2.Check Point to the maximum. HTTPS Inspection

In the previous lesson, we touched upon the problem of human factors in Information Security. As a result, we concluded that it does not matter how high-quality and expensive equipment you use, because everything “rests” in the setting that needs to be done correctly. In this lesson we will look at the https inspection . Quite a few underestimate the importance of this feature without which modern network protection is unthinkable. But first things first.
Web traffic protection
Almost all modern NGFW or UTM solutions have the functionality of checking web traffic. This categorization of sites and verification of downloadable content and the definition of web applications. And the last item (web applications) is very important, because A huge number of services can work through the same port. And if with verification of HTTP traffic almost all vendors have no problems, then HTTPS is a real challenge for modern security tools.
Https
I think that there is not much point in telling what HTTPS is and how important it is for the organization of a secure Internet. Thanks to HTTPS, you can be sure that it is impossible to intercept or change the transmitted information between the client (browser) and the server (web-server). According to statistics for 2017, the share of HTTPS traffic exceeded 50%.
')
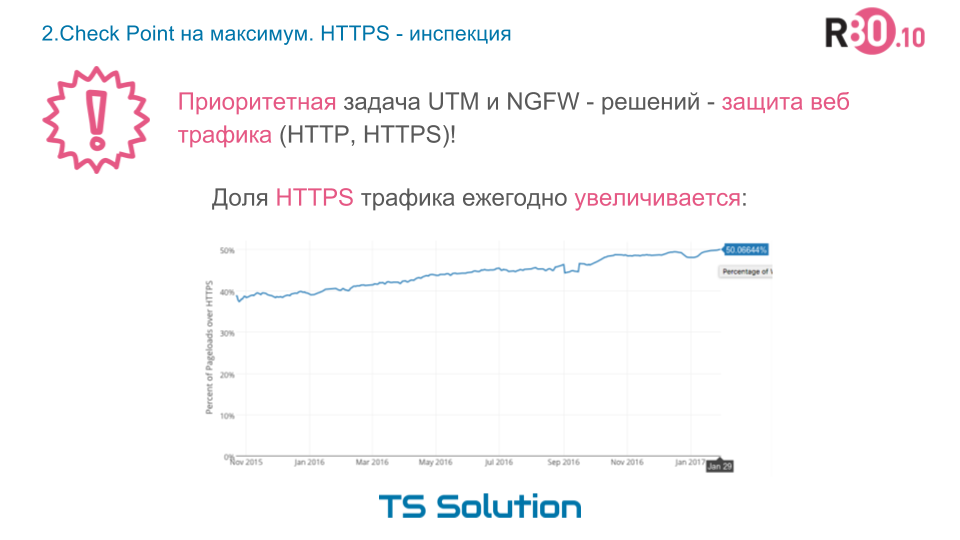
Moreover, modern browsers (for example, google chrome) will mark http-sites with authorization form as untrusted, and google will lower them in search results. All this will provoke an even more rapid increase in the proportion of HTTPS traffic.
As mentioned earlier, HTTPS is used for secure communication between two nodes on the Internet. At the same time, HTTPS is not some kind of new protocol; in general, this is plain HTTP, but SSL or TLS is used as a transport protocol to protect traffic. It is these protocols that are responsible for the authentication, encryption and integrity of the traffic. We will not consider in detail the work of these protocols, but I highly recommend this article to anyone interested. In a rough approximation, the work of HTTPS is as follows:
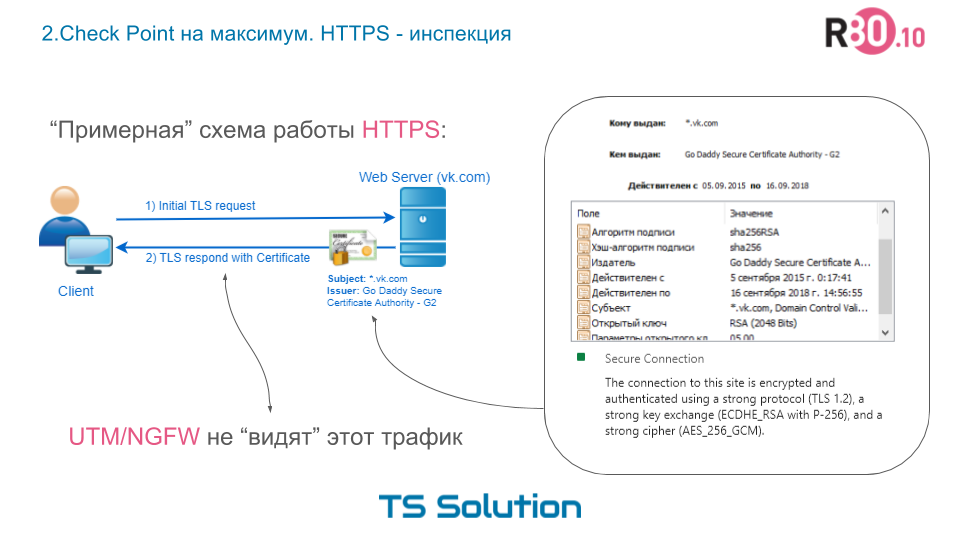
Those. the client initiates a TLS request to the Web server and receives a TLS response, and also sees a digital certificate, which naturally must be trusted. An example of a certificate when accessing the site vk.com is shown above. It contains the secure connection settings and the public key. In addition, the browser can “tell” which version of TLS is being used. I repeat that this is a very simplified description of how TLS works.
After a successful TLS Handshake, data transfer begins in encrypted form. It would seem that this is very good (the way it is). However, for the "bezopasnik" in the company is a real headache. Since he does not “see” this traffic and cannot check its contents either by antivirus, intrusion prevention system (IPS), or DLP system, nothing ... And this in turn represents a very serious vulnerability. Since most sites switch to HTTPS, then without an HTTPS inspection, your Internet gateway cannot check most of the Web traffic (because it is encrypted). In addition, attackers are increasingly using cloud file storage to spread viruses, which also work over HTTPS. Thus, no matter how high-quality and expensive your firewall is (whether it is a UTM or NGFW solution), it will skip absolutely all viruses and malware without HTTPS inspection enabled. Even the notorious test virus EICAR, which is detected by any antivirus, will successfully pass your protection through HTTPS. We will consider it by example.
HTTPS Inspection
The HTTPS inspection technology is designed to solve the problem of security. Its essence to ugliness is simple. In fact, the device that organizes the HTTPS inspection performs a man-in-the-middle attack . It looks something like this:
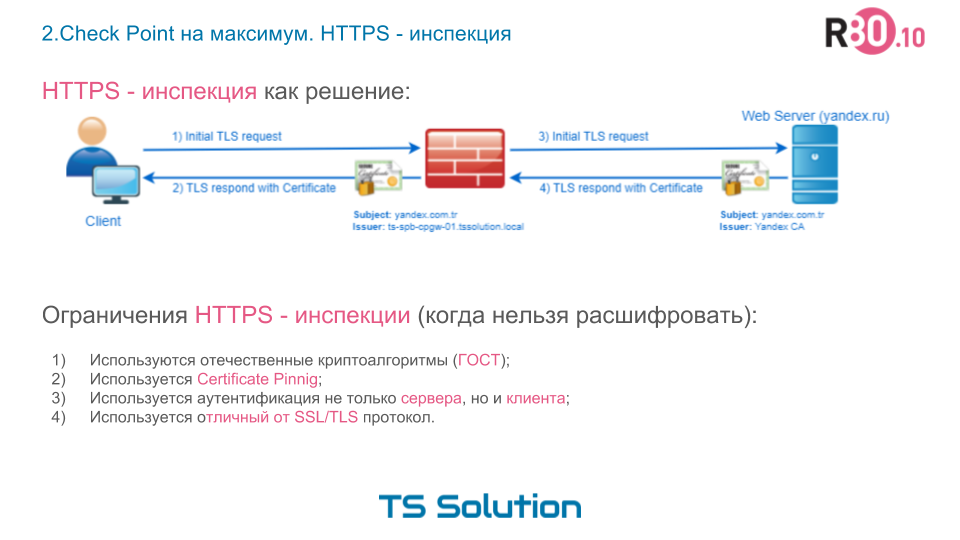
Those. Check Point intercepts the user's request, picks up an HTTPS connection with it, and from itself picks up an HTTPS session with the resource the user has accessed. In this case, the client is presented with a certificate that Check Point has released himself. Of course, this certificate must be trusted. To do this, Check Point has the ability to import a certificate from a trusted CA (subordinate certificate). When importing, make sure that the certificate has a signature algorithm not lower than sha256 , since if it is for example sha1 , then modern browsers will “swear” on such certificates. Or, you can generate a self-signed certificate, which you must then make trusted for all computers. This is the way we look at an example.
Thus, being in the middle between two encrypted connections, Check Point is able to check the traffic and all files, both with the help of antivirus and with other blades (IPS, Threat Emulation, etc.). You can read more about Check Point HTTPS Inspections here .
Limitations of HTTPS Inspection
However, not all so simple. The man-in-the-middle method does not always work. There are cases when it is simply impossible to decrypt https traffic. Here are some examples:
1) Domestic cryptoalgorithms (GOST) are used instead of standard SSL / TLS.
At the moment, no foreign solution can provide the correct decryption of such HTTPS traffic (although I personally don’t know any domestic solutions that can do this https inspection). As a solution, you can configure exceptions in the HTTPS inspection for sites in this category.
2) Certificate Pinnig is used.
Those. The client application knows in advance the certificate of the server to which it is accessing. Usually, the certificate’s serial number is checked. In this case, the application will simply not look into the local trust store, and naturally, an attempt will be made when attempting to spoof. Most often this problem applies to fat clients (such as Skype, Telegram) that use SSL / TLS as a transport. In addition, just the other day I discovered that the updated version of google chrome also began to use certificate pinning technology for its services (youtube, google drive, gmail, and so on). This makes it impossible to use https inspections. Google is actively concerned about user safety, but it makes life safer for people. In this case there are two ways out:
- Set exceptions in https inspections for Google services. I am sure that this is highly undesirable for companies.
- Use another browser ... For example, Firefox.
I am sure that many are interested in the problem of such applications as a telegram, etc. Unfortunately (or fortunately) at the moment it is not possible to decrypt this traffic. Either you block these applications, because at the network level, it is impossible to “see” this traffic, or use an additional level of protection in the form of some agents on users' computers, for example, the CheckPoint SandBlast Agent , which can check already decrypted traffic for malware (for example, received files via instant messenger).
3) Authentication is used not only the server but also the client.
This is typical of websites from the financial services category, when a client uses a special key or token to access any portal portal. Naturally, in this case, the device that performs the HTTPS inspection will simply not be able to organize the https connection to the server, since does not possess the necessary key. The problem is solved only by setting exceptions in the HTTPS inspection.
4) A protocol other than SSL / TLS is used.
In this case, it's not about GOST encryption, but about a relatively new protocol from google - quic . The Google company is beginning to actively transfer its services to this protocol. At the same time, it is currently impossible to decrypt it. The only solution in this case is to block the protocol quic, after which google services begin to use standard SSL / TLS.
Customization
Describing the setting in text format is quite time consuming, so we made a short video. The first part describes the above theory, and in the second part we try to download the virus via HTTPS, and then we will configure the HTTPS inspection and compare the result.
Conclusion
The most important thing to take out of this lesson is that the HTTPS inspection is a MANDATORY component of modern security. Without this feature, your network has a huge black hole in terms of security. And this applies not only to Check Point, but to all other solutions. Be sure to test your network in this way. All that is needed is some kind of test virus and client machine, preferably without an antivirus, so that it cannot block the download of the file (for the purity of the experiment).
This concludes the second lesson, thank you for your attention!
PS I would like to thank Alexey Beloglazov for help in preparing the lesson.
Source: https://habr.com/ru/post/341200/
All Articles