Another operating system architecture
I decided to take a short pause in daily hobby coding, and share with you a description of what I actually do. So, I try to develop and implement a virtual machine for a non-existent operating system, which I, perhaps, will also someday begin to implement. I will not argue with foaming at the mouth, proving why another OS is needed, I will answer briefly: mainly because I am interested.
1. There are two main entities: module and stream.
2. The module contains unchanged code and changeable data.
3. The module is permanent.
The last point says that the module always exists. In practice, this should be implemented through virtual memory. Those. the module pages currently in use are loaded into RAM, and unused pages are downloaded to disk. Permanent support should be at the system level, i.e. completely transparent to the application programmer. This can be considered a swap, brought to a logical conclusion, when we no longer need to load the module into RAM, since it will be in the “eternal” swap, and automatically loaded upon request. In other words, the file system is no longer needed.
')
4. The module has many external procedures available to call from the outside. Module data is only available indirectly through its external procedures.
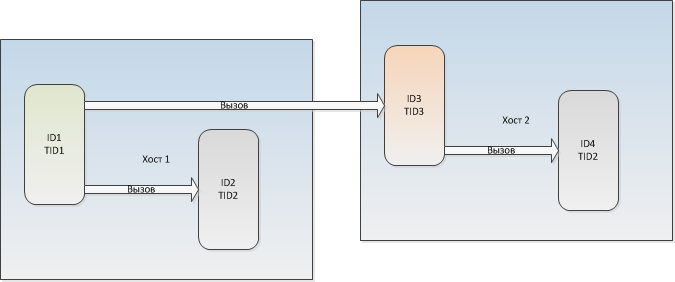
5. The module has an instance UUID (ID) and a type UUID (TID).
6. When copying a module, a new ID is generated for the copy, but the old TID is saved.
7. The module can be found by ID in the global network, or by TID on the local host.
Each TID on the local host corresponds to only one module, even if there are several modules with the same TID.
8. A thread can call an external procedure by its module ID and its numeric identifier.
9. A thread can call an external procedure using the TID of its module located on the same host and its numeric identifier.
Roughly speaking, TID is necessary for using modules as dynamically loaded libraries. In fact, the hosts will have a lot of the same code (system software, codecs, etc.), access to which must be very effective, and which does not make sense to use remotely.
1. The external procedure call is synchronous.
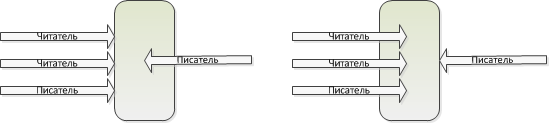
2. An external procedure can be a function (f-procedure), a reader (r-procedure) or a writer (w-procedure). The F-procedure does not use modifiable module data, the r-procedure reads modifiable data, and the w-procedure modifies it.
3. Calling the f-procedure of the module is called without blocking.
4. The r-procedure call is not blocked if other r-procedures are already called in this module.
5. The call of the r-procedure and the w-procedure is blocked if the w-procedure is already called in this module.
6. If r-procedures and w-procedures are blocked, when unlocking the first one, the w-procedure is performed.
Those. there may be many readers without a writer, or just one writer. The writer has a higher priority over readers.
In the above theses, a lot of things are missing. In particular, the security architecture is completely absent. Alas, I cannot formulate it yet.
In subsequent posts, I will describe the overall architecture of the virtual machine, as well as the details of its implementation up to the current state of the project. By the way, the current implementation is able to execute programs for calculating factorial and quick sorting. For those who are prematurely curious, I give a link to the repository: github.com/ababo/AntOS-VM-Prototype

So, my current vision of the system architecture.
1. There are two main entities: module and stream.
2. The module contains unchanged code and changeable data.
3. The module is permanent.
The last point says that the module always exists. In practice, this should be implemented through virtual memory. Those. the module pages currently in use are loaded into RAM, and unused pages are downloaded to disk. Permanent support should be at the system level, i.e. completely transparent to the application programmer. This can be considered a swap, brought to a logical conclusion, when we no longer need to load the module into RAM, since it will be in the “eternal” swap, and automatically loaded upon request. In other words, the file system is no longer needed.
')
4. The module has many external procedures available to call from the outside. Module data is only available indirectly through its external procedures.
5. The module has an instance UUID (ID) and a type UUID (TID).
6. When copying a module, a new ID is generated for the copy, but the old TID is saved.
7. The module can be found by ID in the global network, or by TID on the local host.
Each TID on the local host corresponds to only one module, even if there are several modules with the same TID.
8. A thread can call an external procedure by its module ID and its numeric identifier.
9. A thread can call an external procedure using the TID of its module located on the same host and its numeric identifier.
Roughly speaking, TID is necessary for using modules as dynamically loaded libraries. In fact, the hosts will have a lot of the same code (system software, codecs, etc.), access to which must be very effective, and which does not make sense to use remotely.

Now the multithreaded synchronization model.
1. The external procedure call is synchronous.
2. An external procedure can be a function (f-procedure), a reader (r-procedure) or a writer (w-procedure). The F-procedure does not use modifiable module data, the r-procedure reads modifiable data, and the w-procedure modifies it.
3. Calling the f-procedure of the module is called without blocking.
4. The r-procedure call is not blocked if other r-procedures are already called in this module.
5. The call of the r-procedure and the w-procedure is blocked if the w-procedure is already called in this module.
6. If r-procedures and w-procedures are blocked, when unlocking the first one, the w-procedure is performed.
Those. there may be many readers without a writer, or just one writer. The writer has a higher priority over readers.

In the above theses, a lot of things are missing. In particular, the security architecture is completely absent. Alas, I cannot formulate it yet.
In subsequent posts, I will describe the overall architecture of the virtual machine, as well as the details of its implementation up to the current state of the project. By the way, the current implementation is able to execute programs for calculating factorial and quick sorting. For those who are prematurely curious, I give a link to the repository: github.com/ababo/AntOS-VM-Prototype
Source: https://habr.com/ru/post/341110/
All Articles