Fake emails from almost any person in less than 5 minutes and ways to protect

What is email authentication?
For most of the past 40 years, users had to take a leap of faith every time they opened an email. Do you think that the letter really comes from the person specified in the sender column? Most will easily answer “yes” and in fact will be very surprised to learn how easy it is to fake email from almost any sender.
When creating the Internet, there was originally no way to verify the identity of the sender. During the development of basic e-mail protocols, the cost of computing power, implementation, and ease of use were balanced with the risk of fraud. It was hard to imagine that 84% of all email in the future would have a malicious load and be phishing or spam.
')
The result is that the headers of letters, including the From: and Reply-to: fields, are very easy to fake. In some cases, it is as easy as typing "john@company.com" in the "From:" field. By combining this with unsuspecting content, convincing graphics and formatting, it is possible to deceive people who thought that the message in their mailbox really came from the bank, the Federal Tax Service, the head or president of the United States.
Taking into account the widespread distribution of e-mail, you are aware of the basis of our current information security crisis. Weakness in email has led to a mass of phishing attacks aimed at getting people to click on malicious links, download and open malicious files, send a W-2 form (similar to 2-NDFL in the US), or transfer funds to criminals.
Most recently, Coupa, a Silicon Valley company, was in the spotlight after sending payroll data to all 625 employees to a fraudster. Last year, one of Europe's largest companies, Leoni AG, lost $ 45 million when an employee mistakenly transferred money to a fraudster account because of a fake email. The FBI estimates phishing attacks like “Compromise business correspondence” (BEC - Business Email Compromise) cost US companies $ 3 billion a year.
On databreaches.net a list of phishing forms of the W-2 was compiled. The work on the list this year indicates that the number of cases since 2016 is growing and at the moment it consists of 204 reports . From the list it can be understood that there are known cases of theft of data of thousands of employees and this type of fraud is very common.
How an attacker can spoof unprotected email from almost any person in less than 5 minutes
In fact, a fake address in the "from" field is the basis and initial stage of most attacks. Why worry about email fraud with a conditional “company.com” when it is possible to simply register a similar fake domain (for example, c0mpany.com) and use it? Or create a Gmail account (randomaddress1347356@gmail.com), give it a friendly name that looks like the name of the company's CEO? Because, in fact, to fake sending a letter from the address of a real person is even easier than registering a fake domain or creating a Gmail account.
Three easy ways
On the Internet you can easily find sites that allow you to send fake letters. There are dozens of them, here are just a couple of examples: spoofbox.com and anonymailer.net. Many of them are free, some cost money, these services are positioned as legitimate, and the main purpose of the use is supposed to be a rally of friends.
The usage algorithm is simple. You only need to enter the recipient's email address in the "To:" field, put any desired email address in the "From:" field and confirm the sending after creating the message. According to the terms of the user agreement, the responsibility for damage lies entirely with the clients of the service.
The next method is to send using the UNIX command line . If you have a computer with a customized mail service, just enter this command:
mail -aFrom:whatever@anydomain.comThe result is a message in which the “From” field will contain “any@anydomain.com”. Having entered the subject line and the rest of the message, after pressing Ctrl + D the message will be sent to the recipient. The performance of this idea depends on how your system is configured. However, it works in many cases.
Using PHP , you can create an email with a few lines of very simple code:
<?php $to = 'nobody@example.com'; $subject = 'the subject'; $message = 'hello'; $headers = 'From: webmaster@example.com' . "\r\n" . 'Reply-To: webmaster@example.com' . "\r\n" . 'X-Mailer: PHP/' . phpversion(); mail($to, $subject, $message, $headers); ?> In fact, these are lines of code used as an example in the online tutorial for the mail () function with additional / header headers.
These spoofing tools are greatly simplified. To make the messages more realistic, it takes a little more work and, of course, social engineering skills. But the main technical component is very simple. The only thing that really prevents spoofing is email authentication using SPF record sharing, DKIM signatures, and DMARC. Next, we describe how these technologies work and how they differ. They are not new, but fortunately for scammers, most domains on the Internet are not yet secure. For example, only about 4% of .gov domains use authentication. What about the other 96%? Attackers can send emails under the guise of outgoing mail from these domains at any time.
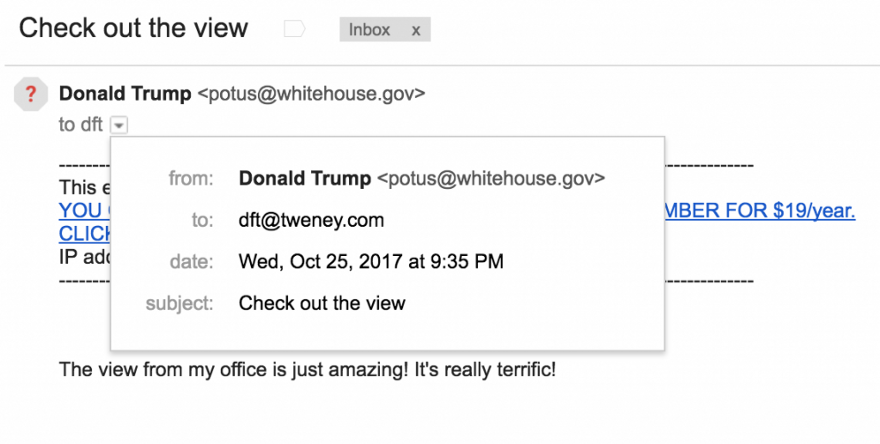
According to the source , one of the four letters from .gov domains is fraudulent. Domains justice.gov, House.gov, Senate.gov, Whitehouse.gov, and also democrats.org, dnc.org, gop.com, rnc.org. and DonaldJTrump.com - all of them can be easily used for spoofing by mail scammers.
Ways to protect against spoofing
The simplicity described above of using the e-mail vulnerability without authentication and the widespread use of these methods as an initial stage for the largest cyber attacks, focuses the attention of the IT community on the need to use mail authentication technologies. By implementing email authentication, you can ensure that any user — an employee, client, or partner who receives an email — can determine if the email has been sent by a legitimate company representative. In addition, you can get transparency and control of who sends email on your behalf.
The importance of this has increased dramatically due to the rapid growth of cloud services ( SaaS ), more than 10,000 of which send email on behalf of their clients on sales, marketing, customer support, HR, accounting, legal and other services. Thanks to forced authentication, you can block anyone who is trying to send an email on your behalf — spammers, phishers, and even “gray” senders who may be legitimate but not listed by you in the list of allowed ones.
Authentication email standards allow the mail server to verify that the email with your domain in the "From:" field was allowed to be sent on your behalf. Before getting the message in the recipient's inbox, the mail server can check:
- Using an SPF record , does the sending server have the right to use the domain name (or names) specified in the message headers?
- If a cryptographic DKIM signature is attached to the message, using the public version of the key in the DNS record of the domain, you can decrypt the headers of the incoming messages and find out whether the message really comes from the stated sender.
- By configuring DMARC , domain owners can create rules for processing emails that come from unauthorized domains and check if the headers match each other (for example, From: and Reply-to fields :). The rules include instructions on what the receiving server should do with unauthenticated messages, for example, do not skip them, put them in a spam folder, or mark them as potentially dangerous. Email authentication gives the domain owner global control over what happens to messages sent on their behalf by anyone and anyone. For example, if you submit a domain as the sender of the mail and publish a DMARC record requesting information, then you will receive from all recipient domains that also support DMARC, statistics on all mail that comes with a return address from your domain. The statistics come in XML and contain the IP address of each sender that is signed by your domain, the number of messages from each IP address, the result of processing these messages in accordance with the DMARC rules, SPF results and DKIM results
Why is sharing of these technologies necessary?
In a simplified sense, SPF allows you to create a white list for IP addresses. If a mail server with an IP address that is not on your list tries to send an email using your domain, the SPF authentication test will fail. However, the big problem with SPF is that it uses the domain specified in the Return-Path field for authentication, and not the From field that people actually read.
Worse, phishing intruders can configure SPF records for their own domains. Then they can send emails that seem to come from a company or a trusted brand, but the domain of this company will be displayed in the From field, and the domain of the fraudster in Return-Path. Such letters will be authenticated by SPF. The additional use of DMARC solves this problem by allowing the domain owner to require “leveling”, which means that the return and outgoing addresses must be the same.
SPF records are text, but the syntax is rather complex. You can easily make typos that are difficult to detect. In doing so, they will make SPF recording useless. An analysis of the SPF records of all 62 sponsors of the RSA 2017 conference showed that only 58 published SPF, while 17 sponsors of the conference on cyber security had errors in the record. Companies that do not have much experience in the IT field often find SPF even more difficult.
Also, DKIM is not particularly effective against fraud without the use of DMARC. To stop phishing, the most important address is the domain in the "From" field. However, checking only DKIM signatures says nothing about the domain in this field. The domain used for signing a message may be completely different from the domain specified in the "From" field. In other words, hackers can create messages that subscribe via DKIM using the domain they control, but in the "From" field there will be your bank email. Most people do not intend to dig into the headers of all incoming messages to make sure that the DKIM signature data is legitimate. It is also worth considering a large number of legitimate postal services that can do mailings on behalf of the sender and the problem of preserving the privacy of the private key used to sign messages.
These two early standards, while important, contain important gaps. DMARC builds on and complements them. DMARC significantly increases the credibility of the email you send, regardless of whether you receive emails from your own email servers or cloud services that you allow to send emails.

The main contributions of DMARC are:
- setting a policy that tells receiving e-mail servers what to do with e-mail messages that are not authenticated (nothing, quarantine or rejection),
- reporting mechanism.
Having a policy and feedback mechanism is what makes it all work.
Check that DMARC is configured using services.
→ mxtoolbox.com
→ mail-tester.com and others.
The article is based on a translation from sources:
→ How to Fake an Email
→ What is Email Authentication?
→ What is SPF?
→ What is DKIM?
→ What is DMARC?
Related articles on Habrahabr:
→ We forge letters from the largest Russian banks
→ Set up DKIM / SPF / DMARC records or defend against spoofing
→ Why does Sberbank have an incorrect SPF record for a domain?
→ Implementing DMARC to protect your corporate domain from spoofing
Source: https://habr.com/ru/post/341096/
All Articles