Bad Rabbit ransomware Trojan: Bad, Bad Rabbit

On October 24, notifications of mass attacks with the help of the Bad Rabbit Trojan ransomware fell on us. The main goal is Russian organizations and consumers, but there are reports of victims from Ukraine.
Here’s what the ransom demand for hapless victims looks like:

What a view
Bad Rabbit (translated as “bad rabbit”) is a previously unknown family of ransovari.
')
How to multiply
The dropper of the extortioner is distributed due to drive-by downloads . The goal is visited by a completely legitimate site, while the malicious dropper is loaded from the infrastructure of the attacker. No exploits are used, the victim launches the dropper manually - he pretends to be an Adobe Flash installer.
We found a number of compromised websites, all of which are news or media.
Whom the tooth sharpens
Most of the targets are located in Russia. Similar, but smaller volumes of attacks were observed in other countries - Ukraine, Turkey and Germany.
When did Kaspersky Lab detect the threat?
We fixed the initial attack vector in the morning of October 24th. The attack continued until noon, but we still detect isolated cases of infection.
What is the difference with ExPetr? Or is it the same malware?
Our observations show that this was a targeted attack on corporate networks using methods similar to the ExPetr toolkit .
Technical details
According to our telemetry, this evil rabbit breeds by passing loading.
The ransomware dropper is loaded from hxxp: // 1dnscontrol [.] Com / flash_install.php
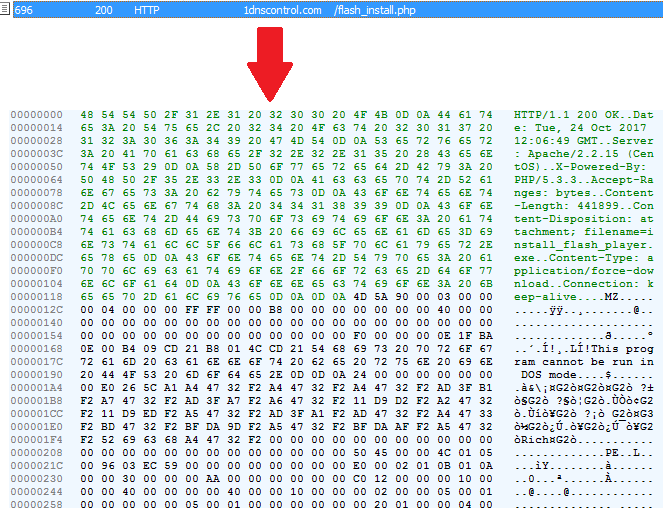
According to our data, victims are redirected to a malicious resource from legitimate and harmless news sites.
The downloaded file named install_flash_player.exe is launched by the victim manually. In order to work correctly, it needs elevated administrative privileges, which it is trying to get using the standard UAC request. When launched, it will save the malicious DLL as C: \ Windows \ infpub.dat and launch it using rundll32.

Pseudo-code for installing a malicious DLL file
infpub.dat brute-force NTLM authentication manager credentials on Windows machines with pseudo-random IP addresses.

Hard-coded list of accounts
infpub.dat also installs the malicious utility dispci.exe on C: \ Windows and creates a task to start it.

Pseudocode of the procedure that creates the task that starts the malware
Moreover, infpub.dat acts as a typical extortionist-cryptographer: through the built-in list of extensions, it finds the victim's data files and encrypts them using the RSA-2048 public key.
Open cyber villain key and list of extensions
Parameters of the villainous public key:

Apparently, the executable file dispci.exe was created based on the code of the harmless utility DiskCryptor. It acts as a disk encryption module, which also installs a modified bootloader and interferes with the normal boot process of an infected machine.
The sample of the analyzed threat turned out to be with a twist: it seems that its authors are ardent fans of the “Game of Thrones”. Some lines of code contain the names of various characters in the series (or books).
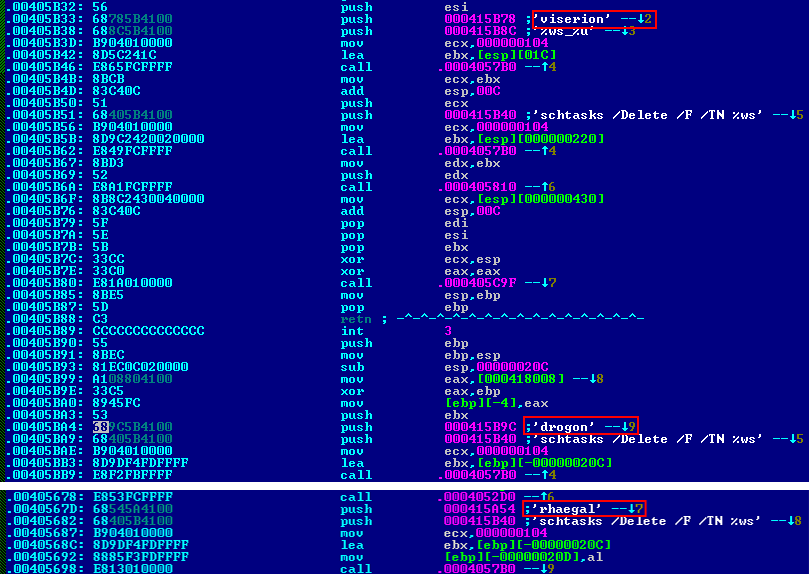
The name of the dragon from the “Game of Thrones”

Character Name “Game of Thrones”
A bad rabbit encrypts files and a hard disk according to a typical cryptographic scheme, using the AES-128-CBC and RSA-2048 algorithms. Interestingly, the Trojan compares the hashes of the names of running processes with a given table. And the hashing algorithm is similar to the one used by the famous exPetr.
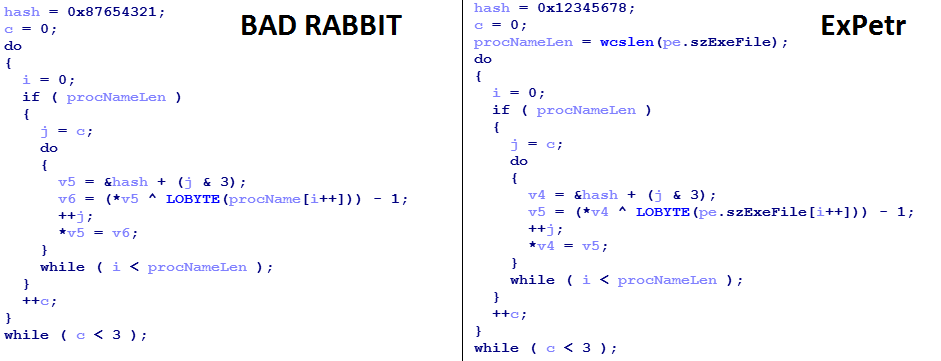
Comparison of Bad Rabbit and ExPetr hashing procedures

Special branch of the program

Procedure for initialization of runtime flags
Full list of hashes from process names:

The rabbit sends the DiskCryptor driver (originally called dcrypt.sys, and the Trojan disguises it as cscc.dat and puts it in C: \ Windows \) IOCTL codes to encrypt the hard disk partitions. Some functions are simply taken from the DiskCryptor sources, from the drv_ioctl.c file, others are developed by the authors of the rabbit.
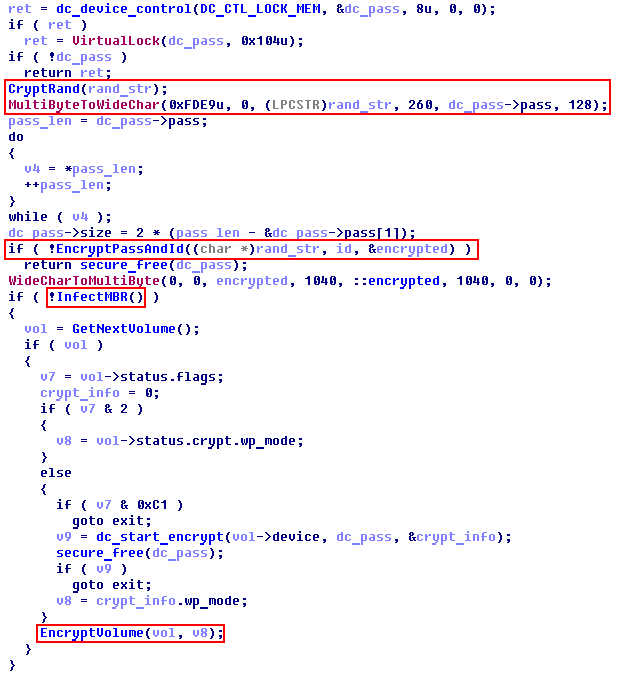
Pseudocode procedure that generates a password and encrypts disk partitions
Kaspersky Lab experts carefully prepare the “bad rabbit” for possible loopholes in its cryptographic algorithms.
Our clients can feel protected if they have activated all the protective mechanisms of the products (KSN and System Watcher are not disabled), as well as updated bases.
As an extra precaution, it makes sense to block the execution of the files C: \ Windows \ infpub.dat and C: \ Windows \ cscc.dat .
IOCs:
1dnscontrol [.] Com /
fbbdc39af1139aebba4da004475e8839 - install_flash_player.exe
1d724f95c61f1055f0d02c2154bbccd3 - C: \ Windows \ infpub.dat
b14d8faf7f0cbcfad051cefe5f39645f - C: \ Windows \ dispci.exe
Source: https://habr.com/ru/post/340944/
All Articles