected) + STM32F042.
I will attach here also a video showing PIN input. In my opinion, not the most convenient way. It is especially hard to enter words like this to restore the backup of the wallet.
Issue price - 58.00 €
The main drawback is the quality of the manufacture of the device itself. The left button sometimes perceives a single press as a double.
KEEPKEY

- Supports Bitcoin, Litecoin, Dogecoin, Namecoin, Testnet, Ethereum, and Dash.
- The main feature is a 3.12 ″ OLED display with a resolution of 256 × 64.
- Inside is used STM32F205RGT6.
- This is the only hardware wallet in question that allows you to use your firmware. For security reasons, when using third-party firmware, the device displays a warning when it is turned on.
- Complies with FIPS PUB 140-2 and FIPS PUB 180-2.
- As well as Trezor comes in a special package that can not be opened without being noticed.
The PIN input mechanism is the same as in Trezor, so there will be no separate video.
The price of the issue is $ 129.00 . More than the competition, but the screen is really good.
Bitlox

If previous wallets were more like classic tokens or devices of the TrustScreen class, then this one emulates smart cards.
- Supports Bitcoin and more recently Ethereum.
- Contains inside a battery that charges on Micro USB.
- It communicates via Bluetooth LE.
- Only 4 mm in thickness.
- Display eink - 2 ".
- It supports multiple PIN codes: to connect the device, to work with wallets, to conduct a transaction.
- The random number sensor has been certified by NIST.
- It also has a special PIN, which will lead to a complete cleaning of the device.
- It has services for work via TOR (BITLOX2twvzwbzpk.onion) or I2P (BITLOX.i2p).
A distinctive feature of this hardware wallet is a “vigorous” website. As well as the explicit positioning is not so much on the protection of funds, as on privacy and use in Darknet.
The price of the issue is $ 98.00 .
digitalbitbox

Another interesting device. Although it does not have a screen for displaying transaction information, I decided to include it in my mini-review. Already very non-standard idea.
- Supports Bitcoin (BTC) and Ethereum (ETH, ETC, and ERC20 tokens). The developers claim that they are working on expanding this list.
- Supports U2F.
- You can at any time extract or backup a microSD card.
- Supports work with Tor and Tails OS.
- Private keys are stored on a secure chip that is protected from physical data extraction.
- Simple design does not cause additional attention.
- Payment verification and two-factor authentication on a mobile application.
- Does not require the display or input of words on the screen to restore access to the wallet. You simply insert the backup microSD.
- All USB communication is encrypted using AES-256-CBC.
- One button to work with the device.
Breaking into
Not to mention the hacking history of hardware wallets. Josh Datko and Chris Quartier at the DEF CON conference gave a presentation on which they shared their tools and methods that allow hacking into some hardware wallets for cryptocurrency.
Demonstrated the application of these techniques to the microcontroller STM32F205, which was used in devices from Trezor and Keepkey.

The presentation was based on a study performed by Jochen Hoenicke in 2015, which resulted in a private key being compromised in a Trezor device using an oscilloscope worth $ 70. Vulnerability was closed by the manufacturer. This, however, does not exclude the possibility of the emergence of new similar attacks both to the indicated devices and to devices from other manufacturers.
Let's sum up
Hardware wallets will not protect your funds from all possible threats, but their proper use will in most cases protect your funds in cryptocurrency, unless, of course, you have them :) At least they are many times more reliable than software wallets. There are already many models on the market, so there is plenty to choose from, including for the price. Although delivery to Russia still have a little tricky.
Source: https://habr.com/ru/post/341456/
All Articles