How to integrate with Cisco security solutions? Overview of two dozen APIs available to all
Today, the theme of SOC and SIEM has become very fashionable in Russia. All of them build and write. Did you know that Russia already has about a dozen of its own security event monitoring systems (SIEM)? This number has exceeded the number of commercial SOCs offering their services to customers who fall under the requirements of 187-FZ on the safety of critical information infrastructure and will be forced to promptly give the data on incidents to GOSFNR. But whatever goal the creators of SIEM and SOC pursue, and no matter what level of maturity they are in, they still face the basic task of collecting security events and logs from scattered information protection tools.
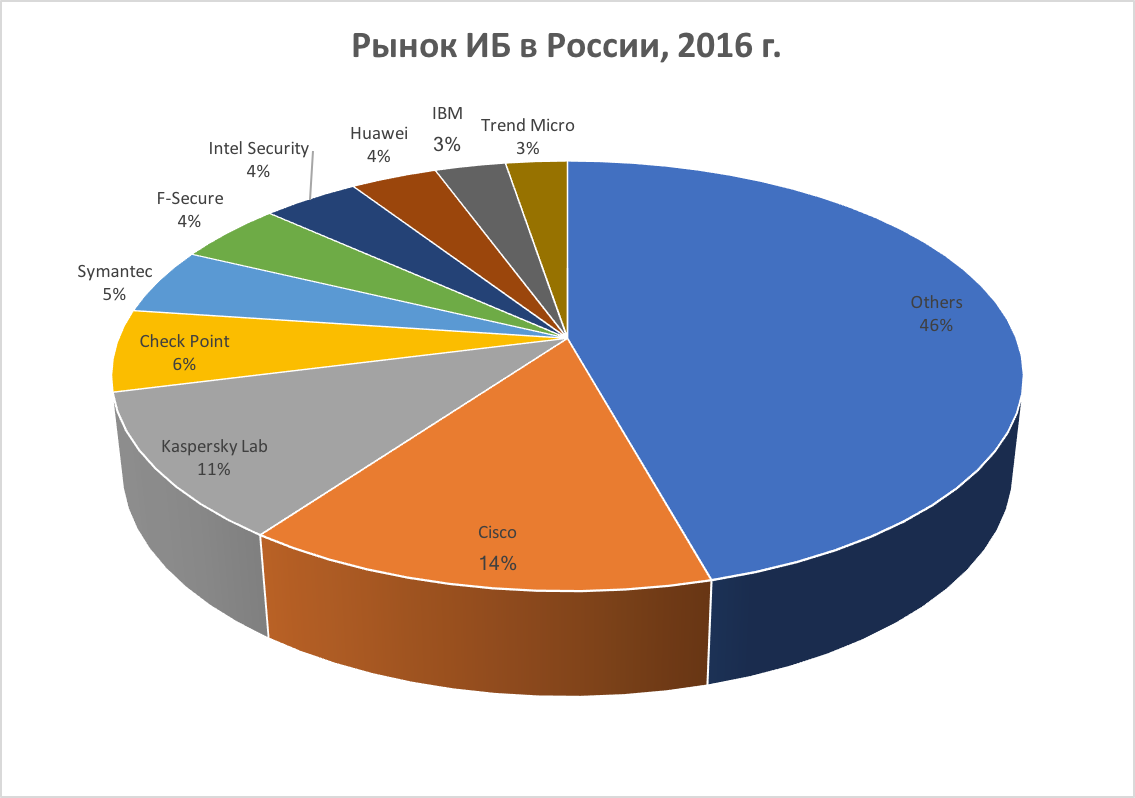
According to the company Canalys (and it is the only one who continues to evaluate the Russian market of information security solutions), Cisco remains the leader in the domestic market. Therefore, it is quite reasonable to assume that one of the first tasks that must confront the developers of SIEM / SOC is integration with the solutions of our company. But around this integration there are many myths and misconceptions that can be described by the dialogue that I recently had with one of the domestic manufacturers of SIEM:
- Why don't you integrate with Cisco solutions?
- So you already have all the proprietary?
- No, it is not so!
- Yes? And they told me that you have closed APIs and access to them costs money.
- No, and it is not!
')
Therefore, I decided today to briefly describe the APIs that exist for Cisco, and with which you can connect to its cybersecurity solutions. They can be divided into several types:
The first type of API includes:
Let's look at an example of working with the API for AMP for Endpoints , a solution that is placed on personal and mobile devices running Windows, Linux, iOS, Android, MacOS, and which protects against a wide range of threats. Suppose we want to receive security events that have occurred recently. To do this, use the “GET / v1 / events” request, which has many additional options that allow you to make selections on a specific node or group of nodes, the hash of the file of interest, type of event, time, etc. For example, we may be interested in events for a specific node and then the request through AMP for Endpoints API will look like this:
The answer will be as follows:
The second type of API includes:
As an example, the second type of API will look at how the Threat Grid API is used . Suppose we want to check the status of a previously loaded file for analysis. Such a request might look like this:
and the answer is:
We see that the Threat Grid API returns us the value of the threat level by a hundred point scale for different types of file behavior (Threat Grid can evaluate up to 800 different parameters depending on the loaded file). The total value (threat_score) is 95, which means that the file being analyzed is malicious.
We can give an example of working with another API that allows evaluating the security of domains, information about which we can receive from ITU, mail gateways, proxies, Internet access control tools, etc. Using the OpenDNS Investigate API, we can formulate a request to verify the domain of interest to us:
And in the answer we get the values of various parameters by which OpenDNS evaluates the security of domains, IP addresses, autonomous systems, etc .:
The third type of API includes:

The fourth type includes
A natural question arises: how to get access to these APIs? Everything is very simple. Cisco has a special Cisco Security Technical Alliance Program, which consists of two large sections:
In order to integrate your SIEMs and SOCs with Cisco solutions, it is enough just to register on DevNet and, having received code samples, modify your solutions by equipping them with the appropriate components and software calls through the API. In principle, this is already enough to interact with Cisco security solutions. This is completely free (excluding your programmers' salaries). If your task is to enter the international market, to demonstrate your products to a wide audience, to prove serious intentions for integration with Cisco, which is the world leader in the cybersecurity market, then certain investments and SPP membership are necessary. It is along this path that companies like Check Point, ThreatQuotient, Anomali, Symantec, etc. went.

I hope that after such a brief excursus, no one will have any doubt that Cisco solutions are open like no one to integrate with external security products and services. In this direction, the company has been moving for several years, confirming the previously put forward slogan, which the Cisco Cybersecurity Division follows, - “Open. Simple Automation (Openness. Simplicity. Automation).
According to the company Canalys (and it is the only one who continues to evaluate the Russian market of information security solutions), Cisco remains the leader in the domestic market. Therefore, it is quite reasonable to assume that one of the first tasks that must confront the developers of SIEM / SOC is integration with the solutions of our company. But around this integration there are many myths and misconceptions that can be described by the dialogue that I recently had with one of the domestic manufacturers of SIEM:
- Why don't you integrate with Cisco solutions?
- So you already have all the proprietary?
- No, it is not so!
- Yes? And they told me that you have closed APIs and access to them costs money.
- No, and it is not!
')

Therefore, I decided today to briefly describe the APIs that exist for Cisco, and with which you can connect to its cybersecurity solutions. They can be divided into several types:
- APIs that allow access to security events, logs, and context, which are collected by Cisco solutions in a protected enterprise network.
- APIs that allow you to access Cisco cloud security services for checking suspicious files, domains, IP addresses, etc.
- APIs that allow you to manage Cisco solutions from external systems.
- APIs to enrich Cisco solutions with external threat data.
The first type of API includes:
- eStreamer API . An API that allows you to send security events from the multi-functional Firepower security platform to your SIEM.
- Host Input API . An API that allows you to collect information about vulnerabilities and other information about nodes on the network. It is the same that uses the same MaxPatrol from Positive Technologies to transfer Firepower information about vulnerabilities, operating systems and applications on scanned nodes, which is then correlated with threat data collected by the intrusion detection system NGIPS or the anti-malware AMP system on the Firepower platform.
- JDBC Database Access API . An API that allows you to query Firepower database from various applications.
- pxGrid . This is a whole framework that allows you to exchange security context (who, where, how, from where, with what got access) between the Cisco ISE network access control system and external solutions (SIEM, MDM, ITU, NAC, IRP, UEBA, CASB, IAM, VM and others.). Using this API, you can receive information about user access events and devices directly from the Cisco network infrastructure (switches, routers, access points, etc.).
- MDM API . Allows third-party MDM solutions (for example, Airwatch, MaaS360, Meraki, SAP, XenMobile, Symantec, MobileIron, Good, Intune, etc.) to obtain information about the status of a mobile device from ISE.
- AnyConnect Network Visibility Module Collection . Using this API, the AnyConnect security client provides IPFIX data to correlate it with network traffic analysis tools (for example, Cisco Stealthwatch).
- AMP for Endpoints API . An API that allows you to give out security events related to malicious code, Cisco AMP (Advance Malware Protection) security tools that are detected, third-party solutions, or other Cisco solutions (for example, Cisco Cognitive Threat Analytics). Such events may include vulnerable computers, device trajectory (network activity), communication with internal or external nodes, infections, etc.
- ESA REST API . Allows you to collect statistics for security events and E-mail Security Appliance.
- Stealthwatch Data Exporter SDK . Allows you to collect network flow events from the Cisco Stealthwatch network traffic monitoring system and use them for your own purposes.
Let's look at an example of working with the API for AMP for Endpoints , a solution that is placed on personal and mobile devices running Windows, Linux, iOS, Android, MacOS, and which protects against a wide range of threats. Suppose we want to receive security events that have occurred recently. To do this, use the “GET / v1 / events” request, which has many additional options that allow you to make selections on a specific node or group of nodes, the hash of the file of interest, type of event, time, etc. For example, we may be interested in events for a specific node and then the request through AMP for Endpoints API will look like this:
GET /v1/events?connector_guid[]=af73d9d5-ddc5-4c93-9c6d-d5e6b5c5eb01&limit=1 The answer will be as follows:
{ "version": "v1.2.0", "metadata": { "links": { "self": "https://api.amp.cisco.com/v1/events?connector_guid[]=af73d9d5-ddc5-4c93-9c6d-d5e6b5c5eb01&limit=1", "next": "https://api.amp.cisco.com/v1/events?connector_guid%5B%5D=af73d9d5-ddc5-4c93-9c6d-d5e6b5c5eb01&limit=1&offset=1" }, "results": { "total": 41, "current_item_count": 1, "index": 0, "items_per_page": 1 } }, "data": [ { "id": 6455442249407791000, "timestamp": 1503024774, "timestamp_nanoseconds": 98000000, "date": "2017-08-18T02:52:54+00:00", "event_type": "Threat Detected", "event_type_id": 1090519054, "detection": "benign_qa_testware7", "detection_id": "6455442249407791109", "group_guids": [ "b077d6bc-bbdf-42f7-8838-a06053fbd98a" ], "computer": { "connector_guid": "af73d9d5-ddc5-4c93-9c6d-d5e6b5c5eb01", "hostname": "WIN-S1AC1PI6L5L", "external_ip": "10.200.65.31", "user": "johndoe@WIN-S1AC1PI6L5L", "active": true, "network_addresses": [ { "ip": "10.0.2.15", "mac": "08:00:27:85:28:61" } ], "links": { "computer": "https://api.amp.cisco.com/v1/computers/af73d9d5-ddc5-4c93-9c6d-d5e6b5c5eb01", "trajectory": "https://api.amp.cisco.com/v1/computers/af73d9d5-ddc5-4c93-9c6d-d5e6b5c5eb01/trajectory", "group": "https://api.amp.cisco.com/v1/groups/b077d6bc-bbdf-42f7-8838-a06053fbd98a" } }, "file": { "disposition": "Unknown", "file_name": ".zip", "file_path": "\\\\?\\C:\\Users\\johndoe\\Downloads\\.zip", "identity": { "sha256": "f8a6a244138cb1e2f044f63f3dc42beeb555da892bbd7a121274498cbdfc9ad5", "sha1": "20eeee16345e0c1283f7b500126350cb938b8570", "md5": "6853839cde69359049ae6f7bd3ae86d7" }, "archived_file": { "disposition": "Malicious", "identity": { "sha256": "46679a50632d05b99683a14b91a69ce908de1673fbb71e9cd325e5685fcd7e49" } }, "parent": { "process_id": 3416, "disposition": "Clean", "file_name": "explorer.exe", "identity": { "sha256": "80ef843fa78c33b511394a9c7535a9cbace1deb2270e86ee4ad2faffa5b1e7d2", "sha1": "ea97227d34b8526055a543ade7d18587a927f6a3", "md5": "15bc38a7492befe831966adb477cf76f" } } } } ] } The second type of API includes:
- Threat Grid API . Allows you to send suspicious files to the Threat Grid sandbox for analysis and get verdicts about their status (“clean” or malicious). In conditions when antiviruses no longer effectively recognize modern threats, integration with the sandbox (and there are not so many of them in the world) becomes an essential element of the modern protection system. By the way, one of the answers to the file received for the analysis is to obtain an automatically generated signature for Snort. Considering that almost all domestic attack detection systems are basically built on Snort, this feature will be very useful for many applications.
- OpenDNS Investigate API . Allows you to make requests to the cloud service OpenDNS during investigations, incl. to analyze the harmfulness of domains.
- OpenDNS Umbrella API . Allows you to implement custom policies for controlling access to the Internet, blocking specific domains that are missing in the base of OpenDNS.
As an example, the second type of API will look at how the Threat Grid API is used . Suppose we want to check the status of a previously loaded file for analysis. Such a request might look like this:
https://panacea.threatgrid.com/api/v2/search/submissions?q=23aea7cf60fca3c6527c2b5255c6036f2dc414f8368196e198df091cf03dd95f&api_key=llgtslnd5cvb14h4p8m6e6s27f&before=2017-02-28&limit=1 and the answer is:
{ "api_version": 2, "id": 7589645, "data": { "index": 0, "total": 3, "took": 416, "timed_out": false, "items_per_page": 1, "current_item_count": 1, "items": [ { "item": { "properties": { "metadata": null }, "tags": [ "Kovter" ], "vm_runtime": 300, "md5": "f3247e81cc3474559d0e14e2f15837d0", "private": false, "organization_id": 1, "state": "succ", "login": "adminharry", "sha1": "bfafd7f2cd9adff7782f4854bc712bf134ad56f6", "sample": "9b7ad0711262b31219ea1d41119868d8", "filename": "23aea7cf60fca3c6527c2b5255c6036f2dc414f8368196e198df091cf03dd95f", "analysis": { "metadata": { "malware_desc": [ { "sha1": "bfafd7f2cd9adff7782f4854bc712bf134ad56f6", "magic": "PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows", "filename": "23aea7cf60fca3c6527c2b5255c6036f2dc414f8368196e198df091cf03dd95f.exe", "size": 369566, "sha256": "23aea7cf60fca3c6527c2b5255c6036f2dc414f8368196e198df091cf03dd95f", "type": "exe", "md5": "f3247e81cc3474559d0e14e2f15837d0" } ], "sandcastle_env": { "controlsubject": "winxp-x86-intel-2017.01.17", "vm": "winxp-x86", "vm_id": "9b7ad0711262b31219ea1d41119868d8", "sample_executed": 1487231873, "analysis_end": "2017-02-16T08:03:48Z", "analysis_start": "2017-02-16T07:57:01Z", "run_time": 300, "sandcastle": "3.4.36.10823.577ea7a-1", "current_os": "2600.xpsp.080413-2111" }, "general_details": { "report_created": "2017-02-16T08:03:57Z", "sandbox_version": "pilot-d", "sandbox_id": "car-work-074" } }, "behaviors": [ { "name": "excessive-suspicious-activity", "threat": 90 }, { "name": "pe-encrypted-section", "threat": 9 }, { "name": "process-check-virtualbox", "threat": 90 }, { "name": "memory-execute-readwrite", "threat": 25 }, { "name": "registry-autorun-key-bat-file", "threat": 95 }, { "name": "ie-proxy-disabled", "threat": 49 }, { "name": "malware-kovter-registry", "threat": 95 }, { "name": "registry-large-data-entry", "threat": 40 }, { "name": "service-dll-registration", "threat": 25 }, { "name": "files-created-batch", "threat": 25 }, { "name": "file-handler-registration", "threat": 85 }, { "name": "antivirus-service-flagged-artifact", "threat": 95 }, { "name": "registry-detection-productid", "threat": 42 }, { "name": "registry-script-detected", "threat": 25 }, { "name": "registry-ie-zone-settings-modified", "threat": 49 }, { "name": "modified-file-in-user-dir", "threat": 56 }, { "name": "registry-modified-rootcerts", "threat": 36 }, { "name": "registry-detection-bios", "threat": 42 }, { "name": "mshta-in-registry", "threat": 95 }, { "name": "registry-autorun-key-modified", "threat": 48 } ], "threat_score": 95 }, "status": "job_done", "submitted_at": "2017-02-16T07:57:00Z", "sha256": "23aea7cf60fca3c6527c2b5255c6036f2dc414f8368196e198df091cf03dd95f" }, "score": 0.7660416, "matches": null } ] } } We see that the Threat Grid API returns us the value of the threat level by a hundred point scale for different types of file behavior (Threat Grid can evaluate up to 800 different parameters depending on the loaded file). The total value (threat_score) is 95, which means that the file being analyzed is malicious.
We can give an example of working with another API that allows evaluating the security of domains, information about which we can receive from ITU, mail gateways, proxies, Internet access control tools, etc. Using the OpenDNS Investigate API, we can formulate a request to verify the domain of interest to us:
curl --include \ --header "Authorization: Bearer %YourToken%" \ https://investigate.api.opendns.com/security/name/{name}.json And in the answer we get the values of various parameters by which OpenDNS evaluates the security of domains, IP addresses, autonomous systems, etc .:
{ "dga_score": 38.301771886101335, "perplexity": 0.4540313302593146, "entropy": 2.5216406363433186, "securerank2": -1.3135141095601992, "pagerank": 0.0262532, "asn_score": -29.75810625887133, "prefix_score": -64.9070502788884, "rip_score": -75.64720536038982, "popularity": 25.335450495507196, "fastflux": false, "geodiversity": [ [ "UA", 0.24074075 ], [ "IN", 0.018518519 ] ], "geodiversity_normalized": [ [ "AP", 0.3761535390278368 ], [ "US", 0.0005015965168831449 ] ], "tld_geodiversity": [], "geoscore": 0, "ks_test": 0, "found": true } The third type of API includes:
- Remediation API . Allows third-party solutions to manage Cisco Firepower multi-functional security platform.
- FirePOWER 9300 (SSP) REST API . Allows you to build configuration service chains.
- Read / Write REST API for Firepower . Allows you to perform various operations on objects with which Firepower works.
- Management API for ASA . Providing Cisco ASA management from third-party solutions, auditing information security policies, etc.
- CloudLock Enterprise API . Allows you to manage the Cisco CloudLock cloud access control platform and report generation based on information received from CloudLock.
- CloudLock Development API . Allows you to manage cloud micro-services.
- pxGrid . An API that allows not only to give contextual information, but also to manage network access, blocking users and devices through Cisco ISE at the level of switches, routers, access points, etc.
- AMP for Endpoints API . Allows you to manage black lists of applications on AMP for Endpoints, transfer computers from one group to another, etc.

The fourth type includes
- Threat Intelligence Director . A solution that enables Cisco Firepower Multi-Purpose Security Platform to receive and correlate Threat Intelligence data not only from Cisco Talos, but also from external TI platforms that support STIX and TAXII protocols and standards.
- AMP Cloud-based API . An API that allows you not only to send security events related to malicious code, but also to access external Threat Intelligence services. For example, Cisco AMP for Endpoint can not only send suspicious files to the cloud or local Cisco AMP Threat Grid sandbox, but also, for example, to Virus Total.
A natural question arises: how to get access to these APIs? Everything is very simple. Cisco has a special Cisco Security Technical Alliance Program, which consists of two large sections:
- DevNet . This is a two-part platform. The sandbox ( DevNet Sandbox ) provides access to software and hardware, physical and virtual, for rapid development and testing of appropriate solutions. Work with DevNet is free and provided from any device connected to the Internet. The second component of DevNet is a learning lab ( DevNet Learning Labs ), which provides access to learning content, code examples, related to integration with Cisco solutions. The training lab is also free and available to everyone. Most of the APIs mentioned above are presented in DevNet, but there are also separate, more detailed sections on the Cisco website, immersing you with programming features for Cisco security solutions (to access some of them you need to have access to the corresponding products or services).
- Cisco Solution Partner Program (SPP) . If DevNet is a self-service platform that you use to develop and test your integration solutions, then SPP is the next step, which implies a more formal relationship with Cisco. We are talking about independent testing of the developed integration solution, obtaining the status of a technology partner and including its solutions in the corresponding catalog on the Cisco website, which millions of companies around the world have access to.

In order to integrate your SIEMs and SOCs with Cisco solutions, it is enough just to register on DevNet and, having received code samples, modify your solutions by equipping them with the appropriate components and software calls through the API. In principle, this is already enough to interact with Cisco security solutions. This is completely free (excluding your programmers' salaries). If your task is to enter the international market, to demonstrate your products to a wide audience, to prove serious intentions for integration with Cisco, which is the world leader in the cybersecurity market, then certain investments and SPP membership are necessary. It is along this path that companies like Check Point, ThreatQuotient, Anomali, Symantec, etc. went.

I hope that after such a brief excursus, no one will have any doubt that Cisco solutions are open like no one to integrate with external security products and services. In this direction, the company has been moving for several years, confirming the previously put forward slogan, which the Cisco Cybersecurity Division follows, - “Open. Simple Automation (Openness. Simplicity. Automation).
Source: https://habr.com/ru/post/340788/
All Articles