“I will find out! I recognize my brother Kohl! "- The realities of modern information security in the field of wireless technologies
Plowing the vast expanses of the Internet, I repeatedly stumbled upon displeased reviews of users of the free Wi-Fi network of the Moscow metro MT_FREE. The problem was (by the way, things are still there) that the Wi-Fi network of ground-based urban transport had the same name as in the subway. Imagine a situation: you go somewhere, listen to music, do not touch anyone, and then there is a byscis - a bus arises before you; your phone notices the familiar Wi-Fi network and, utterly pleased with its resourcefulness, (to you, of course, not questioning) is speedily connected to it. Instead of music, now you hear only the moaning sound of the bus leaving the distance.

So, wait a second ...
')
The other day I made a simple unit (which is in essence a mixture of powerbank and the well-known Orange Pi with an integrated Wi-Fi module), with which I had just set up an experiment, the task of which was to count the number of citizens (and also their warning about that they should be more serious about the integrity and security of their data), that they do not care about their security in the network. Its essence is simple - OpenWrt is placed on an orange with dnsmasq (the latter is configured so that the client receives the same answer to any DNS request - it must contain the address of the local gateway on which the web server rotates) and an open Wi-Fi network, which is assigned the same notorious SSID - “MT_FREE”, after which the number of people and their smartphones (together with other devices) that connected to this network is counted.
For some time, data is collected and written to a file (in my case, dhcp.leases and php.leases). The dhcp.leases file contains the information needed by the DHCP server to enforce certain IP addresses for each client for some time (some kind of lease). A little different is the case with the php.leases file - after a user deliberately clicking on the “Enter Internet” button, a new line with pre-defined text is written to the file. This is necessary in order to calculate the number of people that could be pressed on the buttonand put themselves in danger later. Just want to draw attention to the fact that this is an ugly to horror crutch that was written on the knee (literally) for a few minutes in a shaking bus.
You, probably, have already guessed without me - these are statistical data that the box has been carefully tamping for four hours. I hasten to notice - the experiment began at seven in the morning and ended at exactly noon. The venue is a rather large town near Moscow.
For a relatively short period of time, a total of 95 devices managed to connect to my access point, of which:
79% of the devices connected to the access point offline, ie, without human intervention. Only 20 people clicked on the “Enter Internet” button (21% of the total amount of all connected devices).
Now I would like to go directly to the practical part and show my “miracle machine” in action.
I am very grateful for the attention paid, amico! See you again!

So, wait a second ...
')
DO NOT EVEN THINK!Another thing.
Material provided for informational purposes only. I do not bear responsibility for any actions you have committed upon reading this article.
“And what actually happened?”
The other day I made a simple unit (which is in essence a mixture of powerbank and the well-known Orange Pi with an integrated Wi-Fi module), with which I had just set up an experiment, the task of which was to count the number of citizens (and also their warning about that they should be more serious about the integrity and security of their data), that they do not care about their security in the network. Its essence is simple - OpenWrt is placed on an orange with dnsmasq (the latter is configured so that the client receives the same answer to any DNS request - it must contain the address of the local gateway on which the web server rotates) and an open Wi-Fi network, which is assigned the same notorious SSID - “MT_FREE”, after which the number of people and their smartphones (together with other devices) that connected to this network is counted.
We get a toy
/etc/dnsmasq.conf
/ etc / config / uhttpd
/ etc / config / dhcp
/ usr / bin / honeypot
...
address = / # / 192.168.1.1
/ etc / config / uhttpd
config uhttpd 'main'
...
option error_page '/index.html'
/ etc / config / dhcp
config dnsmasq
...
option leasefile '/usr/share/dhcp/dhcp.leases'
/ usr / bin / honeypot
### ### ### ### dhcp.leases php.leases ### while :; do clear && echo -e "I'm $HOSTNAME!\\n`date +%H:%M:%S`\\n\\nDHCP leases: `wc -l /usr/share/dhcp/dhcp.leases`\\nPHP leases: `wc -l /usr/share/dhcp/php.leases`" && sleep 1; done For some time, data is collected and written to a file (in my case, dhcp.leases and php.leases). The dhcp.leases file contains the information needed by the DHCP server to enforce certain IP addresses for each client for some time (some kind of lease). A little different is the case with the php.leases file - after a user deliberately clicking on the “Enter Internet” button, a new line with pre-defined text is written to the file. This is necessary in order to calculate the number of people that could be pressed on the button
That's how this utter ugliness looks
<?php shell_exec('echo `date +%H:%M:%S` New DHCP lease and user action! >> /usr/share/dhcp/php.leases'); ?> Well well! And what about delicious?
You, probably, have already guessed without me - these are statistical data that the box has been carefully tamping for four hours. I hasten to notice - the experiment began at seven in the morning and ended at exactly noon. The venue is a rather large town near Moscow.
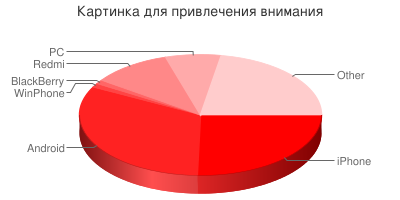
For a relatively short period of time, a total of 95 devices managed to connect to my access point, of which:
- 24 “iPhone” phones (which is noteworthy - as a rule, their hostnames contain the names of the owners)
- 31 Android phones
- 1 "Windows Phone"
- 1 BlackBerry
- 10 "Redmi" by Xiaomi
- 7 portable personal computers like "laptop"
- A number of other devices that support Wi-Fi connectivity.

79% of the devices connected to the access point offline, ie, without human intervention. Only 20 people clicked on the “Enter Internet” button (21% of the total amount of all connected devices).
What is it fraught with?
Social engineering is a scary beast that ordinary citizens usually overlook. We should be wary of this.
As user shanker noted ,
As user shanker noted ,
Threats during automatic connection:
1. Evilgrade type attack
2. Social engineering and password removal (redirect to a similarly controlled site, but without HTTPS, or substitution for an illegitimate certificate)
3. Mining of cryptocurrency by upgrading the content issued to browsers
4. Exploitation of vulnerabilities in browsers (by injection of exploits into the requested pages).
How to protect yourself?
Disable auto-connect to Wi-Fi hotspots and clear the list of access points stored in the device’s memory.
Now I would like to go directly to the practical part and show my “miracle machine” in action.
“Comrades! See all! Lovers are beaten! ”
Due to the fact that in the world I am a seventeen year old convoy and I study at college, any criticism from the community is welcome. Learning, as they say ... Light!
I am very grateful for the attention paid, amico! See you again!
Source: https://habr.com/ru/post/341116/
All Articles