Evolution of malicious extensions: from amateur handicrafts to steganography. Experience team Yandex. Browser
Extensions are a great tool for adding new features to the browser. And with their help they secretly embed advertising, steal data, send spam and even mine-cryptocurrencies. Today we will share with you our experience in dealing with such extensions, you will learn about the main distribution channels of dubious developments and how to disguise the malicious entity from moderators and scanners.

Yandex.Browser initially supported the installation of extensions for Chromium, but at first the earning industry on add-ons was still in its infancy, so there were no special problems. Malicious samples, of course, met: we either found them ourselves, or found out about them from support calls. The unique identifiers (IDs) of such developments were blacklisted on the server, which Yandex.Browser accessed via the API and blocked the installation of potentially dangerous extensions. And the extensions themselves were very rarely camouflaged: all their capabilities were almost always explicitly described in HTML and JS without trying to hide something. But then everything changed.
')
The rapid growth of popularity of Chromium and the ability to automatically install any extensions without confirmation from the user played a cruel joke. Developers of dangerous add-ons did not need to even publish to the Web Store and promote their creation there. It was enough to disguise the extension for a useful utility, a popular game or a new film that had not even reached the cinema. The users themselves found, downloaded and launched exe-files that threw crx-extensions into the browser profile. How do we know about this? Very simple: about a third of the appeals in support began to contain complaints about low-quality and shocking advertisements that floated on top of their favorite sites in the Browser.
Something like this for some users started to look like YouTube. This is a fresh screenshot, but over the years the symptoms have changed little. Count how many foreign ad units are there:
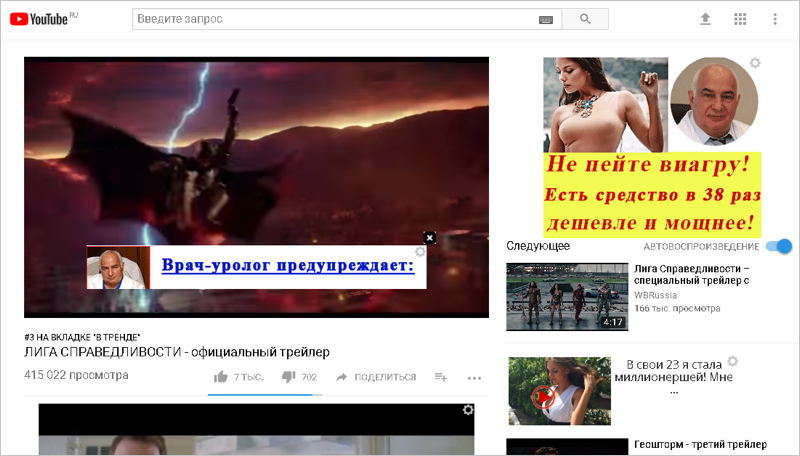
Most of the affected users did not know anything about any extensions, blamed us and deleted Yandex.Browser. Quiet time is over.
From blacklist to hashing
Soon enough, we found an opportunity to slow down the growth of the threat. First of all, they turned off support for those documented Chromium mechanisms that simplified the work for developers of bad extensions. In the usual version of the Browser, we restricted the ability to install extensions through the registry key and forbade the use of corporate policies , which, by the way, were especially popular with Malvari developers, because they did not allow users to delete extensions.

We also created a “headquarters” to combat the new threat, which in real-time received information about extensions distributed among Browser users, could quickly check suspicious ones and block them by ID. And for a while this solved the problem.
Lovers of easy money, who lost convenient installation methods and time advantages, tensed and struck back. In the Windows operating system, any application can interfere with the operation of any other application, which they started using against Yandex Browser. Doubtful programs have learned to throw extensions directly into the browser profile folder, making changes to the settings files. But this is not the most interesting.
The cunning ones understood that we learned about such extensions very quickly, so we found a simple but effective way to prevent blocking by ID. They just started using the same ID as the popular extensions. For example, we could not disable a bad extension with the identifier pioclpoplcdbaefihamjohnefbikjilc, because then a good Evernote Web Clipper would stop working. Cleverly. As a result, we beat off this blow, but at what cost.
The solution was found in comparing the hash of the installed extension with the hash of the original Stora extension. If they do not match, then overwrite the folder with a safe copy. The problem is that the method worked only for those supplements that were published in Store. All the others simply have nothing to compare. Therefore, in 2014 we allowed to install extensions only from trusted sources, which included the Web Store, Opera Addons and our own catalog. With this decision we managed to drive the majority of malicious extensions into Stores, where, as we hoped, the harsh rules and moderation would bring their numbers to a historic minimum. But we were wrong.
5 dollars. That is how much it costs to have a developer account in the Web Store catalog. But professionals on the other side of the barricades are ready to spend money on the generation of accounts and clones of dubious extensions. And then they can only find the source of users. And there are several such methods.
Mimicry
You can copy the name, design and even code from a popular extension to get into the search results in the Web Store. Unfortunately, this method flourishes due to the lack of pre-moderation in the directory. For example, recently there was a case with a fake AdBlock Plus, which installed 37 thousand users. By the time this tweet appeared on Twitter, it was already blocked in our Browser. And not only that. The media wrote about one case, but in reality there were about 10 copies of a fake ad blocker. They behaved relatively modestly: they allegedly did not steal anything, but suddenly opened tabs with advertising. For example, the tab with the address settingsbrowser.online, which redirects to the advertised services and applications.

Distribution via third-party programs
You take a popular utility and repack it so that the installer not only installs the utility itself, but also throws your extension into the profile folder. Then you create a fake official website, which users get through spam. Although now few people are so bother. It is much easier to use one of the affiliate programs, to which the developers of free applications for monetization are connected. Usually this method is easily recognized by the speed of distribution of the add-on among users of the browser.
There is another way to understand that we have disabled the useless extension with malicious features - neither users nor developers almost do not come to us with complaints. Some, however, try to cheat and add an exception to the code for Yandex. Browser. It works like this. If the user has Yandex Browser, then he receives no bad surprises, unlike Google Chrome users. It would seem that this is a problem of other Chromium based browsers, but no. We consider this behavior a hoax and do not remove blocking.
Inline installation
Any site has the ability to distribute its official extension, published in the Chrome Web Store. Just click on the button in the pop-up panel, and the add-on will be in the browser. It remains only to persuade the person to click. For example, a site can go to full-screen mode and simulate a browser lock, which can only be removed using an extension (a live example ).

Or consider another real-life example, which our colleagues talked about last year at Botconf 2016 , but the epidemic continues to this day (these are dozens of clones blocked by us).
Facebook user receives a personal message from his friend, which contains a link to the video.

After clicking on the link, a page opens ( example , another example ), created on the basis of an authoritative free file storage service, where instead of a video is a regular screenshot.
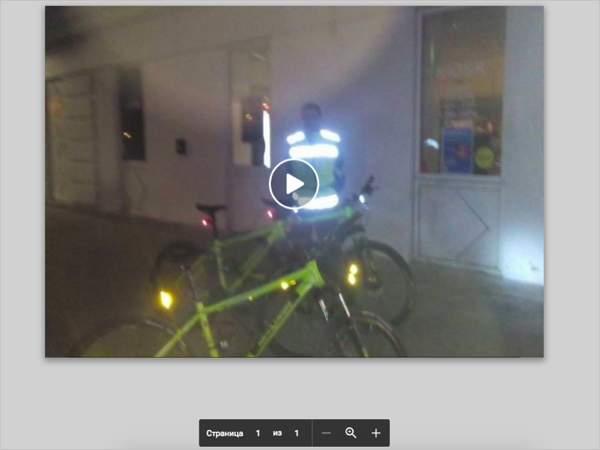
This is a layer between spam on Facebook and those sites where extensions are “offered” or other ads are posted. It is needed for the following reasons. Firstly, social networks and antiviruses do not block all addresses on authoritative domains using a mask. Secondly, generating pages on free services is easier and faster than registering a new site and linking it to an extension. Thirdly, such links look safe, and users are more likely to click on them.
The user clicks on the fake screenshot and gets on the site , which simulates the appearance of YouTube and is based on the service for blogs. Any attempt to start the video will be prompted to install the extension.
An important clarification: right now the page on docs.google.com can redirect not to the specified site, but to another advertisement, because the extension has just been blocked in the catalog, and the author needs to spend time creating a new site-extension bundle. We have already disabled more than 50 extensions from this family, but they continue to appear.
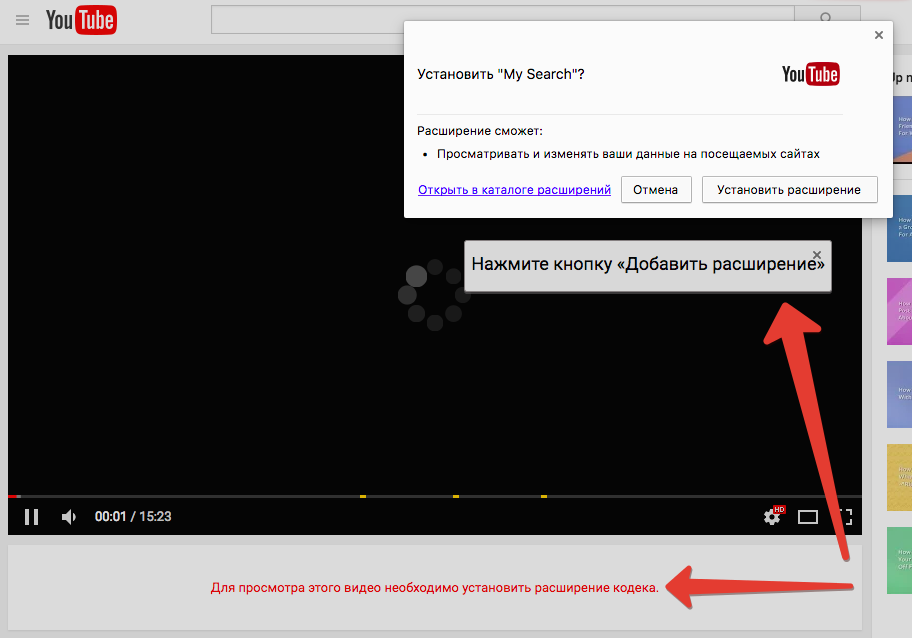
If a person agrees, now he will, against his will, become a source of spam on Facebook.
Moreover, extensions from this family are able to protect themselves. Pay attention to the review:
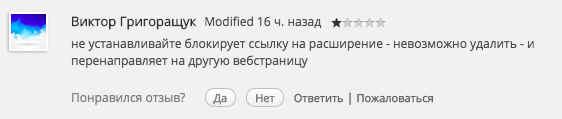
It says that the extension does not allow you to open the chrome: // extensions service page in Chromium (immediately closes it). Using this page is usually recommended to check the list of extensions and remove suspicious. At one time, we also encountered this trick, so in the Yandex Browser the browser: // tune page is isolated from extensions.
Partnership programs
You can not bother with the creation of their extensions, pages and spam, but simply buy a ready-made popular extension and roll out a new version with a surprise (users will not find out about the sale or the release of the new version). Or even create an affiliate program for developers who, in exchange for money, will add your script to their extensions. On average, in the hospital, partners earn 100 rubles per day for every 1500 users. Finding affiliate programs is not difficult. By the way, it is very pleasant to read similar comments on the forums of such programs. No wonder we are working;)

The owners of the affiliate program are ready not only to give their library, but also to create a ready-made extension. The partner will only be required to publish and find traffic.
As you understand, I want to discourage any investment of funds, so the developers of questionable scripts work not only on quantity, but also on “quality”, where by the latter we mean the ability to hide our essence from moderators and automated scanners. The harder it is to find evidence, the longer the expansion will work and the more money it will bring. And in this area for several years there was a significant jump.
From concatenation to steganography
It all started with a primitive concatenation, when a deliberately dangerous code was broken into separate letter fragments. Approximately as in the screenshot. It was naive, but the first inventors might have helped.

We should also say about obfuscation. There is a myth that obfuscation can disguise any logic, but it works exactly the opposite. In reality, this is the most inept way to disguise, because it attracts almost everyone’s attention: antiviruses swear at it, users get scared, moderators check such extensions first. Want to get you out of Stora as quickly as possible? Use code obfuscation.
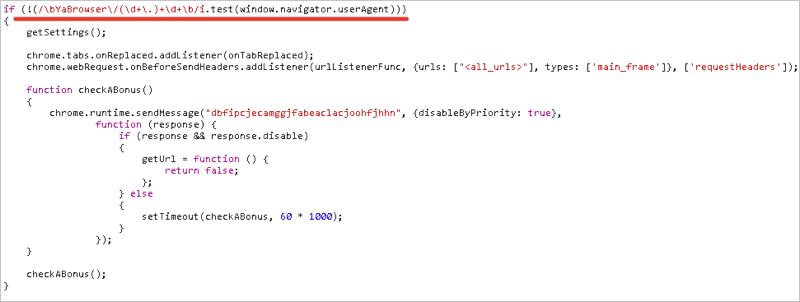
Far smarter are those who maintain the visibility of a decent code, but carry its malicious parts across different modules, confuse the tracks, communicate with themselves using localStorage. Some parts can even be loaded from an external server. And not for all countries (to attract the attention of moderators somewhere in the USA is easier than in Russia), not for all browsers (again, exceptions for Yandex Browser, as in the example above), not in the first days of the extension (to make it harder manual check).
In April of this year, among the developers of dubious extensions, a new fashion began to emerge. Take a look at this picture:

Noticed anything unusual except compression artifacts? And now let's look through the debugger on the work of the extension that contains this image:

The extension extracts part of the code from the image. This technique is called "steganography", and it is well known for viruses for Windows, but it only reached extensions in the spring. Now this method is combined with all the above, and it is found in dozens of extensions ( 71 thousand users , 11 thousand users ). According to our assessment, all these extensions use a script from one author, or rather from one affiliate program, which we are now closely watching. Of course, we catch and disable these extensions, because we do not rely only on our eyes and hands.
Machine learning
We managed to establish a semi-automatic process to identify questionable extensions and disable them. It works approximately as follows. As soon as any new extension appears, and it is started to be installed in the Yandex Browser, the analysis process starts on our servers. We use machines that are constantly trained in already known bad samples to assess the degree of danger of new ones. Explicit abuses are blocked automatically. Questionable pass through manual control.
We have learned how to catch not only those projects that steal passwords, redirect to phishing pages or secretly change / add their advertising to the pages. We also do not miss extensions, secretly replacing links on pages (including for earnings on affiliate programs) and unexpectedly opening tabs with advertised sites. We do not approve of the extraction of cryptocurrency, if the user has not given his explicit consent. We prohibit imitating clicks and other user actions (for example, to cheat likes or send spam on social networks).
For obvious reasons, we cannot disclose the details of the work of our scanners and the factors used in machine learning (we say hello to talented developers of dubious scripts). We can only say that thanks to this process, most malicious add-ons are disabled in the Yandex Browser 1-3 days after the start of their life. This is more than a hundred unique extensions per month and tens of thousands of protected users.
What's next?
No matter how surprising it may have sounded, but it is in RuNet that new methods of cheating users and browsers are being introduced, which are then “exported” further. Now we are opposed not by amateurs, but by a whole industry of creators and distributors of dangerous extensions, who sooner or later will find another way to surprise us. We believe that we will find something to answer them, but there is no perfect protection, therefore, there will always be malicious extensions that we have not disabled yet. And here the help of the whole community will be useful. If you come across such developments, you can safely send information to our team (both through support and in a personal on Habré). We will also be grateful for any ideas and information that will help protect users from unpleasant surprises.

Yandex.Browser initially supported the installation of extensions for Chromium, but at first the earning industry on add-ons was still in its infancy, so there were no special problems. Malicious samples, of course, met: we either found them ourselves, or found out about them from support calls. The unique identifiers (IDs) of such developments were blacklisted on the server, which Yandex.Browser accessed via the API and blocked the installation of potentially dangerous extensions. And the extensions themselves were very rarely camouflaged: all their capabilities were almost always explicitly described in HTML and JS without trying to hide something. But then everything changed.
')
The rapid growth of popularity of Chromium and the ability to automatically install any extensions without confirmation from the user played a cruel joke. Developers of dangerous add-ons did not need to even publish to the Web Store and promote their creation there. It was enough to disguise the extension for a useful utility, a popular game or a new film that had not even reached the cinema. The users themselves found, downloaded and launched exe-files that threw crx-extensions into the browser profile. How do we know about this? Very simple: about a third of the appeals in support began to contain complaints about low-quality and shocking advertisements that floated on top of their favorite sites in the Browser.
Something like this for some users started to look like YouTube. This is a fresh screenshot, but over the years the symptoms have changed little. Count how many foreign ad units are there:

Other terrible examples
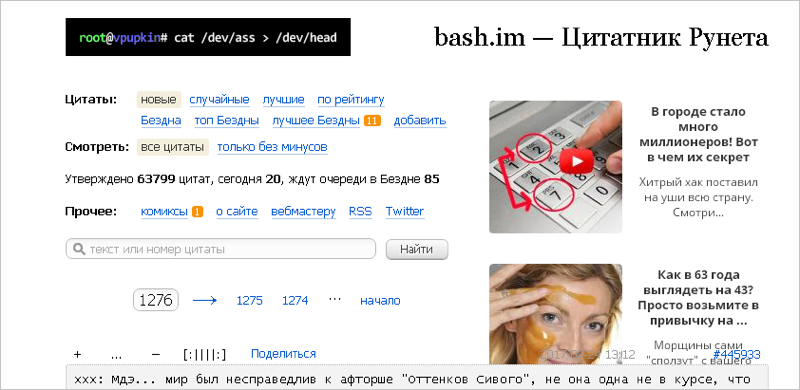


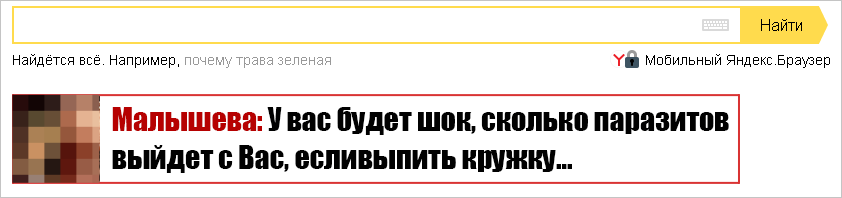





Most of the affected users did not know anything about any extensions, blamed us and deleted Yandex.Browser. Quiet time is over.
From blacklist to hashing
Soon enough, we found an opportunity to slow down the growth of the threat. First of all, they turned off support for those documented Chromium mechanisms that simplified the work for developers of bad extensions. In the usual version of the Browser, we restricted the ability to install extensions through the registry key and forbade the use of corporate policies , which, by the way, were especially popular with Malvari developers, because they did not allow users to delete extensions.

We also created a “headquarters” to combat the new threat, which in real-time received information about extensions distributed among Browser users, could quickly check suspicious ones and block them by ID. And for a while this solved the problem.
Lovers of easy money, who lost convenient installation methods and time advantages, tensed and struck back. In the Windows operating system, any application can interfere with the operation of any other application, which they started using against Yandex Browser. Doubtful programs have learned to throw extensions directly into the browser profile folder, making changes to the settings files. But this is not the most interesting.
The cunning ones understood that we learned about such extensions very quickly, so we found a simple but effective way to prevent blocking by ID. They just started using the same ID as the popular extensions. For example, we could not disable a bad extension with the identifier pioclpoplcdbaefihamjohnefbikjilc, because then a good Evernote Web Clipper would stop working. Cleverly. As a result, we beat off this blow, but at what cost.
The solution was found in comparing the hash of the installed extension with the hash of the original Stora extension. If they do not match, then overwrite the folder with a safe copy. The problem is that the method worked only for those supplements that were published in Store. All the others simply have nothing to compare. Therefore, in 2014 we allowed to install extensions only from trusted sources, which included the Web Store, Opera Addons and our own catalog. With this decision we managed to drive the majority of malicious extensions into Stores, where, as we hoped, the harsh rules and moderation would bring their numbers to a historic minimum. But we were wrong.
5 dollars. That is how much it costs to have a developer account in the Web Store catalog. But professionals on the other side of the barricades are ready to spend money on the generation of accounts and clones of dubious extensions. And then they can only find the source of users. And there are several such methods.
Mimicry
You can copy the name, design and even code from a popular extension to get into the search results in the Web Store. Unfortunately, this method flourishes due to the lack of pre-moderation in the directory. For example, recently there was a case with a fake AdBlock Plus, which installed 37 thousand users. By the time this tweet appeared on Twitter, it was already blocked in our Browser. And not only that. The media wrote about one case, but in reality there were about 10 copies of a fake ad blocker. They behaved relatively modestly: they allegedly did not steal anything, but suddenly opened tabs with advertising. For example, the tab with the address settingsbrowser.online, which redirects to the advertised services and applications.

Distribution via third-party programs
You take a popular utility and repack it so that the installer not only installs the utility itself, but also throws your extension into the profile folder. Then you create a fake official website, which users get through spam. Although now few people are so bother. It is much easier to use one of the affiliate programs, to which the developers of free applications for monetization are connected. Usually this method is easily recognized by the speed of distribution of the add-on among users of the browser.
There is another way to understand that we have disabled the useless extension with malicious features - neither users nor developers almost do not come to us with complaints. Some, however, try to cheat and add an exception to the code for Yandex. Browser. It works like this. If the user has Yandex Browser, then he receives no bad surprises, unlike Google Chrome users. It would seem that this is a problem of other Chromium based browsers, but no. We consider this behavior a hoax and do not remove blocking.

Inline installation
Any site has the ability to distribute its official extension, published in the Chrome Web Store. Just click on the button in the pop-up panel, and the add-on will be in the browser. It remains only to persuade the person to click. For example, a site can go to full-screen mode and simulate a browser lock, which can only be removed using an extension (a live example ).

Or consider another real-life example, which our colleagues talked about last year at Botconf 2016 , but the epidemic continues to this day (these are dozens of clones blocked by us).
Facebook user receives a personal message from his friend, which contains a link to the video.

After clicking on the link, a page opens ( example , another example ), created on the basis of an authoritative free file storage service, where instead of a video is a regular screenshot.

This is a layer between spam on Facebook and those sites where extensions are “offered” or other ads are posted. It is needed for the following reasons. Firstly, social networks and antiviruses do not block all addresses on authoritative domains using a mask. Secondly, generating pages on free services is easier and faster than registering a new site and linking it to an extension. Thirdly, such links look safe, and users are more likely to click on them.
The user clicks on the fake screenshot and gets on the site , which simulates the appearance of YouTube and is based on the service for blogs. Any attempt to start the video will be prompted to install the extension.
An important clarification: right now the page on docs.google.com can redirect not to the specified site, but to another advertisement, because the extension has just been blocked in the catalog, and the author needs to spend time creating a new site-extension bundle. We have already disabled more than 50 extensions from this family, but they continue to appear.

If a person agrees, now he will, against his will, become a source of spam on Facebook.
Moreover, extensions from this family are able to protect themselves. Pay attention to the review:

It says that the extension does not allow you to open the chrome: // extensions service page in Chromium (immediately closes it). Using this page is usually recommended to check the list of extensions and remove suspicious. At one time, we also encountered this trick, so in the Yandex Browser the browser: // tune page is isolated from extensions.
Partnership programs
You can not bother with the creation of their extensions, pages and spam, but simply buy a ready-made popular extension and roll out a new version with a surprise (users will not find out about the sale or the release of the new version). Or even create an affiliate program for developers who, in exchange for money, will add your script to their extensions. On average, in the hospital, partners earn 100 rubles per day for every 1500 users. Finding affiliate programs is not difficult. By the way, it is very pleasant to read similar comments on the forums of such programs. No wonder we are working;)

The owners of the affiliate program are ready not only to give their library, but also to create a ready-made extension. The partner will only be required to publish and find traffic.
As you understand, I want to discourage any investment of funds, so the developers of questionable scripts work not only on quantity, but also on “quality”, where by the latter we mean the ability to hide our essence from moderators and automated scanners. The harder it is to find evidence, the longer the expansion will work and the more money it will bring. And in this area for several years there was a significant jump.
From concatenation to steganography
It all started with a primitive concatenation, when a deliberately dangerous code was broken into separate letter fragments. Approximately as in the screenshot. It was naive, but the first inventors might have helped.

We should also say about obfuscation. There is a myth that obfuscation can disguise any logic, but it works exactly the opposite. In reality, this is the most inept way to disguise, because it attracts almost everyone’s attention: antiviruses swear at it, users get scared, moderators check such extensions first. Want to get you out of Stora as quickly as possible? Use code obfuscation.
Far smarter are those who maintain the visibility of a decent code, but carry its malicious parts across different modules, confuse the tracks, communicate with themselves using localStorage. Some parts can even be loaded from an external server. And not for all countries (to attract the attention of moderators somewhere in the USA is easier than in Russia), not for all browsers (again, exceptions for Yandex Browser, as in the example above), not in the first days of the extension (to make it harder manual check).
In April of this year, among the developers of dubious extensions, a new fashion began to emerge. Take a look at this picture:

Noticed anything unusual except compression artifacts? And now let's look through the debugger on the work of the extension that contains this image:

The extension extracts part of the code from the image. This technique is called "steganography", and it is well known for viruses for Windows, but it only reached extensions in the spring. Now this method is combined with all the above, and it is found in dozens of extensions ( 71 thousand users , 11 thousand users ). According to our assessment, all these extensions use a script from one author, or rather from one affiliate program, which we are now closely watching. Of course, we catch and disable these extensions, because we do not rely only on our eyes and hands.
Machine learning
We managed to establish a semi-automatic process to identify questionable extensions and disable them. It works approximately as follows. As soon as any new extension appears, and it is started to be installed in the Yandex Browser, the analysis process starts on our servers. We use machines that are constantly trained in already known bad samples to assess the degree of danger of new ones. Explicit abuses are blocked automatically. Questionable pass through manual control.
We have learned how to catch not only those projects that steal passwords, redirect to phishing pages or secretly change / add their advertising to the pages. We also do not miss extensions, secretly replacing links on pages (including for earnings on affiliate programs) and unexpectedly opening tabs with advertised sites. We do not approve of the extraction of cryptocurrency, if the user has not given his explicit consent. We prohibit imitating clicks and other user actions (for example, to cheat likes or send spam on social networks).
For obvious reasons, we cannot disclose the details of the work of our scanners and the factors used in machine learning (we say hello to talented developers of dubious scripts). We can only say that thanks to this process, most malicious add-ons are disabled in the Yandex Browser 1-3 days after the start of their life. This is more than a hundred unique extensions per month and tens of thousands of protected users.
What's next?
No matter how surprising it may have sounded, but it is in RuNet that new methods of cheating users and browsers are being introduced, which are then “exported” further. Now we are opposed not by amateurs, but by a whole industry of creators and distributors of dangerous extensions, who sooner or later will find another way to surprise us. We believe that we will find something to answer them, but there is no perfect protection, therefore, there will always be malicious extensions that we have not disabled yet. And here the help of the whole community will be useful. If you come across such developments, you can safely send information to our team (both through support and in a personal on Habré). We will also be grateful for any ideas and information that will help protect users from unpleasant surprises.
Source: https://habr.com/ru/post/341382/
All Articles