Bad Rabbit showed: ransomware encrypts backup data
On Tuesday, October 24, 2017, the extortion program Bad Rabbit struck Russia, Ukraine, Turkey, Germany, Bulgaria, the USA and Japan. Most of all, Russia and Ukraine suffered at the same time, since its distribution began on Russian news sites hacked by hackers. The first victims were Russian agencies Interfax and Fontanka, as well as Ukrainian transport organizations, including Odessa Airport, Kiev Metro and the Ministry of Infrastructure and a number of other organizations.

Our research has shown that the basis of Bad Rabbit is the revised NonPetya code and exPetr, which is also indicated by the model of its behavior and the ultimate goal of attacks. At the same time, we noticed that it includes elements of other extortionists , for example, the approaches used in developing the HDDCryptor cipher. However, at the same time, the people behind Bad Rabbit corrected some errors and brought all the above elements together, having a very interesting result. In addition, for their code, they used the fake Symantec security certificate. Another characteristic of Bad Rabbit is the ability to collect user passwords on infected computers and download additional malicious modules.
The cryptographer in question does not use fundamentally new tricks to attack and infect, but rather the opposite - it relies on a very old method, which implies that users install a fake update to Adobe Flash. Surprisingly, this approach still works, clearly demonstrating the low awareness of companies and consumers in cyber security issues and the dangers behind the extortion programs. Until users take this threat seriously and take the necessary security measures, the risks of losing access to their data remain very high.
Bad Rabbit Key Facts
- Uses code elements NonPetya / ExPetr
- Distributed as an update for Adobe Flash that requires manual installation.
- Uses legitimate driver for encryption
- It makes attempts to spread across the local network in a rather primitive way, but it can also use the SMB EternalRomance vulnerability.
- Replaces the master boot record of the hard drive and makes the computer unusable
- Legitimate driver is not always stable on Windows 10, system crash is possible
- Mainly affected corporate Windows users
Infection Scheme and Specifications
To launch the attack, cybercriminals hacked several popular media sites and put a script on them with a link to the fake Adobe Flash installer, which asked users to run the update when they entered the site. Many users have fallen for this trick, even though security experts have for many years warned people against installing software updates from dubious sources and recommend checking all updates with antivirus software to make sure that there is no hacking or infection with malicious code. Similar fake Adobe software updates were very popular many years ago and, unfortunately, remain effective in our days.
The dropper is distributed from the address hxxp: // 1dnscontrol [.] Com / flash_install.php. After that, the user loads the file install_flash_player.exe, which requires administrative privileges in the system. What is funny - he is trying to get them using the standard request of the User Account Control System (UAC). In the case of launch, the dropper extracts the cryptographic module of the infpub.dat file level (in fact, the dll library), the cryptographic module of the dispci.exe disk level and the kernel mode driver cscc.dat (in fact, the legal dcrypt.sys driver).
After a user “independently” infects his computer, Bad Rabbit tries to spread across the local network using the mimikatz tool, which enables him to retrieve credentials from the authentication system of the local security system in clear text, as well as the built-in list of credentials containing examples of least successful passwords. The attacks of the bad guys remain very effective, because “12345” and “password” have been in the top of the most popular passwords for many years.
As we have already noted, Bad Rabbit uses two types of encryption - file and disk level. It does not imitate chkdsk.exe, as NonPetya did to disguise encryption, and does not use the EternalBlue vulnerability in the Microsoft srv.sys file server, but it can use the EternalRomance vulnerability in the Microsoft srv.sys file server. First, Bad Rabbit runs file-level encryption (infpub.dat via rundll32) if it finds enough files for this. Then, in the Scheduler, he creates tasks for running dispci.exe to encrypt the disks, and then restarts the system. After the first restart, dispci.exe prescribes an extended boot program at the end of the disk, which later assumes all control functions using an MBR-infected disk. Finally, the entire disk is encrypted, the master boot record is replaced, and the computer restarts again, and a message with a ransom request in the amount of 0.05 Bitcoin (approximately $ 275) is displayed on its screen.
What is curious is that on computers with Windows 10, the module used for encryption often causes the appearance of a “blue screen of death” due to compatibility issues. Another point is that when encrypting files, their extension does not change, which can disrupt the operation of the heuristic mechanisms used by some antiviruses that react to an extension change. Bad Rabbit can work offline and, potentially, this means that it can infect other computers through flash drives.
The main purpose of Bad Rabbit are companies and commercial enterprises, and at the moment we are already seeing a decrease in the level of infection. The malicious server is no longer valid, and most of the infected sites that hosted the script for the malicious Flash update are currently disabled or disinfected. However, this does not mean that you can relax. A new attack can occur at any time.
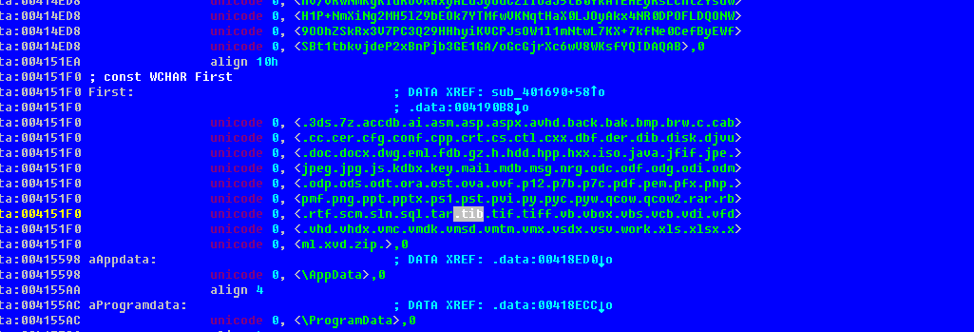
We have been following the problem of ransomware programs for a long time and noticed that users most often rely on backups as the main tool for protecting their data. As it is easy to guess, not only we, but also cybercriminals paid attention to this, therefore almost all new extortionists try to delete or encrypt backup files, including them. For example, Bad Rabbit, as seen in the screenshot above, attacks Acronis Backup files (* .tib).
Unfortunately for Bad Rabbit developers, starting with the Acronis True Image 2017 New Generation version, we provide reliable multi-level data protection using Active Protection technology, and the latest attack perfectly illustrates the effectiveness of our proactive technology. To repel an ransomware attack and protect user data, Active Protection does not need to be constantly updated, connected to the Internet, or use complex predefined rules. All this allows Acronis to provide the safest backup in the world, providing the only solution that combines active and passive approaches to data protection.
How Acronis Active Protection fights Bad Rabbit and any cyber-extortion attempts
Let's take a look at how Active Protection protects data from Bad Rabbit.
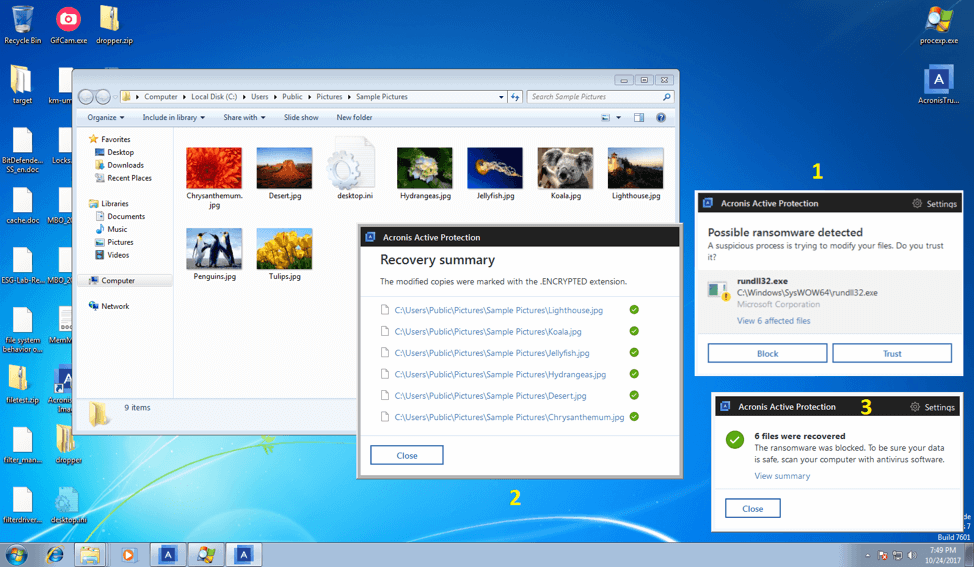
First of all, Acronis Active Protection detects malicious DLL modules launched via rundll32, recommends the user to block the malicious process and automatically cancels all unauthorized changes.
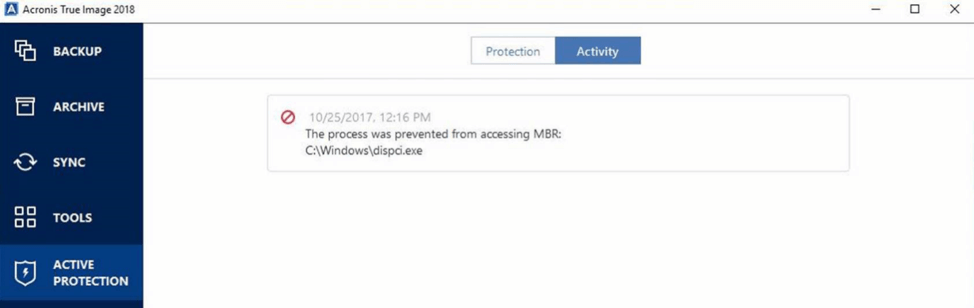
Active Protection also detects and blocks malicious attempts to change the master boot record (MBR) of your hard disk.
Finally, reliable self-defense technologies included in Acronis Active Protection easily prevent Bad Rabbit or any other ransomware program from attempting to encrypt backups.

Earlier this year, the self-defense feature was independently tested in the Anti-malware-test.com lab and found to be very effective, while most other backup solutions are virtually incapable of self-defense.

Reliable backup that can stop the extortion program is an absolute necessity
Consider that if the antivirus program fails and the malware encrypts the backups, your data will be lost forever.
Therefore, it is important to choose a backup solution that:
- Includes proactive technologies against ransomware programs such as Acronis Active Protection .
- Provides a multi-layer protection that works at all stages of a potential attack: it warns, counteracts and restores.
- Offers robust self-defense features that do not allow the ransomware program to endanger either local or cloud backups.
- It works fast, because slow recovery means a waste of time and money. Acronis technologies have been independently tested, which confirmed their speed advantage over competitors.
Reliable backup solutions from Acronis:
- For business - Acronis Backup 12.5
- For home users - Acronis True Image 2018
- For service providers - Acronis Backup Cloud
')
Source: https://habr.com/ru/post/341318/
All Articles